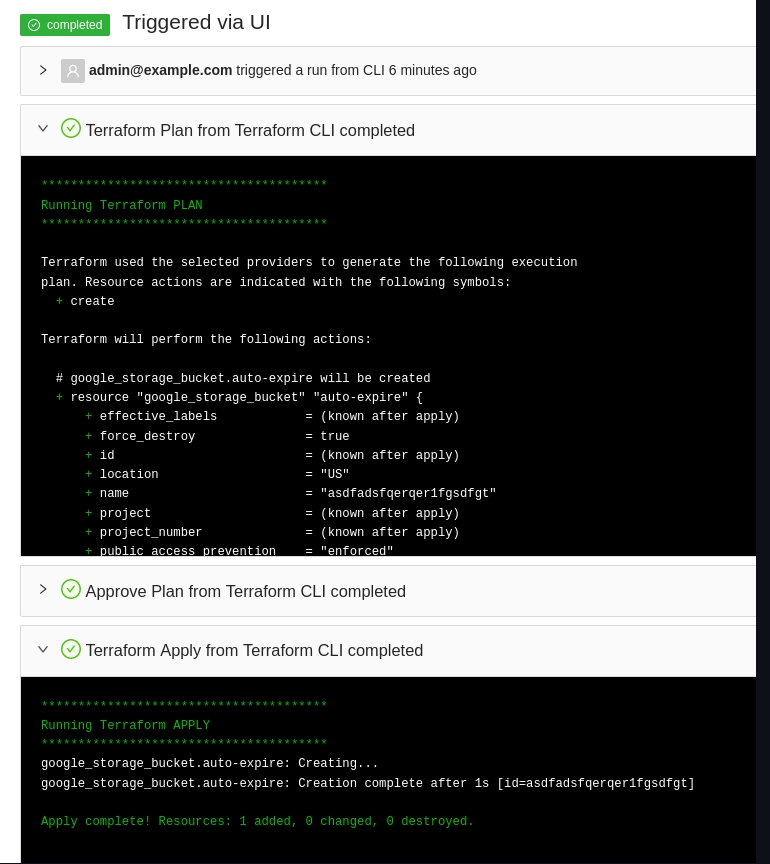
The dynamic provider credential setup in GCP can be done with the Terrraform code available in the following link:
https://github.com/AzBuilder/terrakube/tree/main/dynamic-credential-setup/gcp
The code will also create a sample workspace with all the require environment variables that can be used to test the functionality using the CLI driven workflow.
Make sure to mount your public and private key to the API container as explained here
Mare sure the private key is in "pkcs8" format
Validate the following terrakube api endpoints are working:
Set terraform variables using: "variables.auto.tfvars"
To generate the API token check here
Run Terraform apply to create all the federated credential setup in GCP and a sample workspace in terrakube for testing
To test the following terraform code can be used:

This feature is available from version 2.21.0
To use Dynamic Provider credentials we need to genera a public and private key that will be use to generate a validate the federated tokens, we can use the following commands
You need to make sure the private key starts with "-----BEGIN PRIVATE KEY-----" if not the following command can be used to transform the private key to the correct format
The public and private key need to be mounted inside the container and the path should be specify in the following environment variables
DynamicCredentialPublicKeyPath
DynamicCredentialPrivateKeyPath
To use Dynamic Provider credentials the following public endpoints were added. This endpoint needs to be accessible for your different cloud providers.
The following environment variables can be used to customize the dynamic credentials configuration:
DynamicCredentialId = This will be the kid in the JWKS endpoint (Default value: 03446895-220d-47e1-9564-4eeaa3691b42)
DynamicCredentialTtl= The TTL for the federated token generated internally in Terrakube (Defafult: 30)
DynamicCredentialPublicKeyPath= The path to the public key to validate the federated tokens
DynamicCredentialPrivateKeyPath=The path to the private key to generate the federated tokens
Terrakube will generate a JWT token internally, this token will be used to authenticate to your cloud provider.
The token structure looks like the following for Azure
The token structure looks like the following for GCP
The token structure looks like the following for AWS
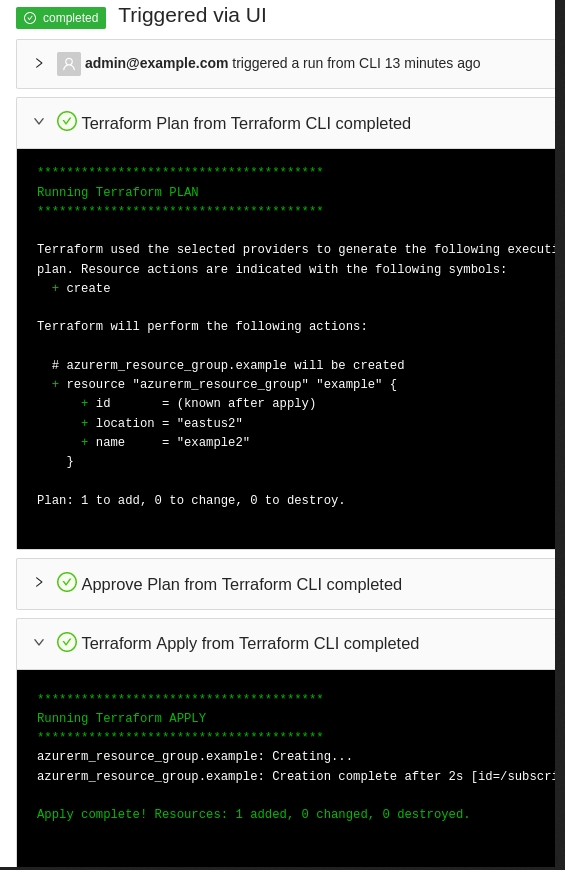
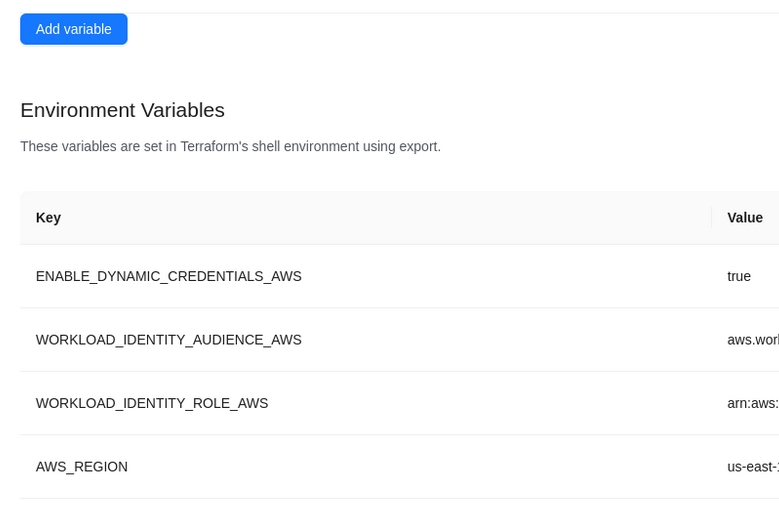
The dynamic provider credential setup in AWS can be done with the Terrraform code available in the following link:
https://github.com/AzBuilder/terrakube/tree/main/dynamic-credential-setup/aws
The code will also create a sample workspace with all the require environment variables that can be used to test the functionality using the CLI driven workflow.
Make sure to mount your public and private key to the API container as explained here
Mare sure the private key is in "pkcs8" format
Validate the following terrakube api endpoints are working:
Set terraform variables using: "variables.auto.tfvars"
To generate the API token check here
Run Terraform apply to create all the federated credential setup in AWS and a sample workspace in terrakube for testing
To test the following terraform code can be used:
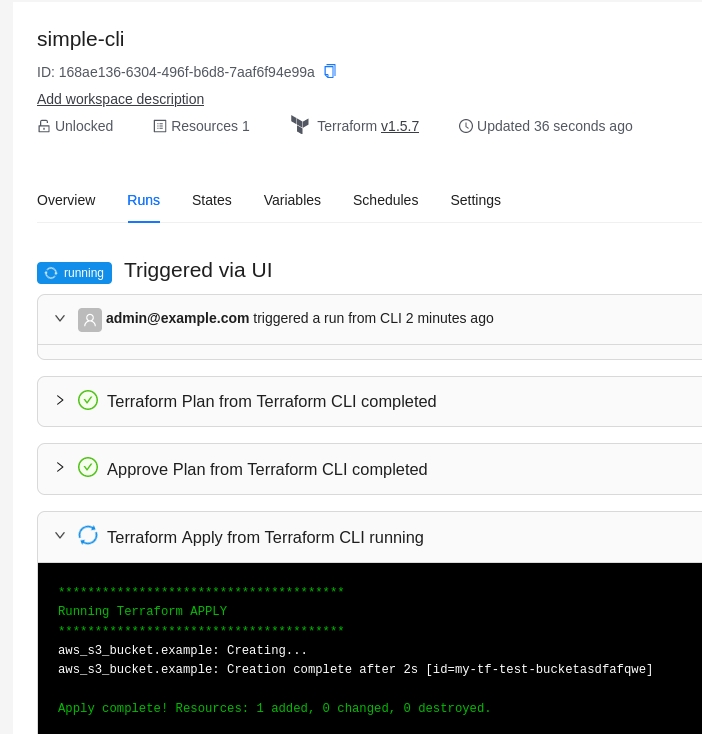
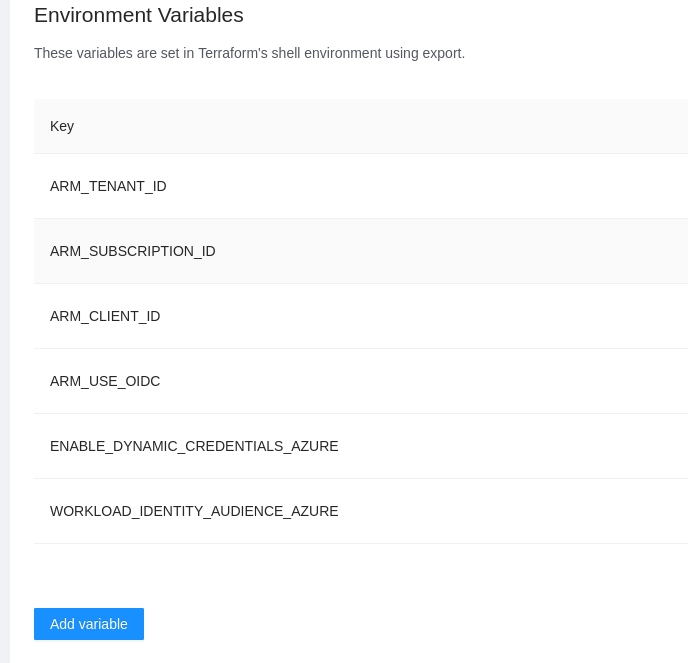
The dynamic provider credential setup in Azure can be done with the Terrraform code available in the following link:
https://github.com/AzBuilder/terrakube/tree/main/dynamic-credential-setup/azure
The code will also create a sample workspace with all the require environment variables that can be used to test the functionality using the CLI driven workflow.
Make sure to mount your public and private key to the API container as explained here
Mare sure the private key is in "pkcs8" format
Validate the following terrakube api endpoints are working:
Set terraform variables using: "variables.auto.tfvars"
To generate the API token check here
Run Terraform apply to create all the federated credential setup in AWS and a sample workspace in terrakube for testing
To test the following terraform code can be used:
When running a job Terrakube will correctly authenticate to Azure without any credentials inside the workspace