Azure Active Directory
Azure Authentication with Dex Connecor require Terrakube >= 2.6.0 and Helm Chart >= 2.0.0
Requirements
Azure Active Directory here
Azure Storage Account
For this example lets image that you will be using the following domains to deploy Terrakube.
registry.terrakube.azure.com
ui.terrakube.azure.com
api.terrakube.azure.com
Setup Azure Authentication
You need to complete the Azure authentication setup for Dex. You can found information in this link
You need to go to your Azure and create a new Application
After the application is created you need to add the redirect URL.
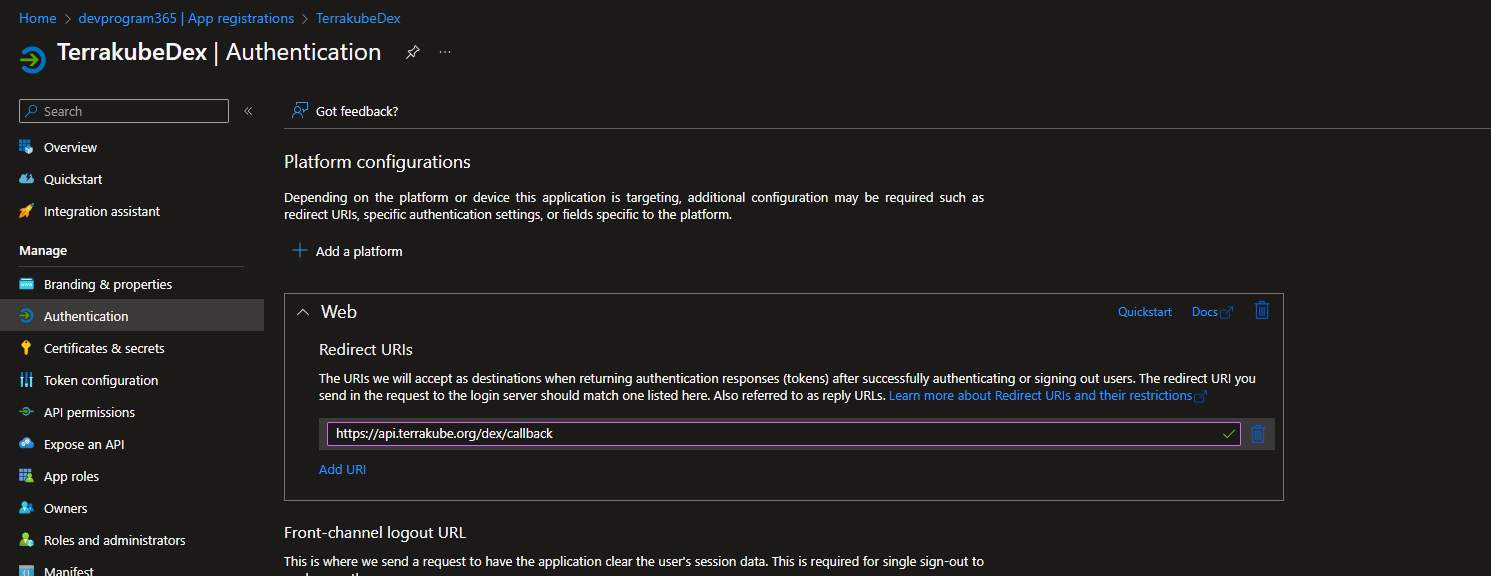
You will also need to add the permission Directory.Read.All and ask a Azure administrator to approve the permission.
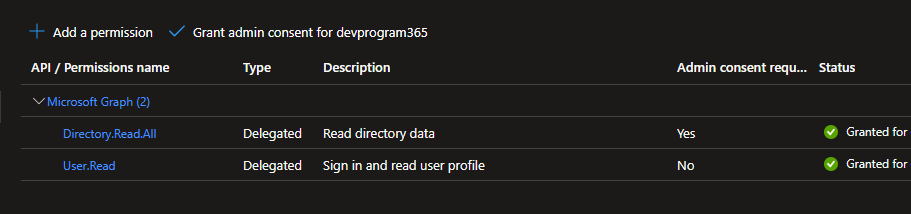
Now you can create the DEX configuration, you will use this config later when deploying the helm chart.
The firt step is to clone the repository.
Replace <<CHANGE_THIS>> with the real values, create the values.yaml file and run the helm install
Run the installation
For any question or feedback please open an issue in our helm chart repository