Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
To use Terrakube’s VCS features with a self-hosted GitHub Enterprise, follow these instructions. For GitHub.com, see the separate instructions.
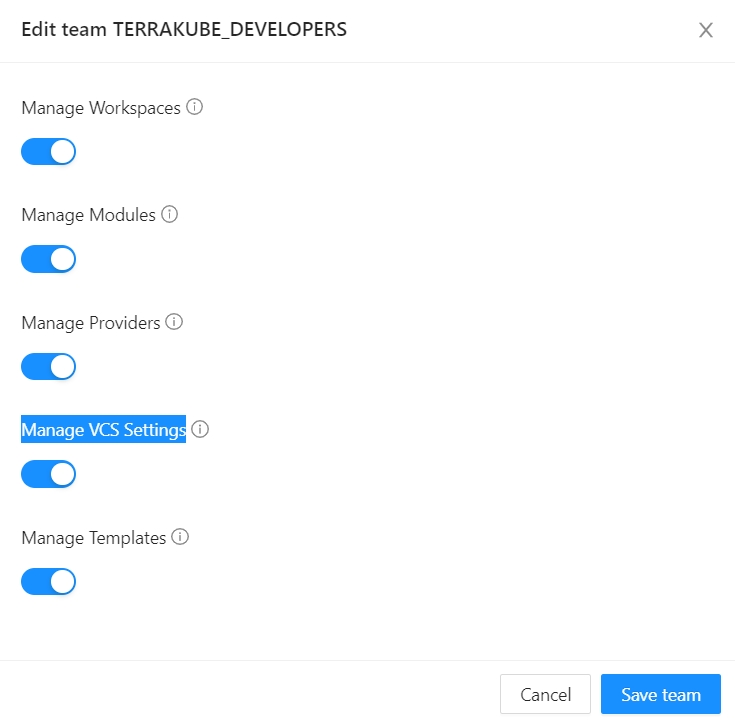
Manage VCS Providers permission is required to perform this action, please check Team Management for more info.
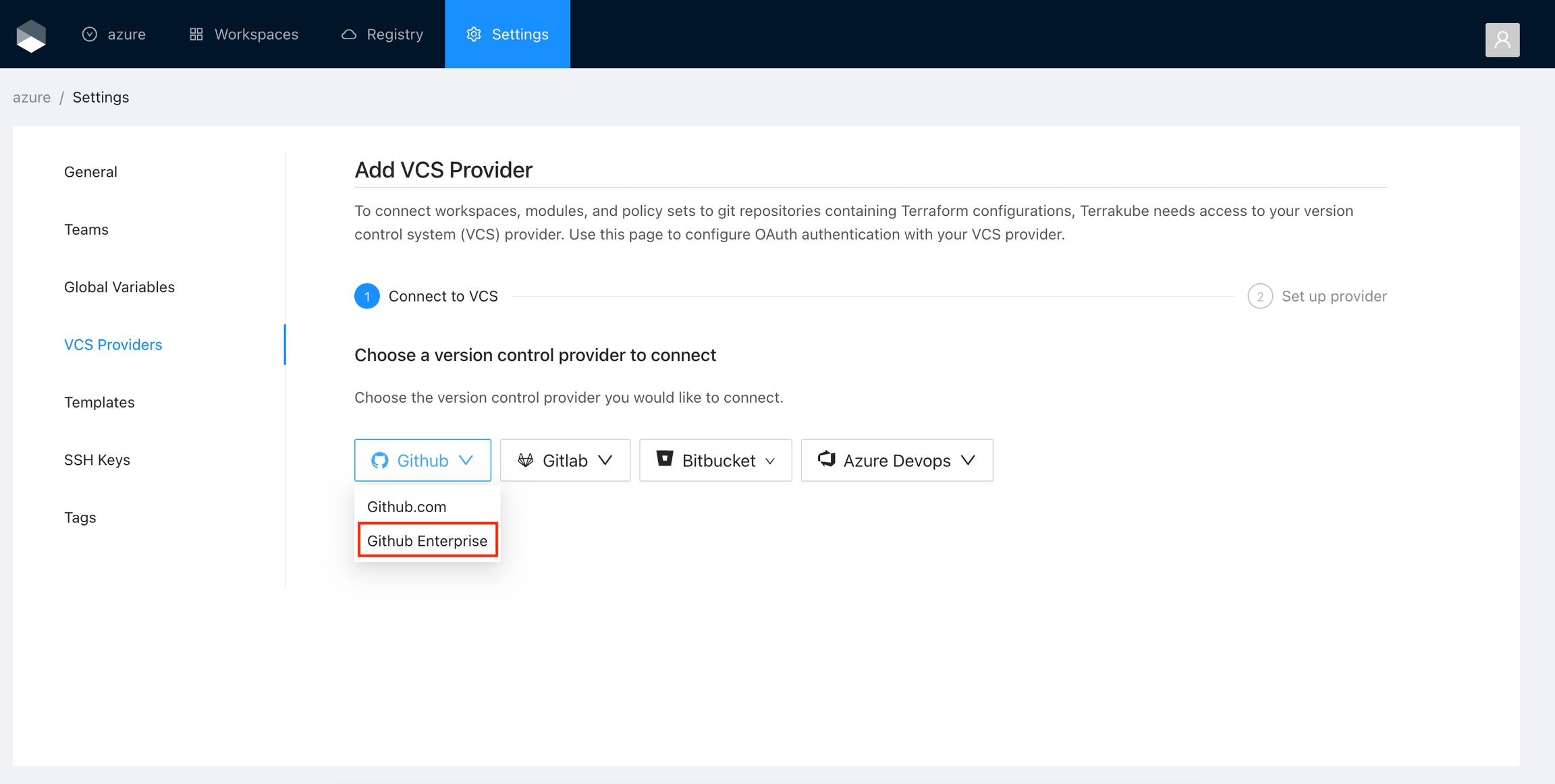
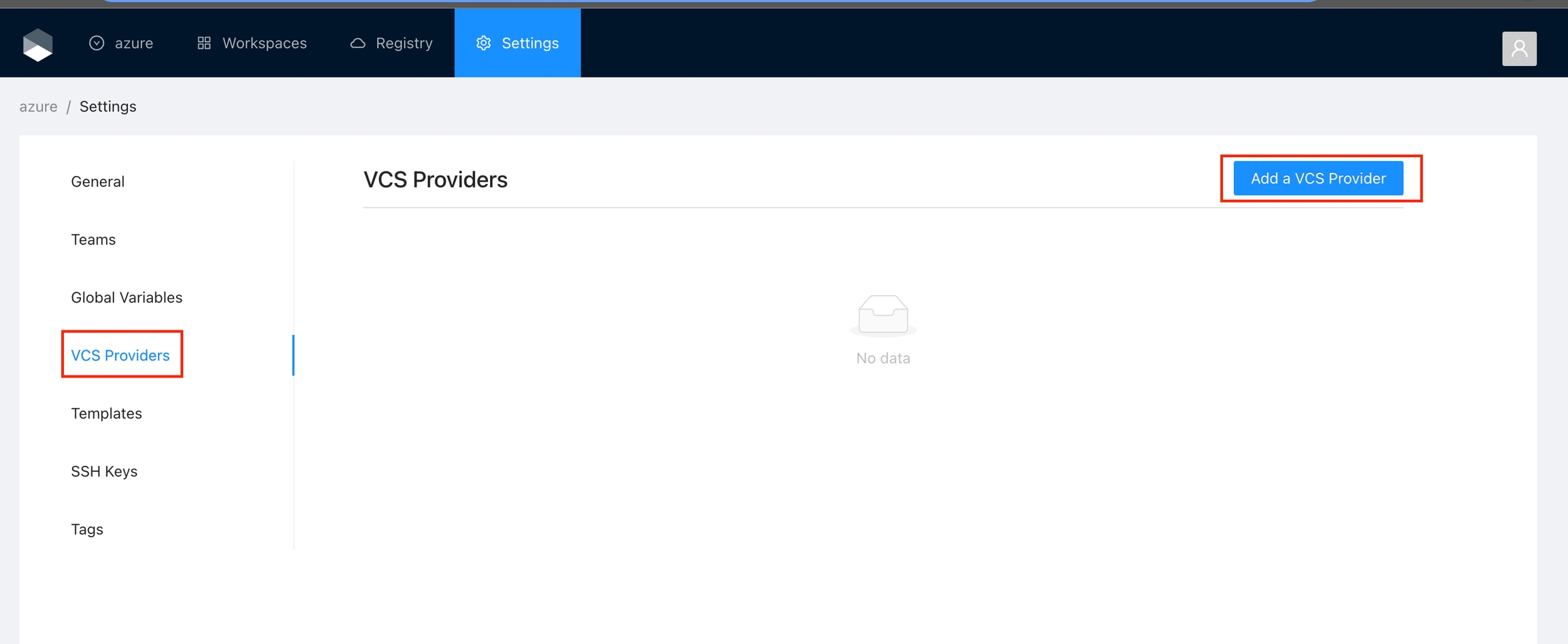
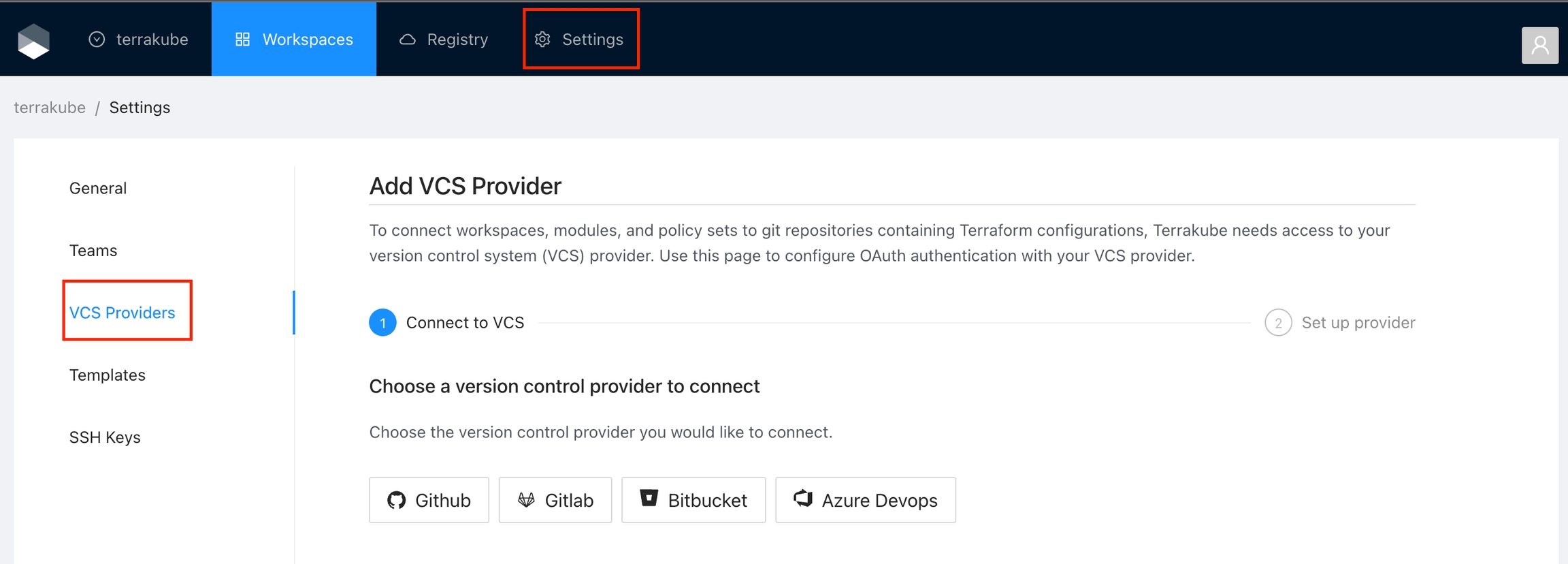
Got to the organization settings you want to configure. Select the VCS Providers on the left menu and click the Add VCS provider button on the top right corner..
If you prefer, you can add a new VCS Provider directly from the Create workspace or Create Module screen.
Click the Github button and then click the Github Enterprise option.
On the next screen, enter the following information about your Github Enterprise instance:
HTTP URL
https://<GITHUB INSTANCE HOSTNAME>
API URL
https://<GITHUB INSTANCE HOSTNAME>/api/v3
Use a different browser tab to access your GitHub Enterprise instance and sign in with the account that you want Terrakube to use. You should use a service user account for your organization, but you can also use a personal account.
Note: The account that connects Terrakube with your GitHub Enterprise instance needs to have admin rights to any shared Terraform configuration repositories. This is because creating webhooks requires admin permissions.
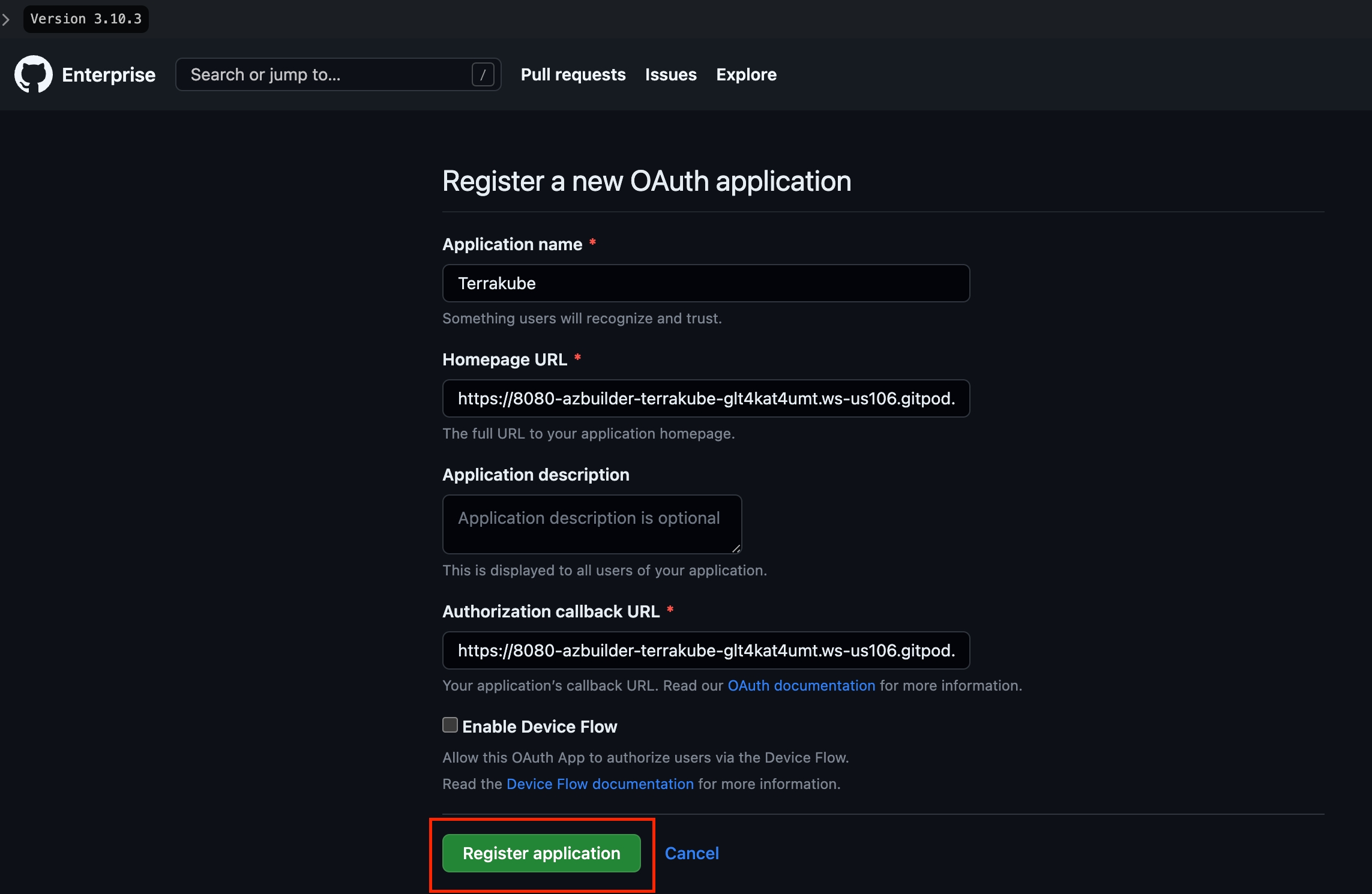
Navigate to GitHub's Register a New OAuth Application page. This page is located at https://<GITHUB INSTANCE HOSTNAME>/settings/applications/new
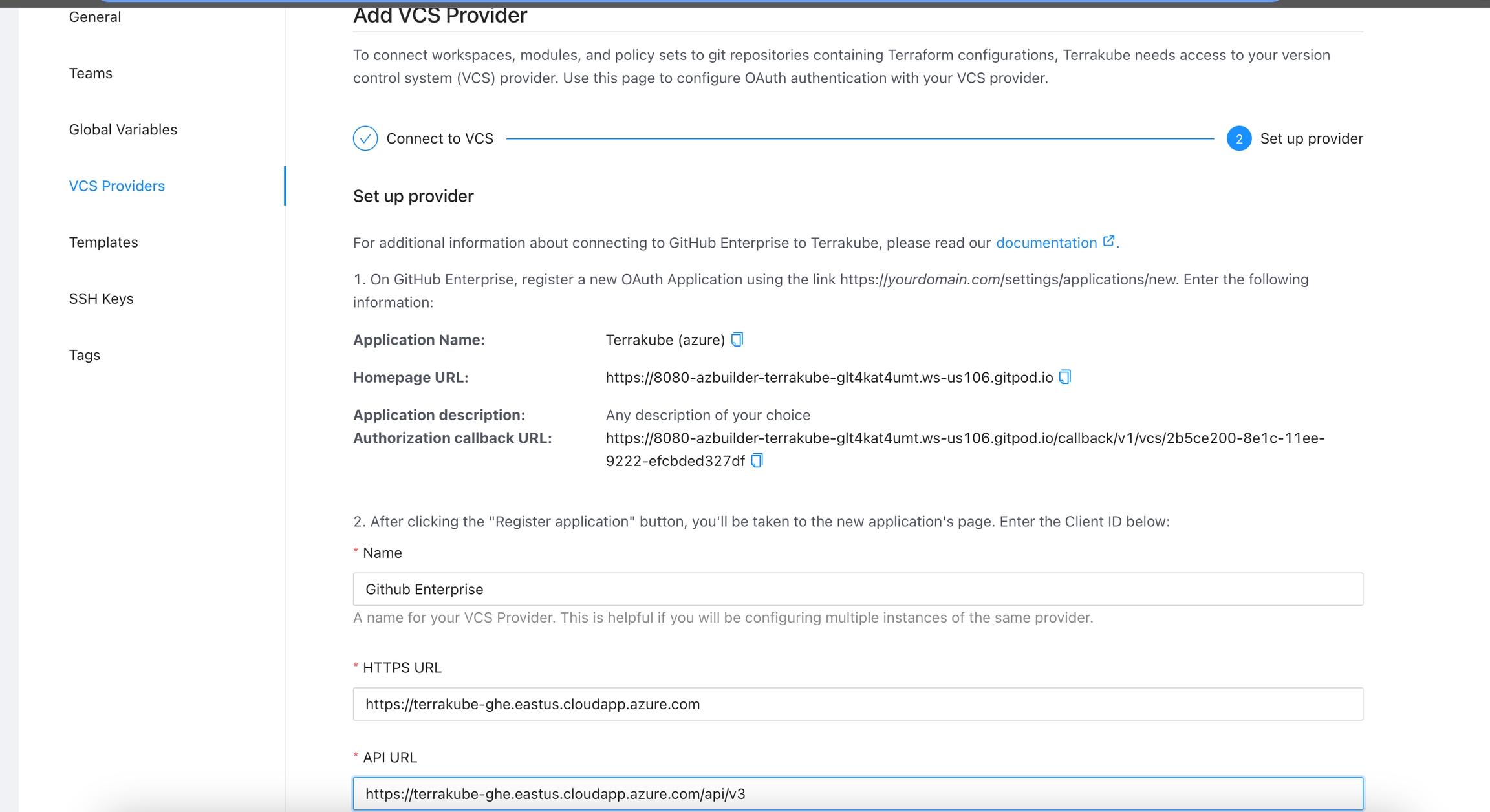
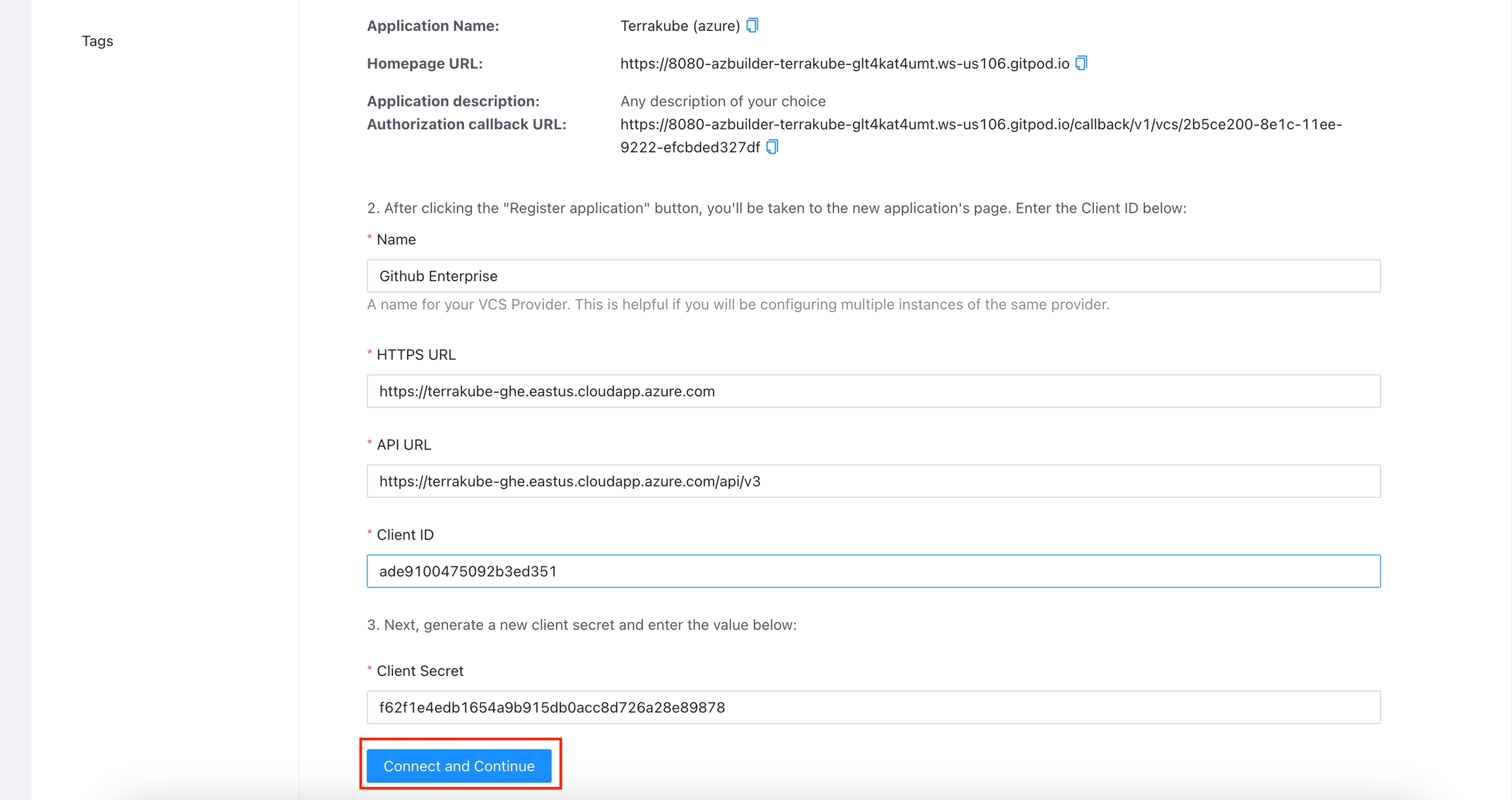
In the Github Enterprise page, complete the required fields and click Register application
Application Name
Your application name, for example you can use your organization name.
Homepage URL
The url for your application or website,
Application Description
Any description you choice
Authorization Callback URL
Copy the callback url from the Terrakube UI
You can complete the fields using the information suggested by terrakube in the VCS provider screen
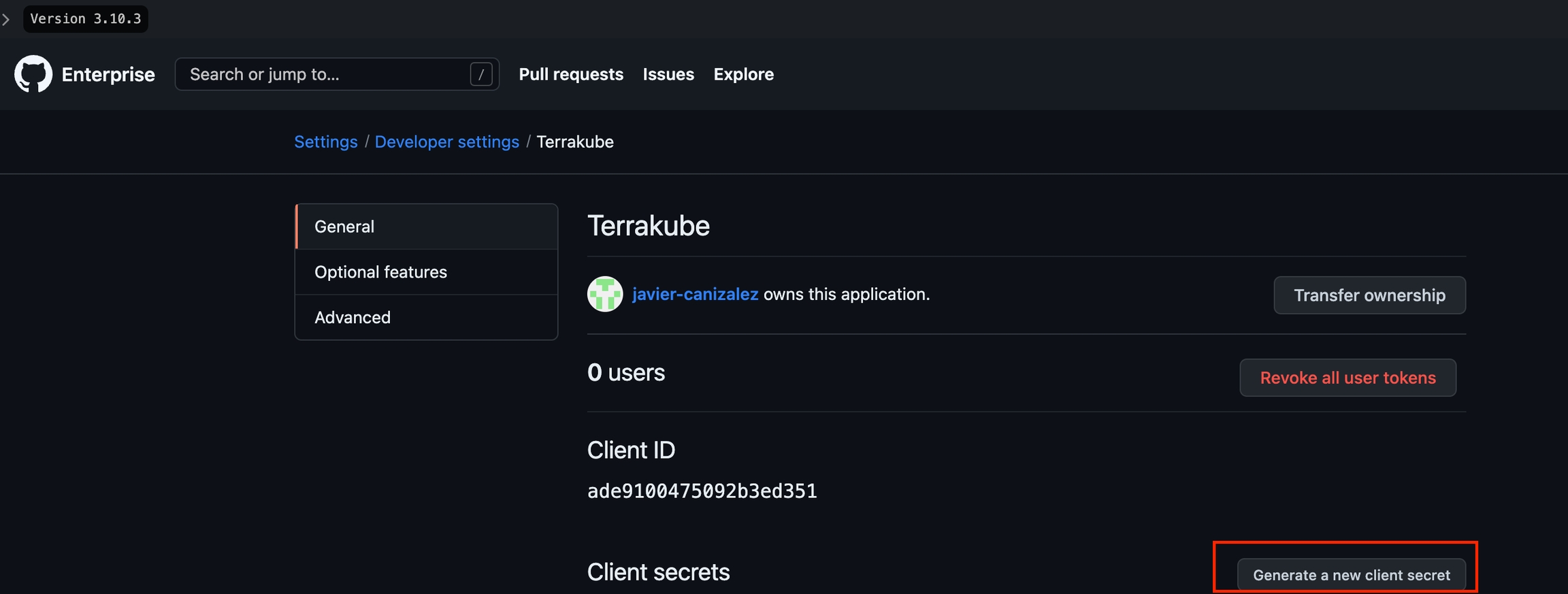
Next, generate a new client secret
Copy the Client Id and Client Secret from Github Enterprise and go back to Terrakube to complete the required information. Then, click the Connect and Continue button
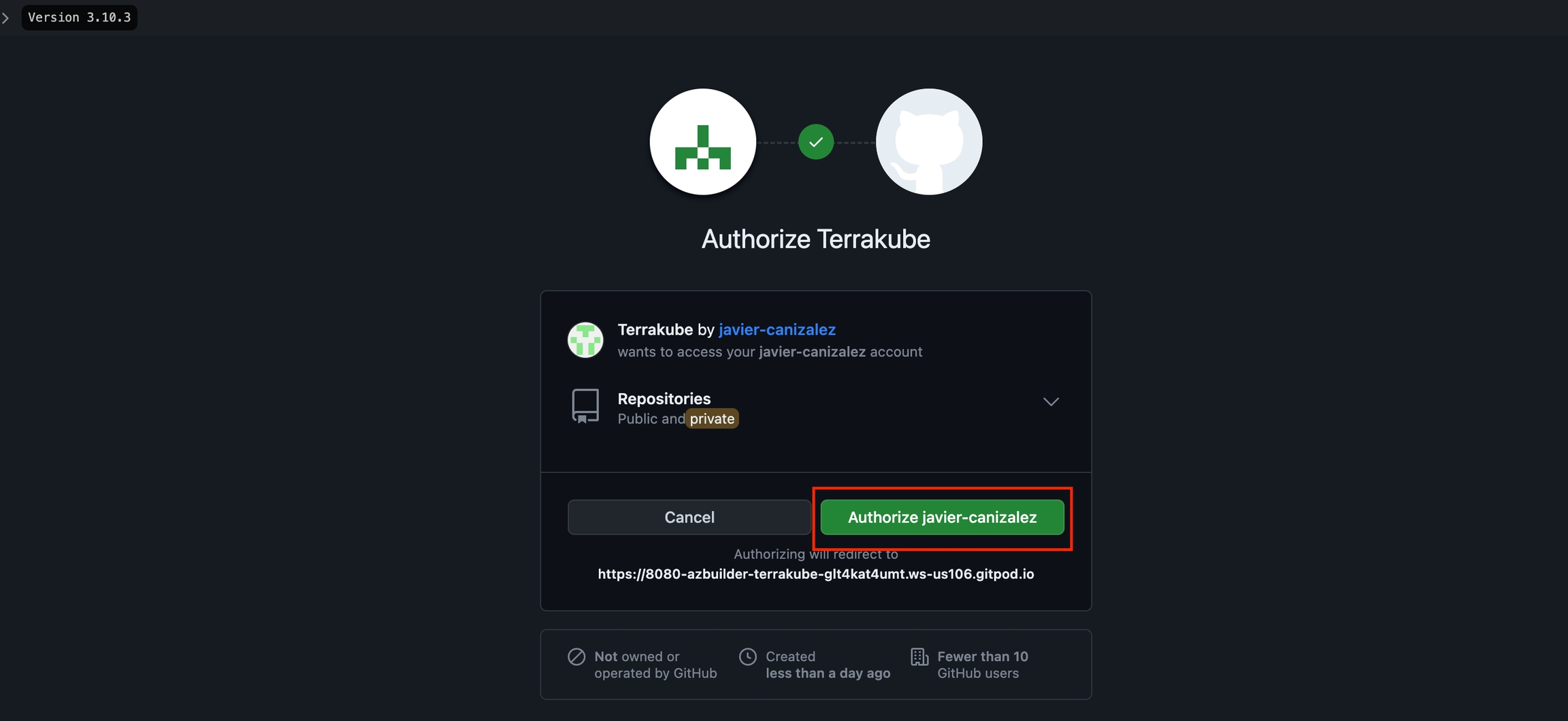
You will be redirected to Github Enterprise. Click the Authorize button to complete the connection.
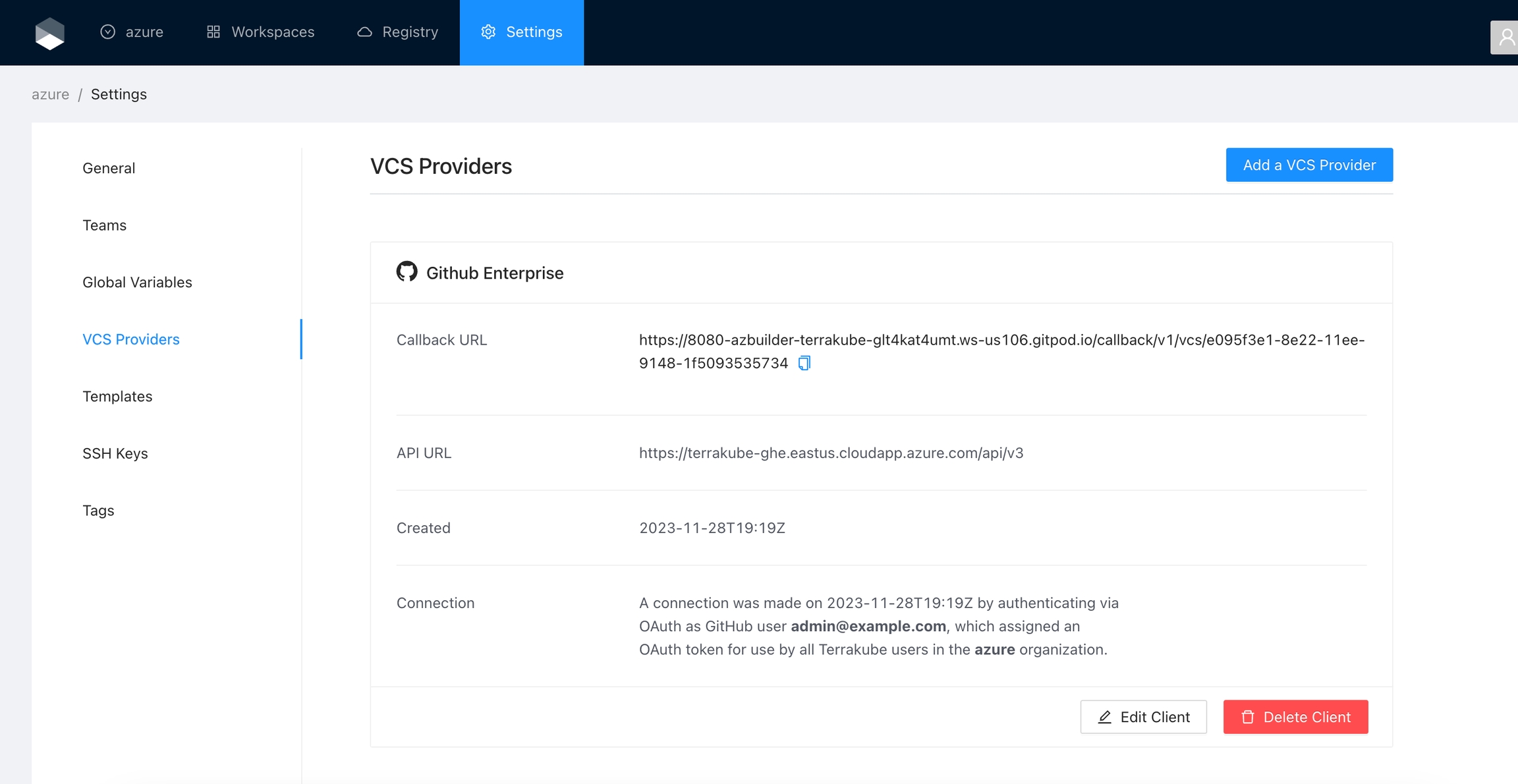
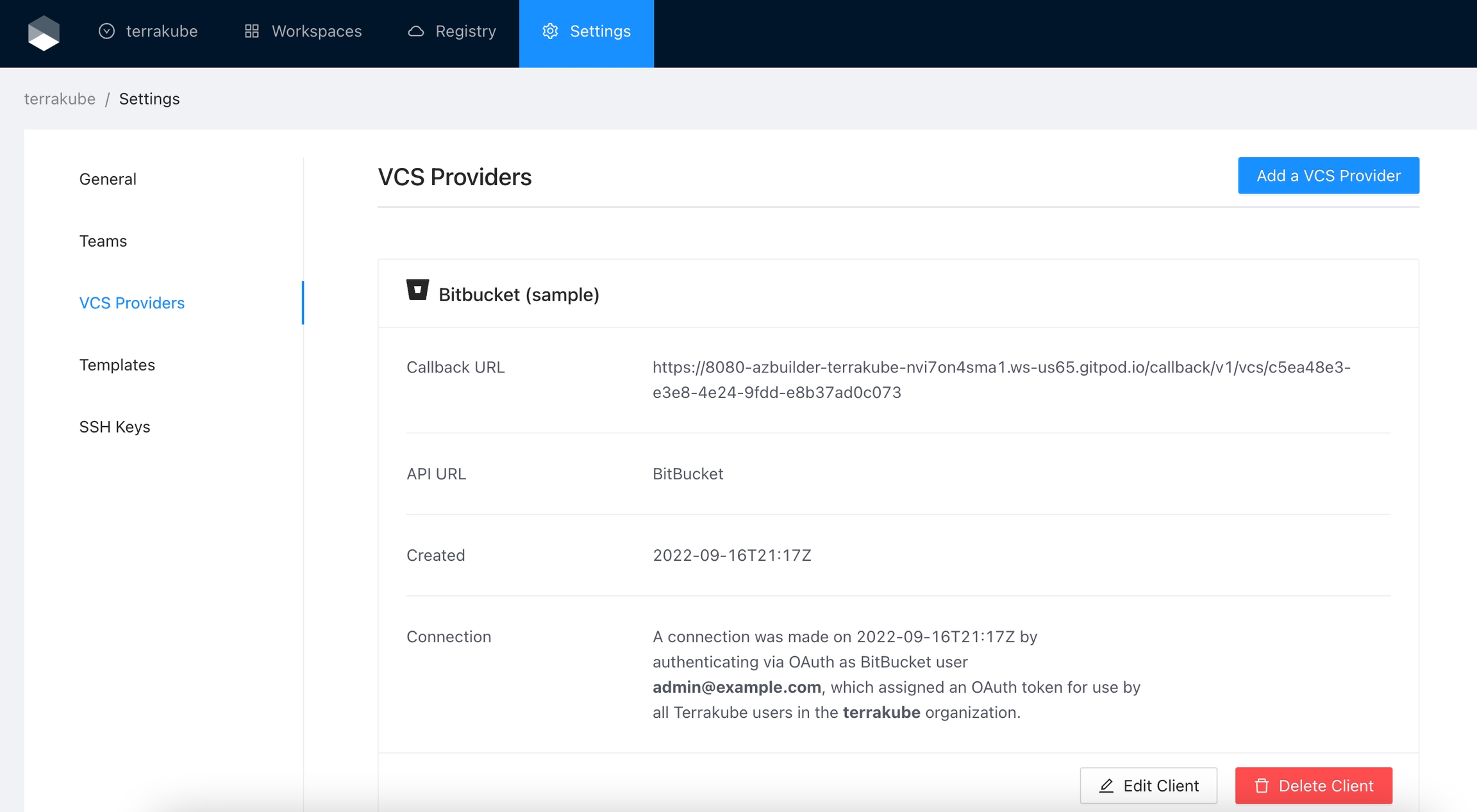
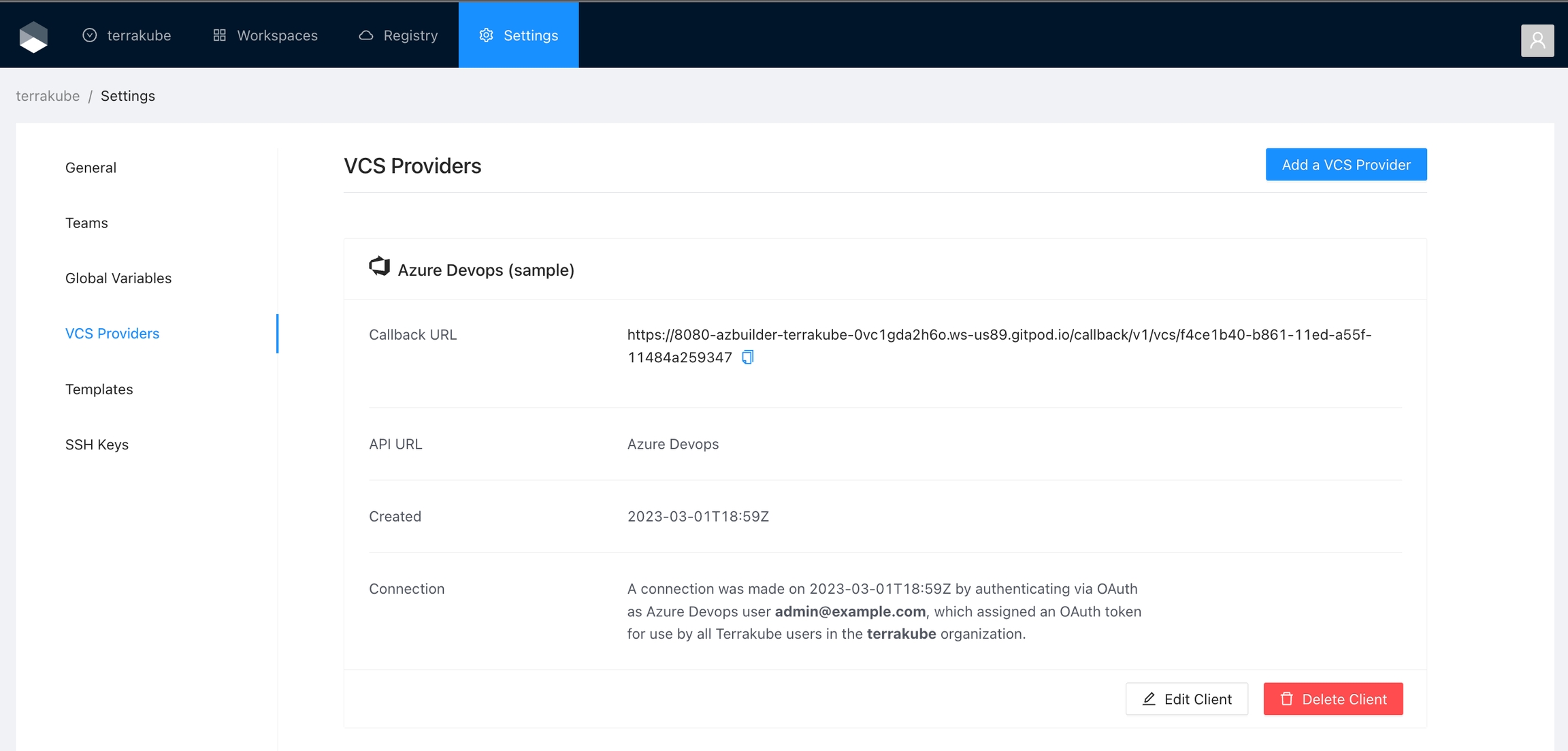
When the connection is successful, you will go back to the VCS provider’s page in your organization. You will see the connection status, the date, and the user who made the connection.
You can now use the connection for your workspaces and modules.
For using repositories from Gitlab.com with Terrakube workspaces and modules you will need to follow these steps:
Manage VCS Providers permission is required to perform this action, please check Team Management for more info.
Navigate to the desired organization and click the Settings button, then on the left menu select VCS Providers
If you prefer, you can add a new VCS Provider directly from the Create workspace or Create Module screen.
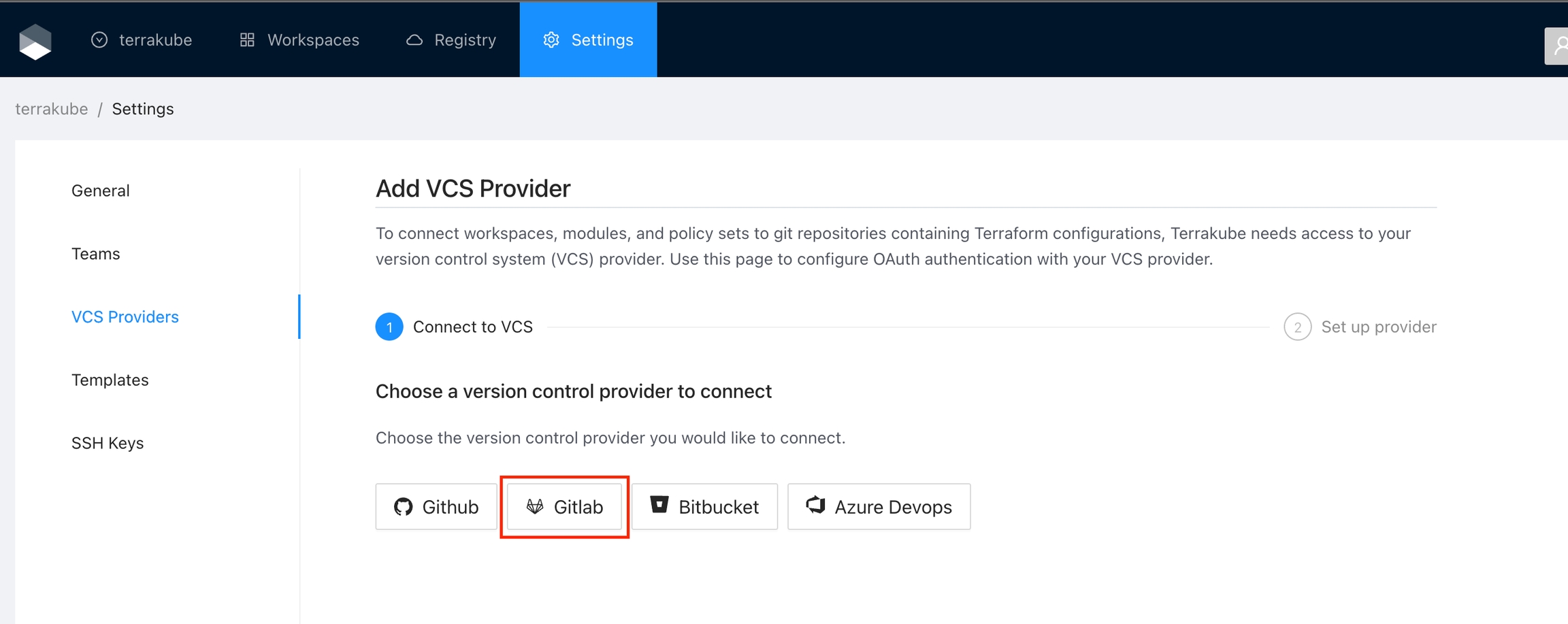
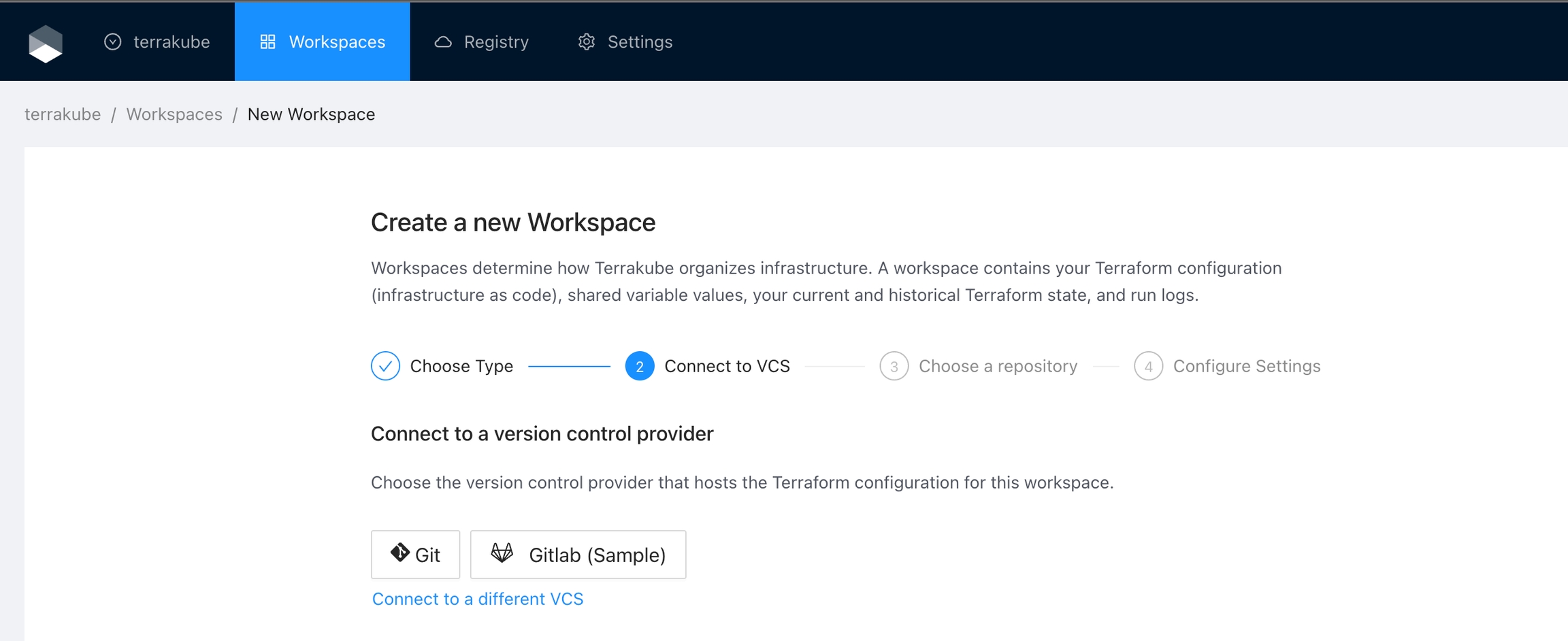
Click the Gitlab button
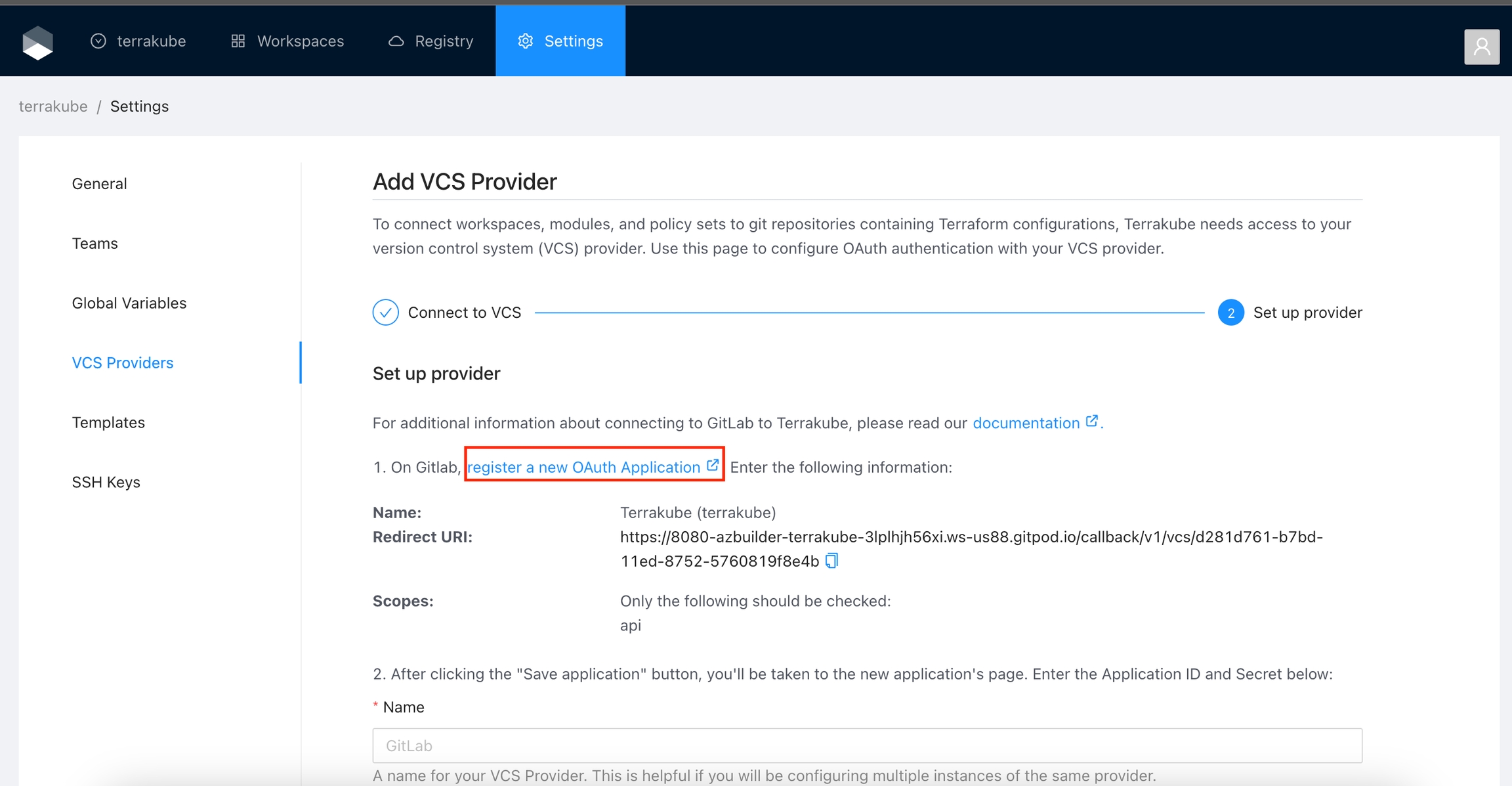
In the next screen click the link to register a new OAuth Application in Gitlab
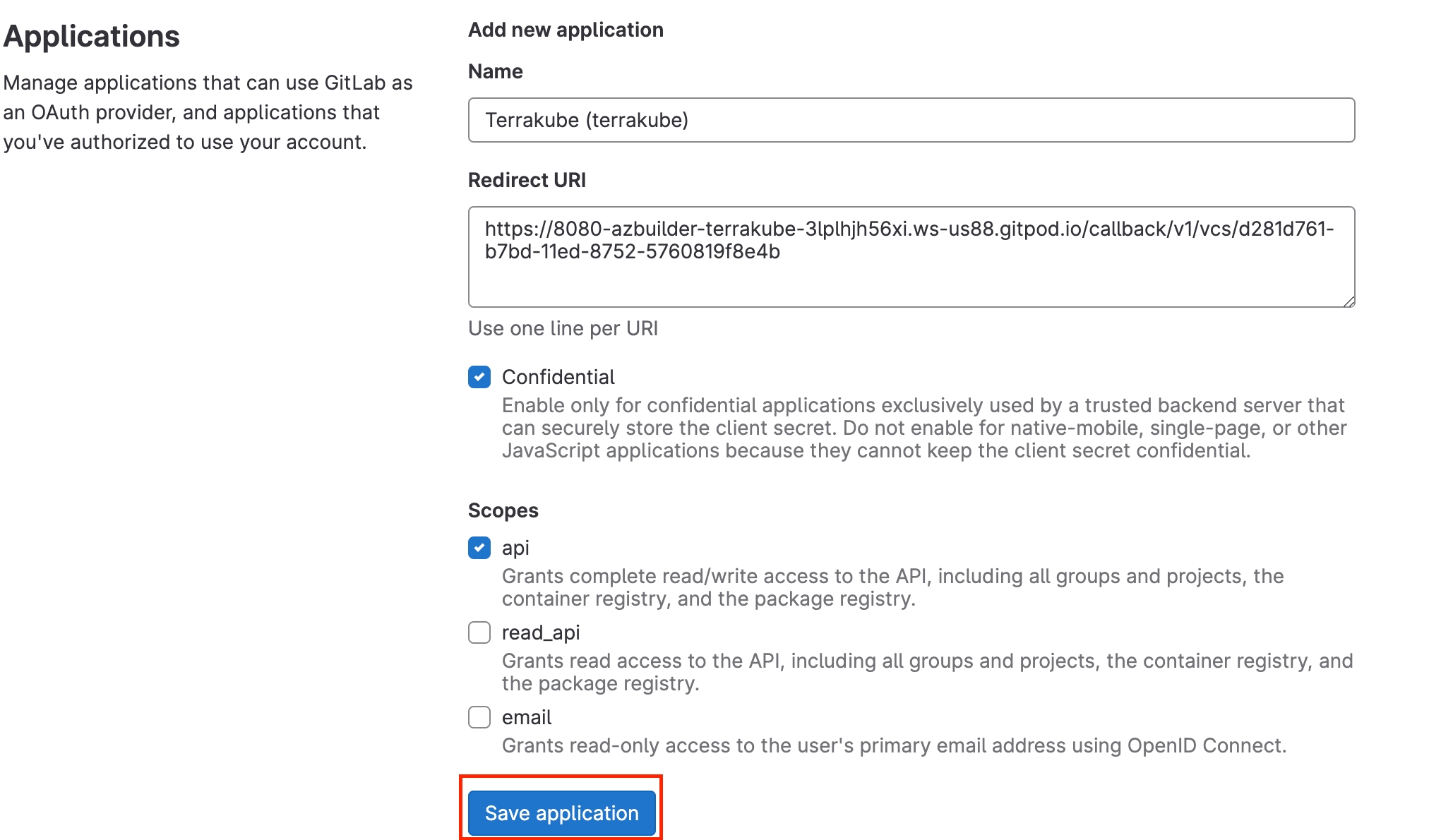
On Gitlab, complete the required fields and click Save application button
Name
Your application name, for example you can use your organization name.
Redirect URI
Copy the Redirect URI from the UI
Scopes
Only api should be checked
You can complete the fields using the information suggested by terrakube in the VCS provider screen
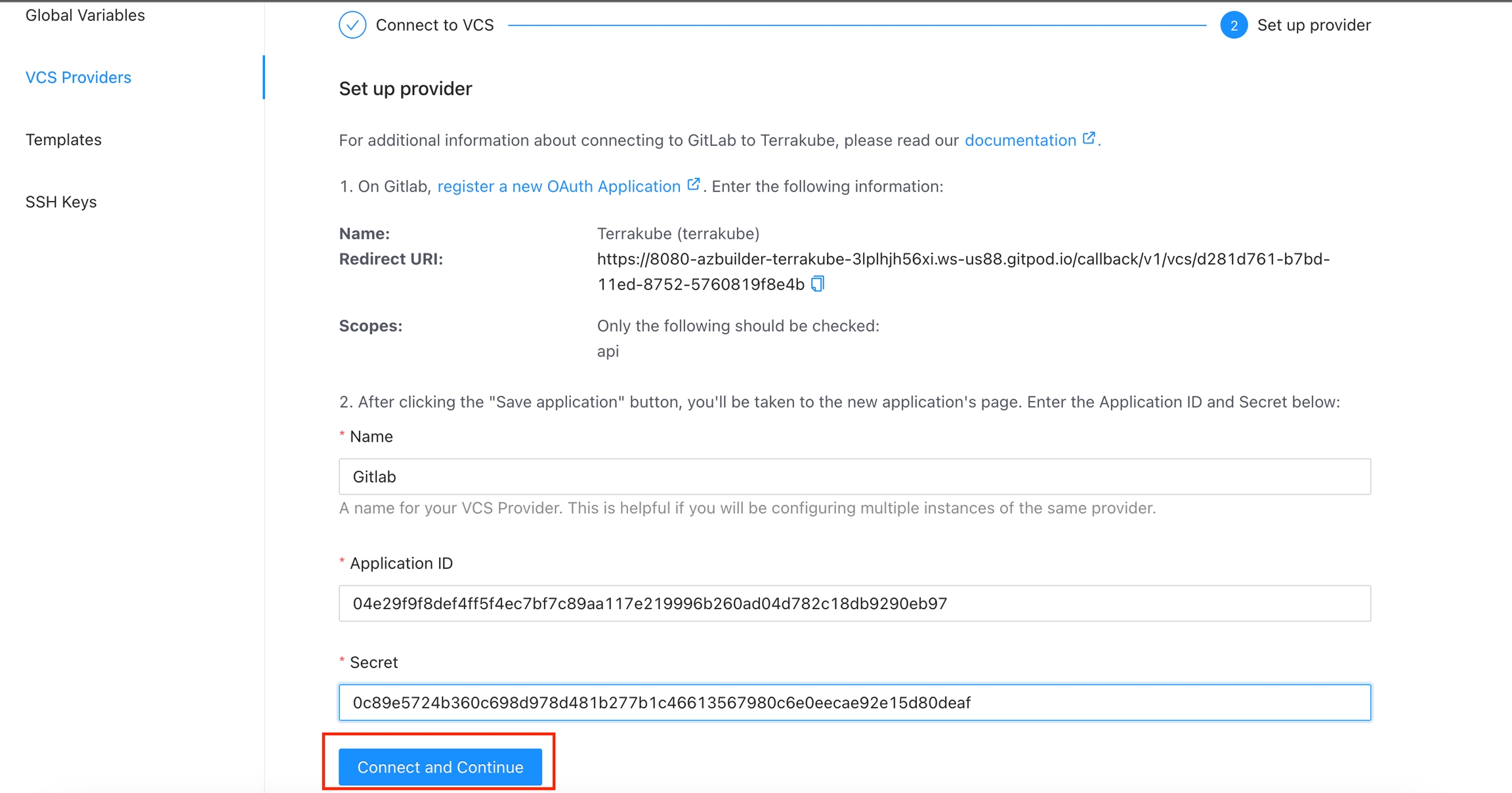
In the next screen, copy the Application ID and Secret
Go back to Terrakube to enter the information you copied from the previous step. Then, click the Connect and Continue button.
You will see a Gitlab window, click the Authorize button to complete the connection
Finally, if the connection was established successfully, you will be redirected to the VCS provider’s page in your organization. You should see the connection status with the date and the user that created the connection.
And now, you will be able to use the connection in your workspaces and modules:
Work in progress
For using repositories from Bitbucket.com with Terrakube workspaces and modules you will need to follow these steps:
Manage VCS Providers permission is required to perform this action, please check Team Management for more info.
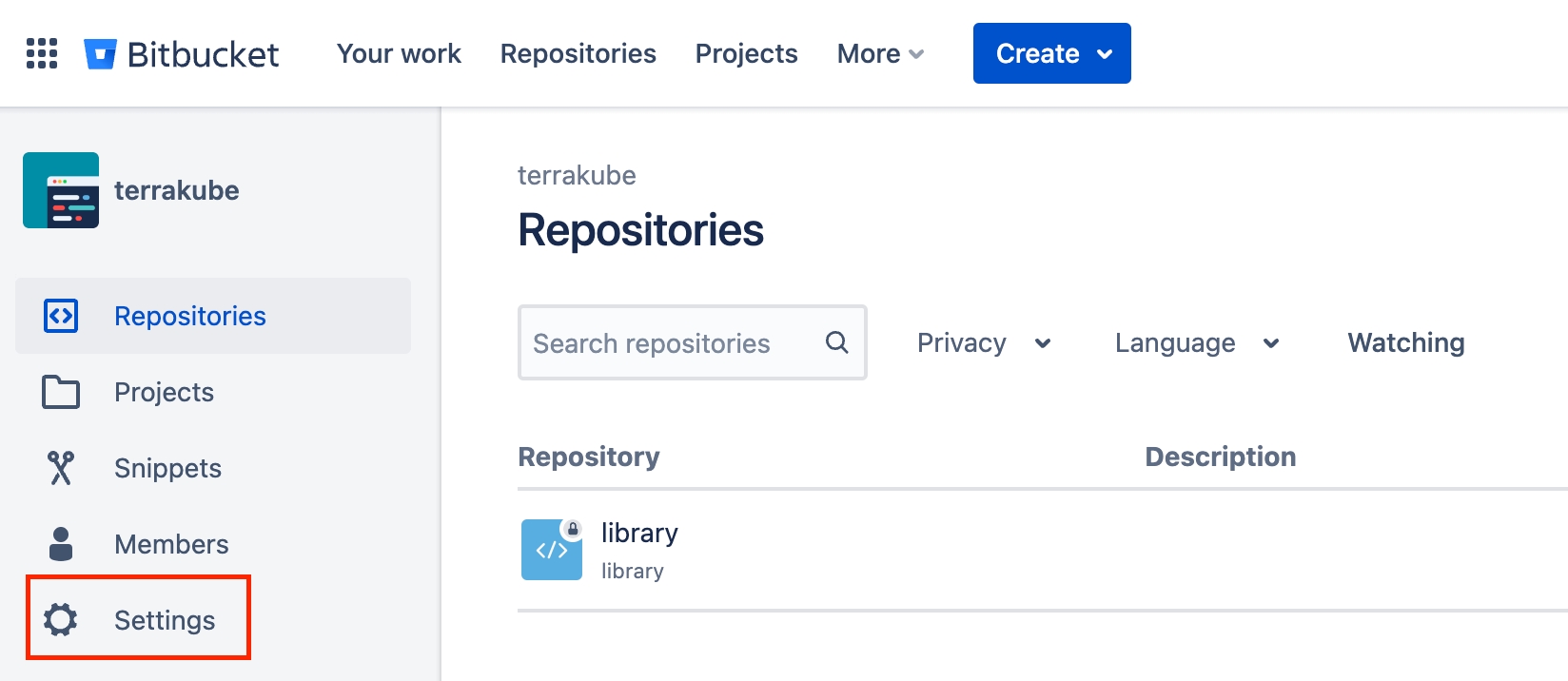
Navigate to the desired organization and click the Settings button, then on the left menu select VCS Providers
If you prefer, you can add a new VCS Provider directly from the Create workspace or Create Module screen.
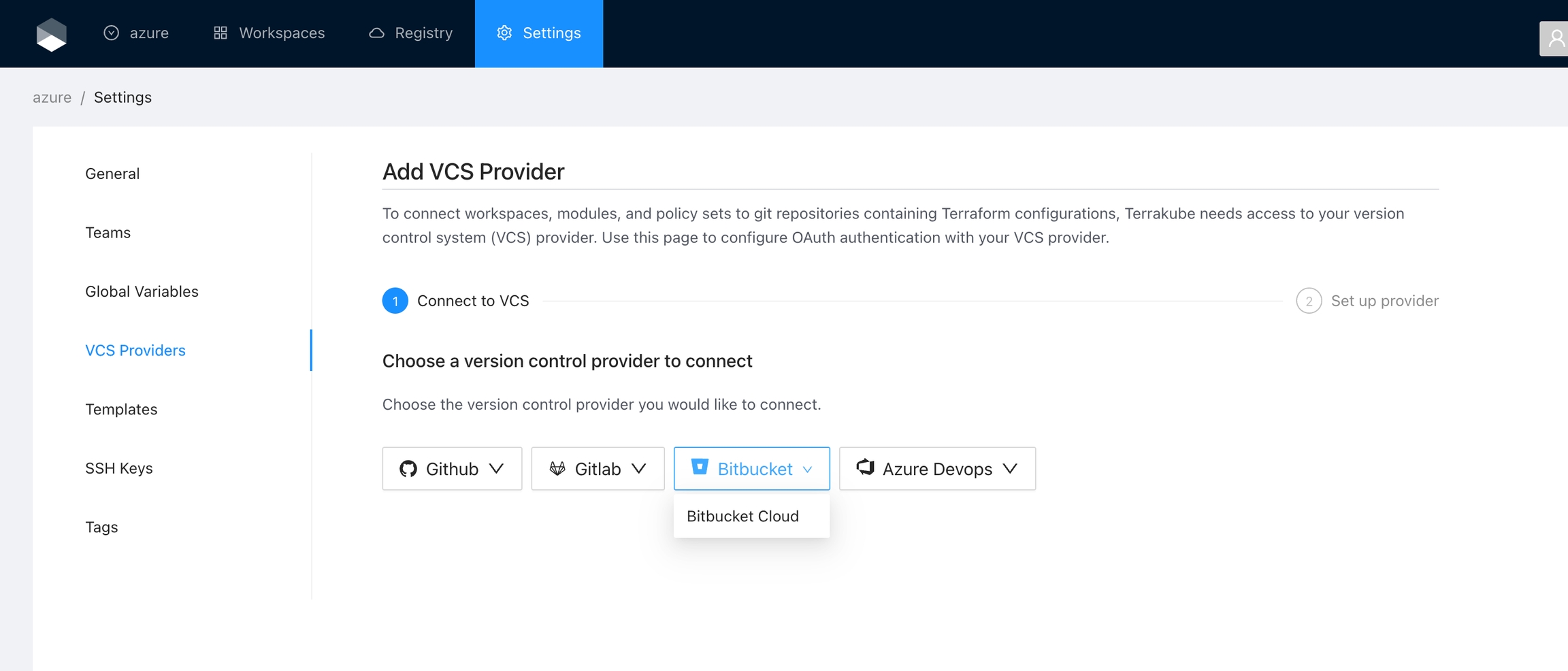
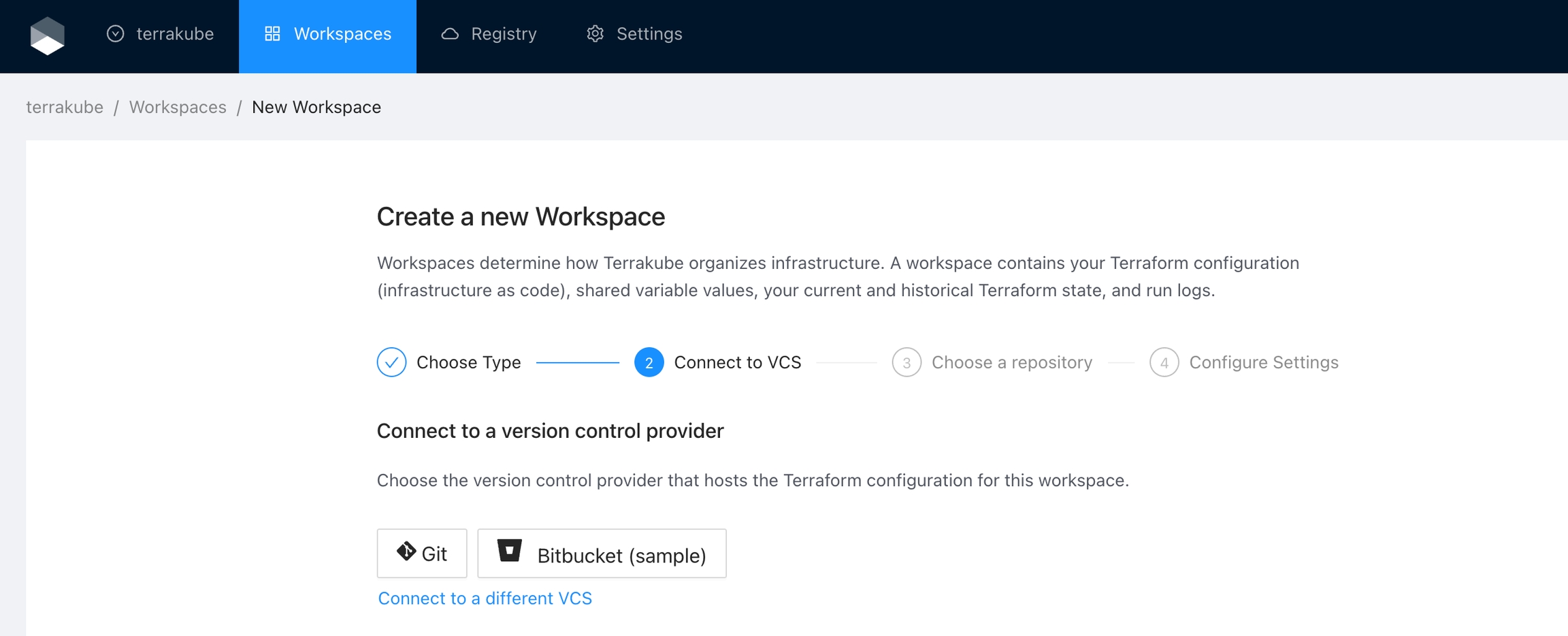
Click the Bitbucket button and then click the Bitbucket Cloud option
Open Bitbucket Cloud and log in as whichever account you want Terrakube to use and click the settings button in your workspace
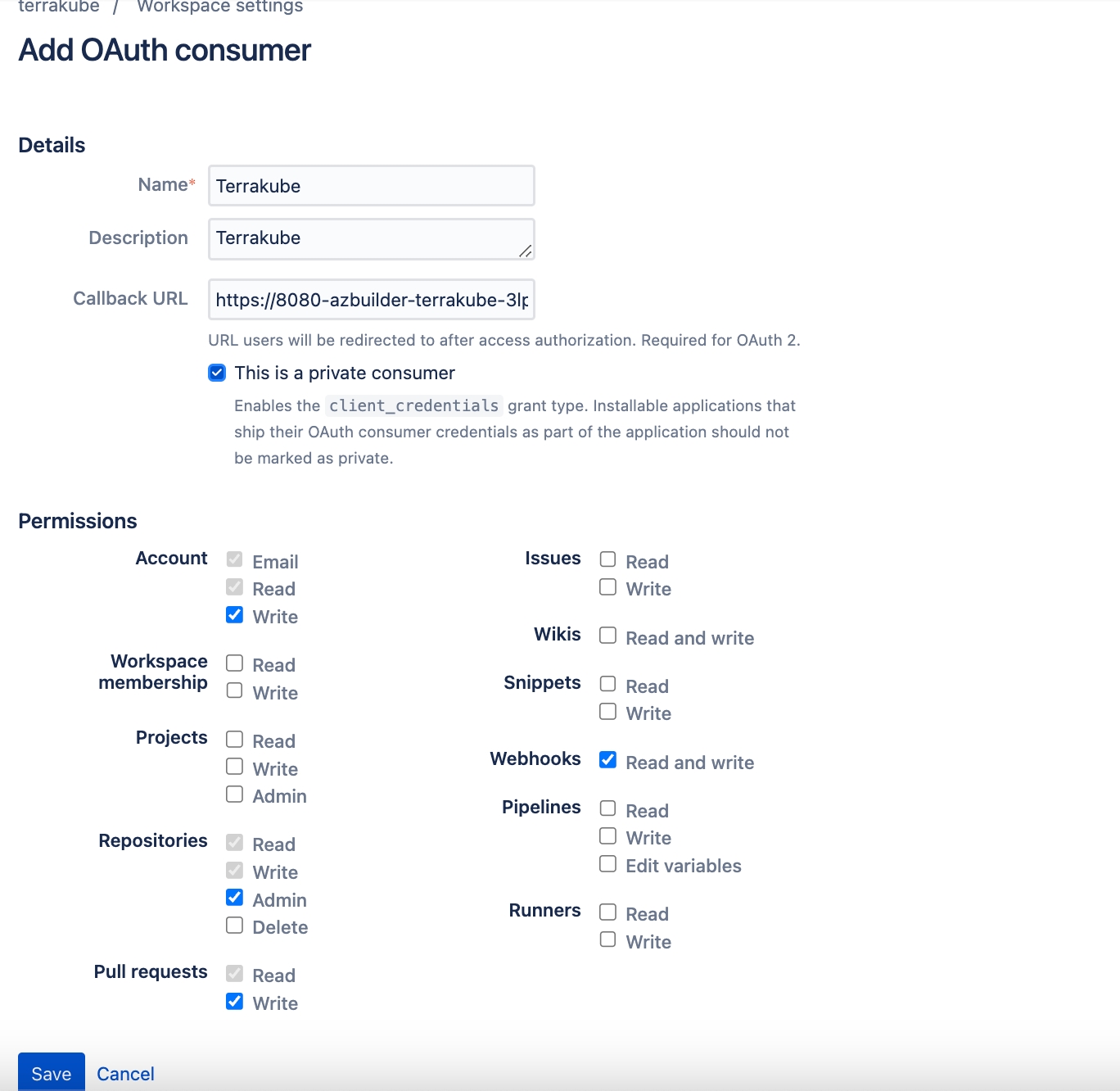
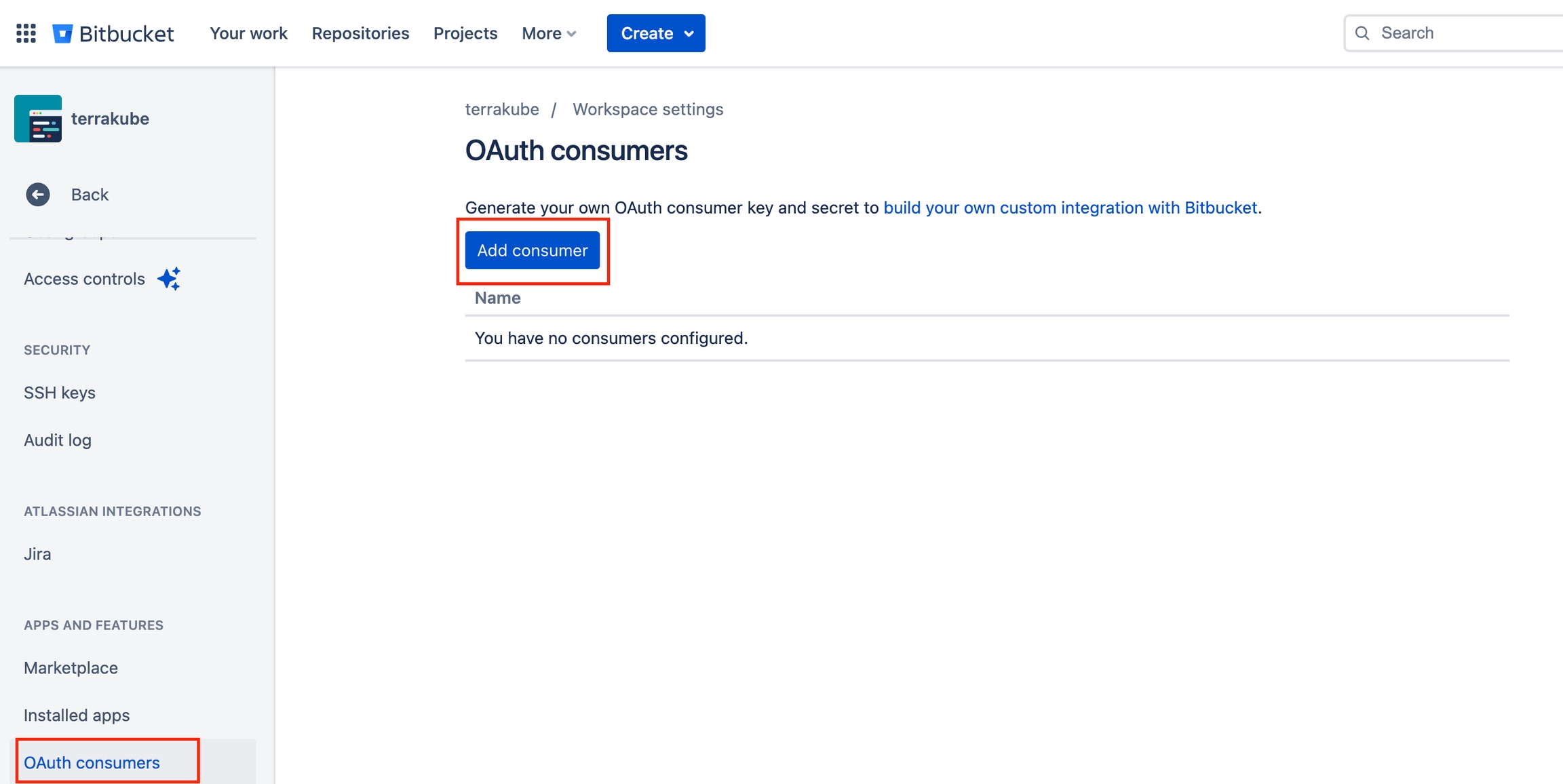
Click the OAuth consumers menu and then click the Add consumer button
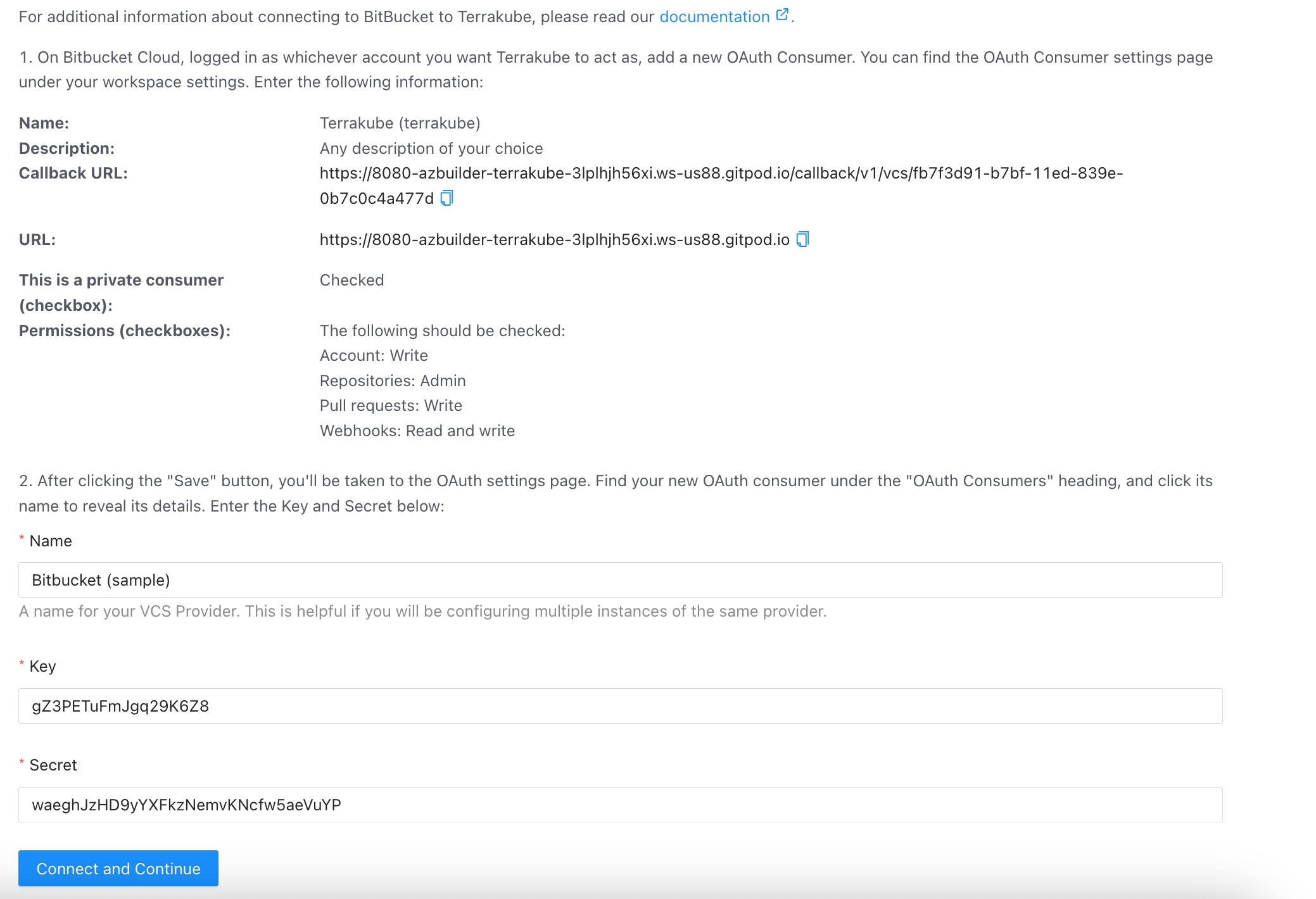
Complete the required fields and click Save button
Name
Your application name, for example you can use your organization name.
Description
Any description of your choice
Redirect URI
Copy the Redirect URI from the Terrakube UI
This is a private consumer (checkbox)
Checked
Permissions (checkboxes)
The following should be checked:
Account: Write
Repositories: Admin
Pull requests: Write
Webhooks: Read and write
You can complete the fields using the information suggested by terrakube in the VCS provider screen
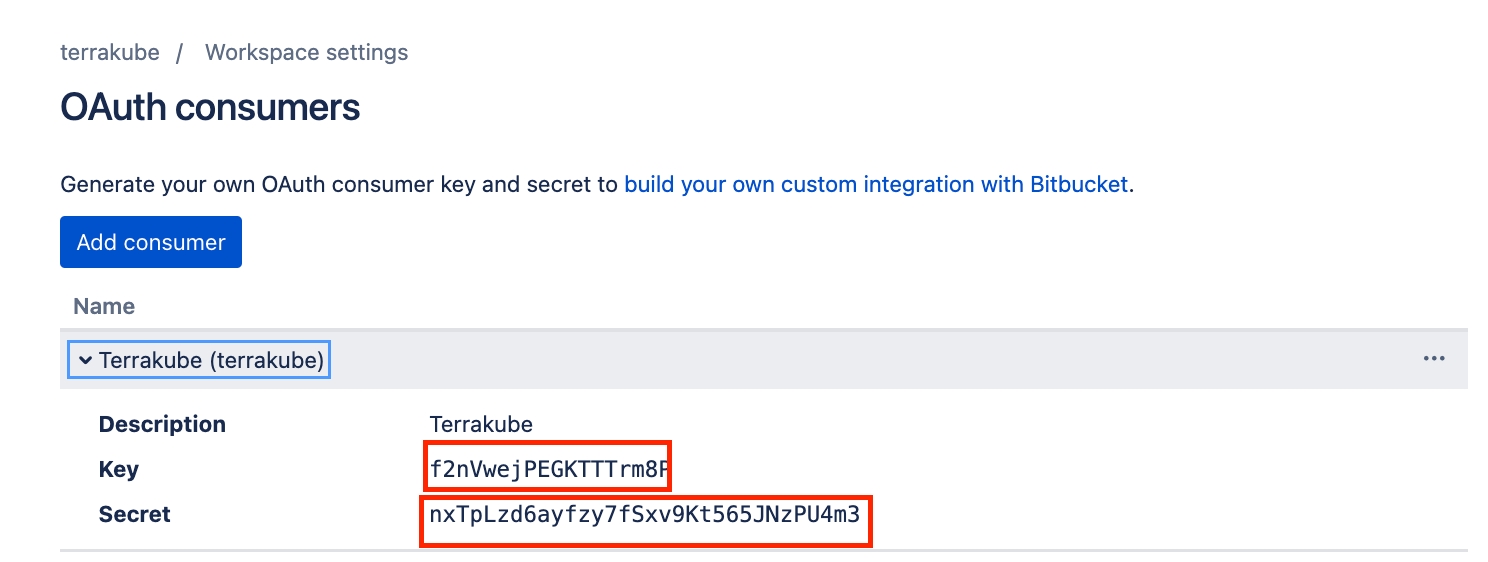
In the next screen, copy the Key and Secret
Go back to Terrakube to enter the information you copied from the previous step. Then, click the Connect and Continue button.
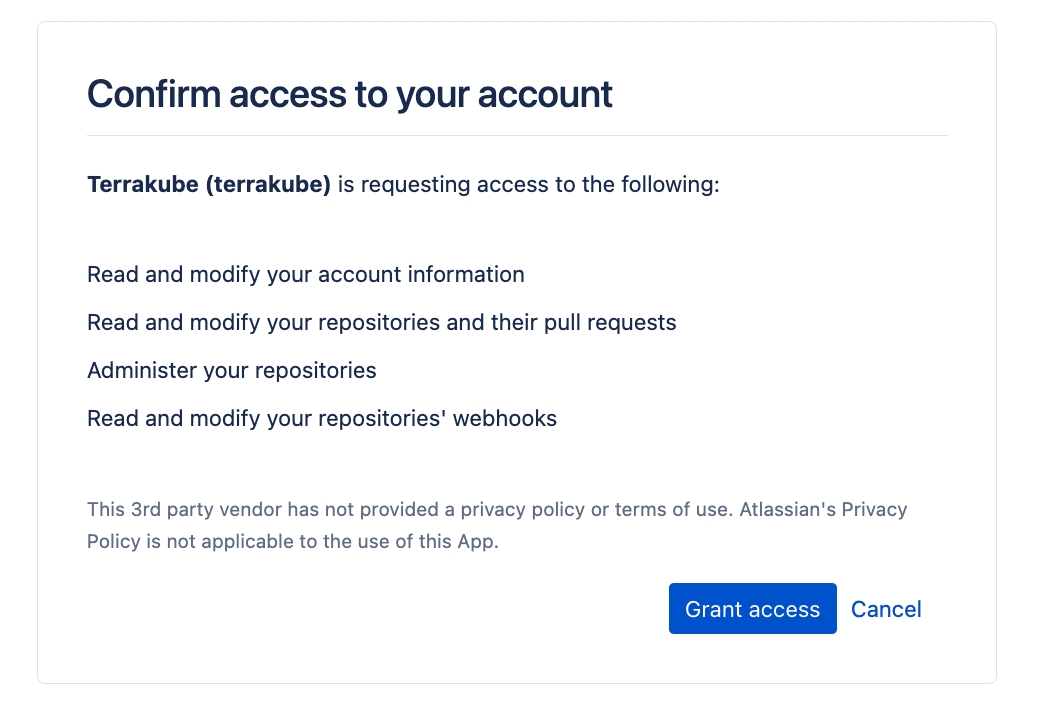
You will see a Bitbucket window, click the Grant Access button to complete the connection
Finally, if the connection was established successfully, you will be redirected to the VCS provider’s page in your organization. You should see the connection status with the date and the user that created the connection.
And now, you will be able to use the connection in your workspaces and modules:
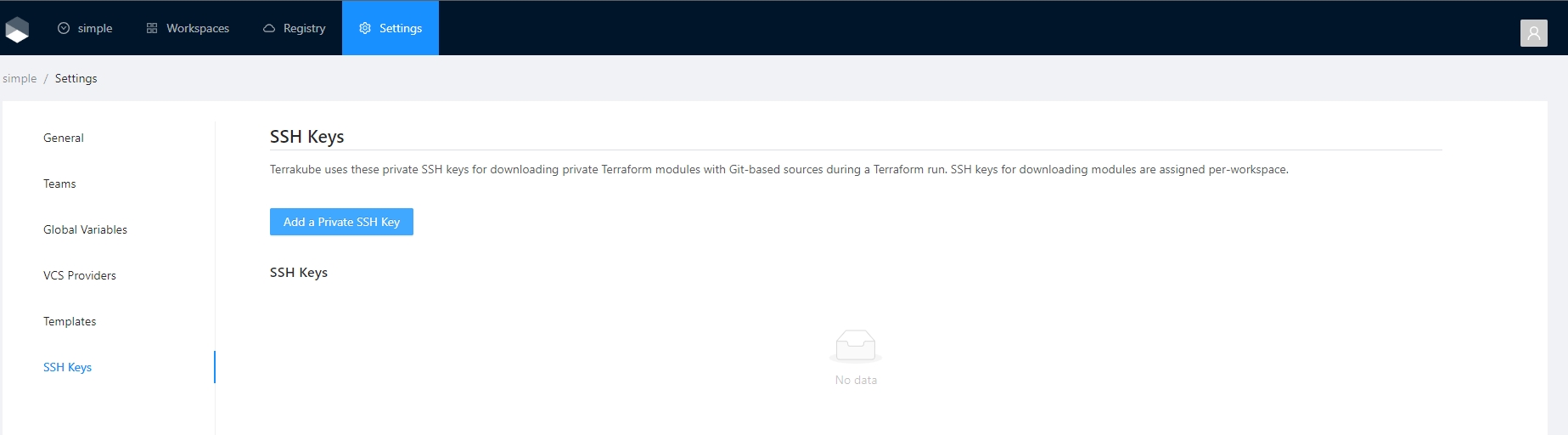
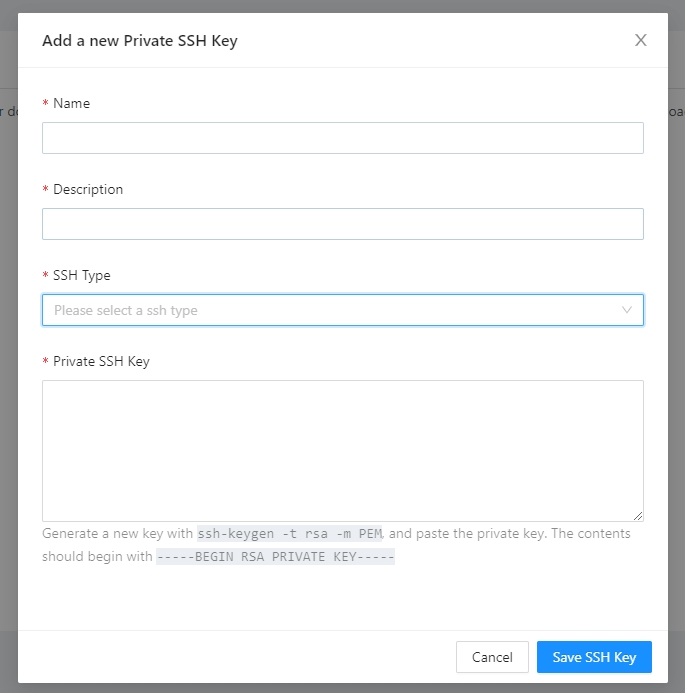
Terrakube can use SSH keys to authenticate to your private repositories. The SSH keys can be uploaded inside the settings menu.
To handle SSH keys inside Terrakube your team should have "Manage VCS settings" access
Terrakube support keys with RSA and ED25519
SSH keys can be used to authenticate to private repositories where you can store modules or workspaces
Once SSH keys are added inside your organization you can use them like the following example:
When using SSH keys make sure to use your repository URL using the ssh format. For github it is something like git@github.com:AzBuilder/terrakube-docker-compose.git
The selected SSH key will be used to clone the workspace information at runtime when running the job inside Terrakube, but it will also be injected to the job execution to be use inside our terraform code.
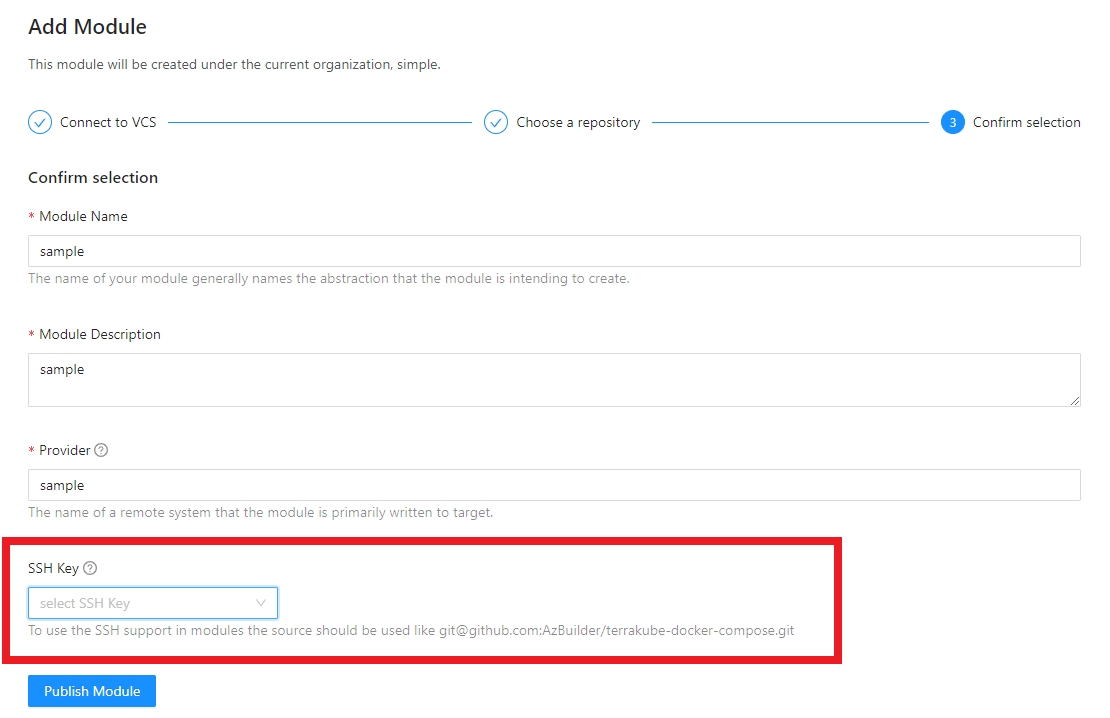
For example if you are using a module using a GIT connection like the following:
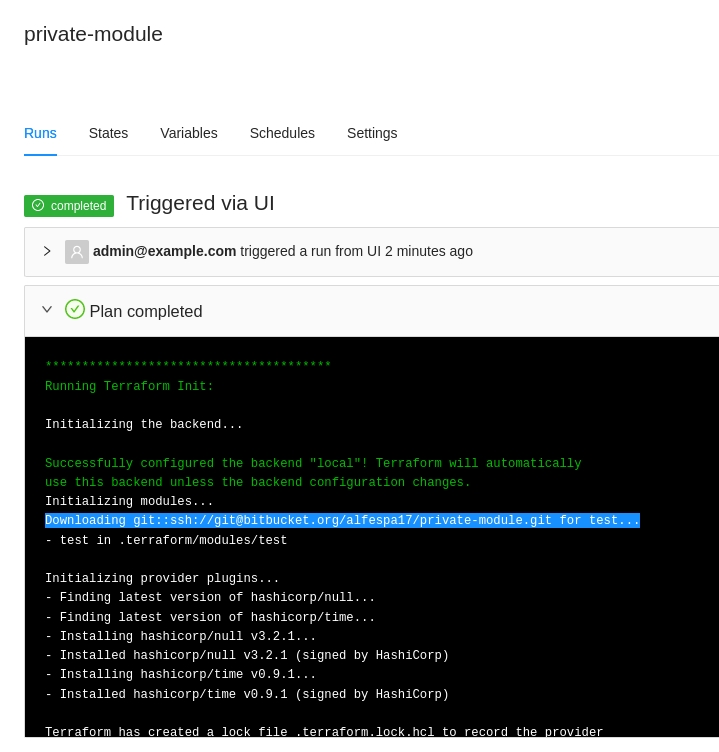
When running the job, internally terraform will be using the selected SSH key to clone the necesary module dependencies like the below image:
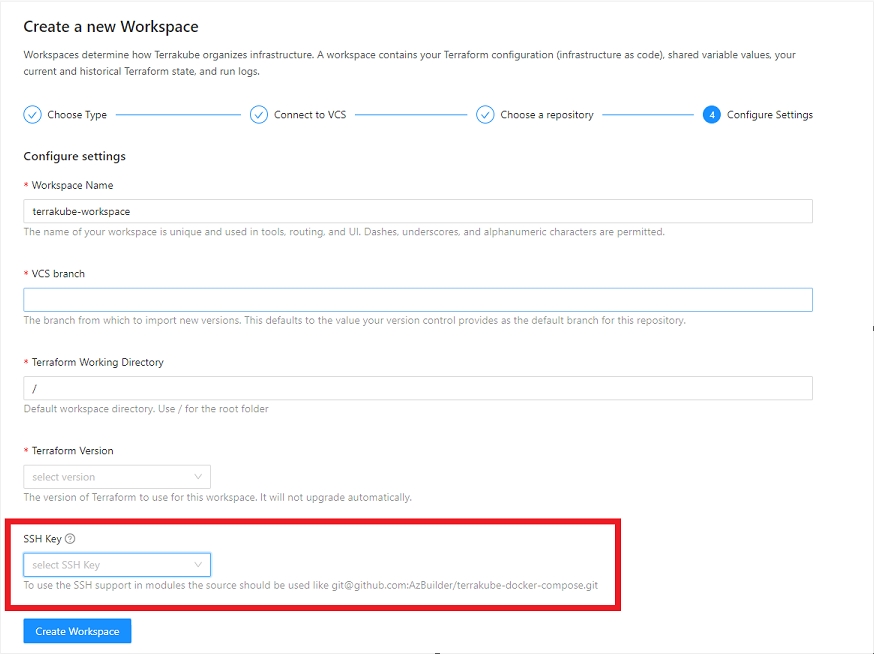
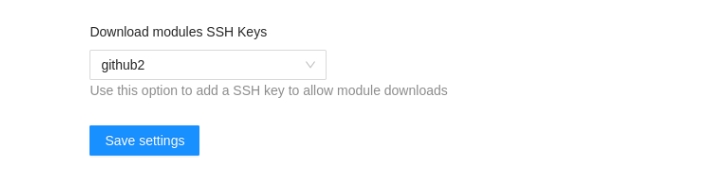
When using a VCS connection you can select wich SSH key should be injected when downloading modules in the workspace settings:
This will allow to use modules using the git format inside a workspace with VCS connection like the following:
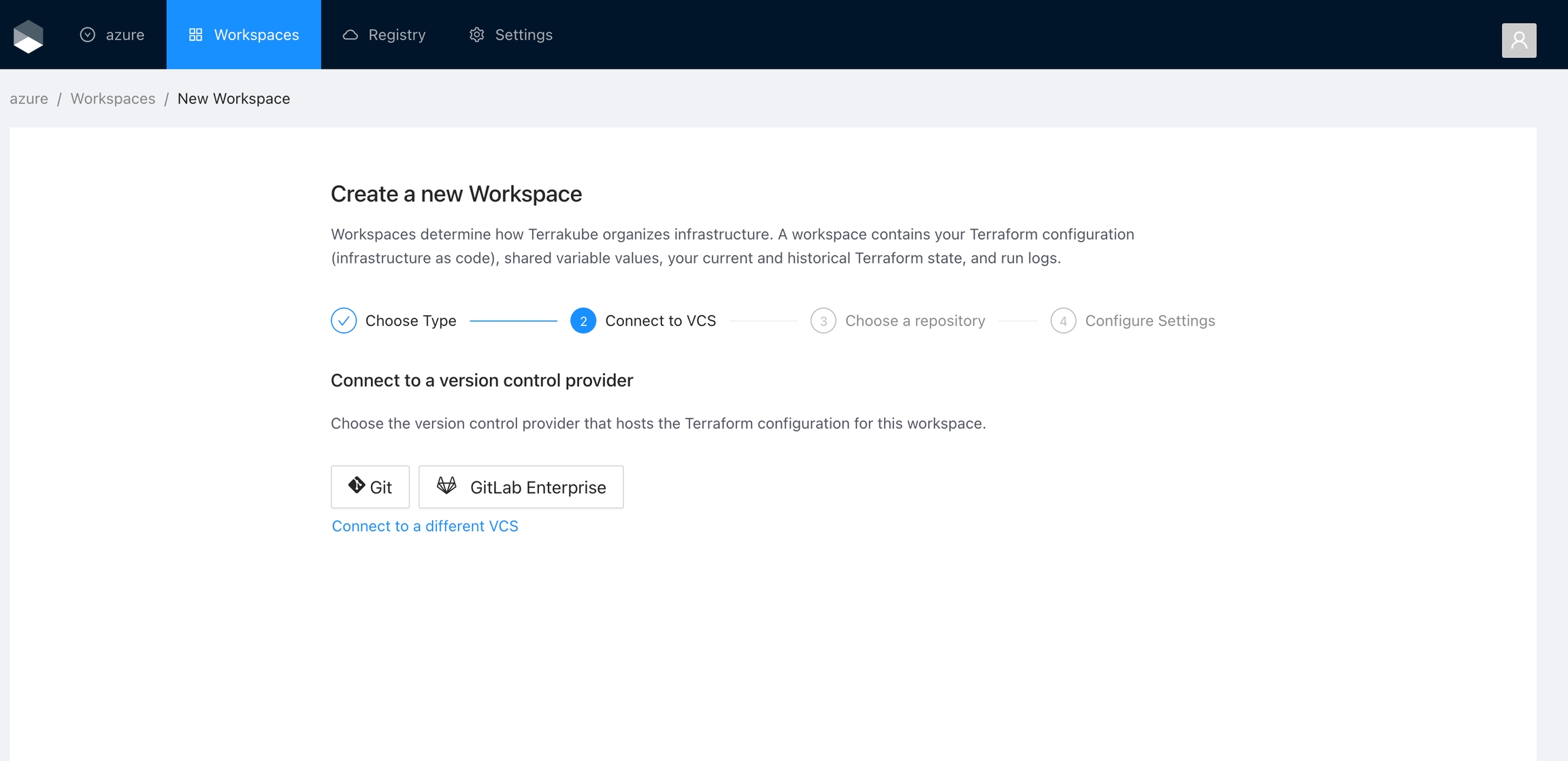
For using repositories from Azure Devops with Terrakube workspaces and modules you will need to follow these steps:
Manage VCS Providers permission is required to perform this action, please check Team Management for more info.
Navigate to the desired organization and click the Settings button, then on the left menu select VCS Providers
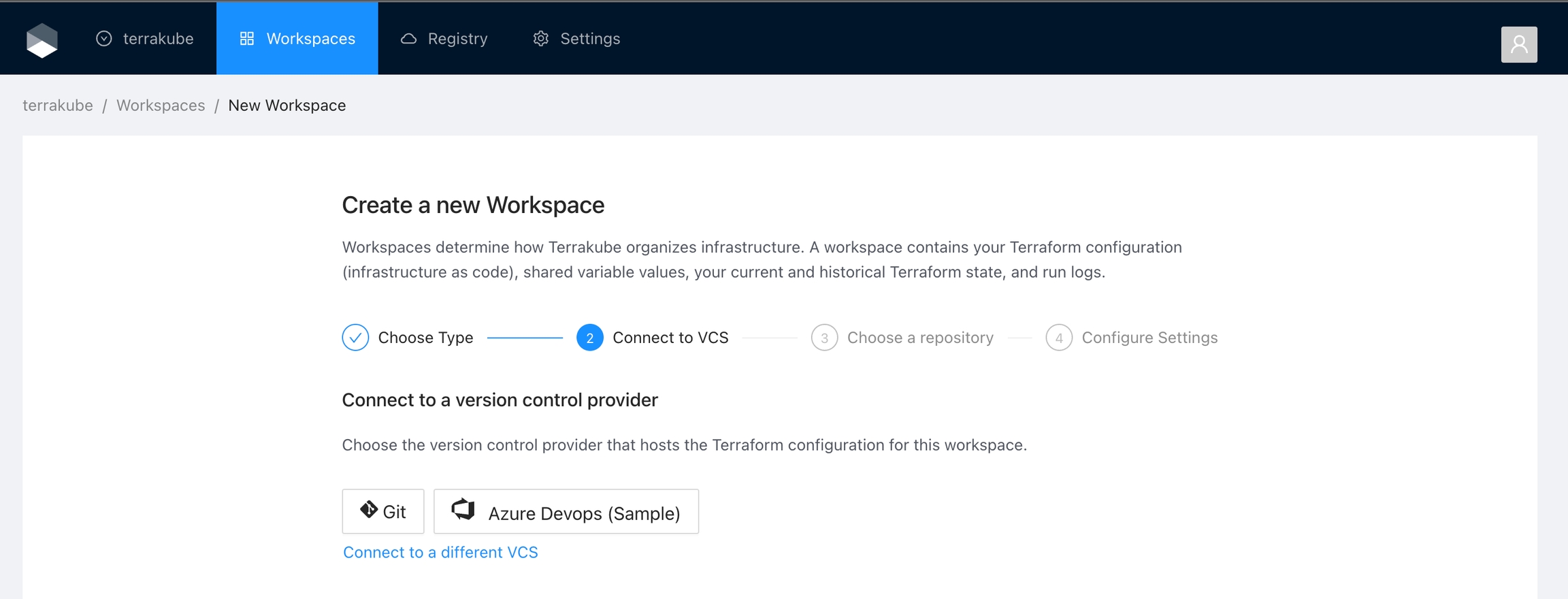
If you prefer, you can add a new VCS Provider directly from the Create workspace or Create Module screen.
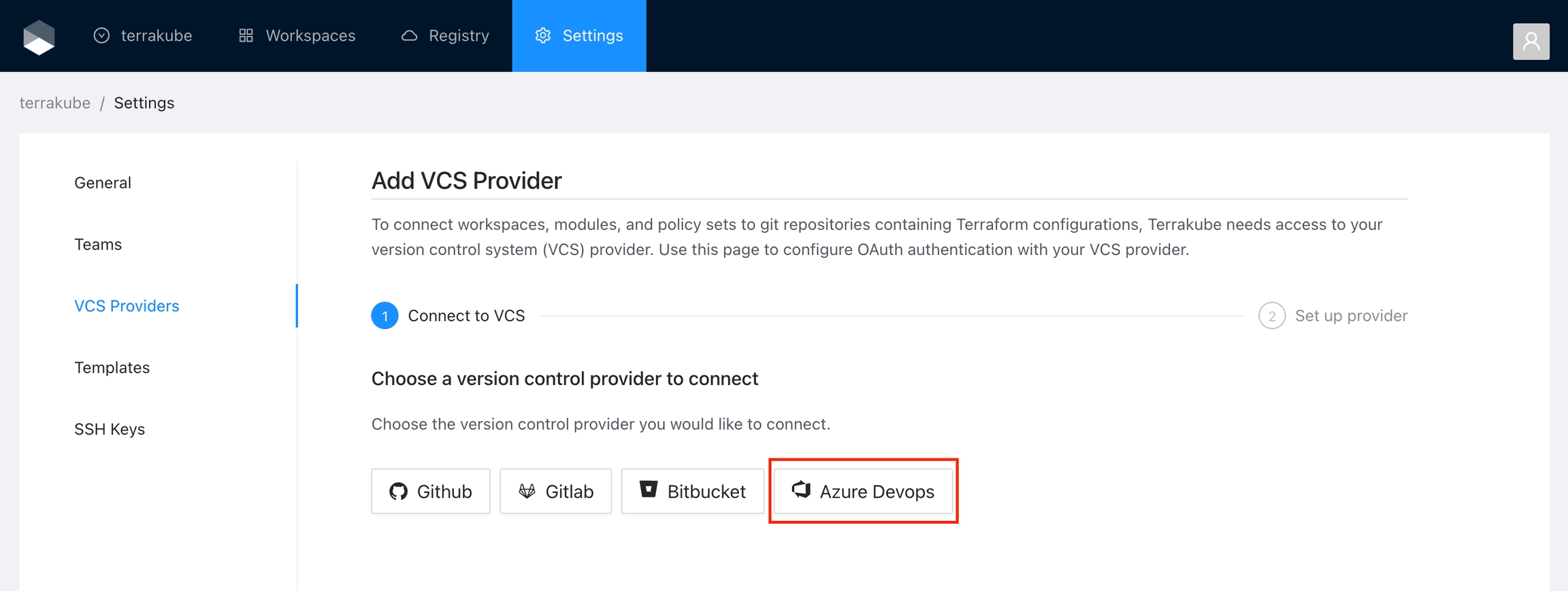
Click the Azure Devops button
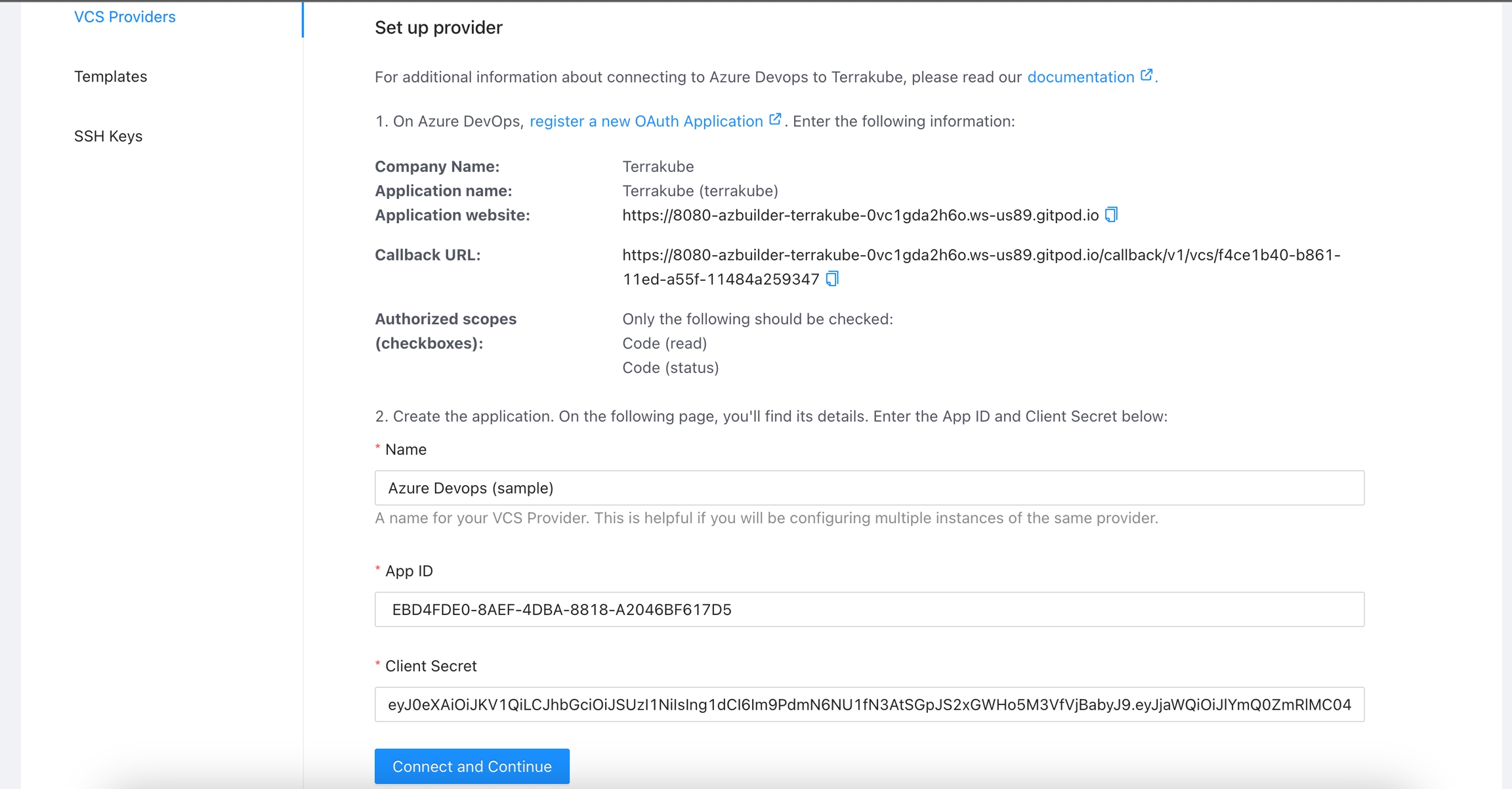
In the next screen click the link to register a new OAuth Application in Azure Devops
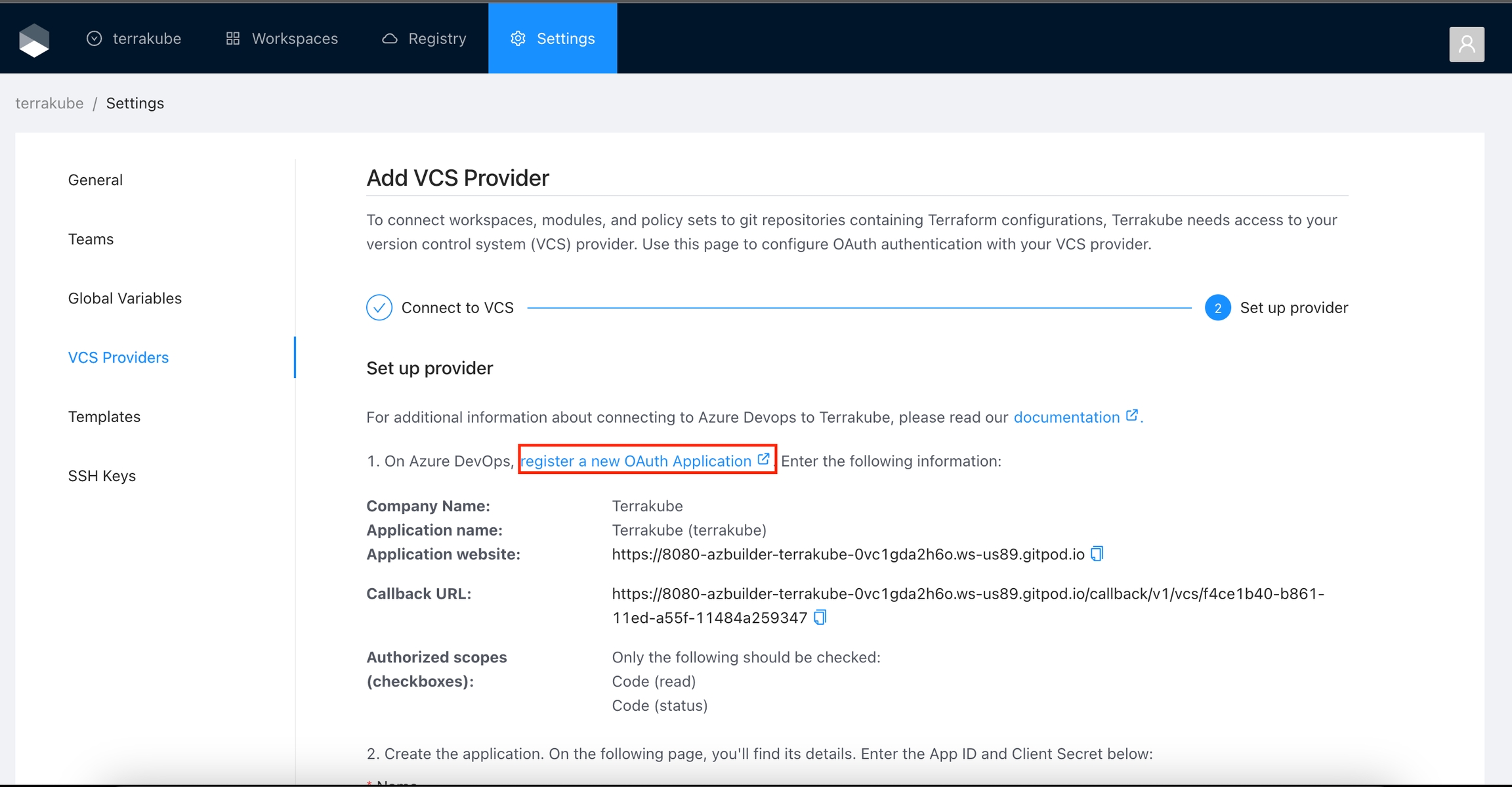
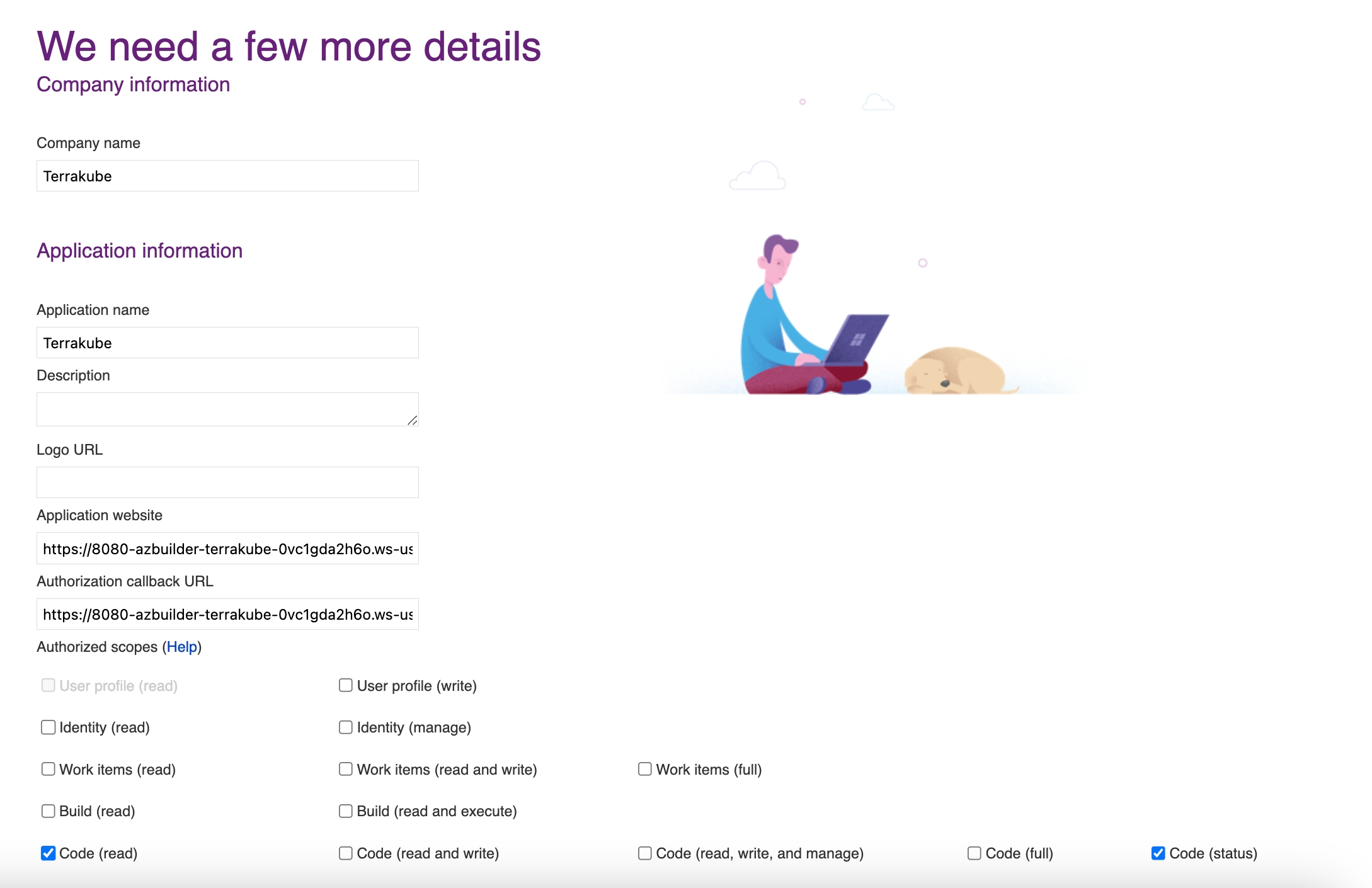
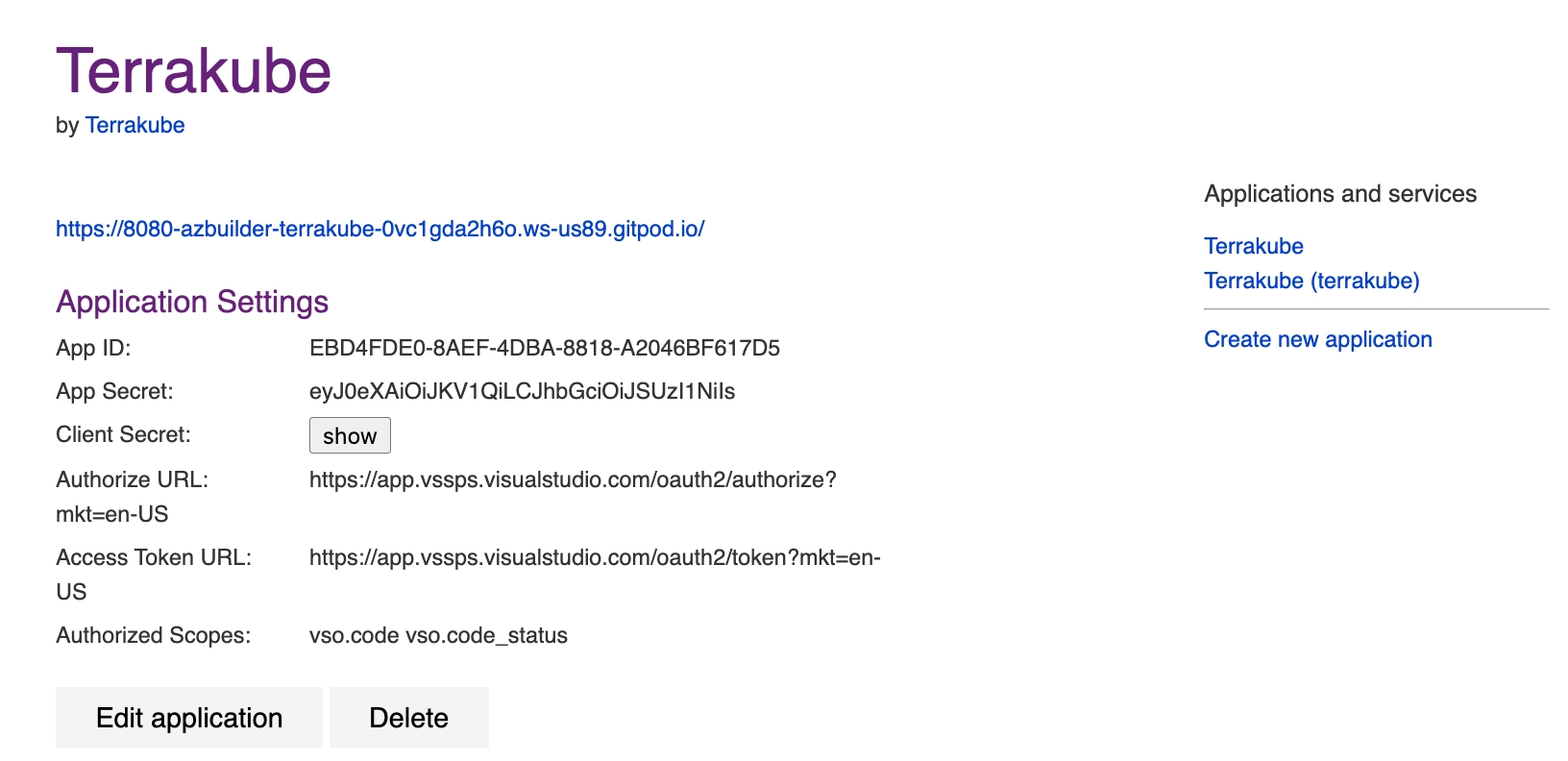
In the Azure Devops page, complete the required fields and click Create application
Company Name
Your company name.
Application name
The name of your application or you can use the Organization name
Application website
Your application or website url
Callback URL
Copy the Callback URL from the Terrakube URL
Authorized scopes (checkboxes)
Only the following should be checked: Code (read) Code (status)
You can complete the fields using the information suggested by terrakube in the VCS provider screen
In the next screen, copy the App ID and Client Secret
Go back to Terrakube to enter the information you copied from the previous step. Then, click the Connect and Continue button.
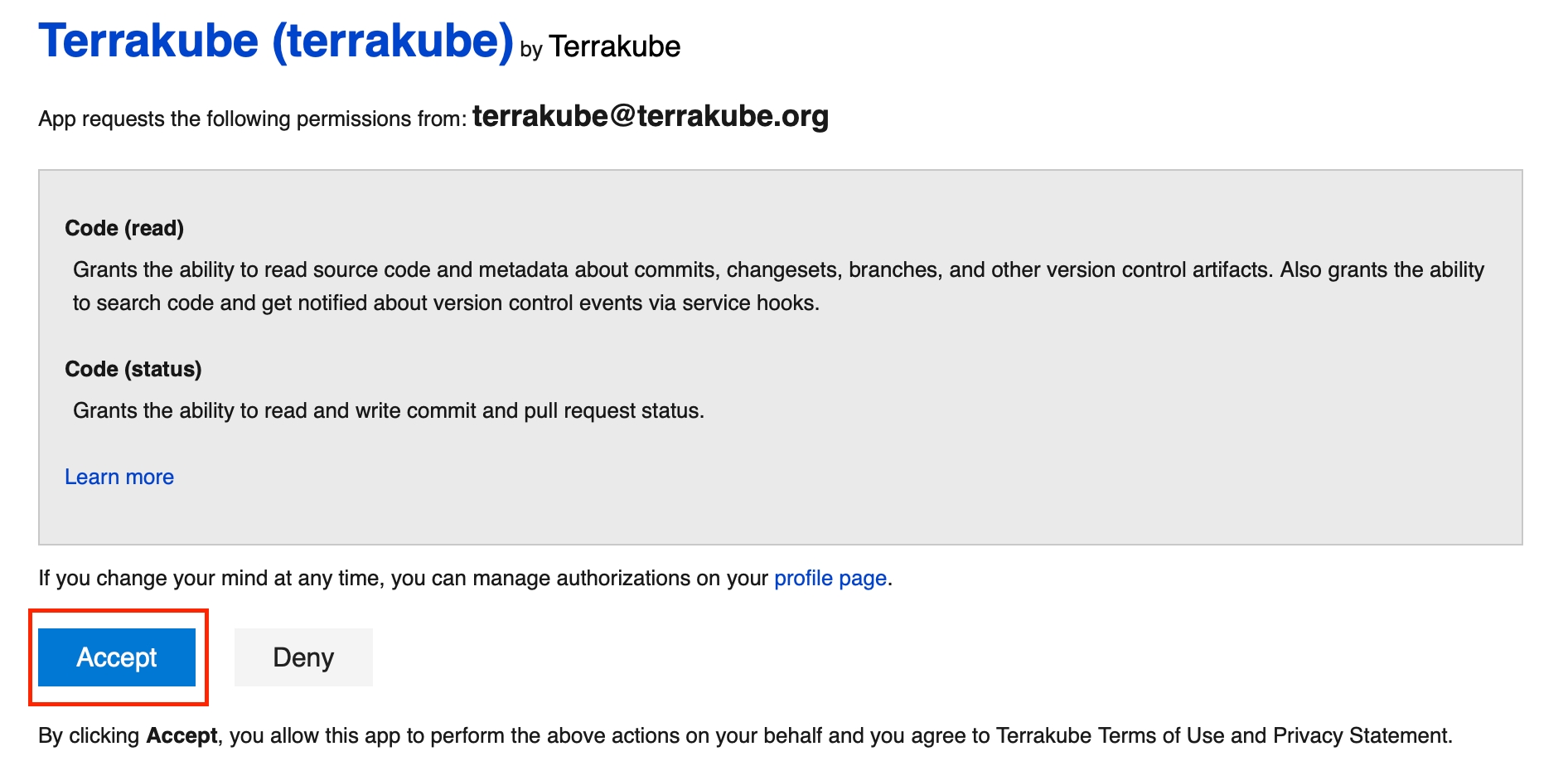
You will see an Azure Devops window, click the Accept button to complete the connection
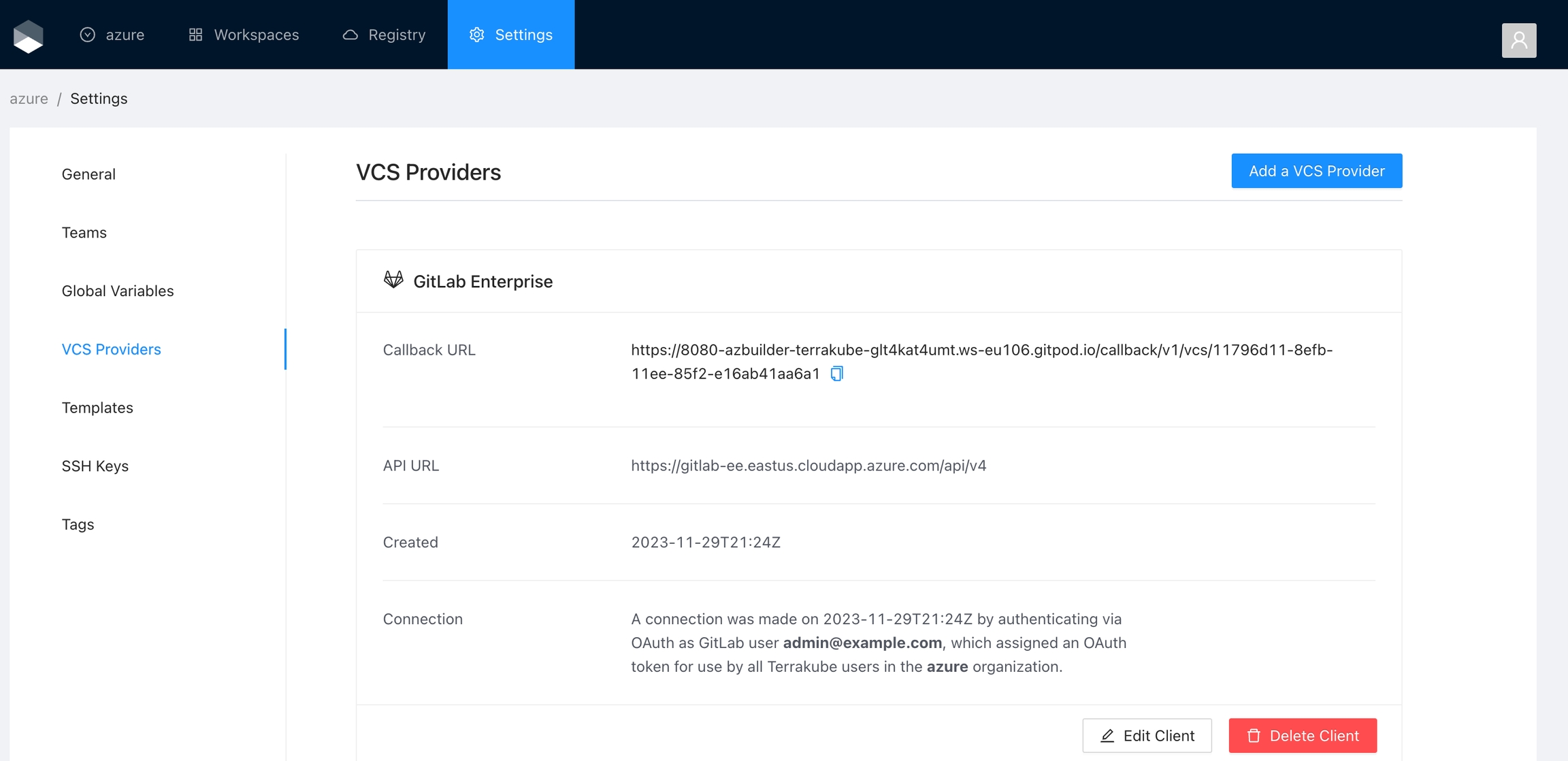
Finally, if the connection was established successfully, you will be redirected to the VCS provider’s page in your organization. You should see the connection status with the date and the user that created the connection.
And now, you will be able to use the connection in your workspaces and modules:
Terrakube empowers collaboration between different teams in your organization. To achieve this, you can integrate Terrakube with your version control system (VCS) provider. Although Terrakube can be used with public Git repositories or with private Git repositories using SSH, connecting to your Terraform code through a VCS provider is the preferred method. This allows for a more streamlined and secure workflow, as well as easier management of access control and permissions.
Terrakube supports the following VCS providers:
Terrakube uses webhooks to monitor new commits. This features is not available in SSH and Azure DevOps.
When new commits are added to a branch, Terrakube workspaces based on that branch will automatically initiate a Terraform job. Terrakube will use the "Plan and apply" template by default, but you can specify a different Template during the Workspace creation.
When you specify a directory in the Workspace. Terrakube will run the job only if a file changes in that directory
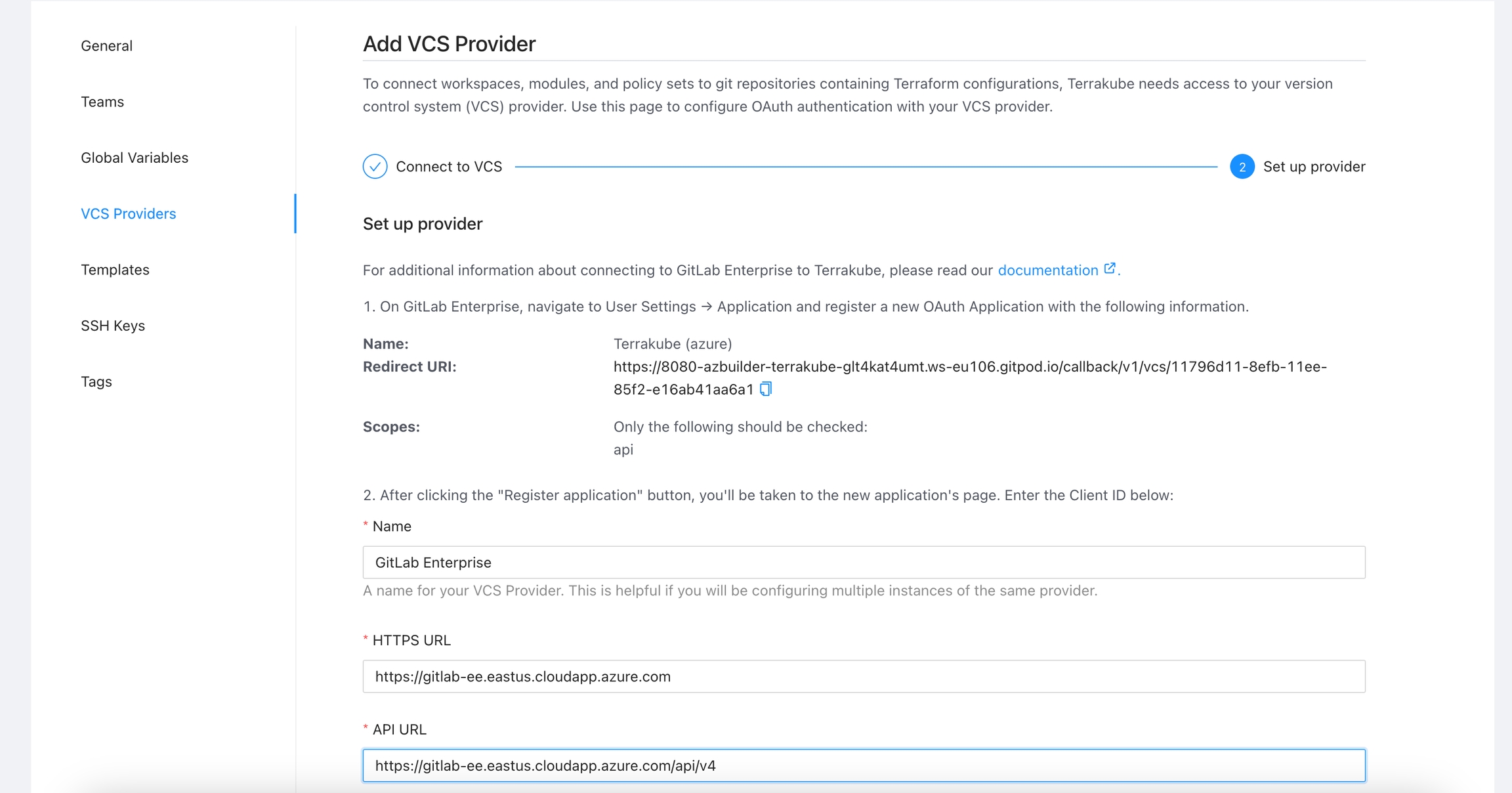
To use Terrakube’s VCS features with a self-hosted GitLab Enterprise Edition (EE) or GitLab Community Edition (CE), follow these instructions. For GitLab.com, .
Manage VCS Providers permission is required to perform this action, please check for more info.
Got to the organization settings you want to configure. Select the VCS Providers on the left menu and click the Add VCS provider button on the top right corner.
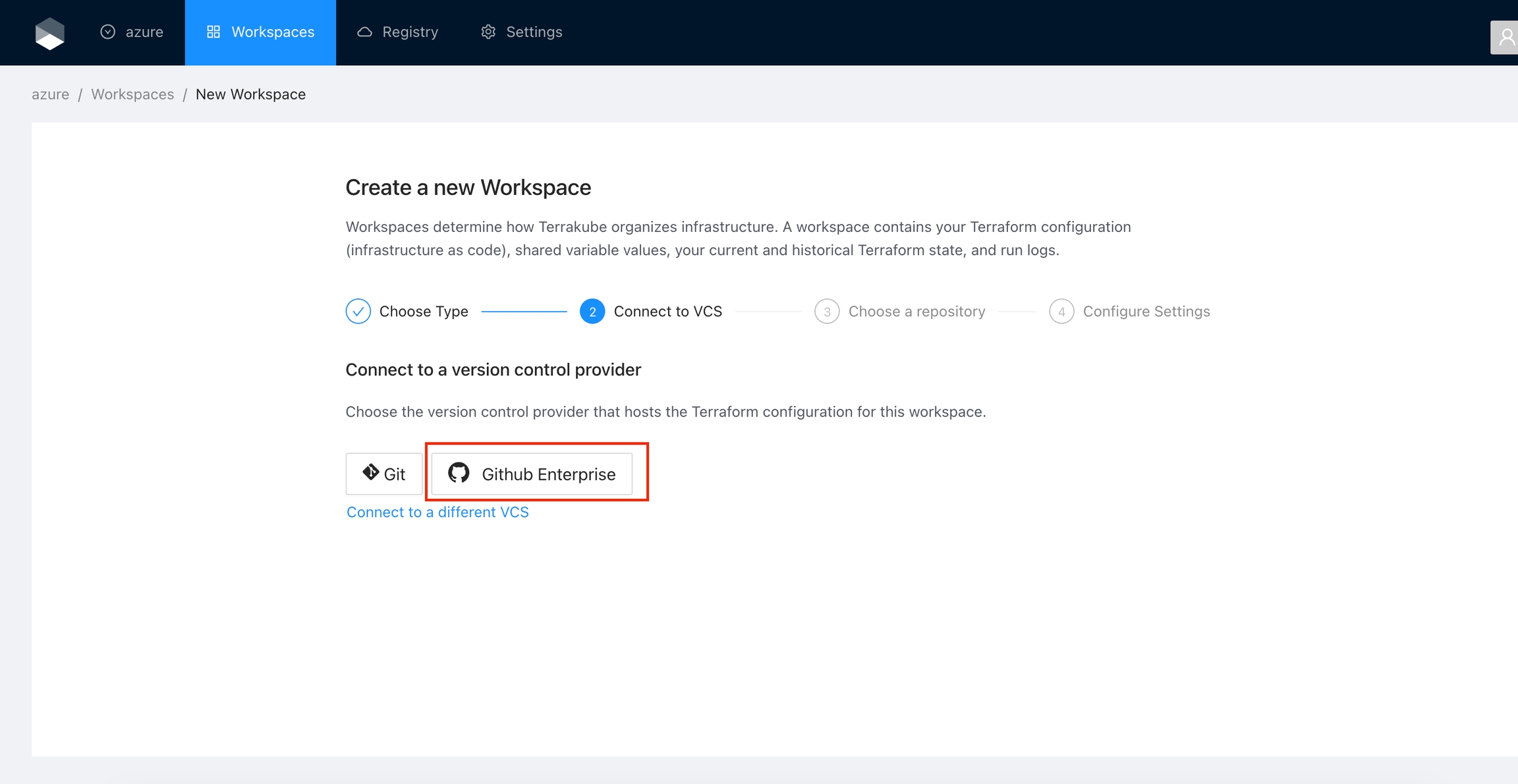
Click the Gitlab button and then click the GitLab Enterprise option.
On the next screen, enter the following information about your GitLab instance:
Use a different browser tab to access your GitLab instance and sign in with the account that you want Terrakube to use. You should use a service user account for your organization, but you can also use a personal account.
Note: To connect Terrakube, you need an account with admin (master) access to any shared repositories of Terraform configurations. This is because creating webhooks requires admin permissions. Make sure you create the application as a user-owned application, not as an administrative application. Terrakube needs user access to repositories to create webhooks and ingress configurations.
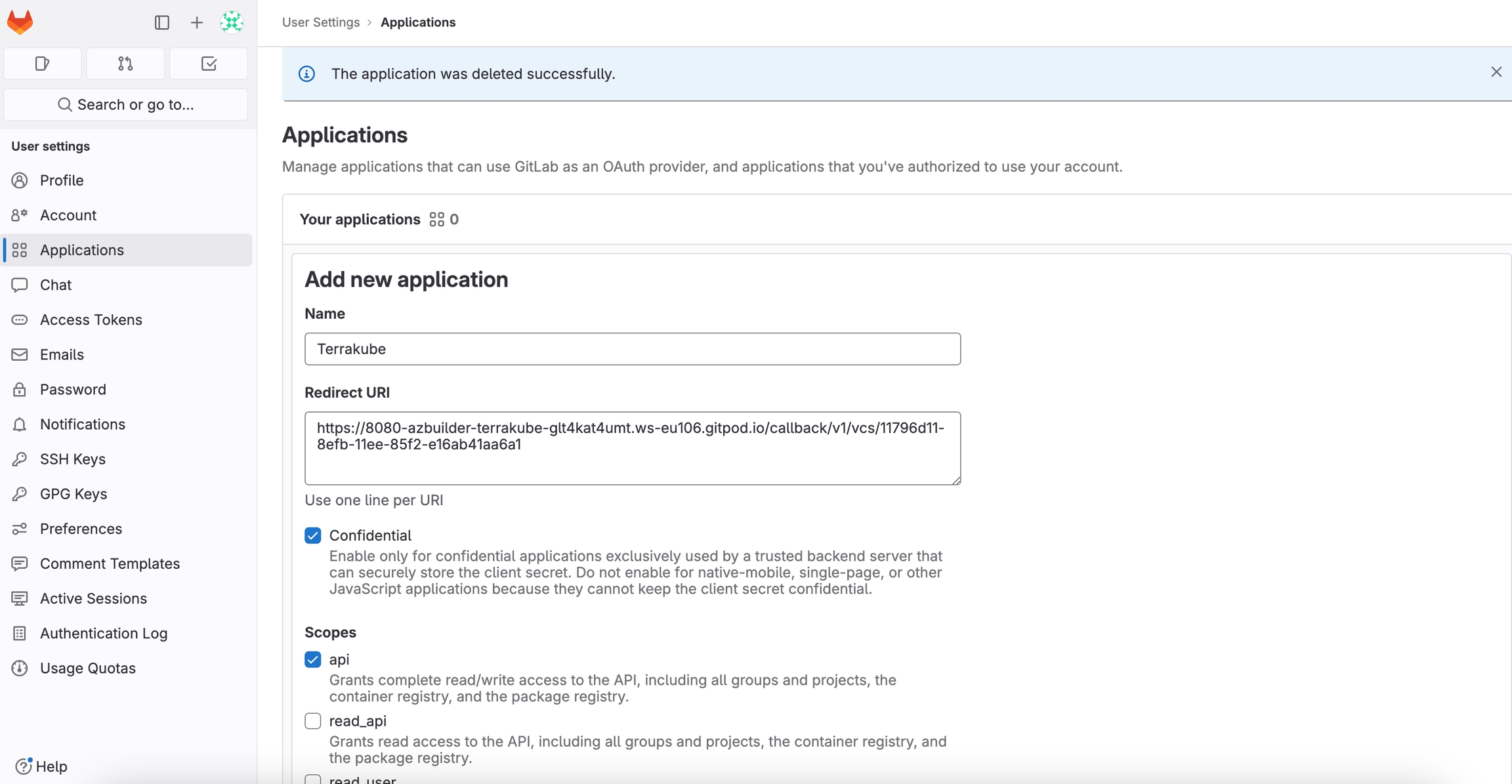
Navigate to GitLab "User Settings > Applications" page. This page is located at https://<GITLAB INSTANCE HOSTNAME>/profile/applications
In the GitLab page, complete the required fields and click Save application
You can complete the fields using the information suggested by terrakube in the VCS provider screen
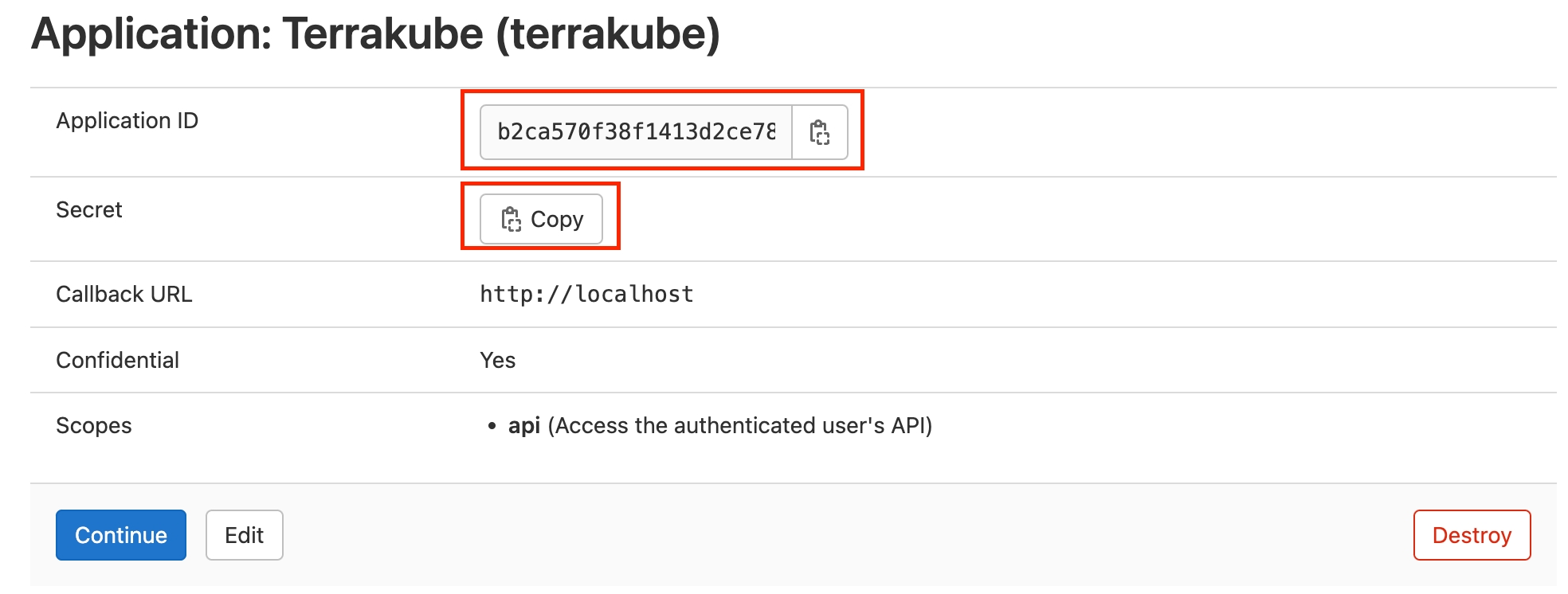
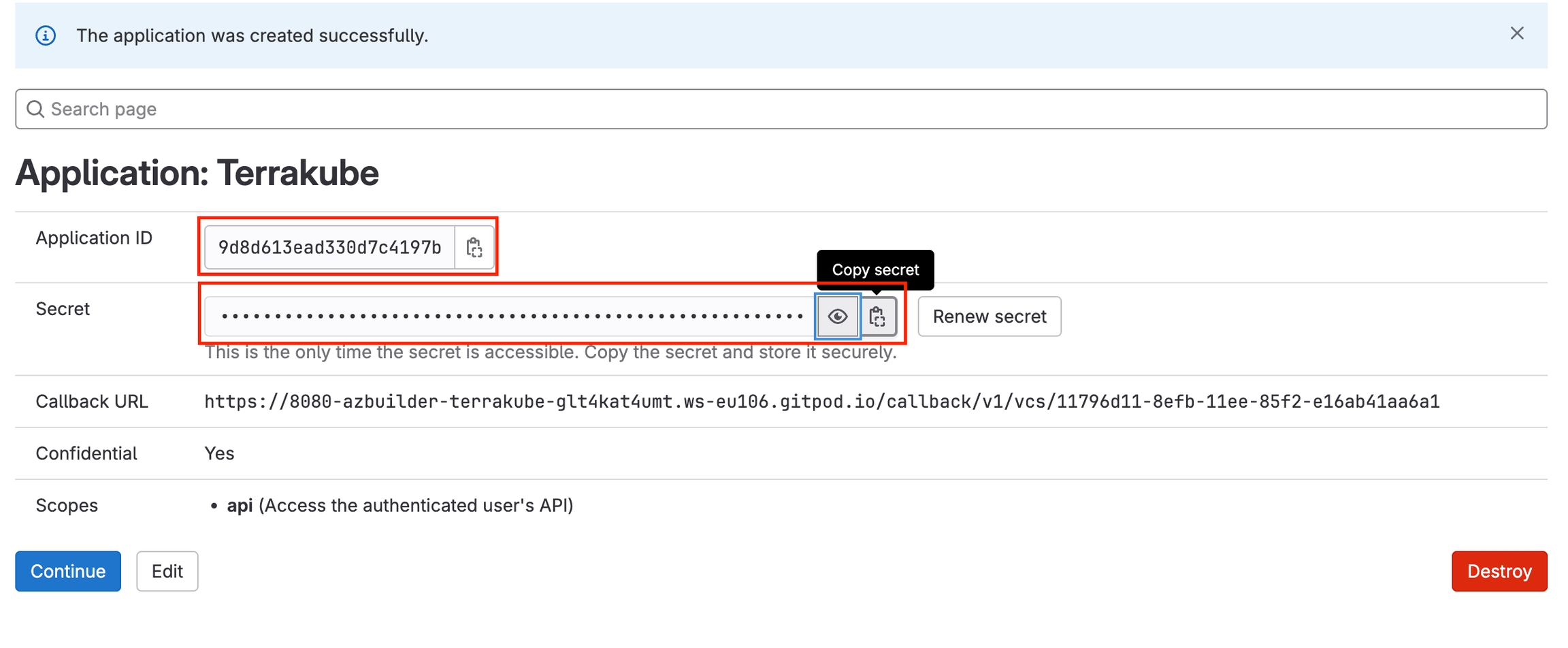
On the next screen, copy the Application ID and Secret
Go back to Terrakube to enter the information you copied from the previous step. Then, click the Connect and Continue button.
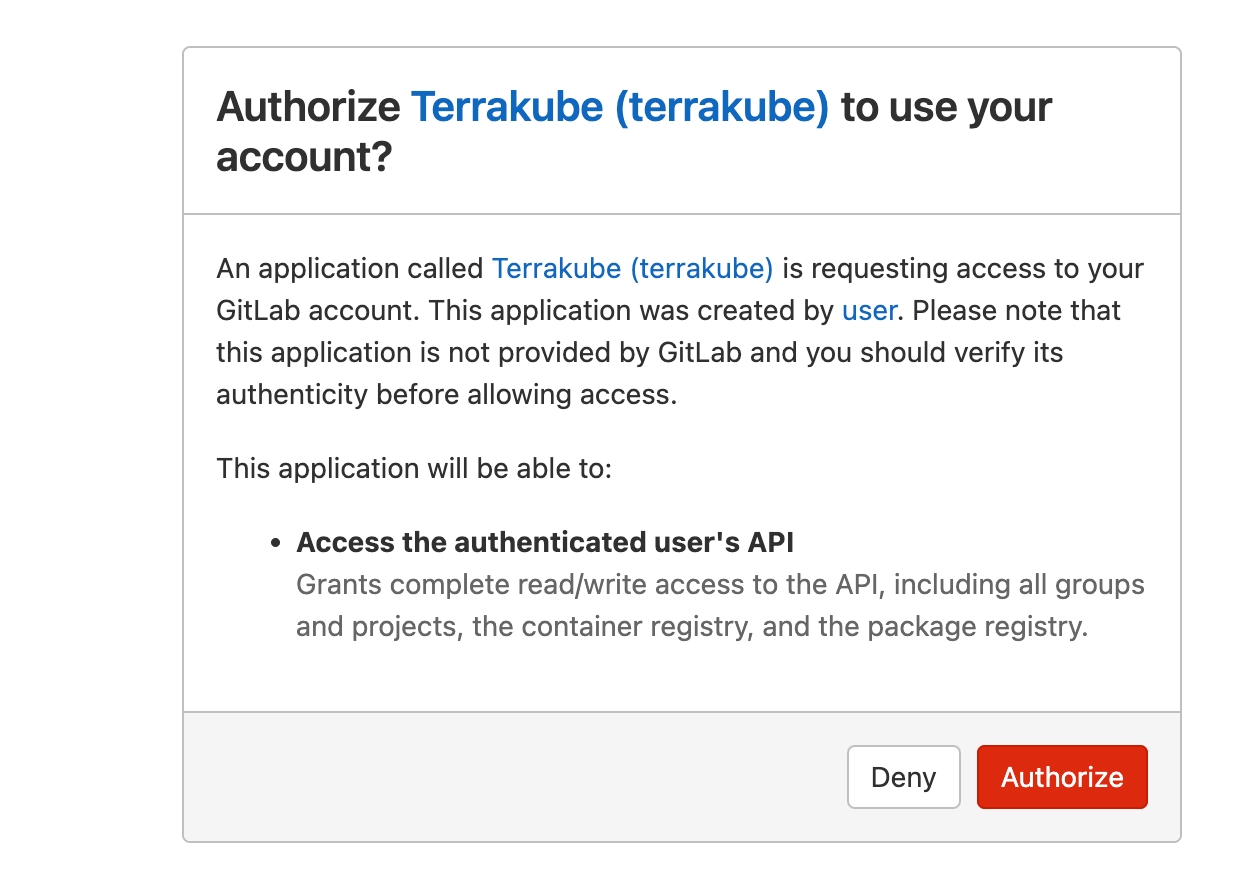
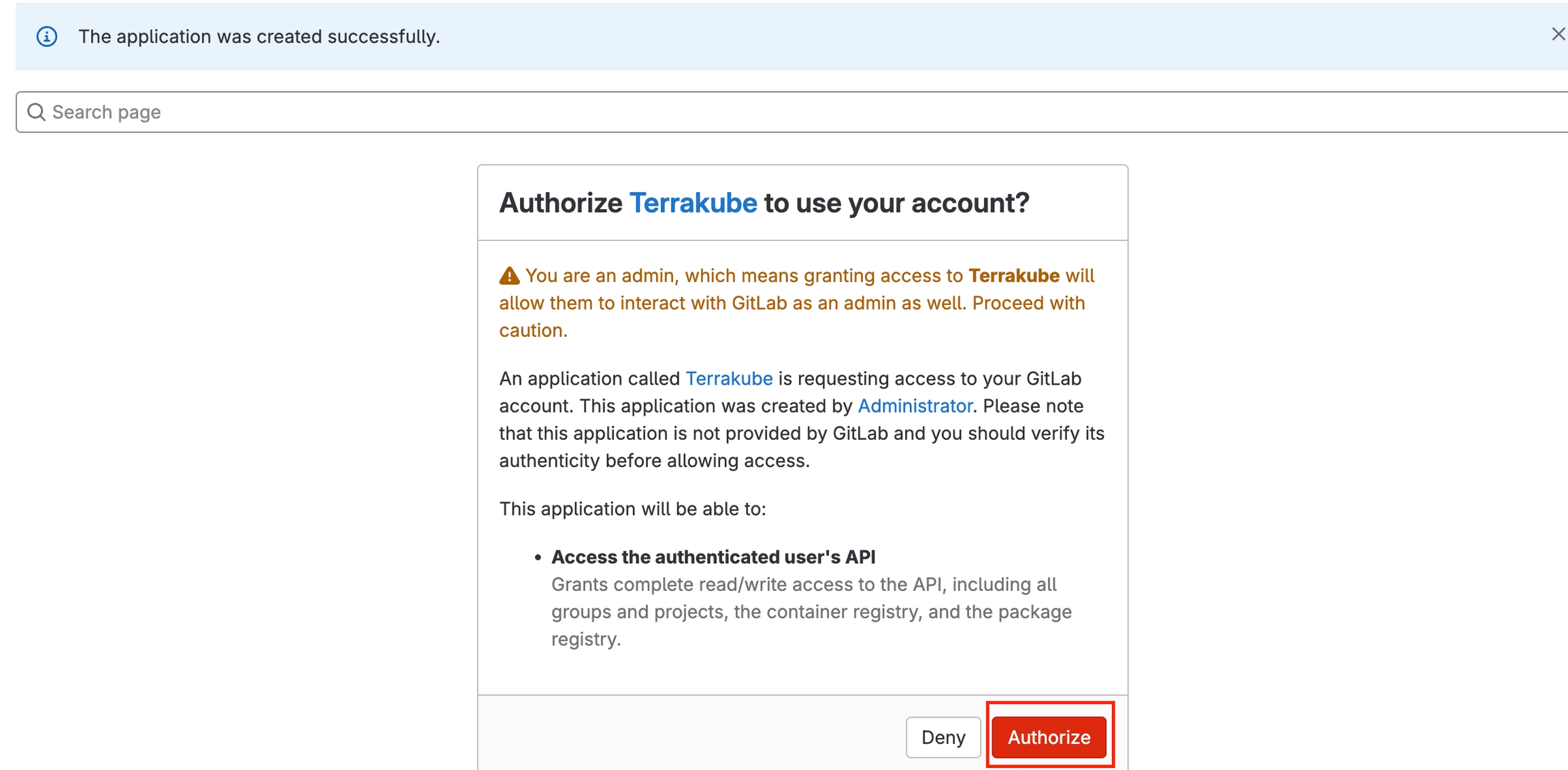
You will be redirected to GitLab. Click the Authorize button to complete the connection.
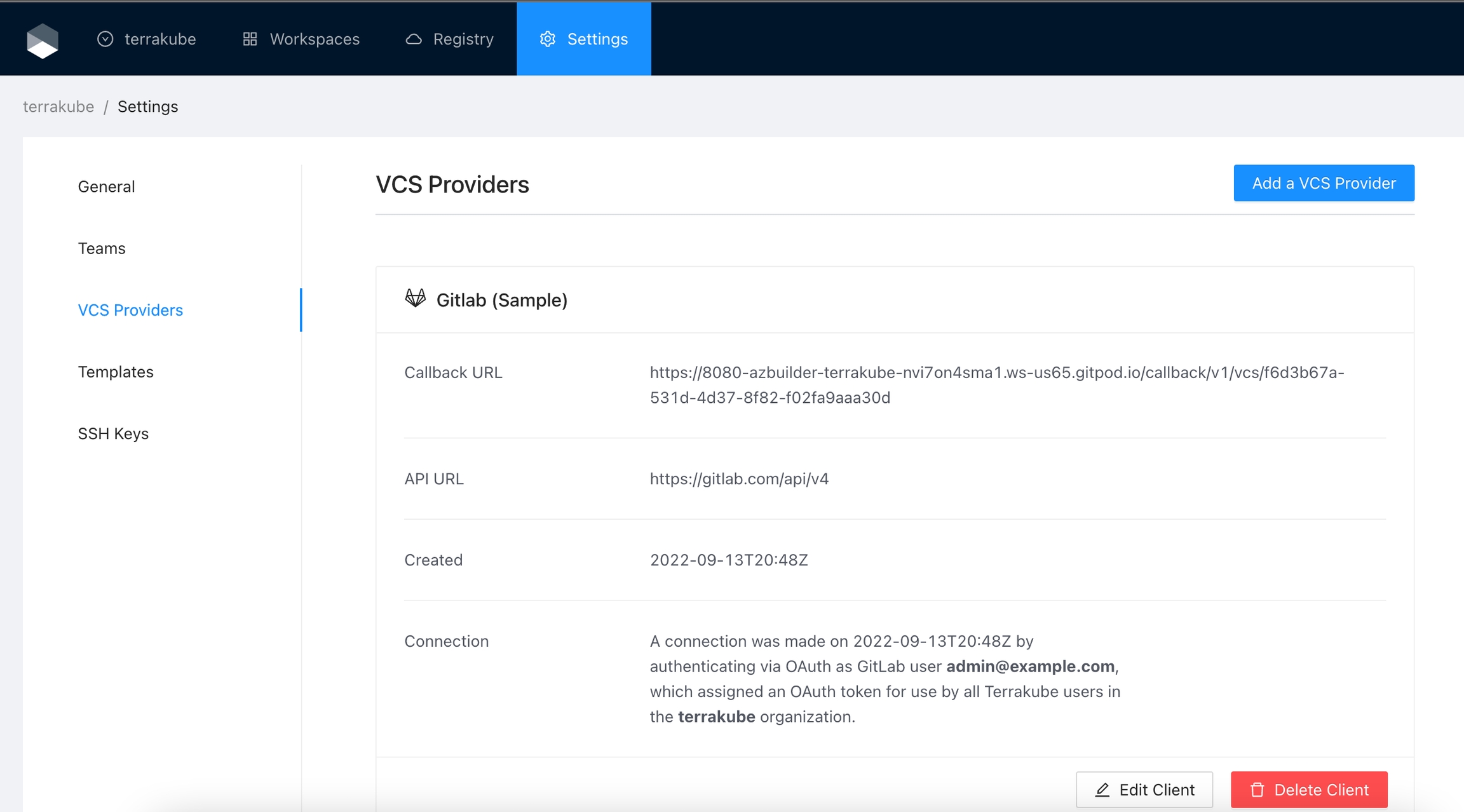
Finally, if the connection was established successfully, you will be redirected to the VCS provider’s page in your organization. You should see the connection status with the date and the user that created the connection.
And now, you will be able to use the connection in your workspaces and modules:
If you prefer, you can add a new VCS Provider directly from the or Create Module screen.
If you have GitLab CE or EE 10.6 or higher, you might also need to turn on Allow requests to the local network from hooks and services. You can find this option in the Admin area under Settings, in the “Outbound requests” section (/admin/application_settings/network). For more details, see the .
HTTP URL
https://<GITLAB INSTANCE HOSTNAME>
API URL
https://<GITLAB INSTANCE HOSTNAME>/api/v4
Name
Your application name, for example you can use your organization name.
Redirect URI
Copy the Redirect URI from the UI
Scopes
Only api should be checked
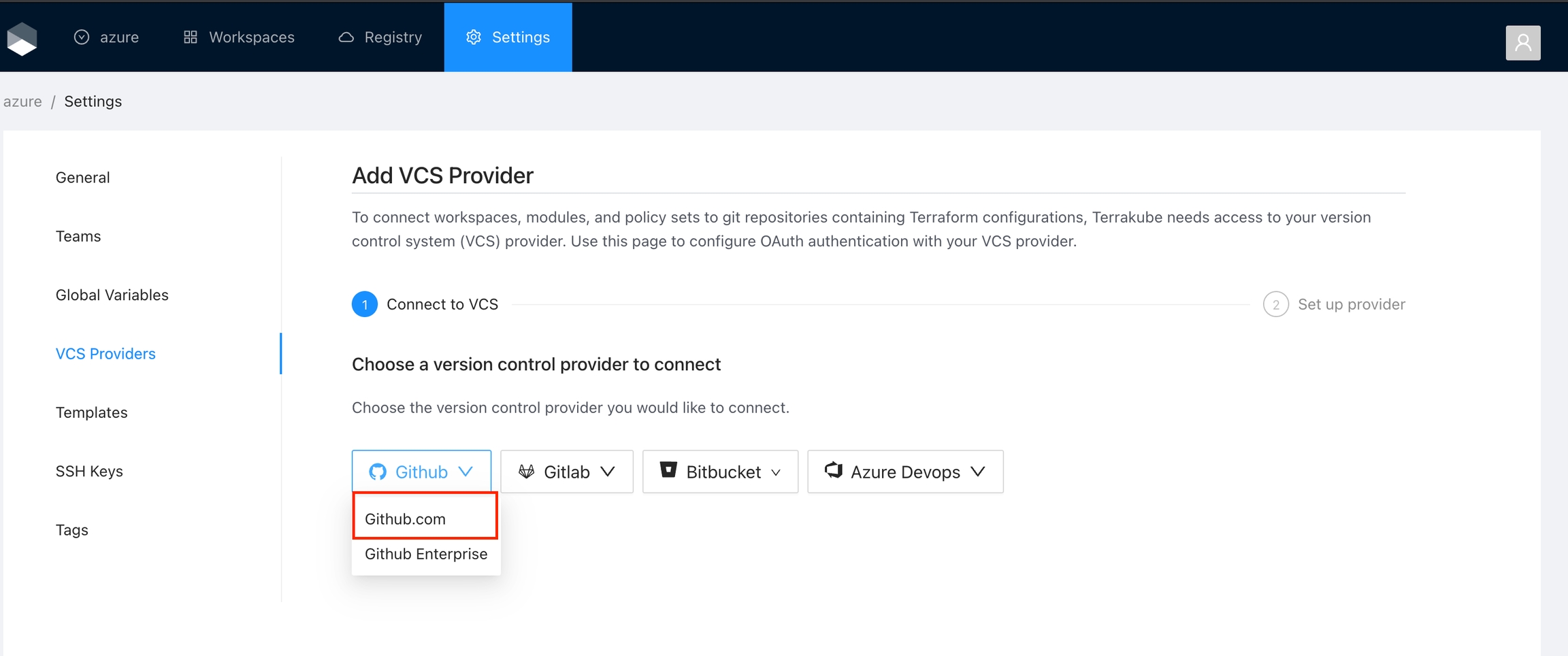
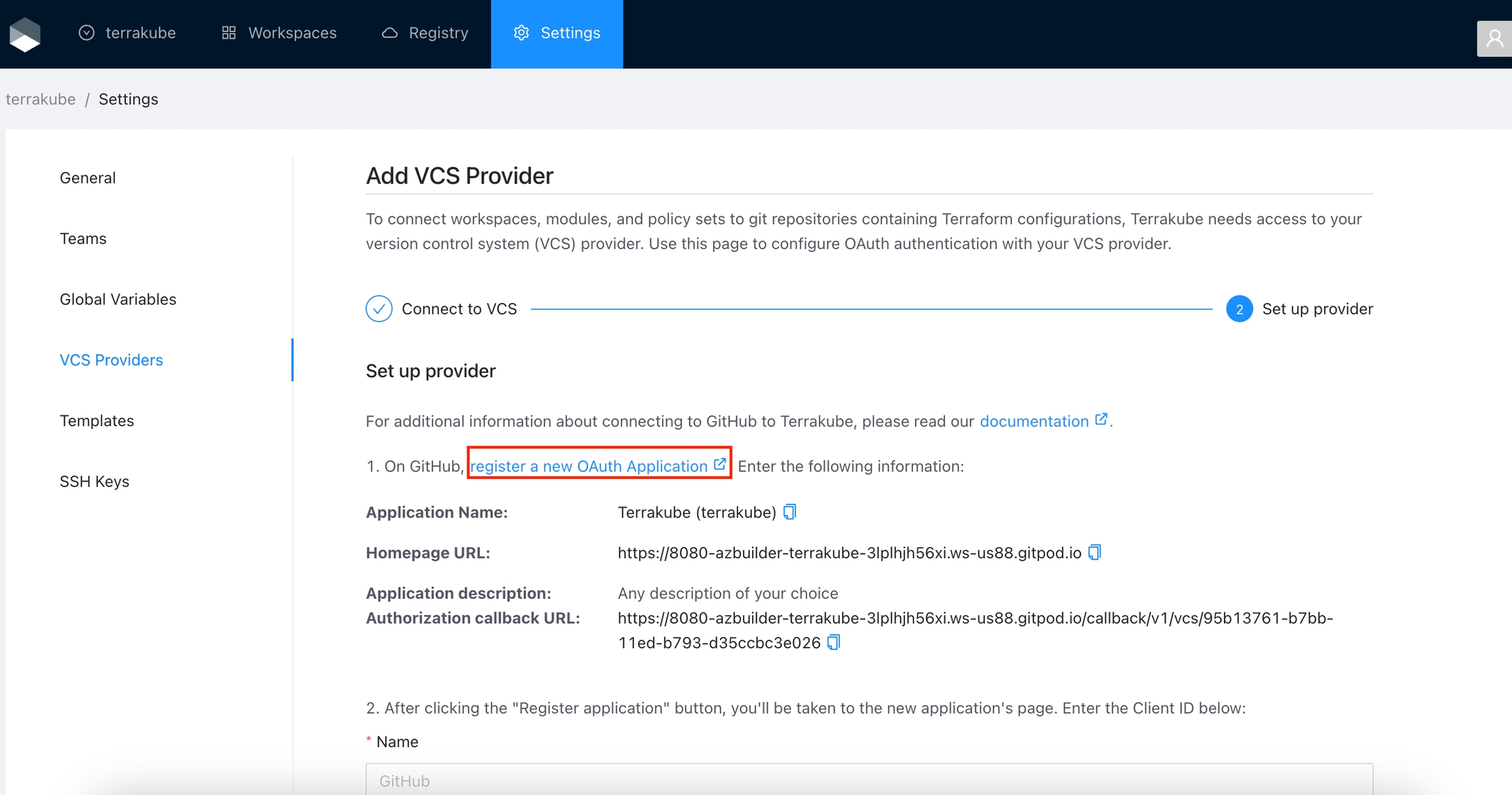
For using repositories from GitHub.com with Terrakube workspaces and modules you will need to follow these steps:
Manage VCS Providers permission is required to perform this action, please check Team Management for more info.
Navigate to the desired organization and click the Settings button, then on the left menu select VCS Providers
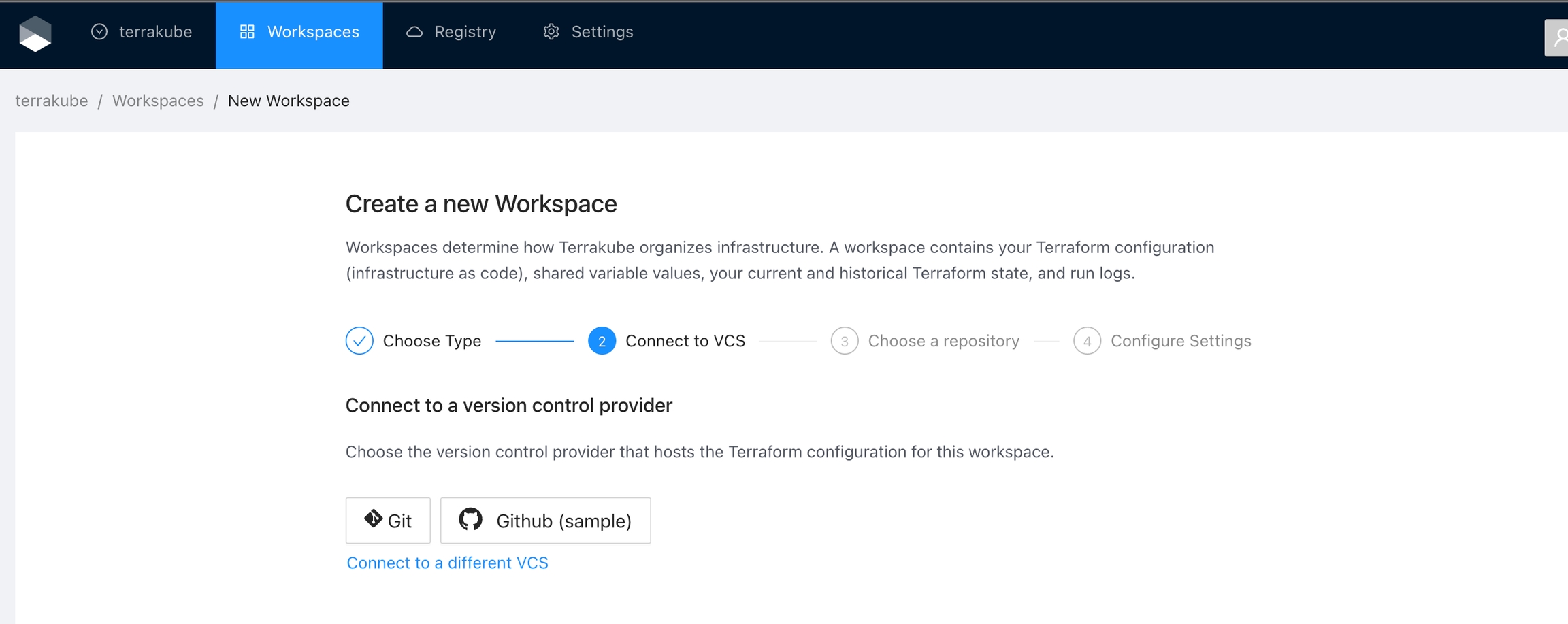
If you prefer, you can add a new VCS Provider directly from the Create workspace or Create Module screen.
Click the Github button and then click the Github Cloud option.
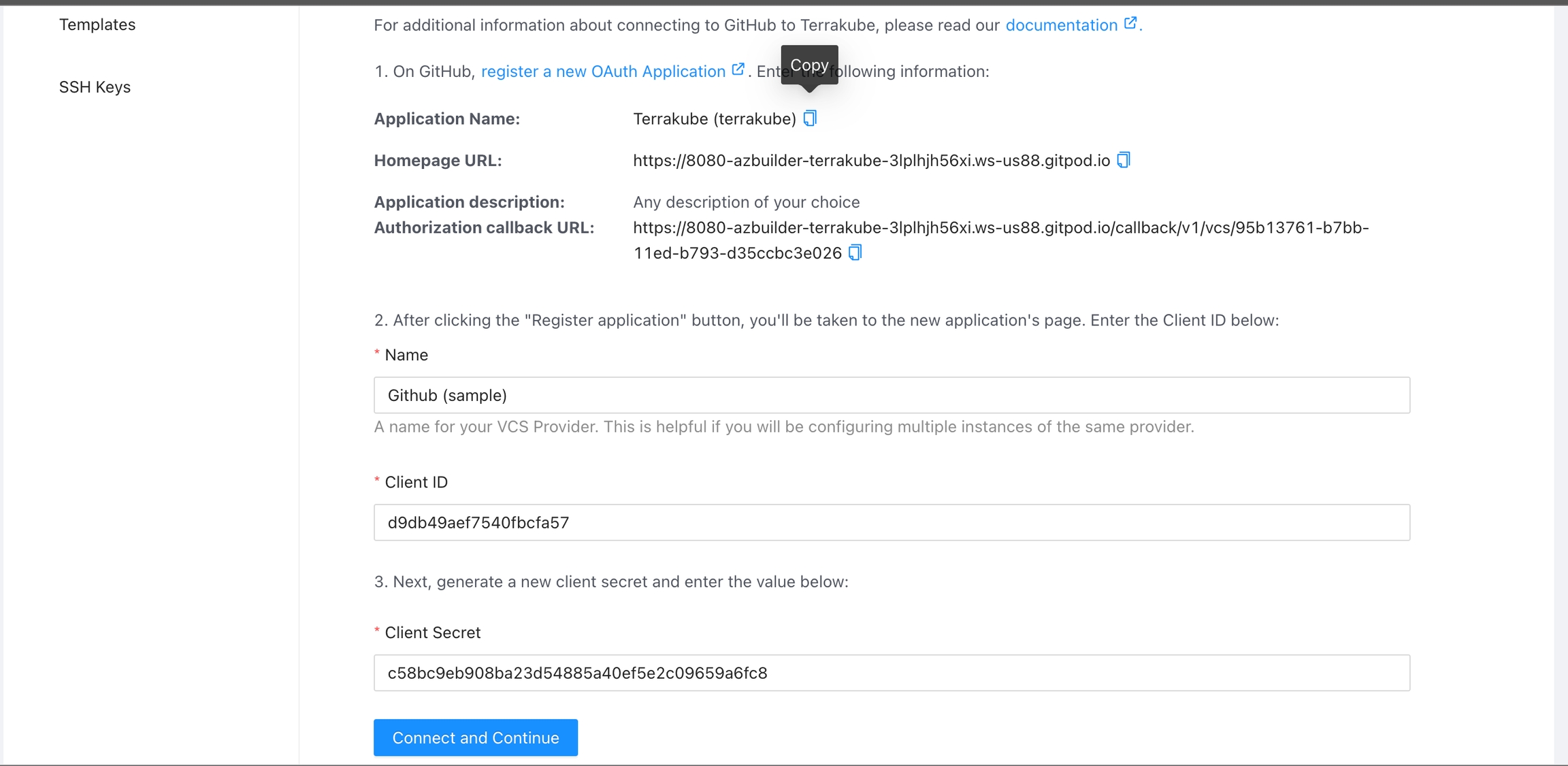
In the next screen click the link to register a new OAuth Application in Github
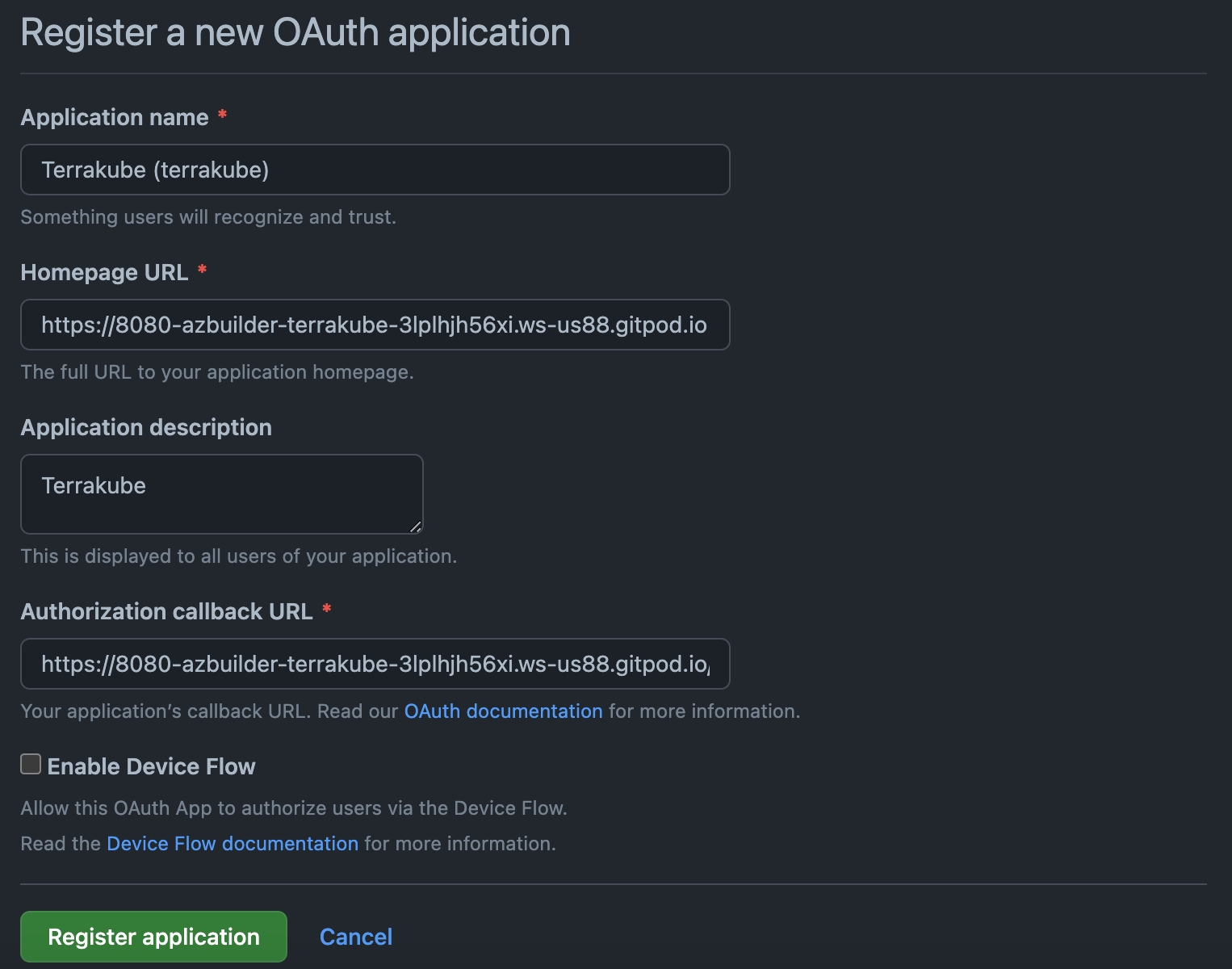
In the Github page, complete the required fields and click Register application
Application Name
Your application name, for example you can use your organization name.
Homepage URL
The url for your application or website,
Application Description
Any description you choice
Authorization Callback URL
Copy the callback url from the Terrakube UI
You can complete the fields using the information suggested by terrakube in the VCS provider screen
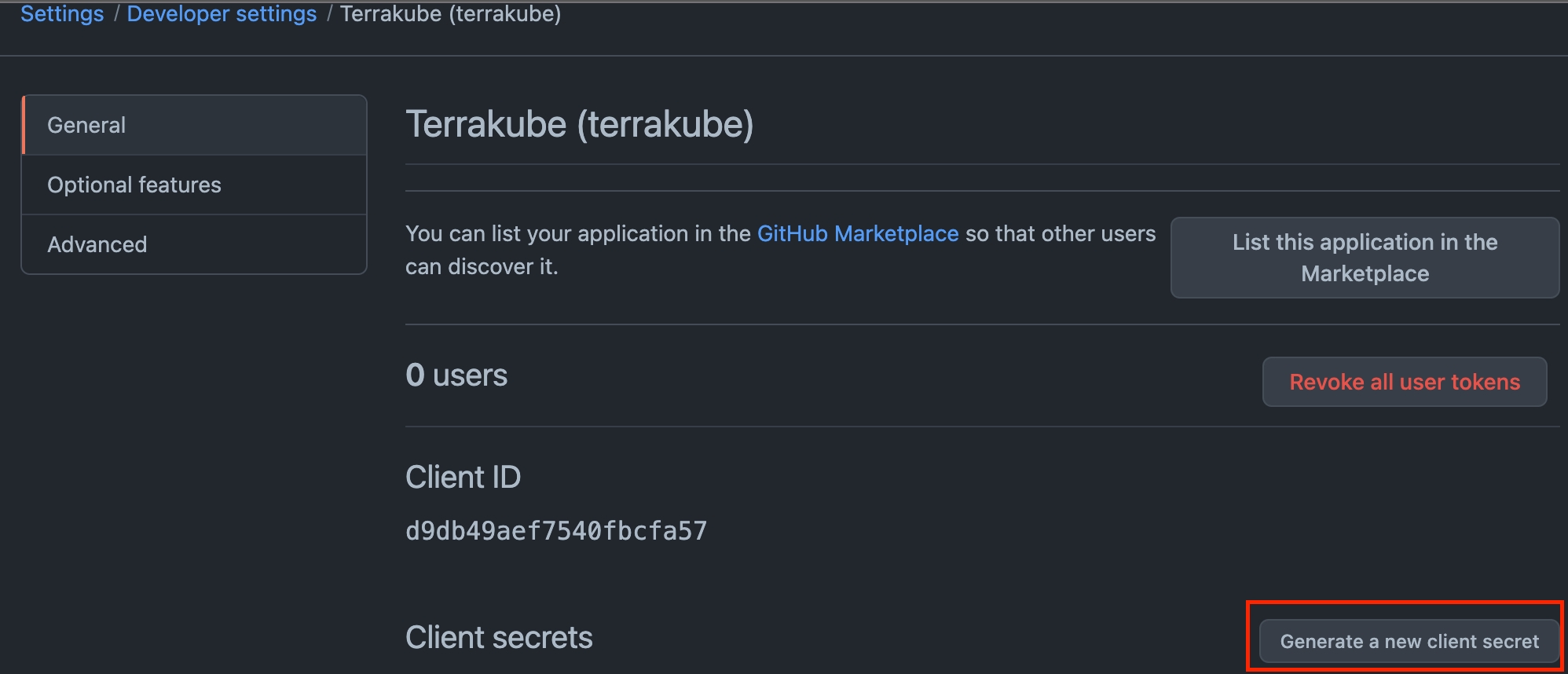
Next, generate a new client secret
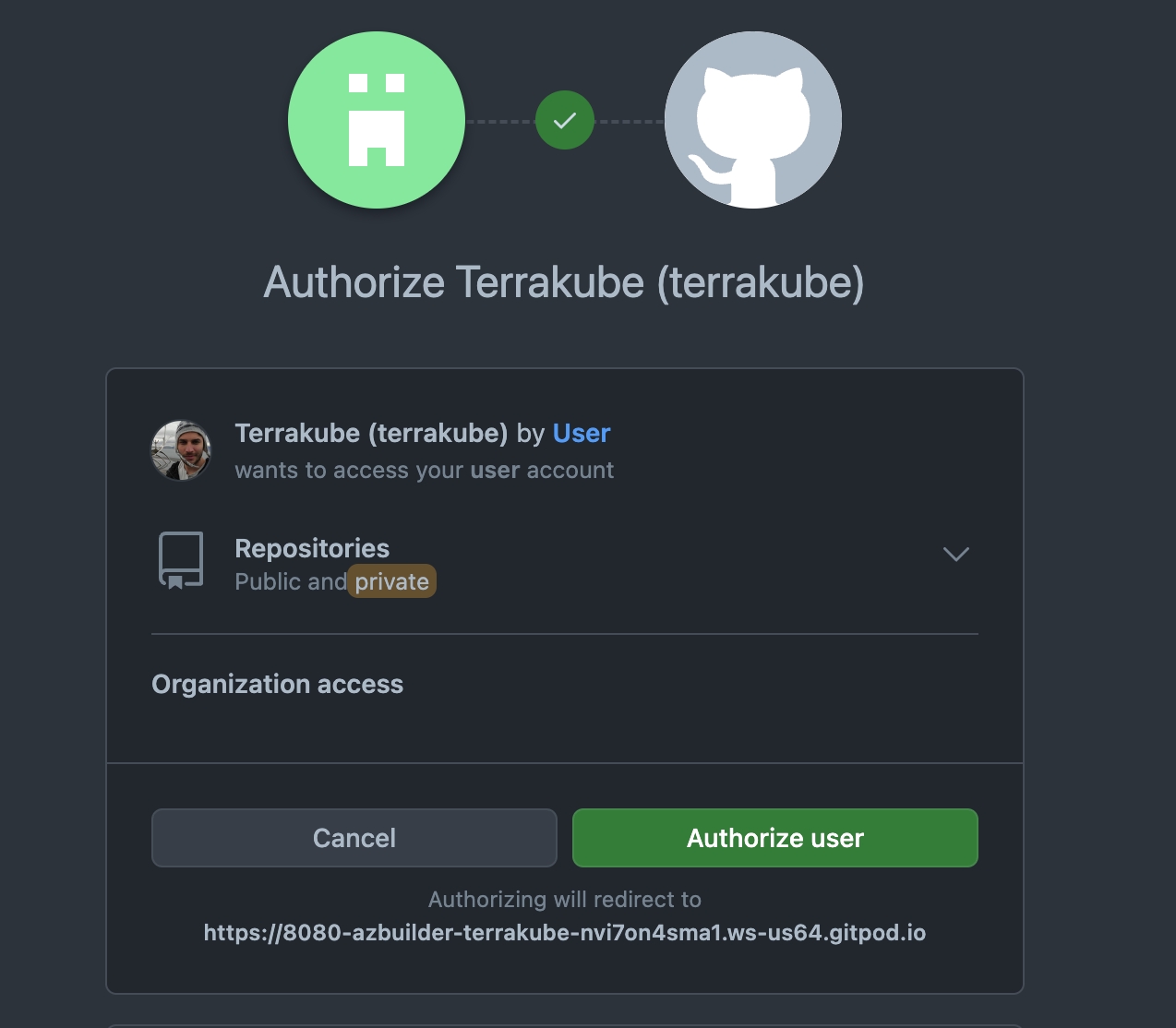
Copy the Client Id and Client Secret from Github and go back to Terrakube to complete the required information. Then, click the Connect and Continue button
You will see the Github page, click the Authorize button to complete the connection
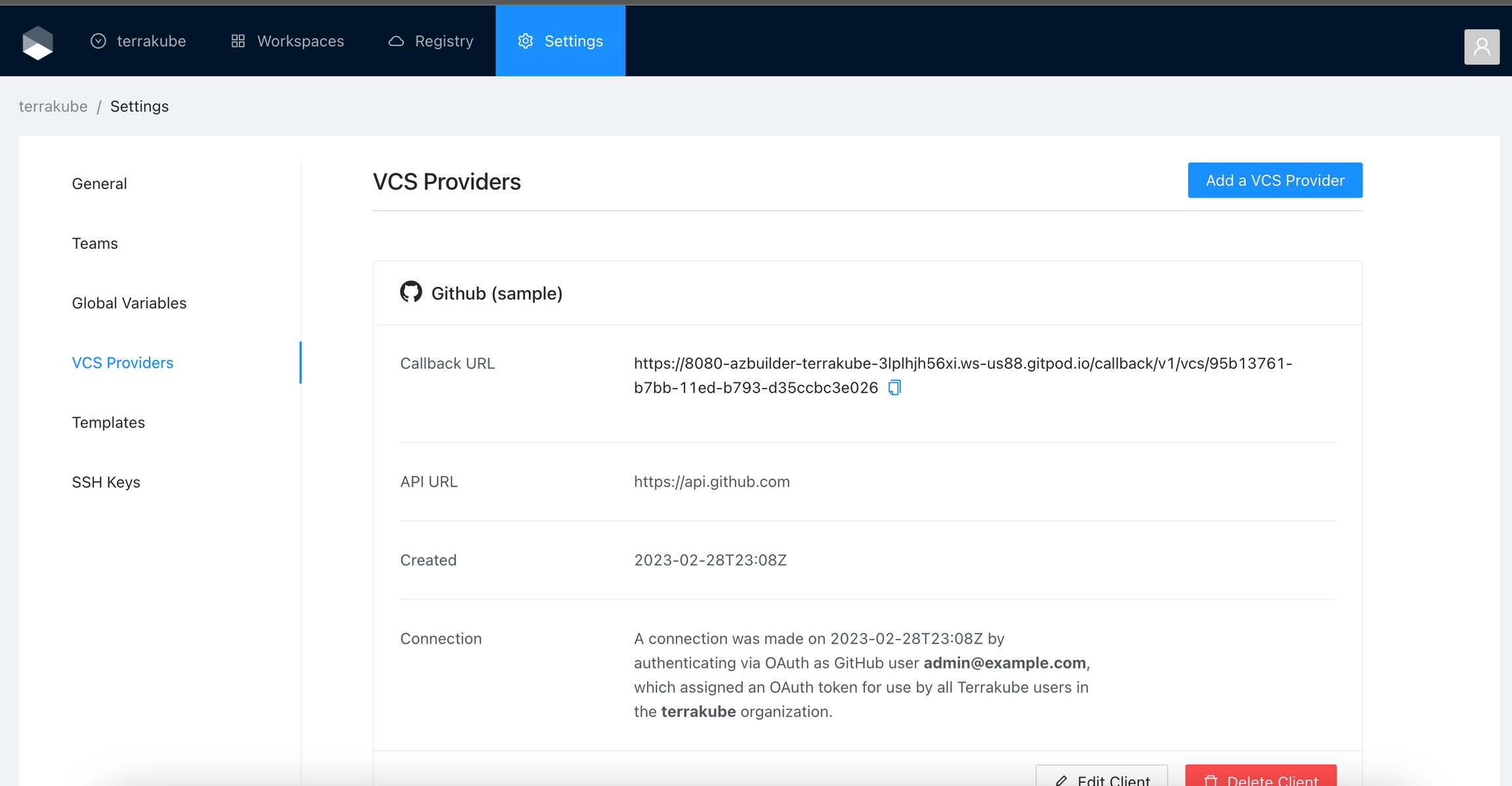
Finally, if the connection was established successfully, you will be redirected to the VCS provider’s page in your organization. You should see the connection status with the date and the user that created the connection.
And now, you will be able to use the connection in your workspaces and modules: