A working Keycloak server with a configured realm.
For configuring Terrakube with Keycloak using Dex the following steps are involved:
Keycloak client creation and configuration for Terrakube.
Configure Terrakube so it works with Keycloak.
Testing the configuration.
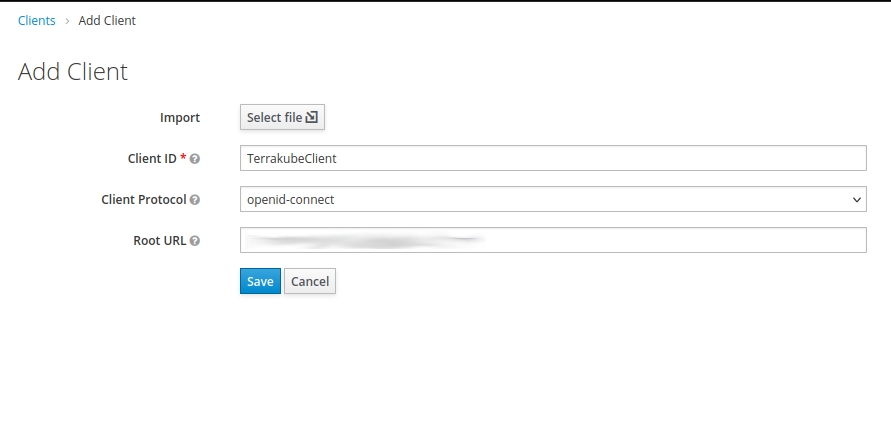
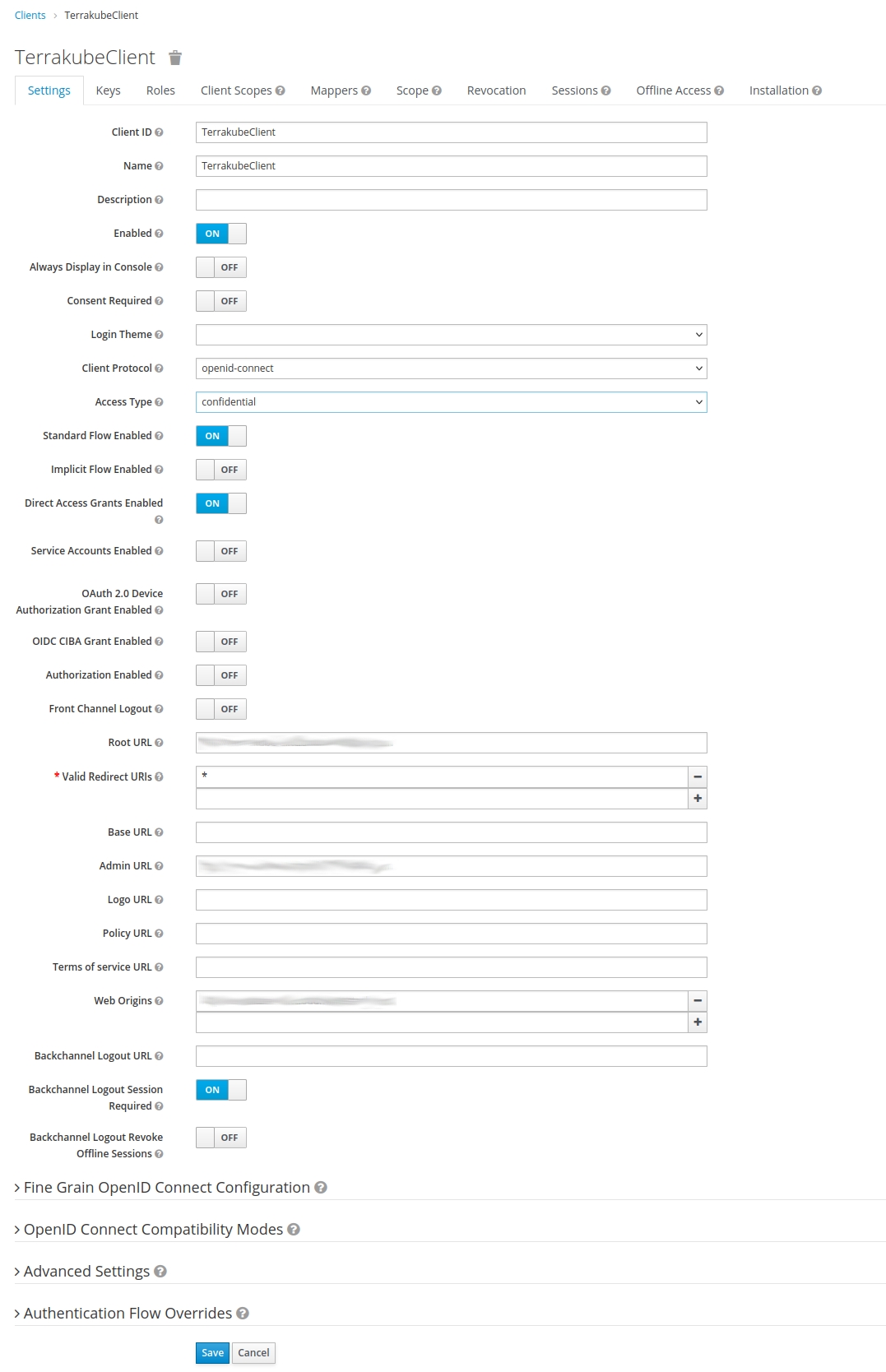
Log in to Keycloak with admin credentials and select Configure > Clients > Create. Define the ID as TerrakubeClient and select openid-connect as its protocol. For Root URL use Terrakube's GUI URL. Then click Save.
A form for finishing the Terrakube client configuration will be displayed. These are the fields that must be fulfilled:
Name: in this example it has the value of TerrakubeClient.
Client Protocol: it must be set to openid-connect.
Access Type: set it to confidential.
Root URL: Terrakube's UI URL.
Valid Redirect URIs: set it to *
Then click Save.
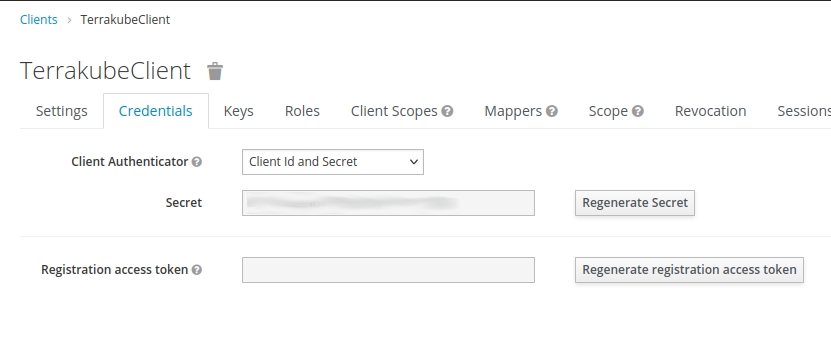
Notice that, since we set Access Type to confidential, we have an extra tab titled Credentials. Click the Credentials tab and copy the Secret value. It will be used later when we configure the Terrakube's connector.
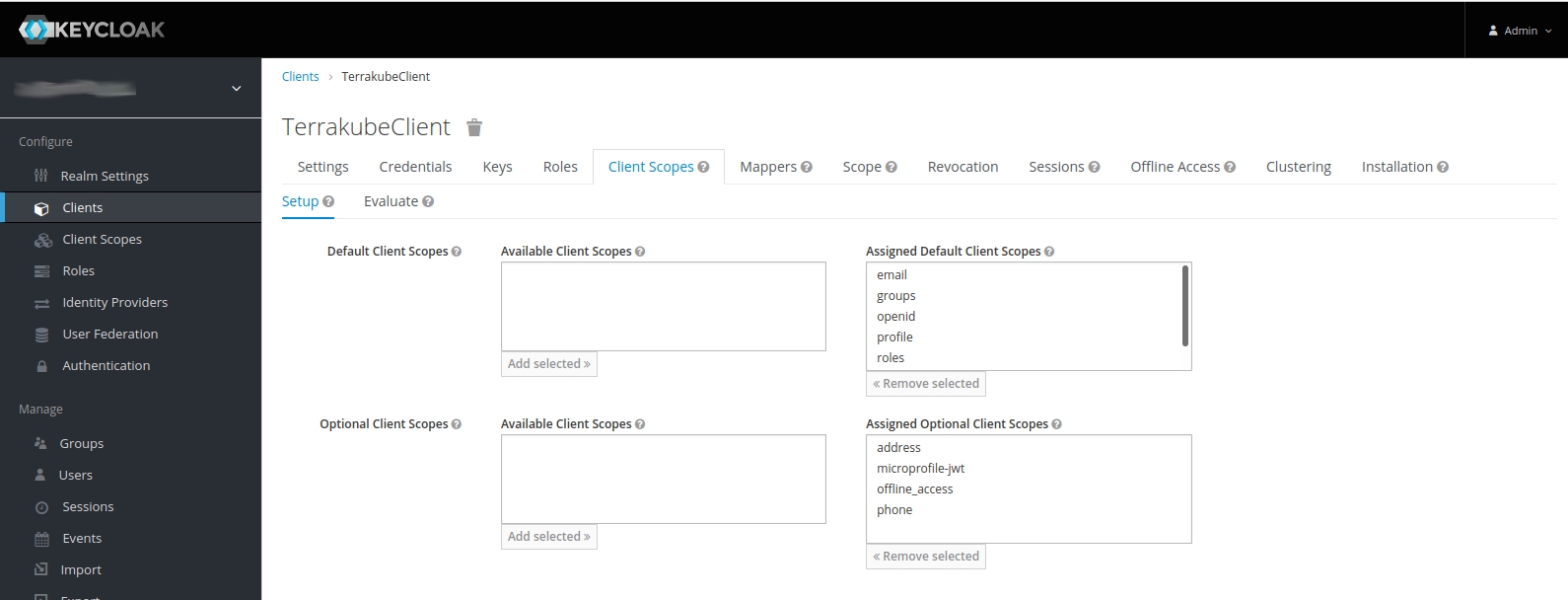
Depending on your configuration, Terrakube might expect different client scopes, such as openid, profile, email, groups, etc. You can see if they are assigned to TerrakubeClient by clicking on the Client Scopes tab (in TerrakubeClient).
If they are not assigned, you can assign them by selecting the scopes and clicking on the Add selected button.
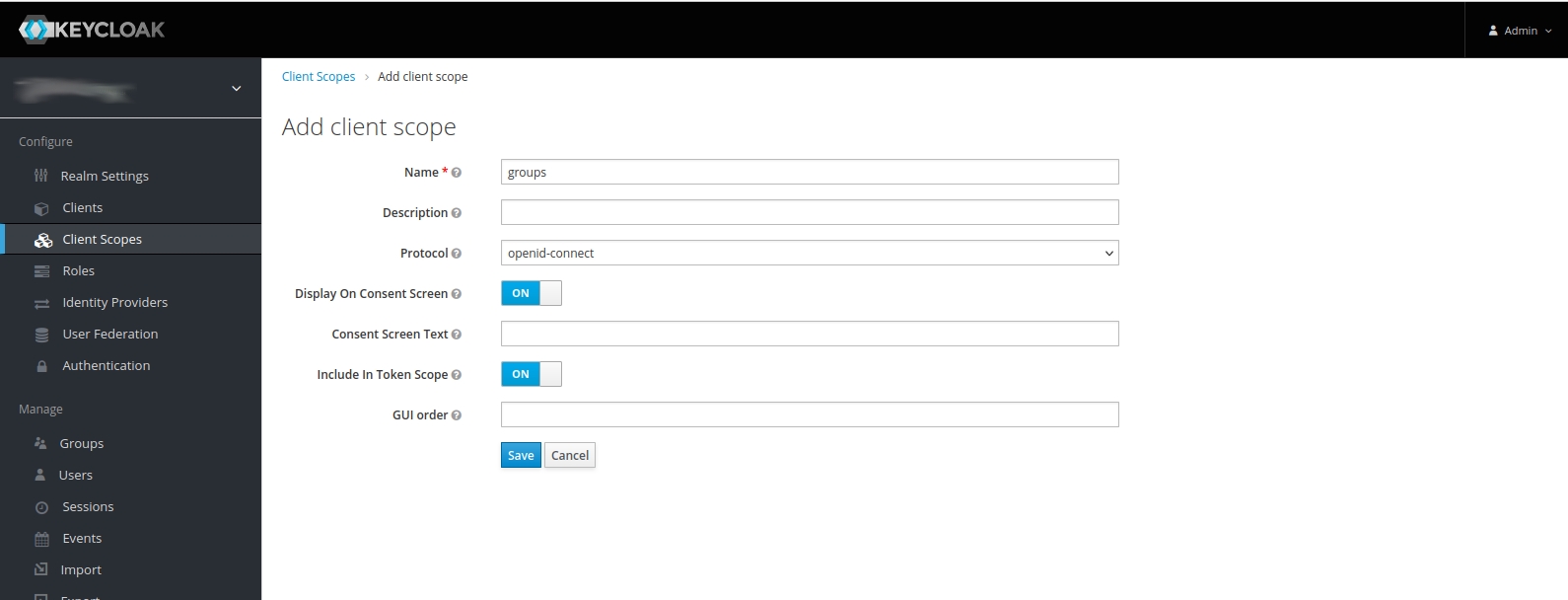
If some scope does not exist, you must create it before assigning it to the client. You do this by clicking on Client Scopes, then click on the Create button. This will lead you to a form where you can create the new scope. Then, you can assign it to the client.
We have to configure a Dex connector to use with Keycloak. Add a new connector in Dex's configuration, so it looks like this:
This is the simpler configuration that we can use. Let's see some notes about this fields:
type: must be oidc (OpenID Connect).
name: this is the string shown in the connectors list in Terrakube GUI.
issuer: it refers to the Keycloak server. It has the form [http|https]://<KEYCLOAK_SERVER>/auth/realms/<REALM_NAME>
clientID: refers to the Client ID configured in Keycloak. They must match.
clientSecret: must be the secret in the Credentials tab in Keycloak..
redirectURI: has the form [http|https]://<TERRAKUBE_API>/dex/callback. Notice this is the Terrakube API URL and not the UI URL.
insecureEnableGroups: this is required to enable groups claims. This way groups defined in Keycloak are brought by Terrakube's Dex connector.
{% hint style="info" %} If your users do not have a name set (First Name field in Keycloak), you must tell oidc which attribute to use as the user's name. You can do this giving the userNameKey:
{% endhint %}
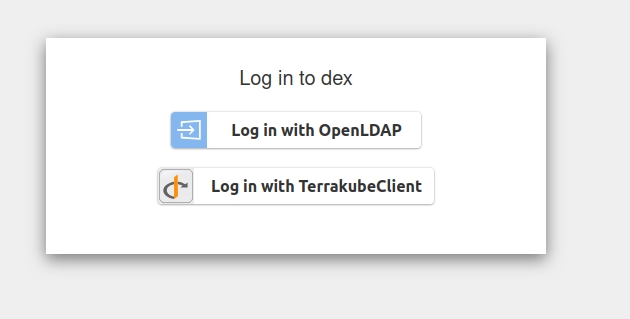
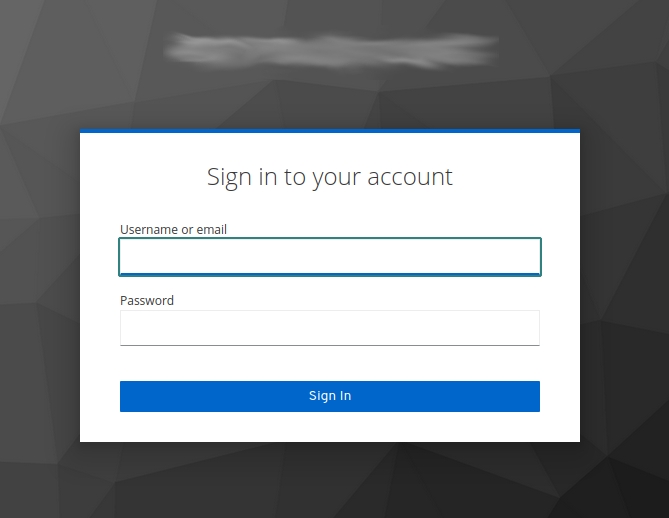
When we click on Terrakube's login button we are given the choice to select the connector we want to use:
Click on Log in with TerrakubeClient. You will be redirected to a login form in Keycloak:
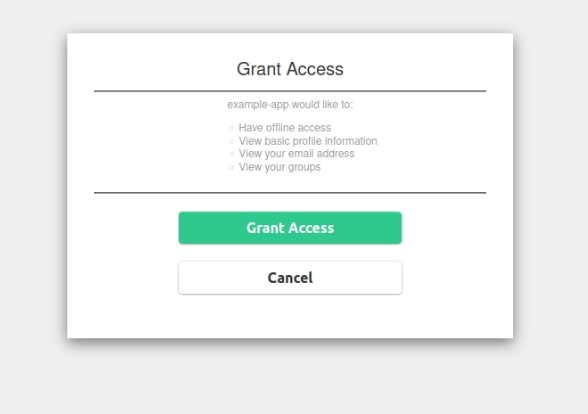
After login, you are redirected back to Terrakube and a dialog asking you to grant access is shown
Click on Grant Access. That is the last step. If everything went right, now you should be logged in Terrakube.
To run Terrakube in Docker Desktop you wil need the following:
Create Github Organization
Create a team called TERRAKUBE_ADMIN and add the members
Install Docker Desktop
Nginx Ingress for Docker Desktop
Azure Storage Account/AWS S3 Bucket/GCP Storage Bucket
To get more information about the Dex Configuration for Github you can check this link
Create a new Github Oauth application with the authorization callback URL "http://host.docker.internal/dex/callback" in this link
Copy the values for Client Id and Client Secret
Update the HOSTS file adding the following
Replace <<CHANGE_THIS>> with the real values, create the values.yaml file and run the helm install
Run the installation
For any question please open an issue in our helm chart repository
You can handle Terrakube users with differen authentication providers like the following
Azure Authentication with Dex Connecor require Terrakube >= 2.6.0 and Helm Chart >= 2.0.0
Azure Active Directory here
Azure Storage Account
For this example lets image that you will be using the following domains to deploy Terrakube.
registry.terrakube.azure.com
ui.terrakube.azure.com
api.terrakube.azure.com
You need to complete the Azure authentication setup for Dex. You can found information in this link
You need to go to your Azure and create a new Application
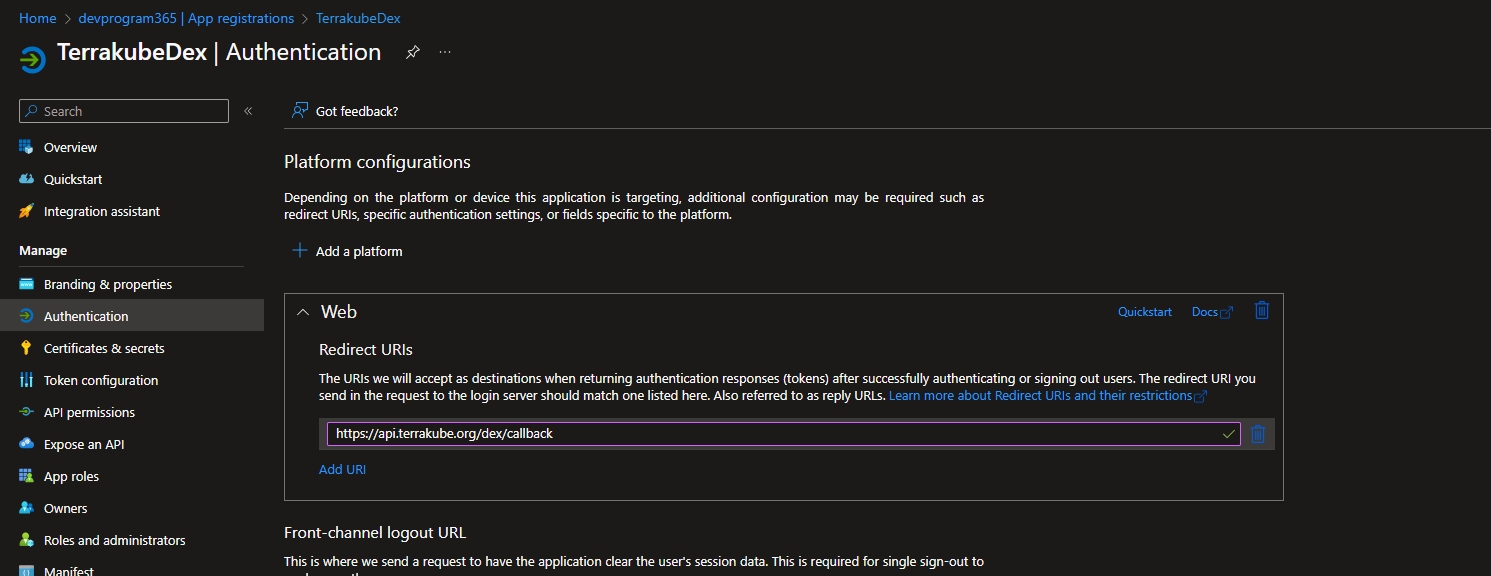
After the application is created you need to add the redirect URL.
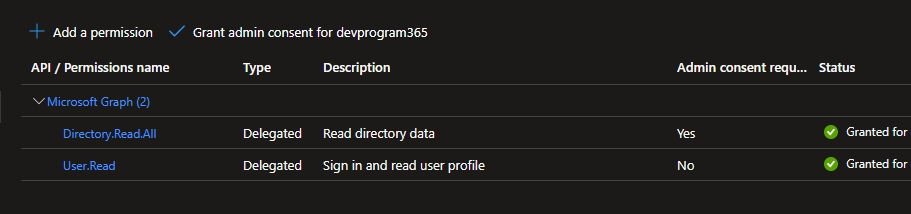
You will also need to add the permission Directory.Read.All and ask a Azure administrator to approve the permission.
Now you can create the DEX configuration, you will use this config later when deploying the helm chart.
The firt step is to clone the repository.
Replace <<CHANGE_THIS>> with the real values, create the values.yaml file and run the helm install
Run the installation
For any question or feedback please open an issue in our helm chart repository
Google Identity Authentication with Dex connector require Terrakube >= 2.6.0 and Helm Chart >= 2.0.0
Google Cloud Identity here
Gooble Storage Bucket
For this example lets image that you will be using the following domains to deploy Terrakube.
registry.terrakube.gcp.com
ui.terrakube.gcp.com
api.terrakube.gcp.com
You need to complete the Google authentication setup for Dex. You can found information in this link
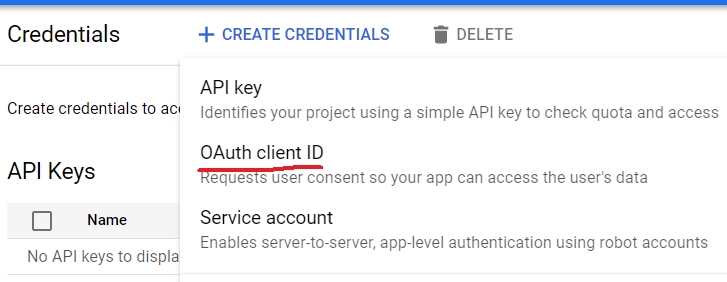
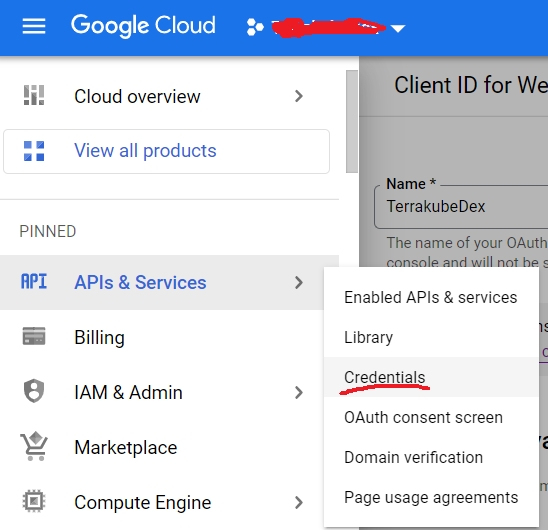
You need to go to your GCP projet and create a new OAuth Application you can follow this steps: firts select "APIs & Services => Credentials"
Once inside the "Credentials" page, you will have to create a new OAuth Client
The OAuth application should look like this with the redirect URL "https://api.terrakube.gcp.com/dex/callback"
For Google authentication we need to get the GCP groups so you need to complete this setup.
Include the Domain Wide Delegation inside the admin consol https://admin.google.com/ for the OAuth application
Using the following permission "https://www.googleapis.com/auth/admin.directory.group.readonly"
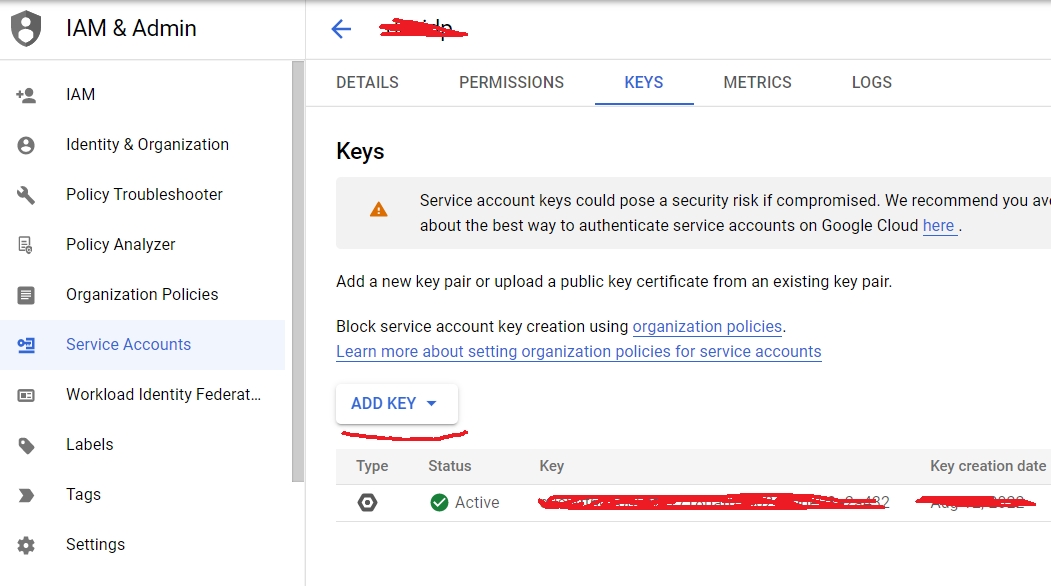
You can now generate the JSON credentials file for your application, you will use this file later in the helm chart.
Now you can create the DEX configuration, you will use this config later when deploying the helm chart.
The firt step is to clone the repository.
Replace <<CHANGE_THIS>> with the real values, create the values.yaml file and run the helm install
Run the installation
For any question or feedback please open an issue in our helm chart repository
AWS Cognito Authentication with Dex Connecor require Terrakube >= 2.6.0 and Helm Chart >= 2.0.0
AWS Cognito
AWS S3 Bucket
For this example lets image that you will be using the following domains to deploy Terrakube.
registry.terrakube.aws.com
ui.terrakube.aws.com
api.terrakube.aws.com
You need to complete the AWS Cognito authentication setup for Dex using the OIDC connector. You can found information in this link
You need to create a new Cognito user pool
You can keep the default values
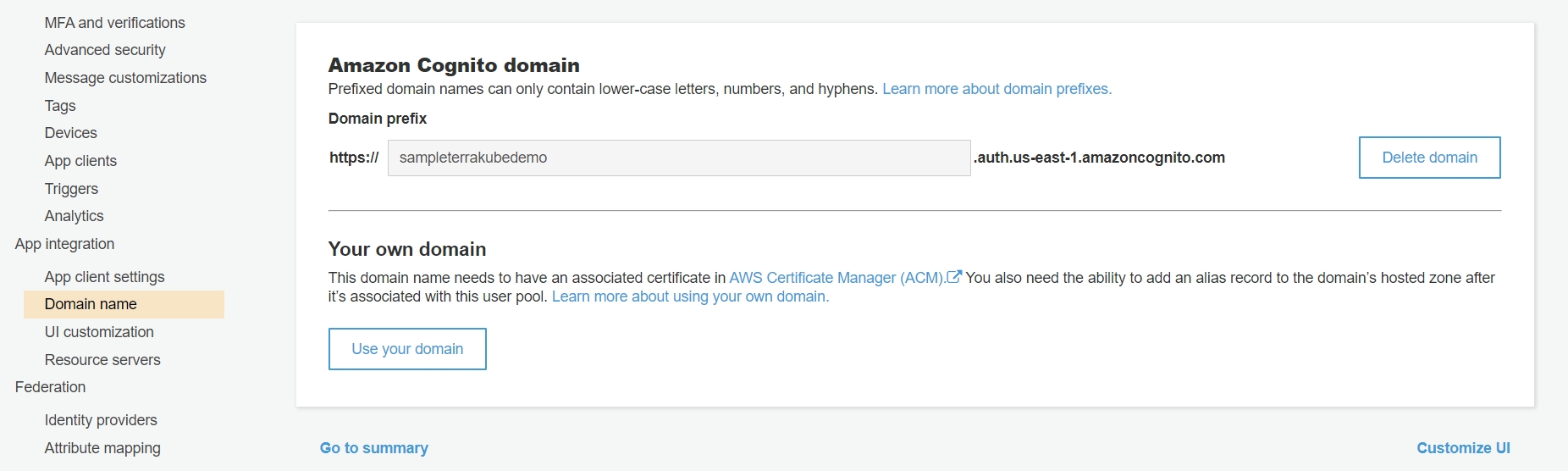
Add the domain name to cognito
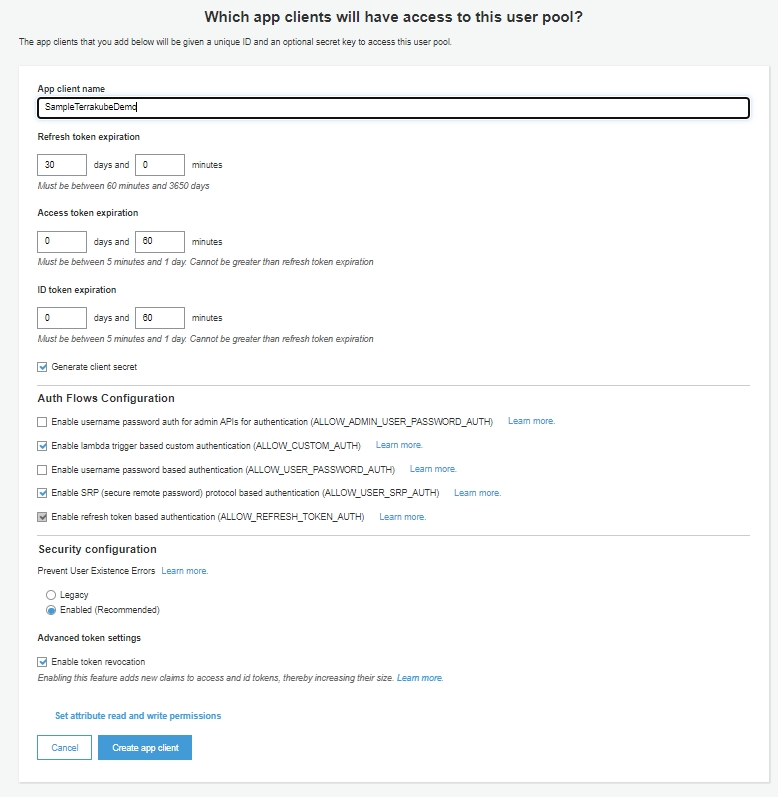
Once the user pool is created you will need to create a new application.
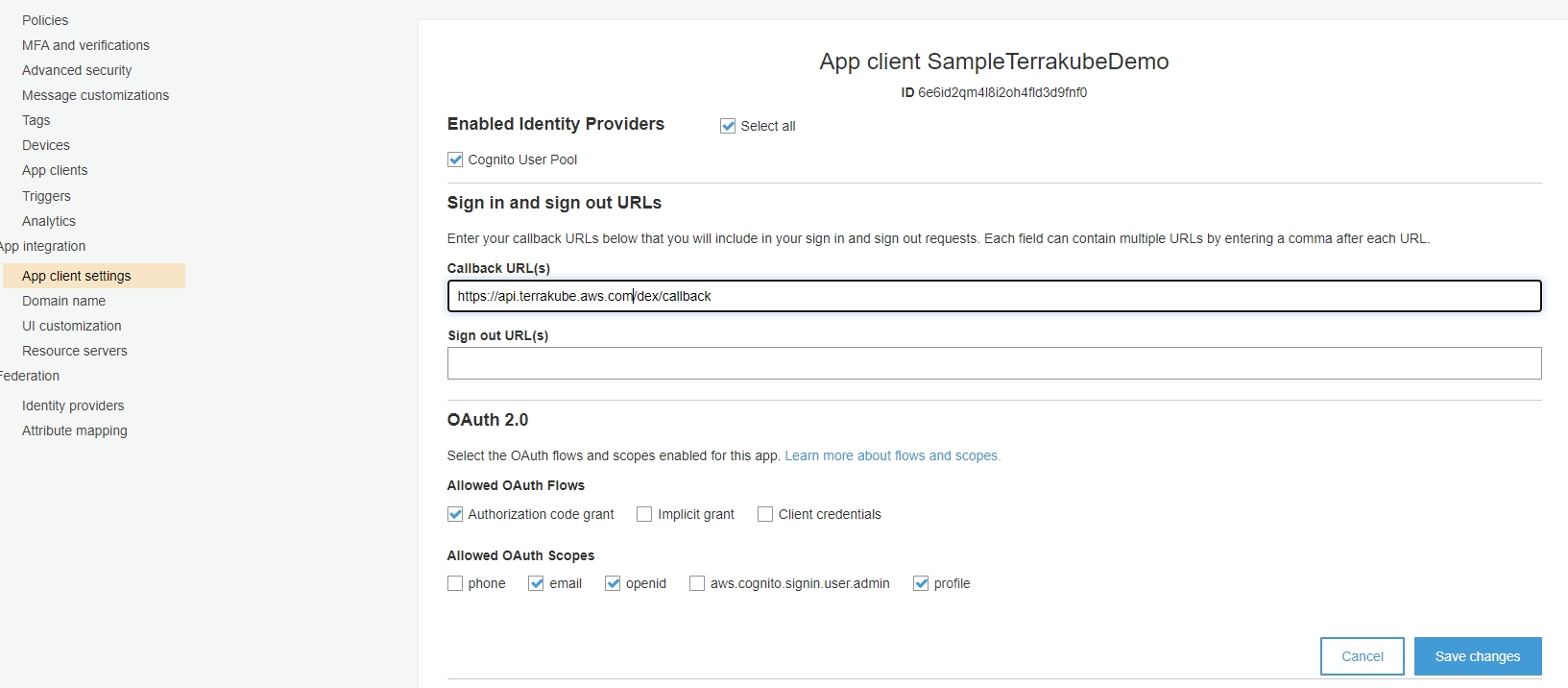
Update the application configuration and update the redirect URL configuration.
Now you can create the DEX configuration, you will use this config later when deploying the helm chart.
The firt step is to clone the repository.
Replace <<CHANGE_THIS>> with the real values, create the values.yaml file and run the helm install
Run the installation
For any question or feedback please open an issue in our helm chart repository