Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Terrakube support sharing the terraform state between workspaces using the following data block.
For example it can be used in the following way:
This feature is supported from Terrakube 2.15.0
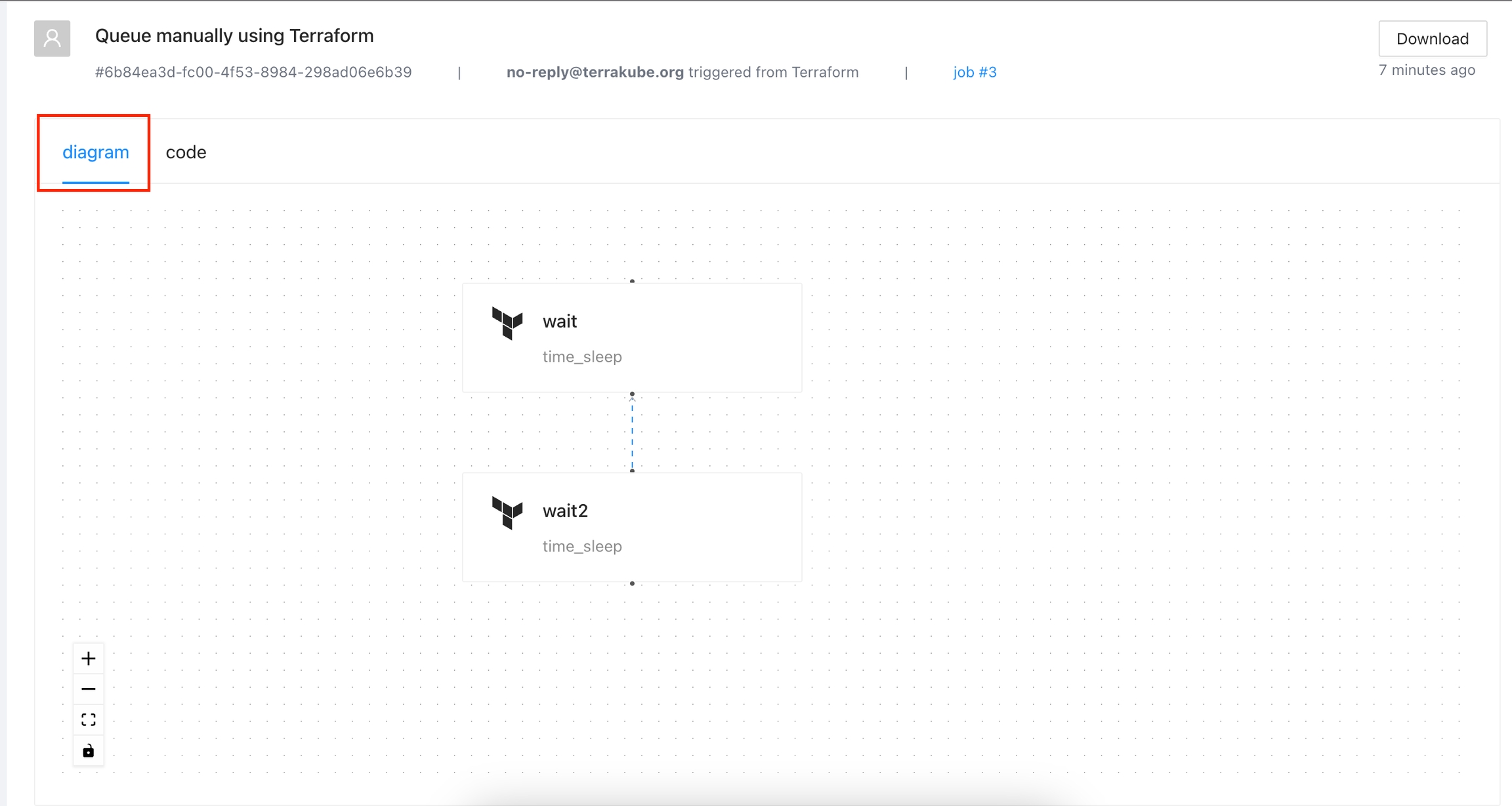
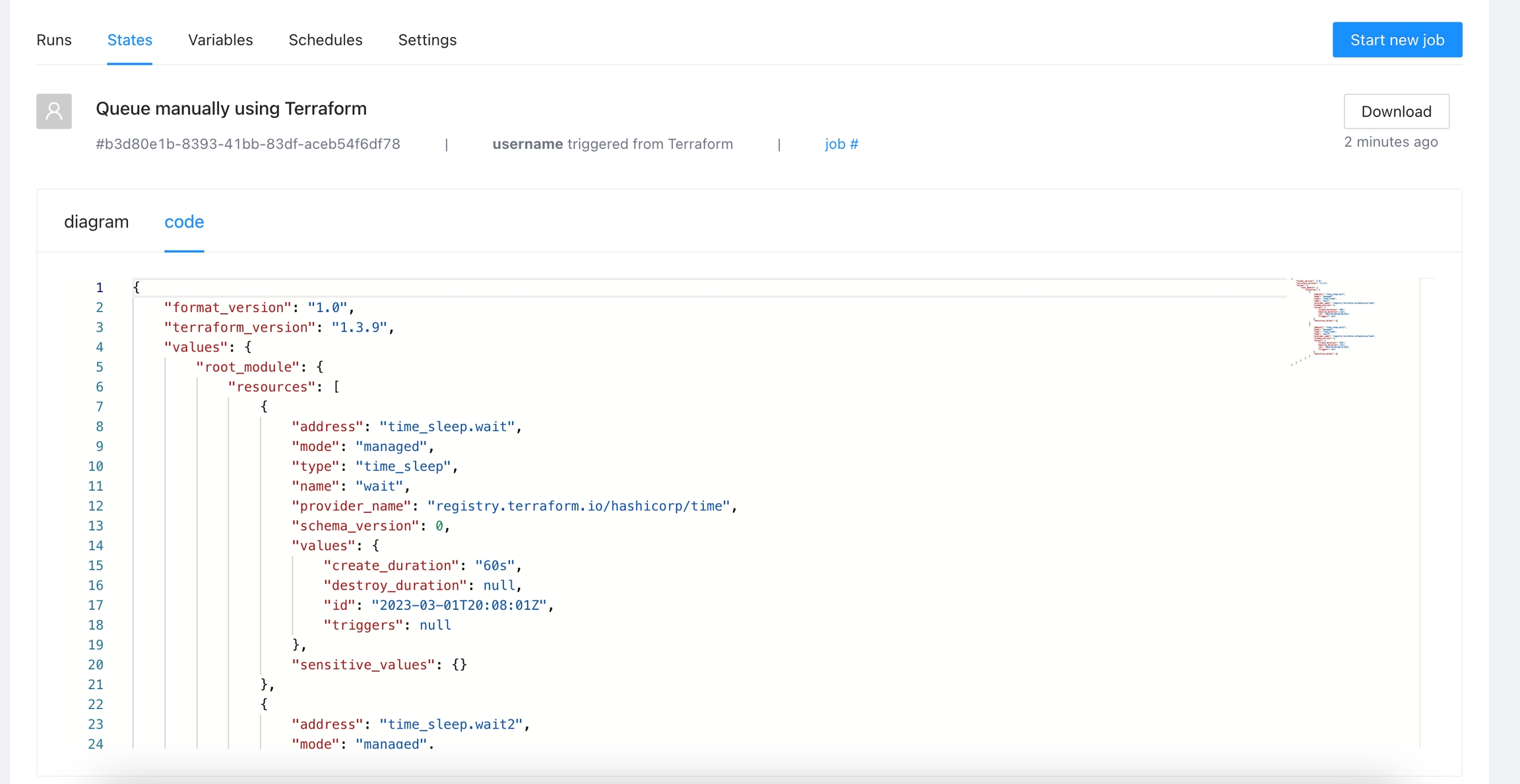
Each Terrakube workspace has its own separate state data, used for jobs within that workspace. In Terrakube you can see the Terraform state in the standard JSON format provided by the Terraform cli or you can see a Visual State, this is a diagram created by Terrakube to represent the resources inside the JSON state.
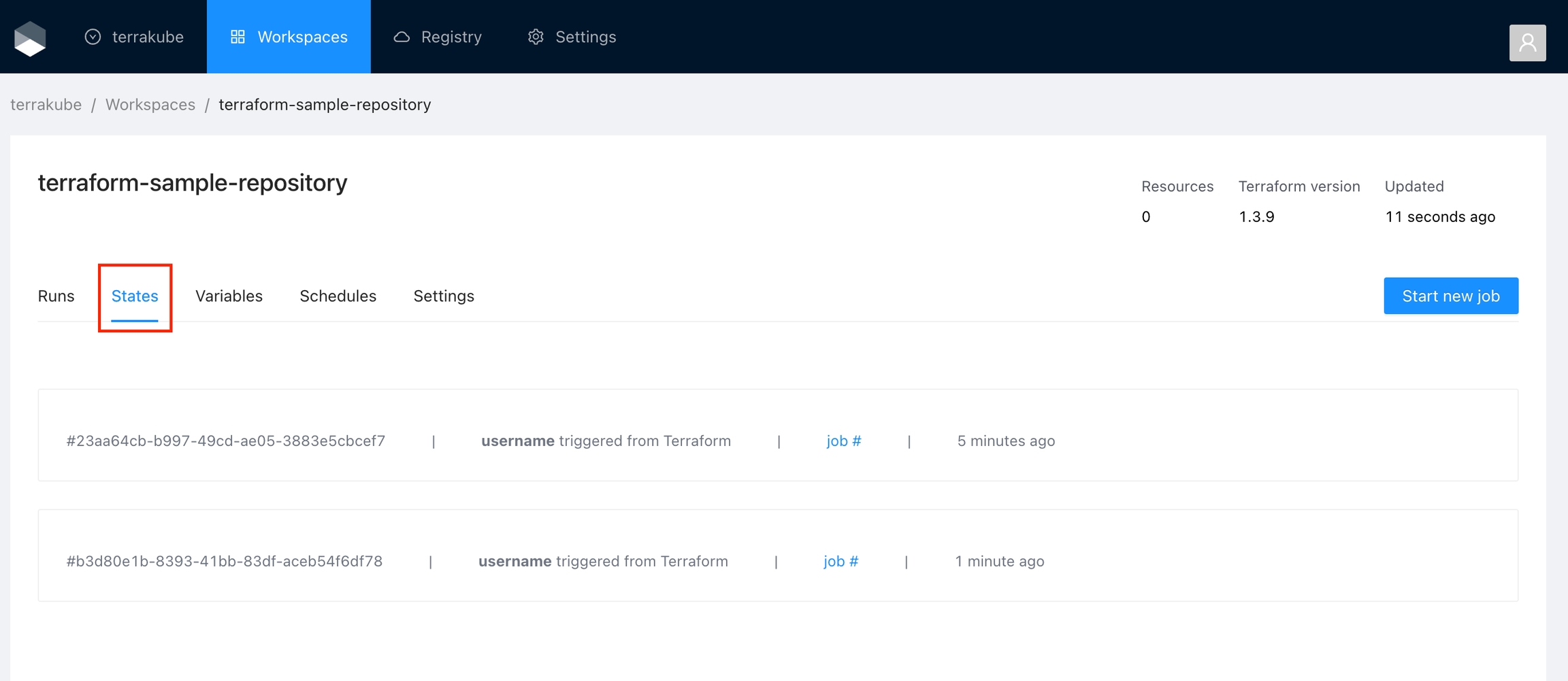
Go to the workspace and click the States tab and then click in the specific state you want to see.
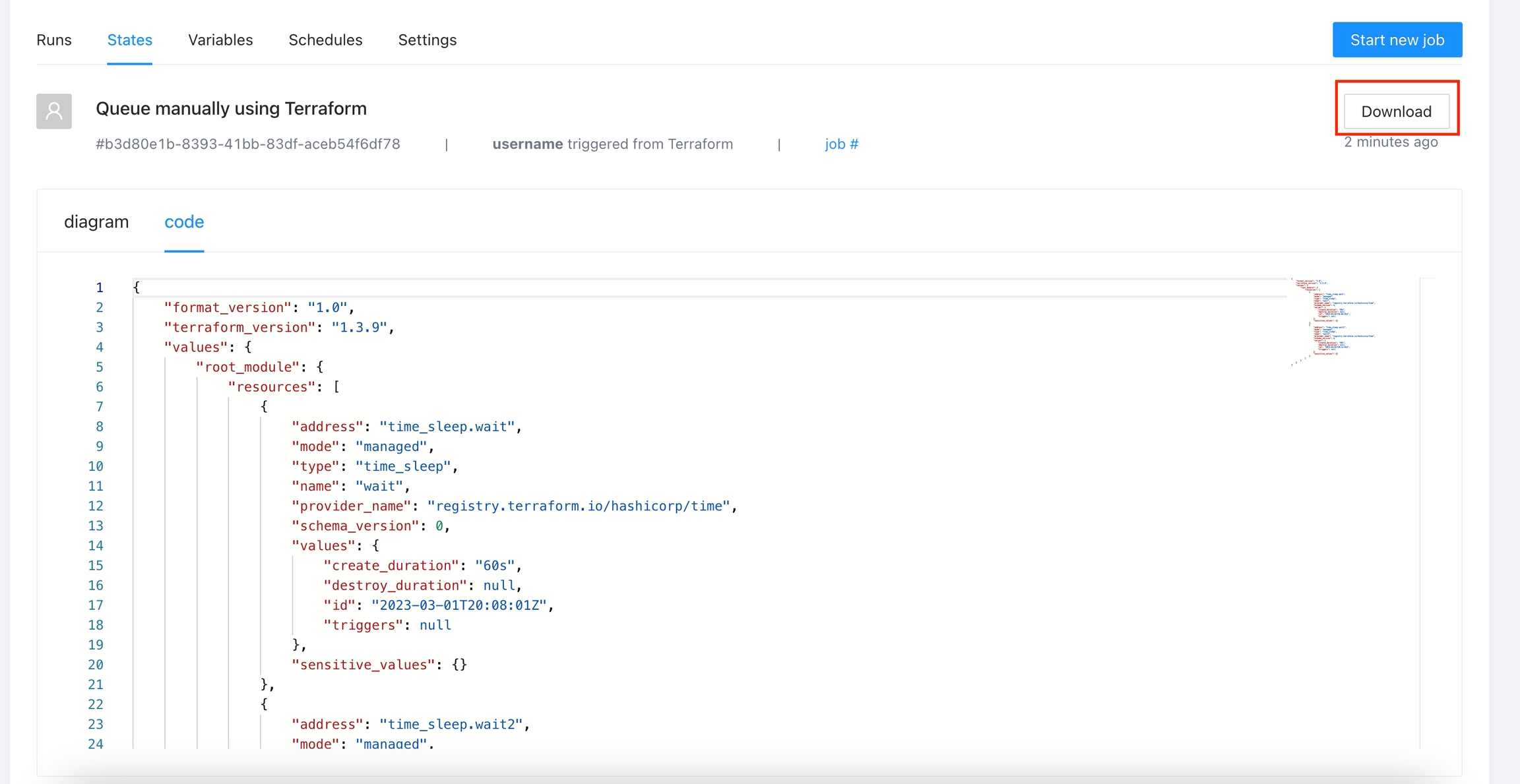
You will see the state in JSON format
You can click the Download button to get a copy of the JSON state file
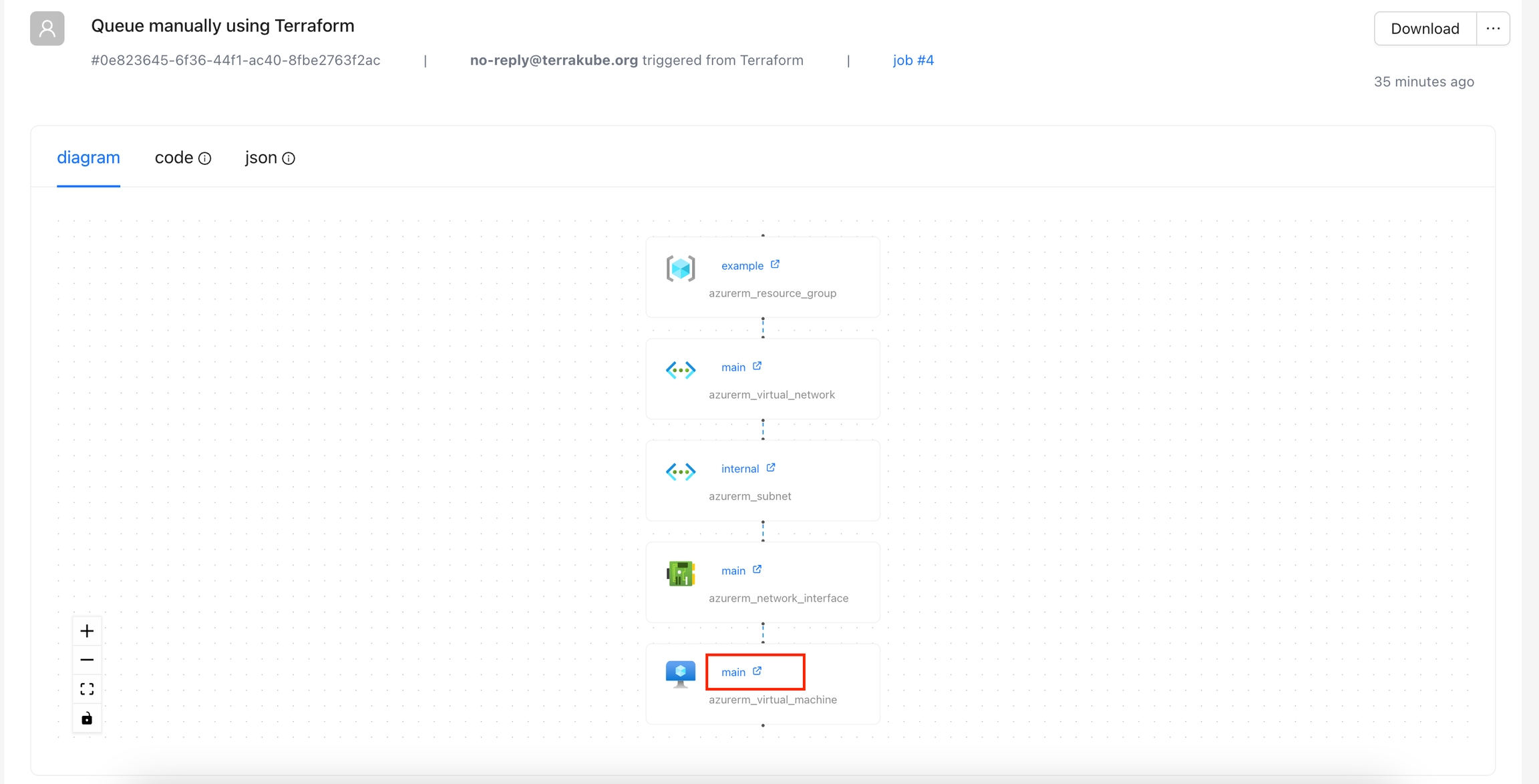
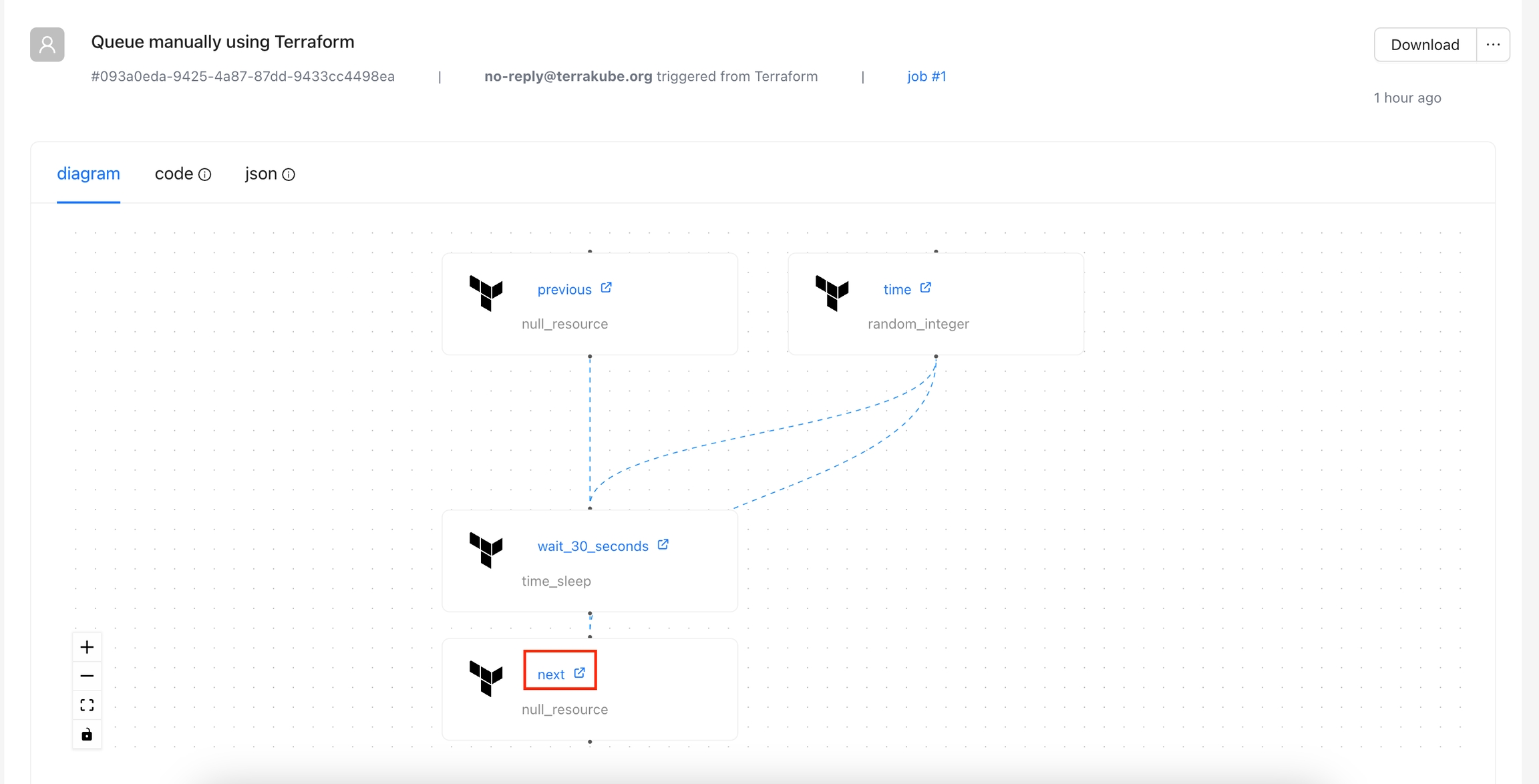
Inside the states page, click the diagram tab and you will see the visual state for your terraform state.
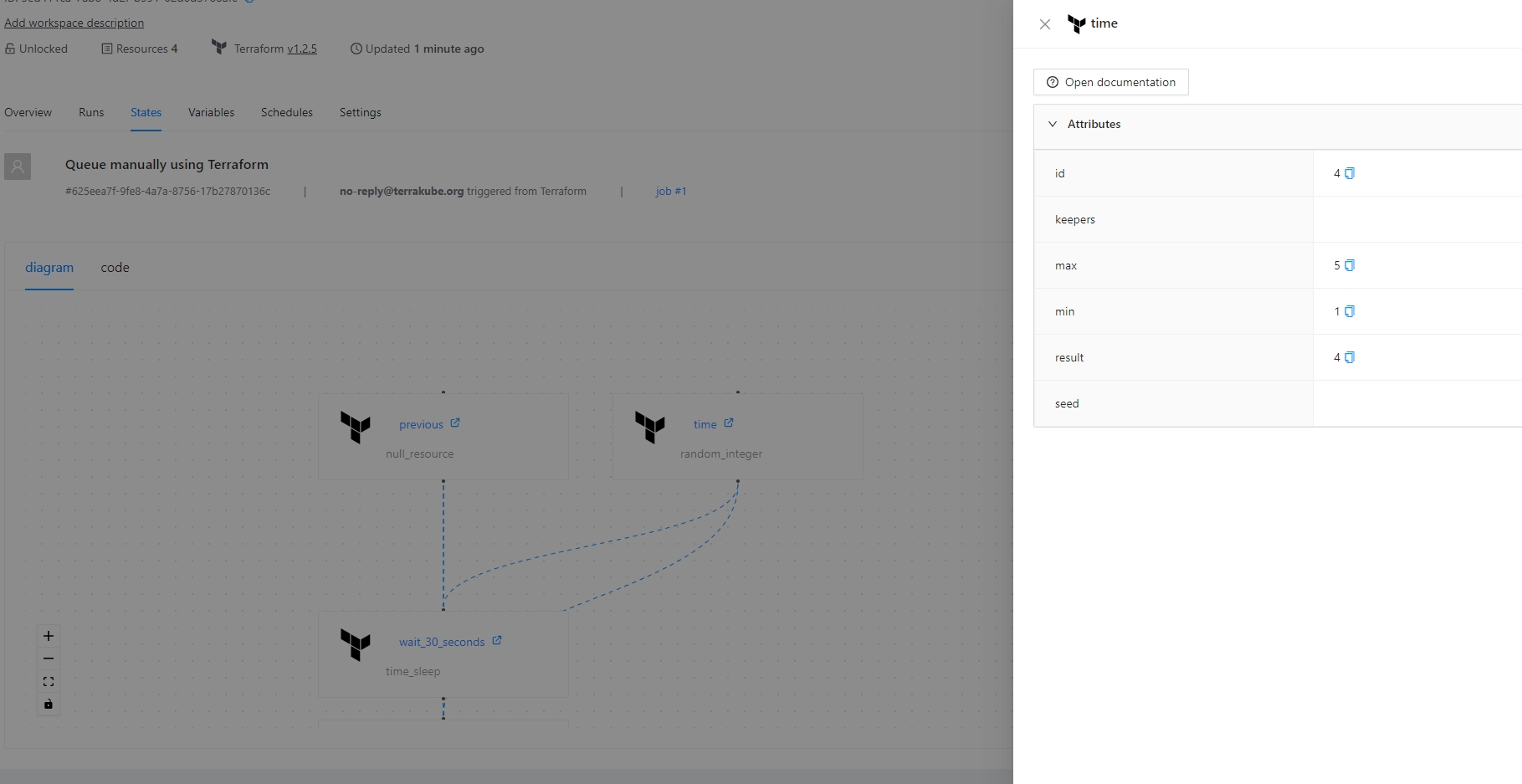
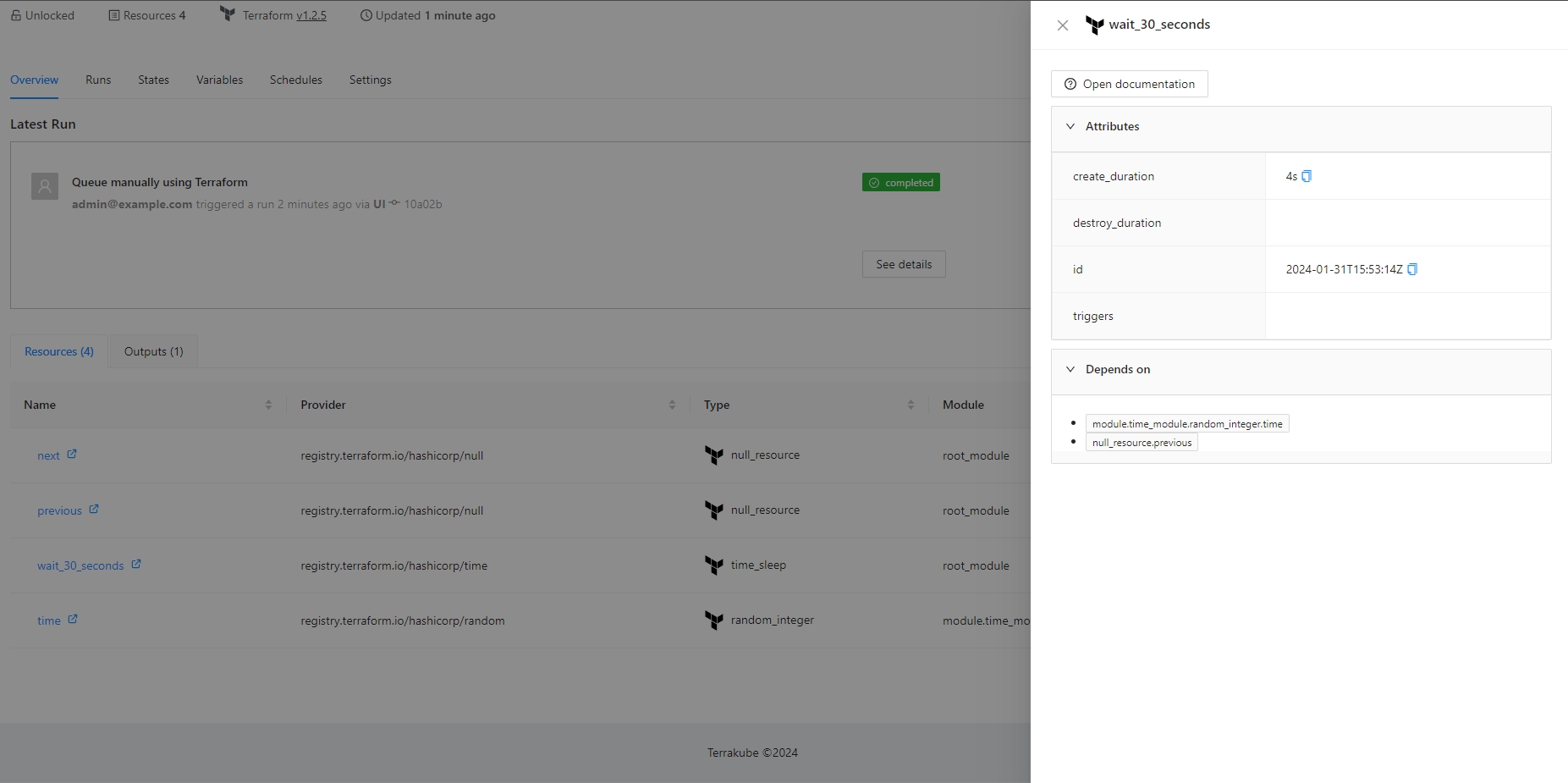
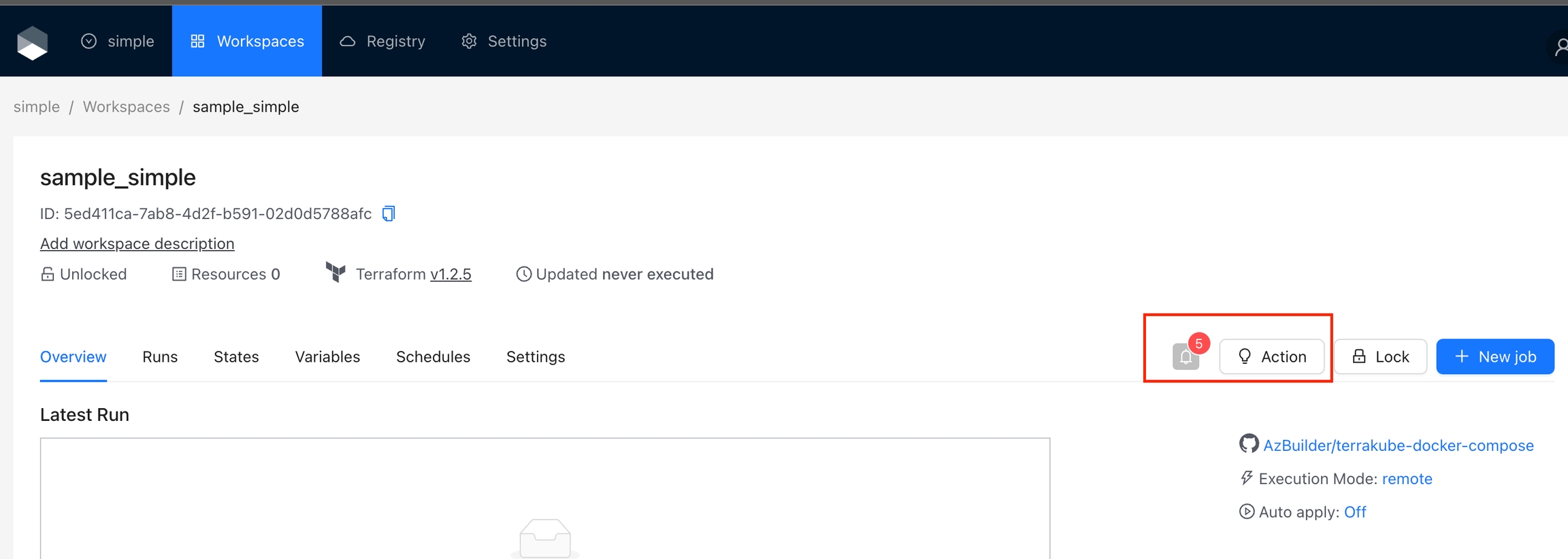
The visual state will also show some information if you click each element like the following:
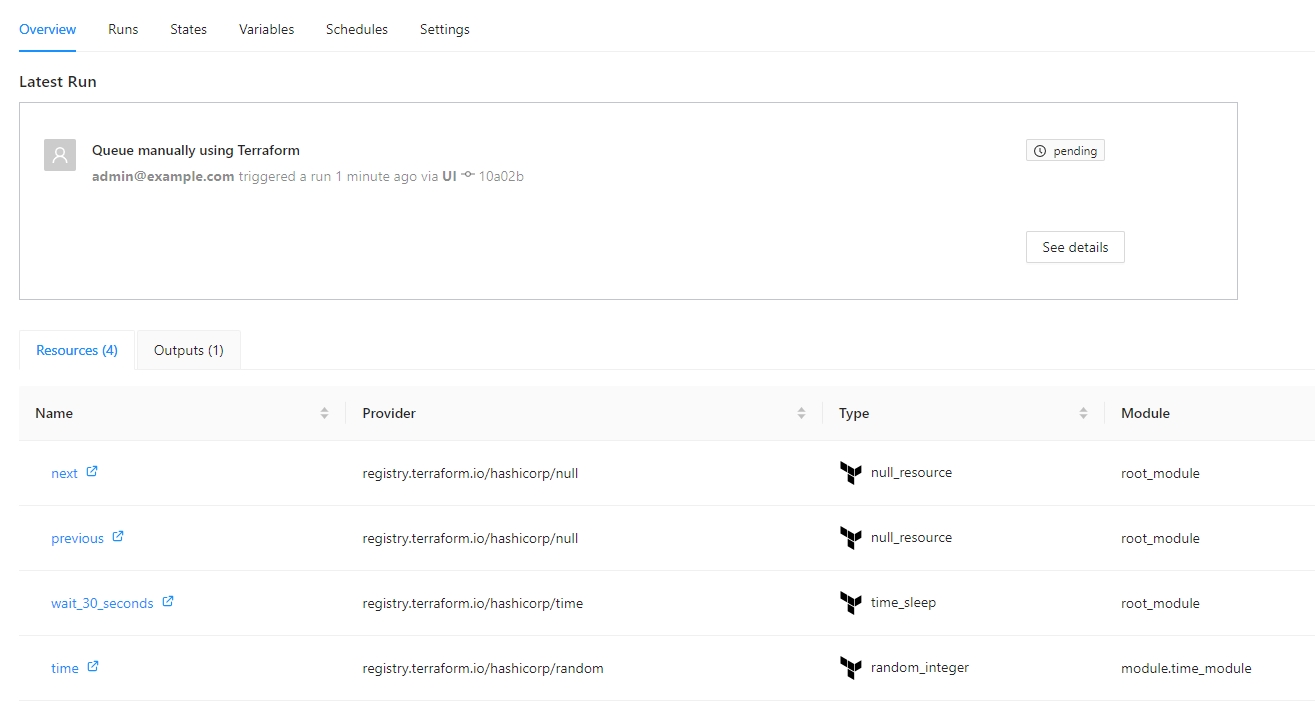
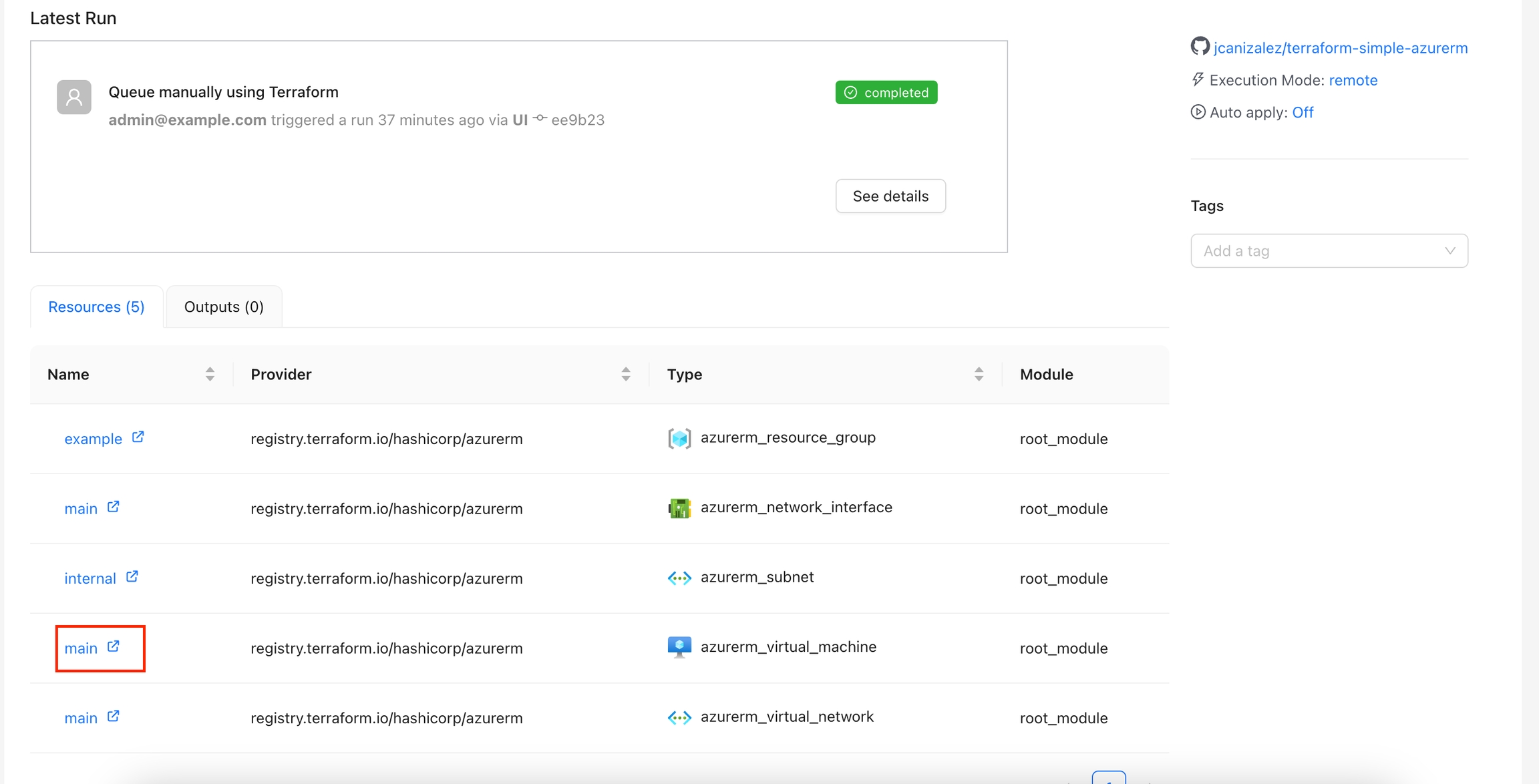
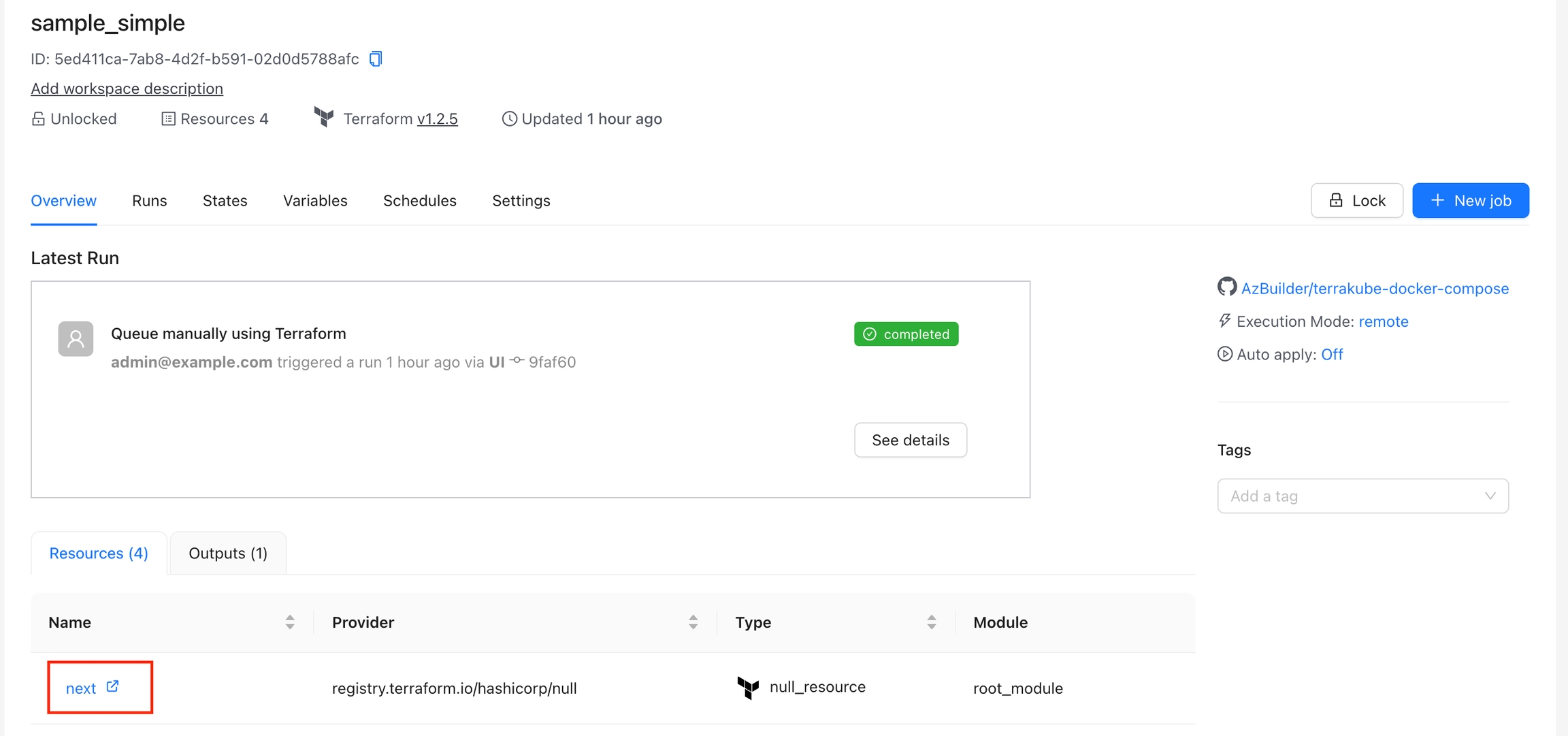
All the resources can be shown in the overview page inside the workspace:
If you click the resources you can check the information about each resouce like the folloing
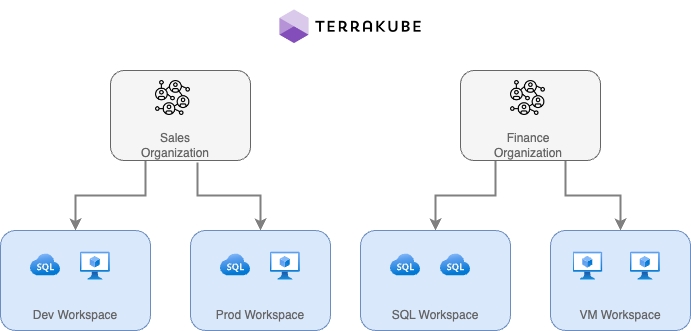
When working with Terraform at Enterprise level, you need to organize your infrastructure in different collections. Terrakube manages infrastructure collections with workspaces. A workspace contains everything Terraform needs to manage a given collection of infrastructure, so you can easily organize all your resources based in your requirements.
For example, you can create a workspace for dev environment and a different workspace for production. Or you can separate your workspaces based in your resource types, so you can create a workspace for all your SQL Databases and anothers workspace for all your VMS.
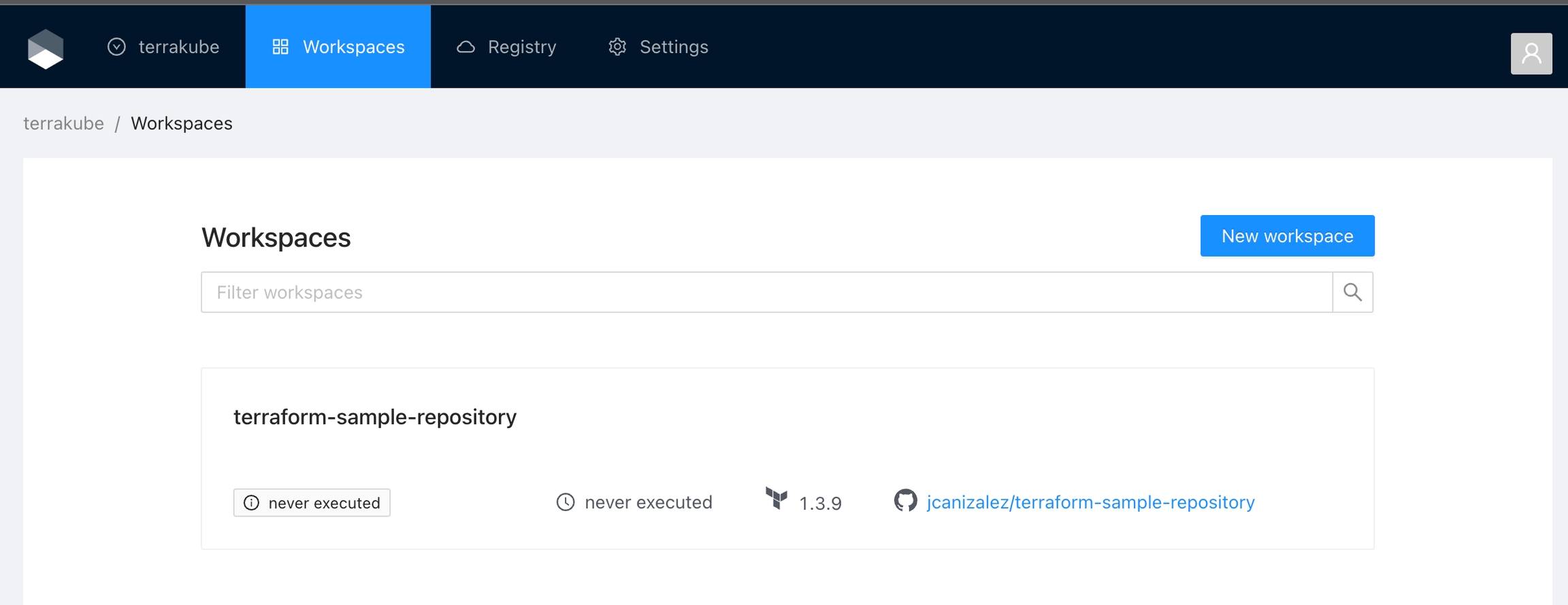
You can create unlimited workspaces inside each Terrakube Organization. In this section:
Manage Workspaces permission is required to perform this action, please check Team Management for more info.
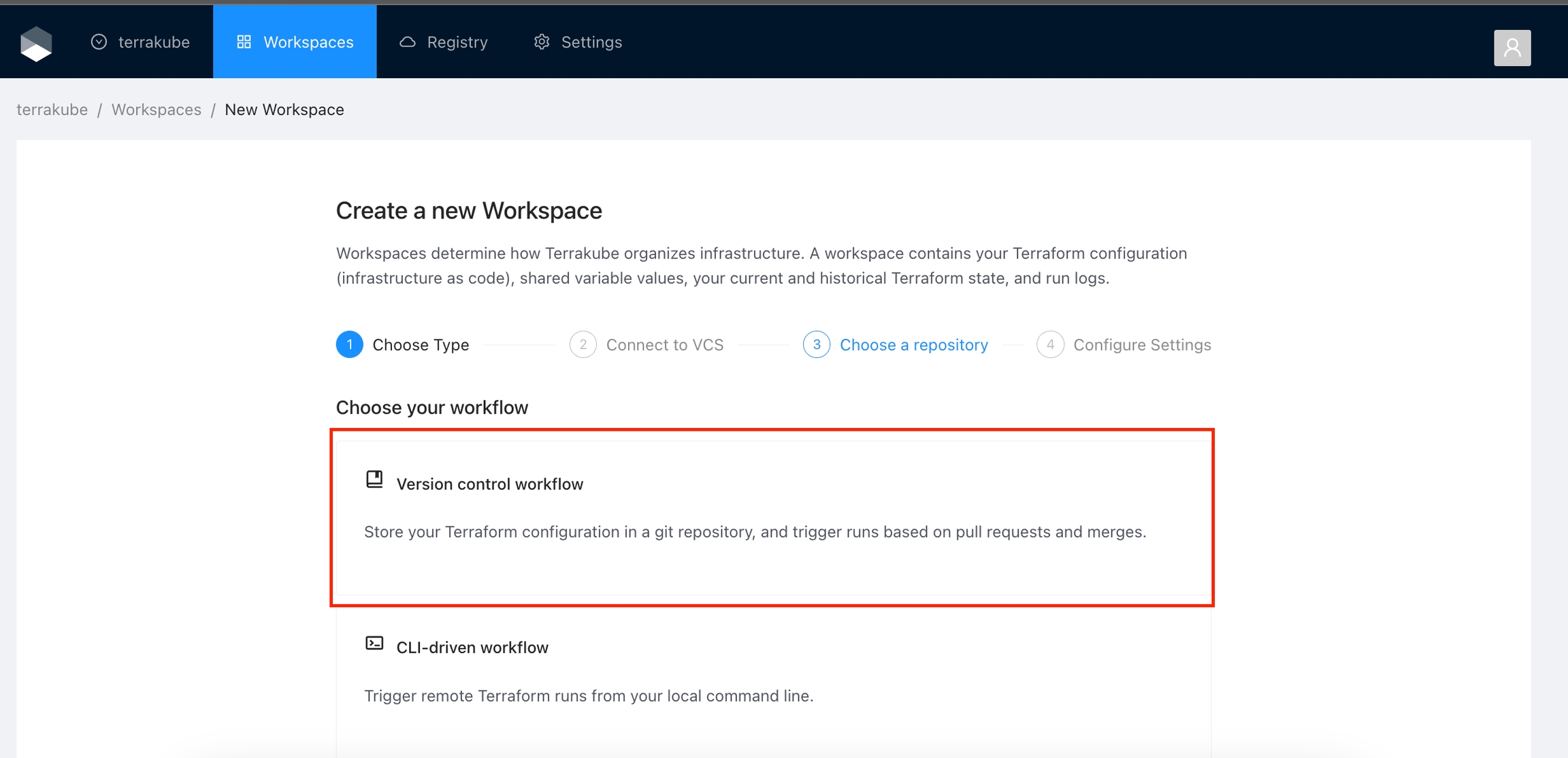
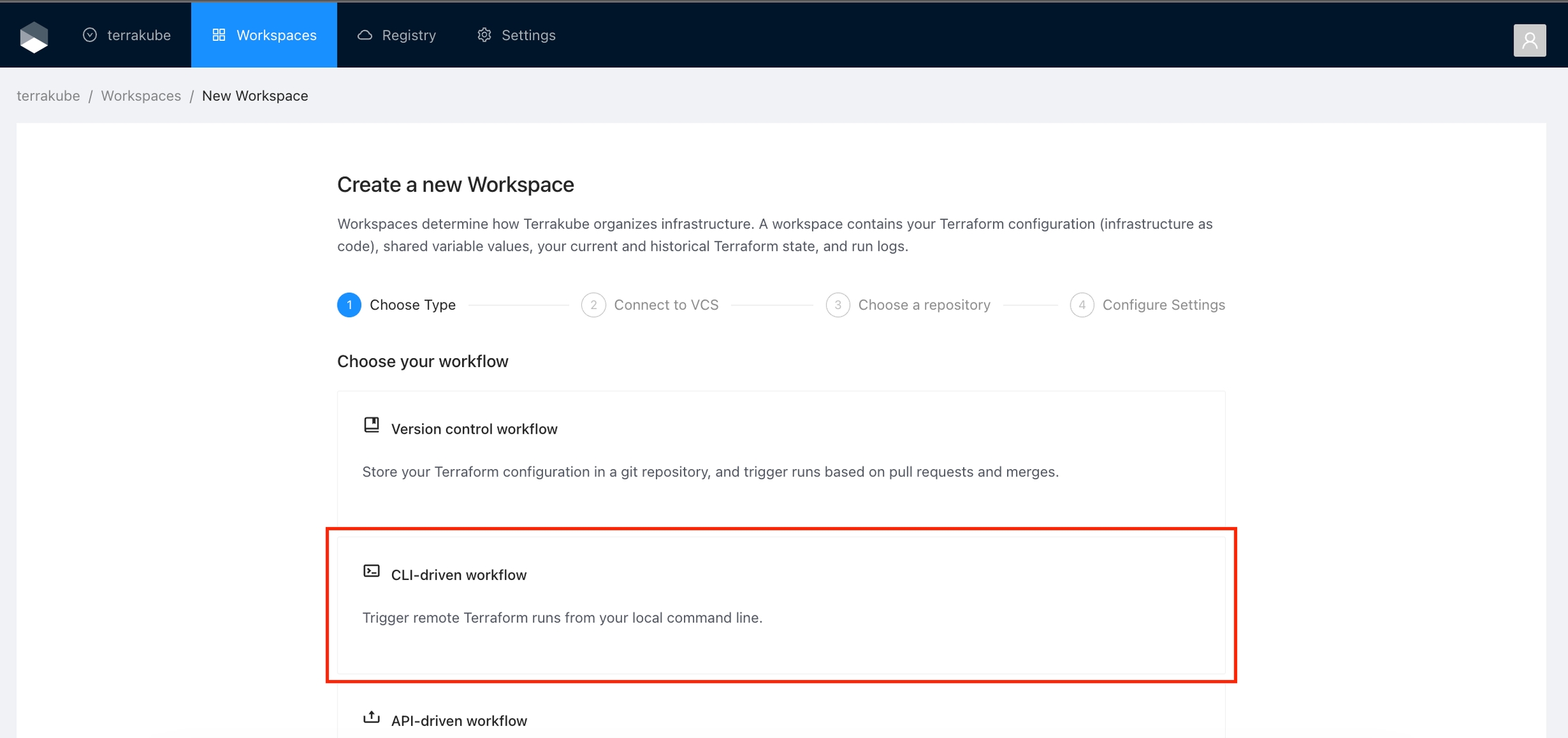
When creating a Workspace, Terrakube supports 3 workflows types and based on the selected workflow you will need to provide some parameters. Please refer to each workflow section for more reference.
Version Control workflow: Store your Terraform configuration in a git repository, and trigger runs based on pull requests and merges.
CLI-driven workflow: Trigger remote Terraform runs from your local command line.
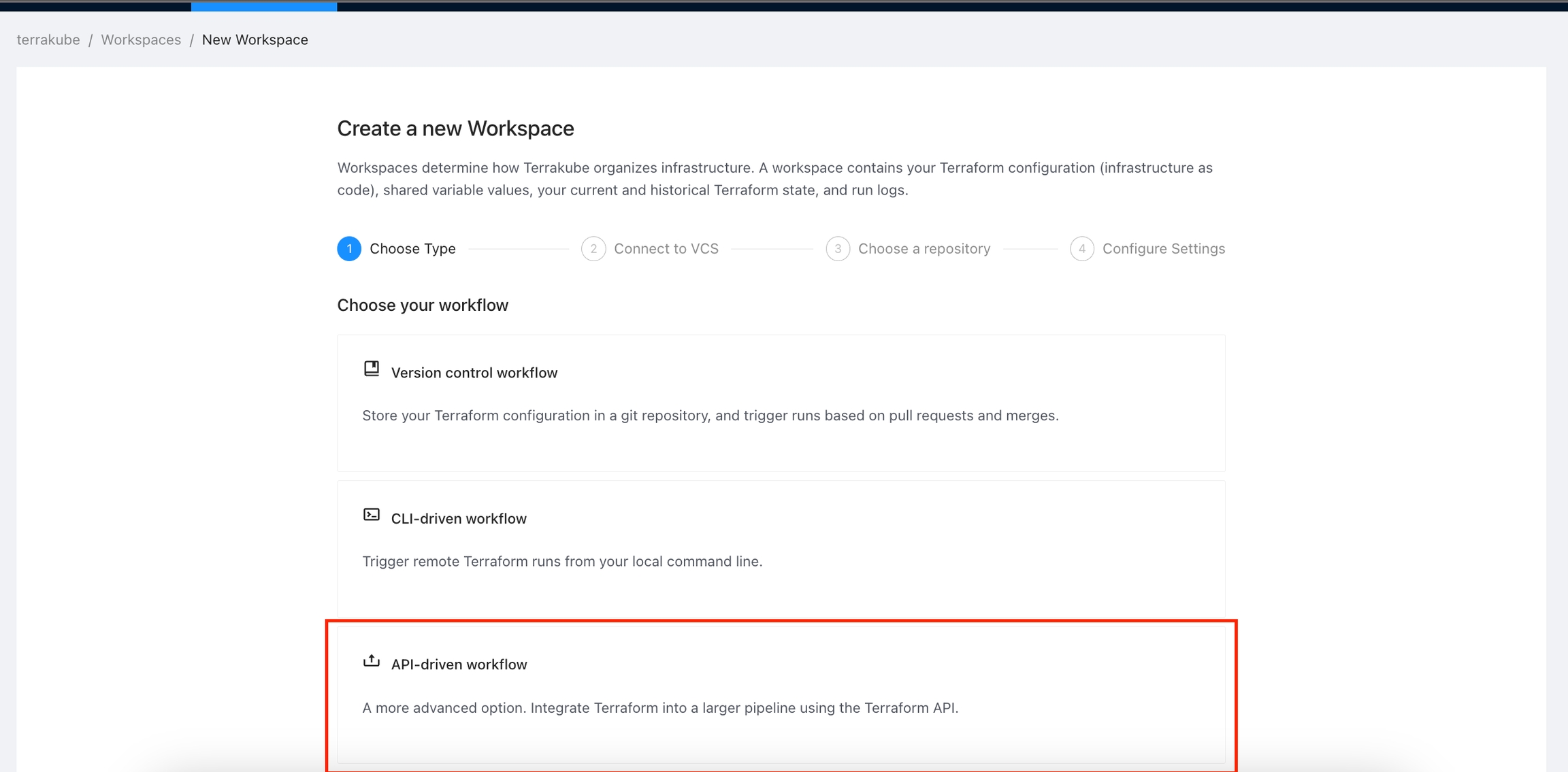
API-driven workflow: A more advanced option. Integrate Terraform into a larger pipeline using the Terrakube API.
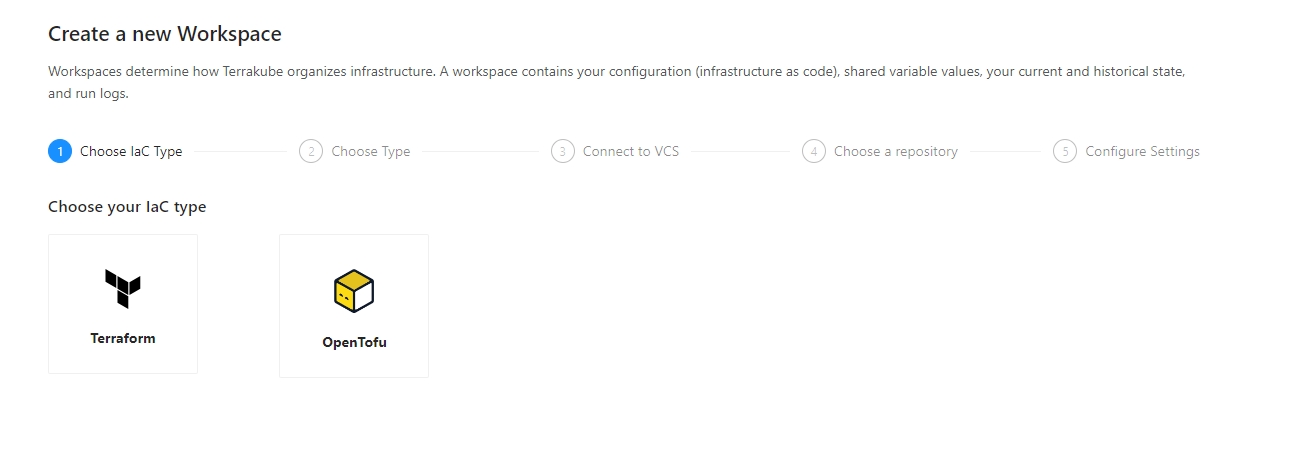
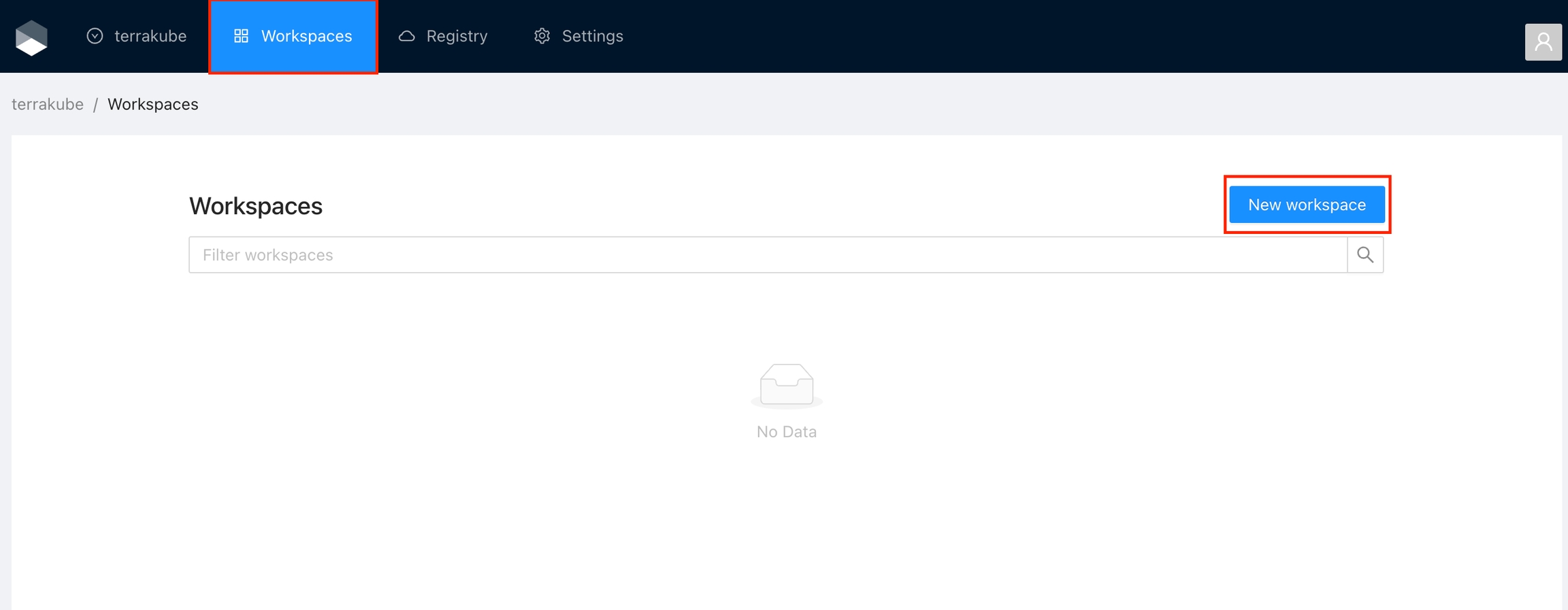
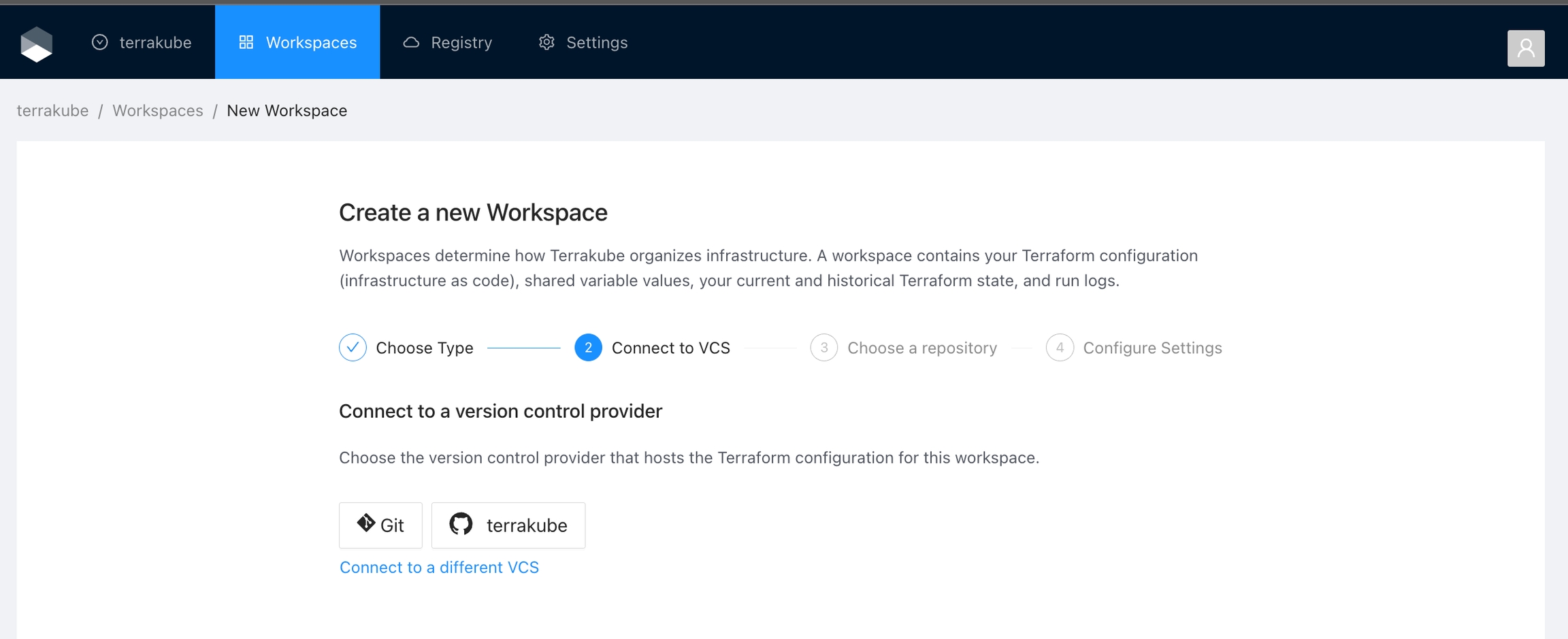
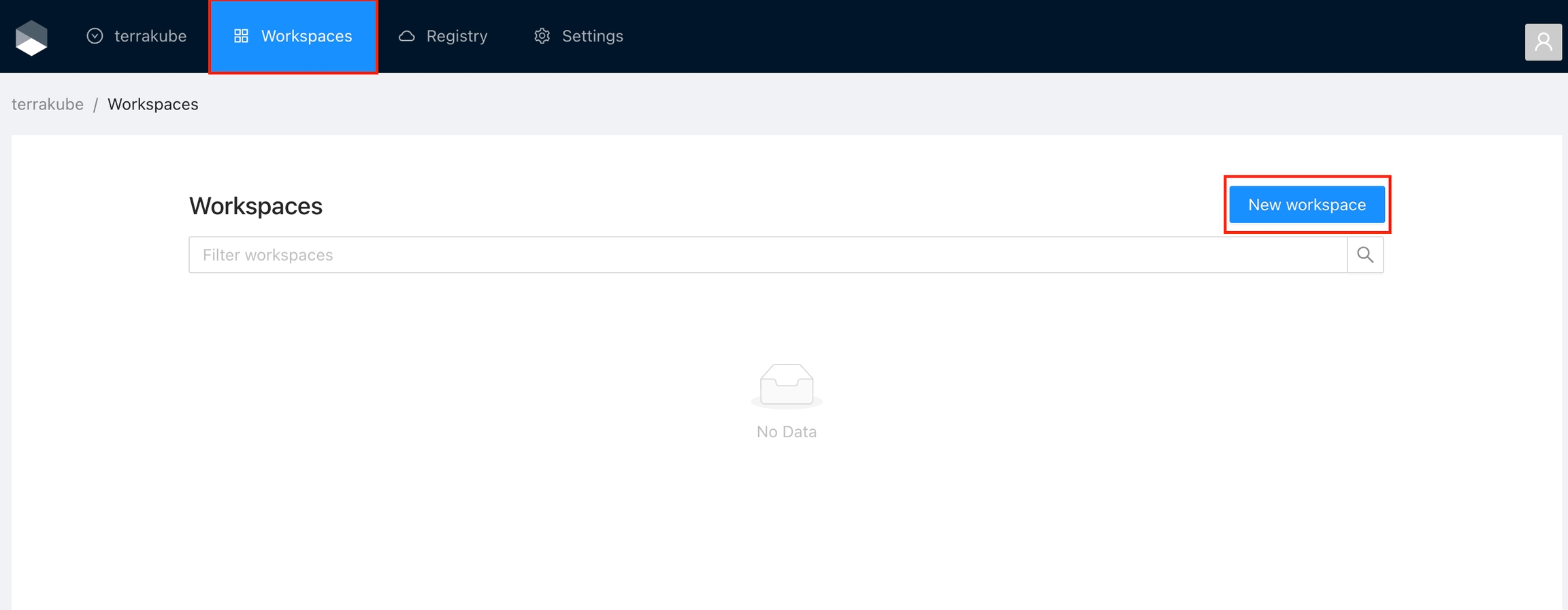
Click Workspaces in the main menu and then click the New workspace button
Select the IaC type for now we support terraform and open tofu
Choose the Version control workflow
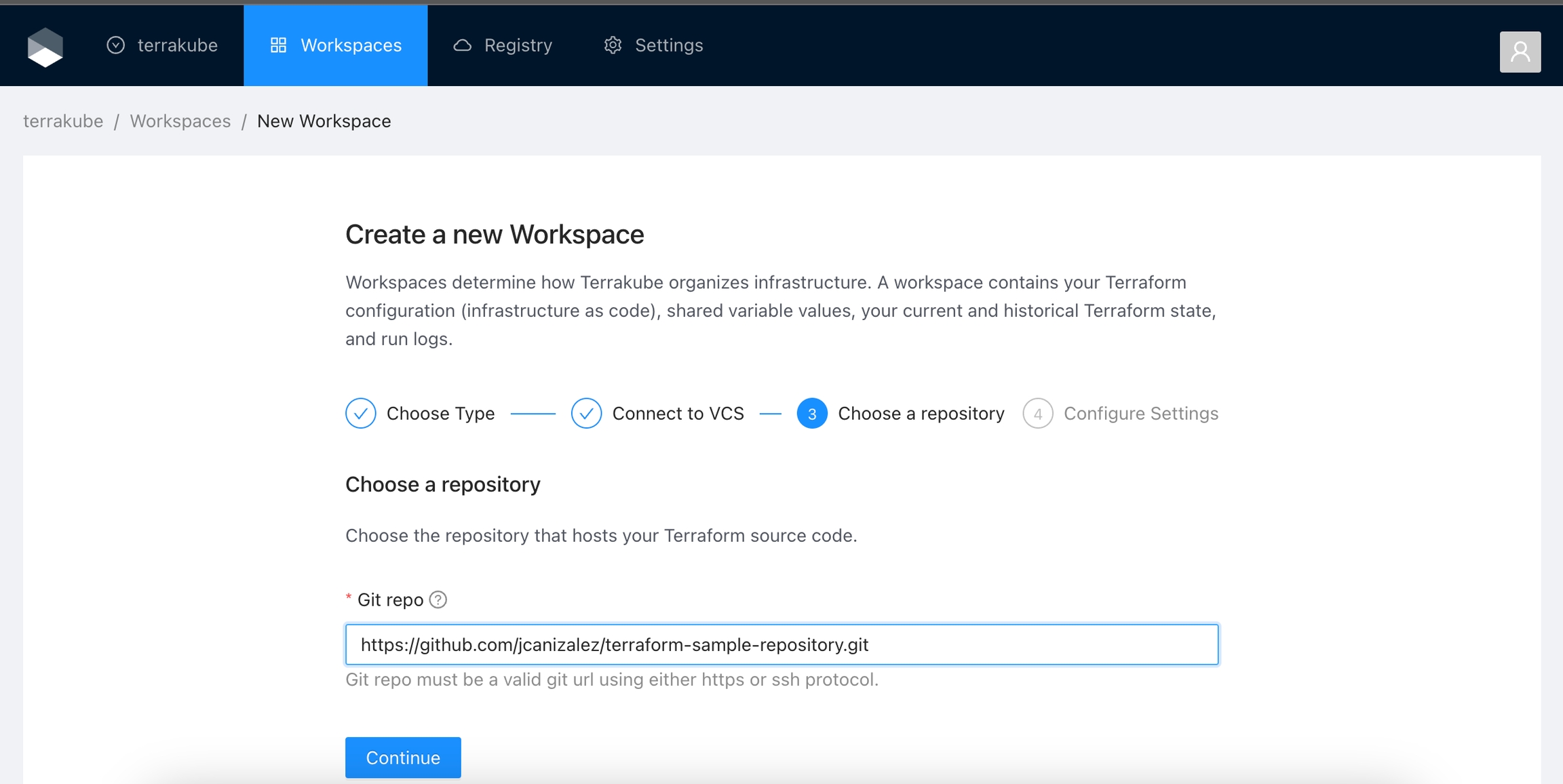
Select an existing version control provider or click Connect to a different VCS to configure a new one. See VCS Providers for more details.
Provide the git repository URL and click the Continue button.
If you want to connect to a private git repo using SSH Keys you will need to provide the url in ssh format. Example git@github.com:jcanizalez/terraform-sample-repository.git. For more information see SSH
Configure the workspace settings.
Workspace Name
The name of your workspace is unique and used in tools, routing, and UI. Dashes, underscores, and alphanumeric characters are permitted.
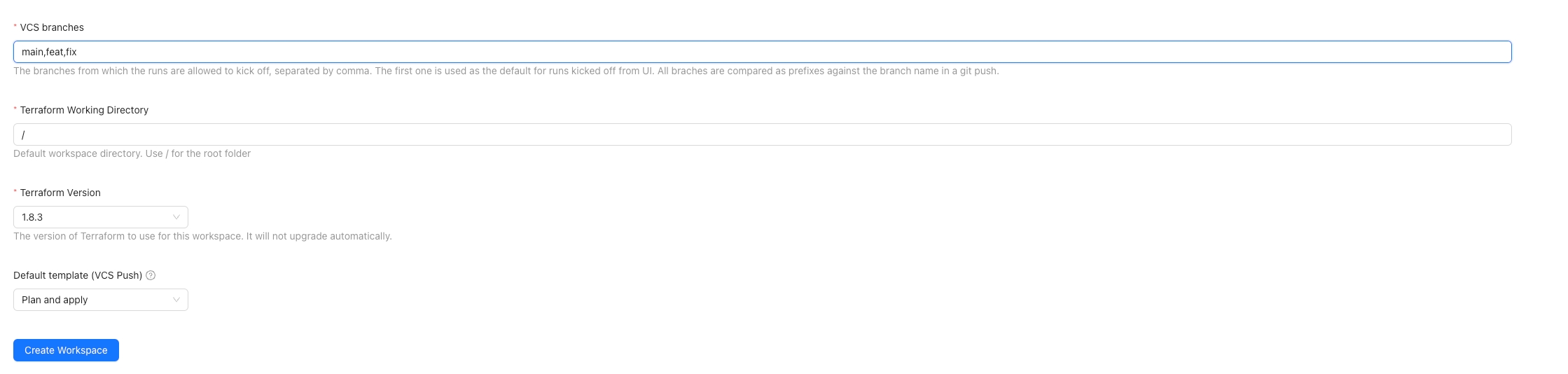
VCS branch
A list of branches separated by comma that jobs are allowed to kicked off from VCS webhook. This is not used for CLI workflow.
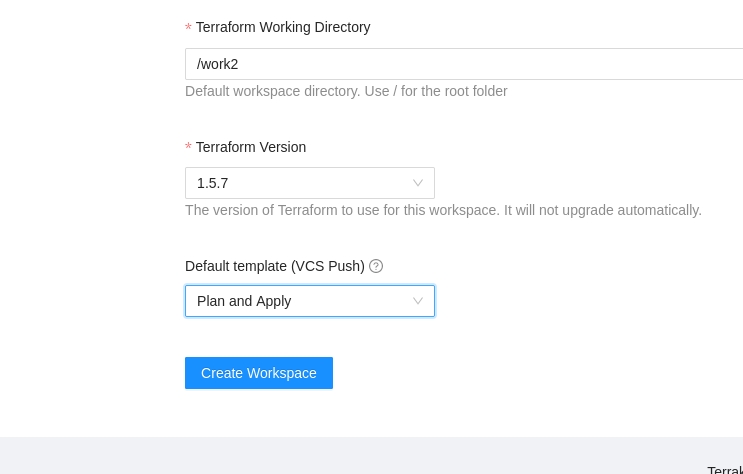
Terraform Working Directory
Default workspace directory. Use / for the root folder
Terraform Version
Once you fill the settings click the Create Workspace button.
When using a VCS workflow you can select which branches, folder and action (aka, Default template (VCS push)) the runs will be triggered from when a git push action happens.
The VCS branches accepts a list of branches separated by comma, the first in the list is used as the default for the runs kicked off from UI. The branches are compared as prefixes against the branch included in the payload sent from VCS provider.
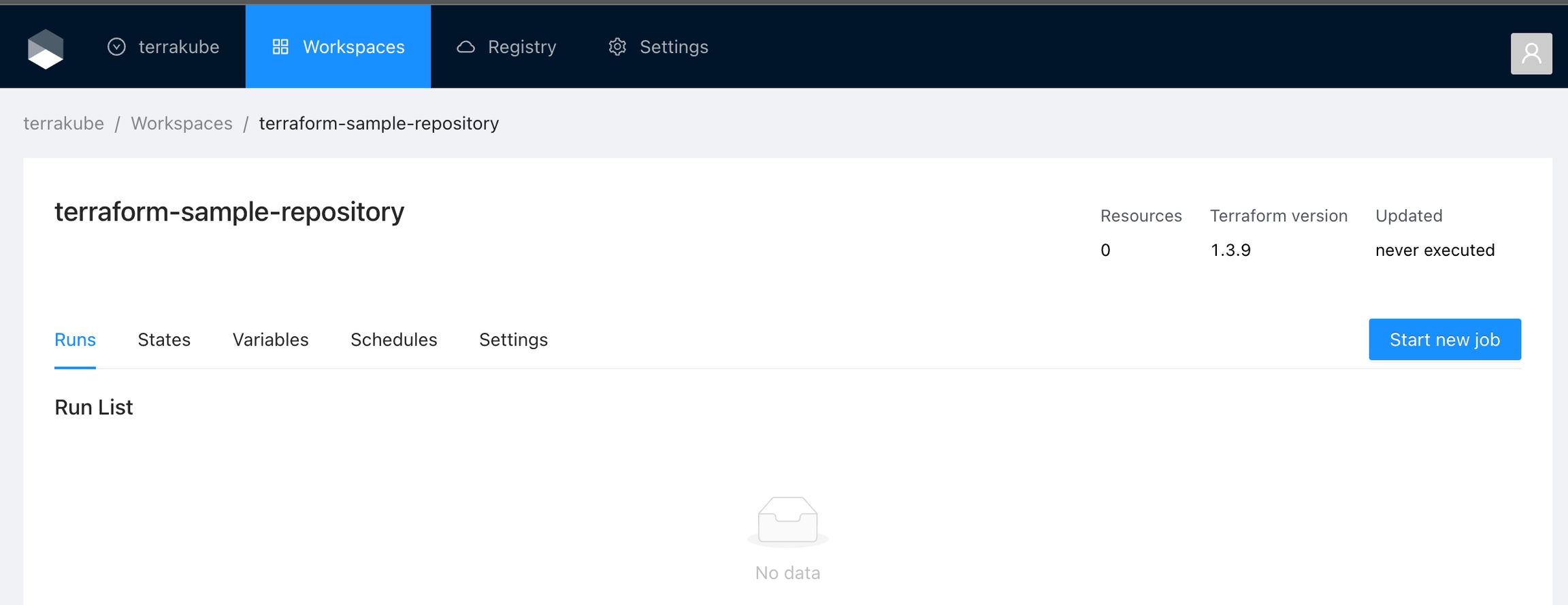
You will be redirected to the Workspace page
And if you navigate to the Workspace menu, you will see the workspace in the Workspaces list
Once you create your workspace, Terrakube sets up a webhook with your VCS. This webhook runs a job based on the selected template every time you push new changes to the set workspace branches. However, this feature does not work yet with Azure DevOps VCS provider.
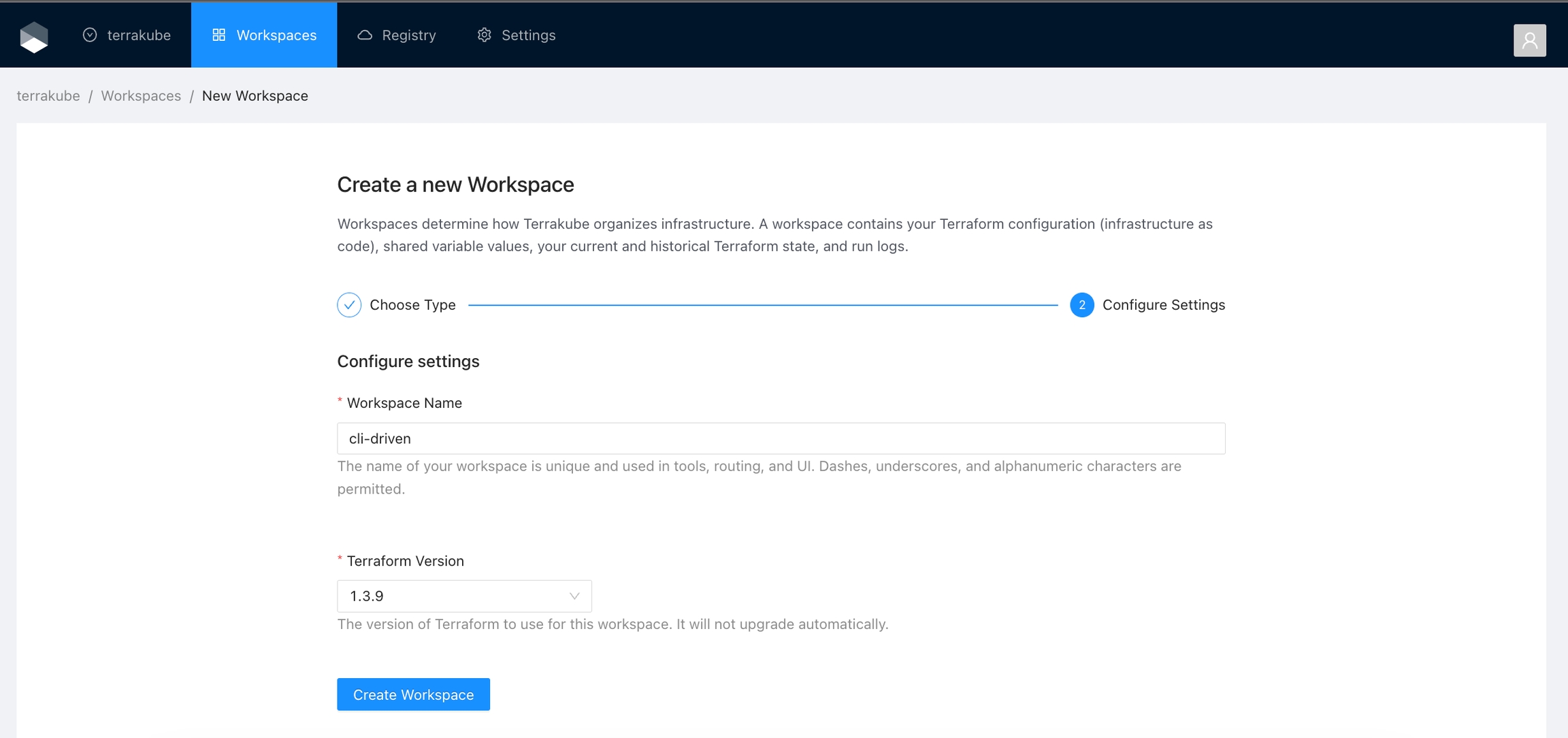
Click Workspaces in the main menu and then click the New workspace button
Choose the CLI-driven workflow
Configure the workspace settings.
Workspace Name
The name of your workspace is unique and used in tools, routing, and UI. Dashes, underscores, and alphanumeric characters are permitted.
Terraform Version
Once you fill the settings click the Create Workspace button.
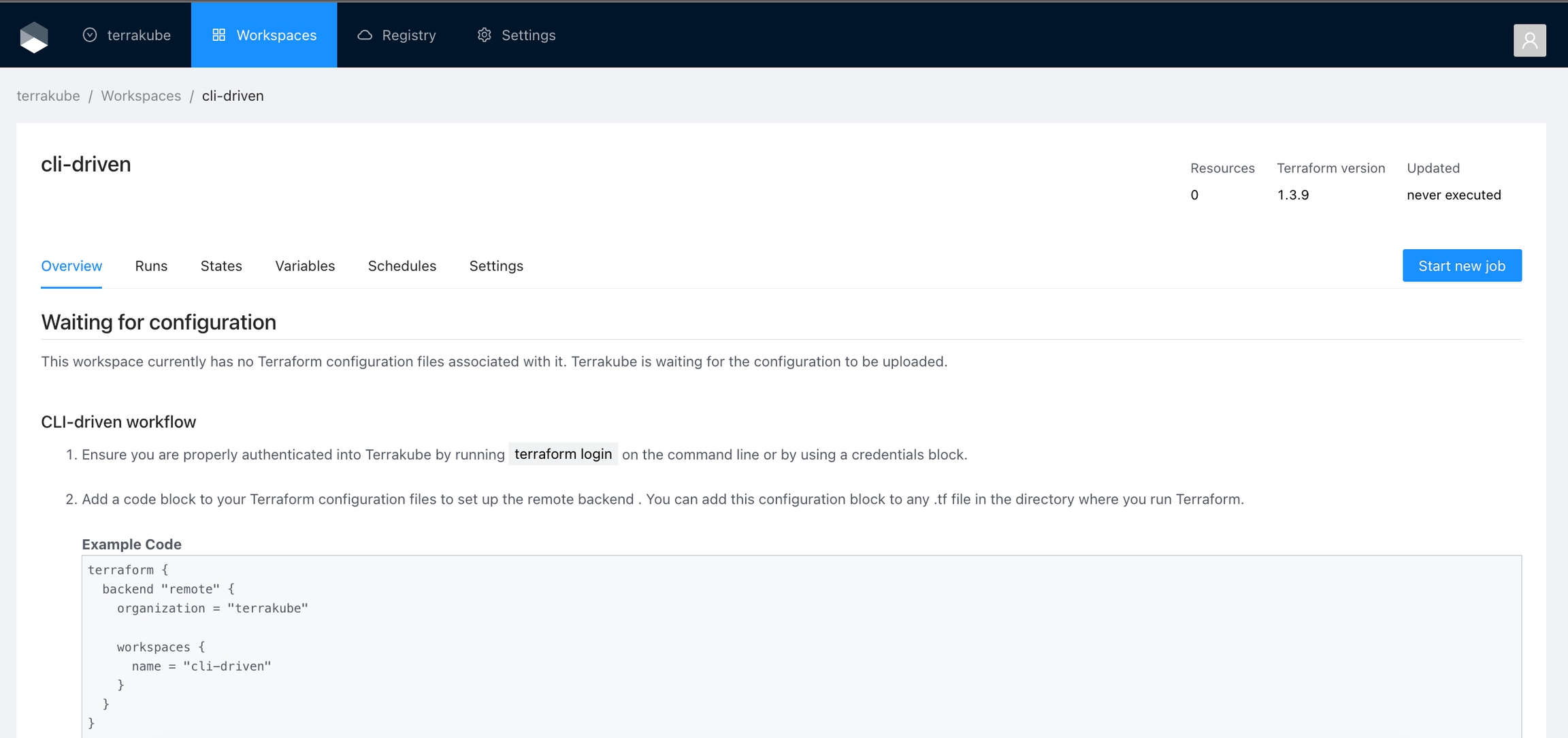
You will be redirected to the Workspace page.
The overview page for CLI-driven workspaces show the step to connect to the workspace using the Terraform CLI. For more details see CLI-driven Workflow
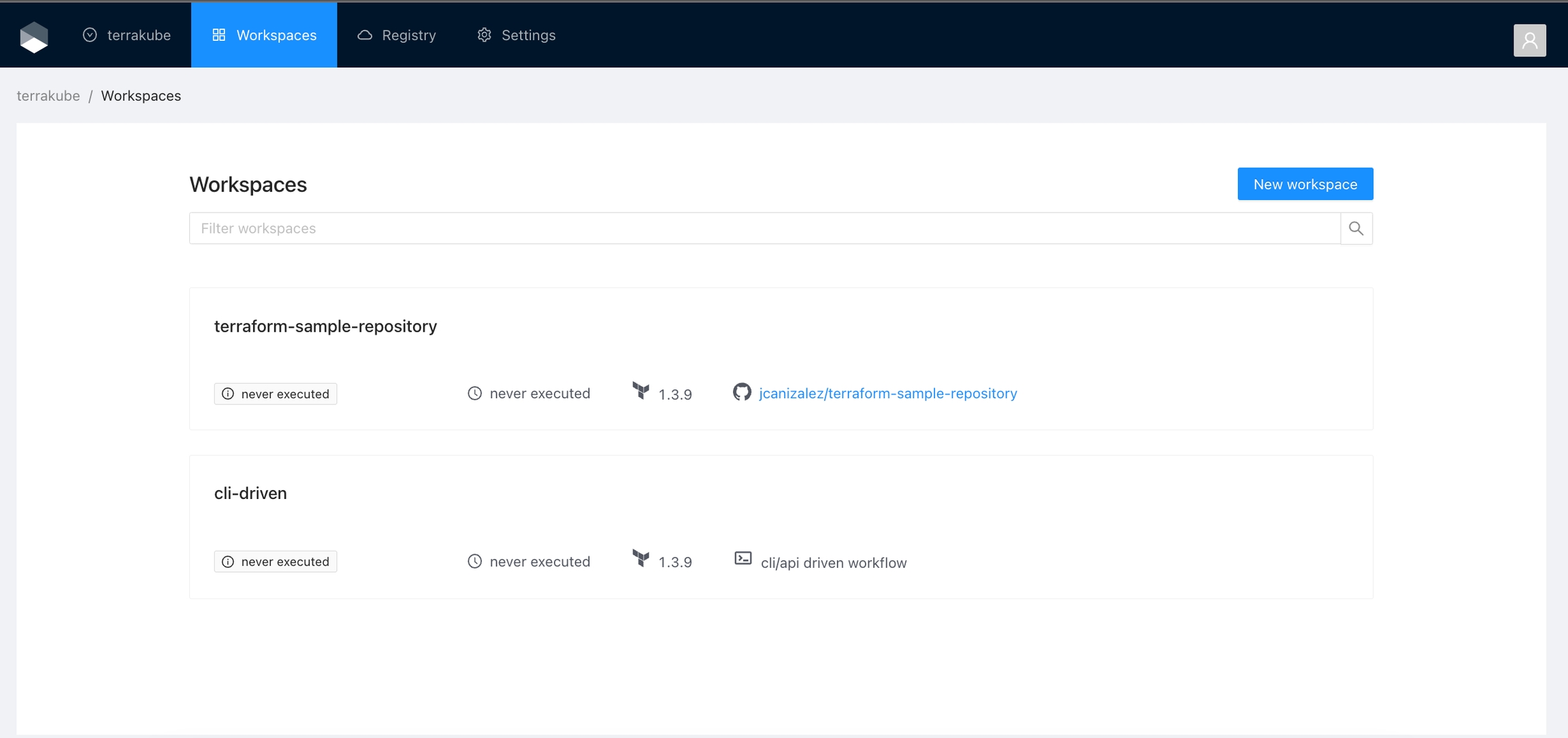
And if you navigate to the Workspace menu you will see the workspace in the Workspaces list
Click Workspaces in the main menu and then click the New workspace button
Choose the API-driven workflow
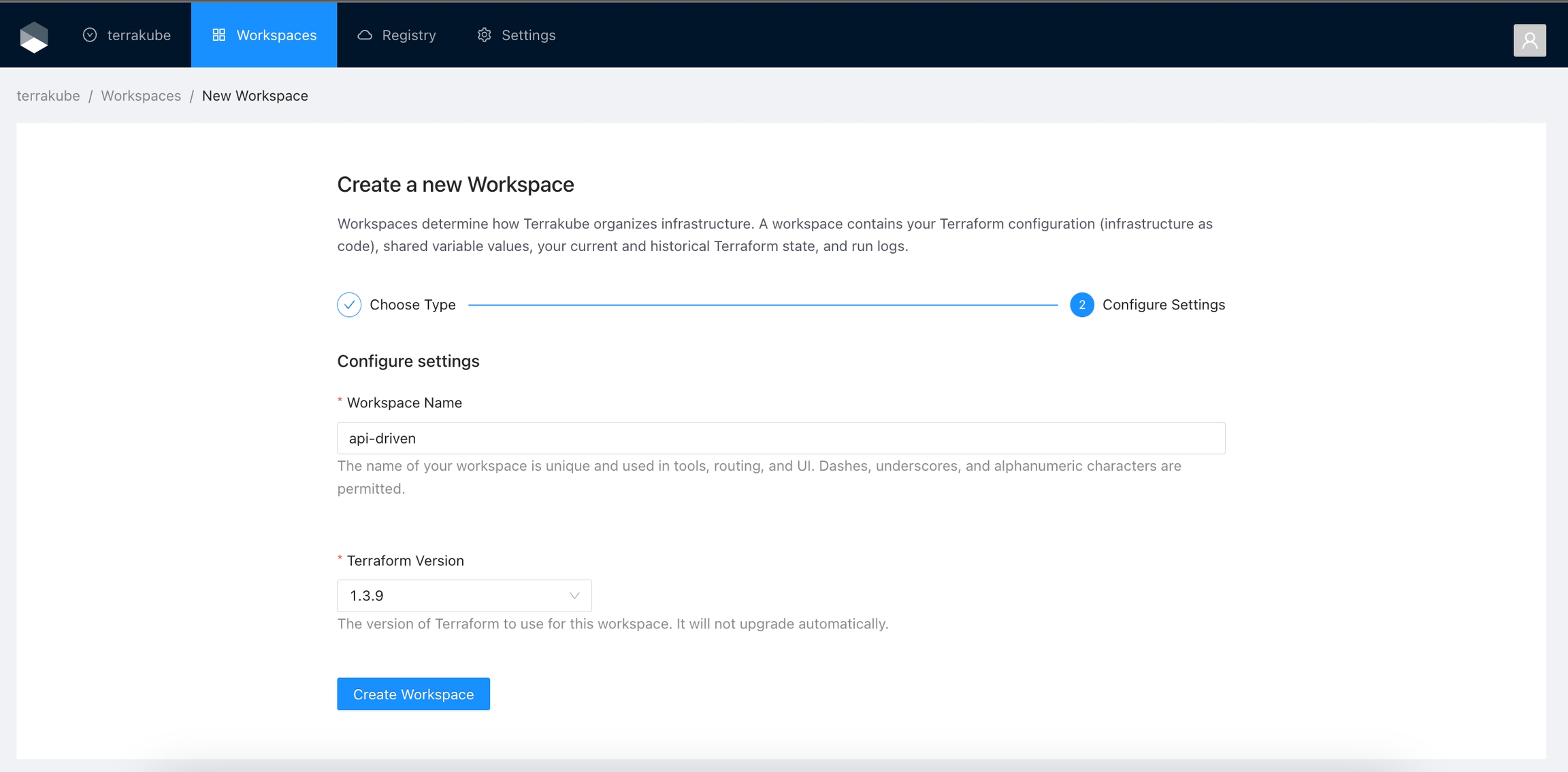
Configure the workspace settings.
Workspace Name
The name of your workspace is unique and used in tools, routing, and UI. Dashes, underscores, and alphanumeric characters are permitted.
Terraform Version
Once you fill the settings click the Create Workspace button.
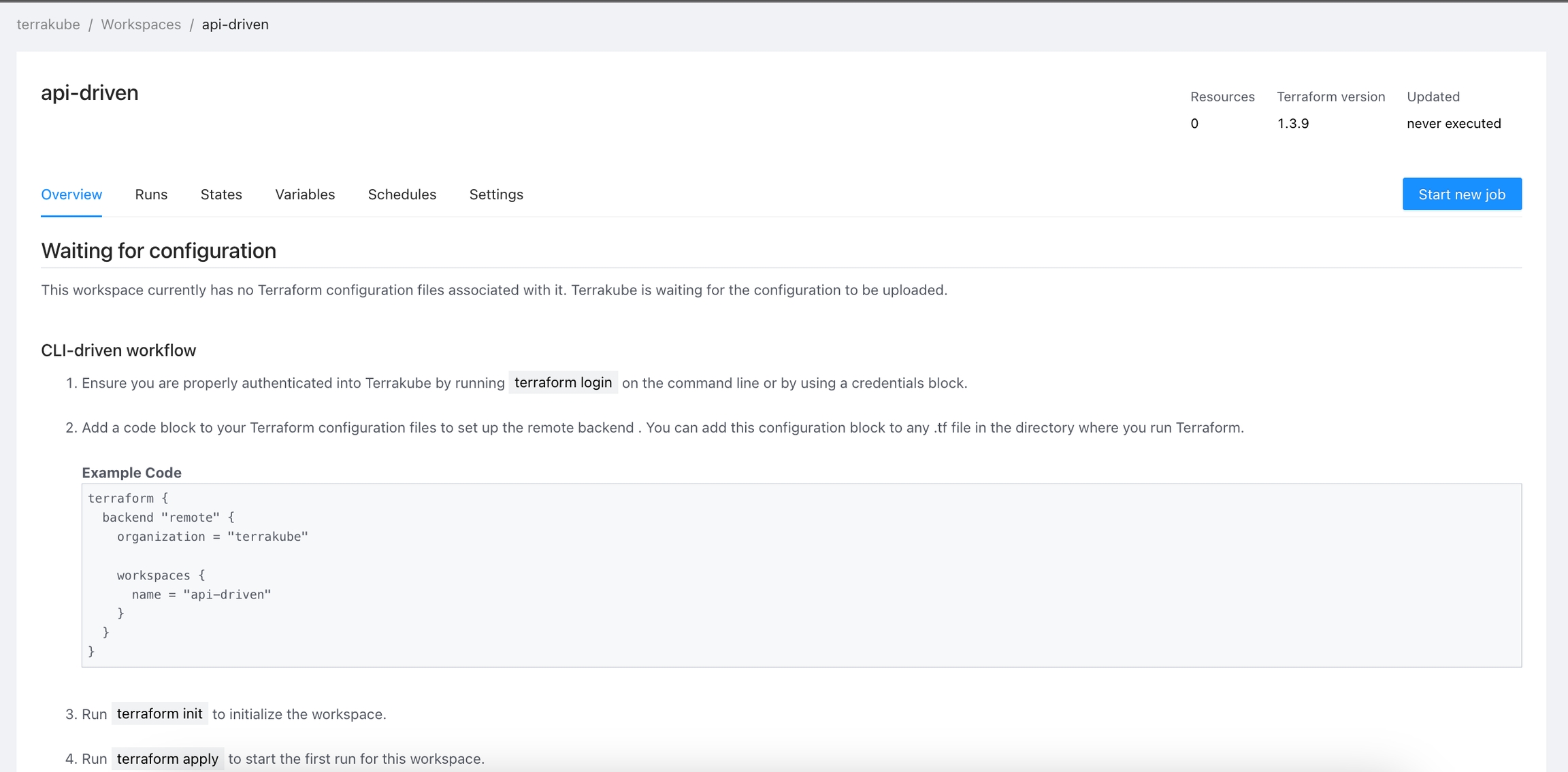
ou will be redirected to the Workspace page.
For more details how to use the Terrakube API. See API-driven Workflow
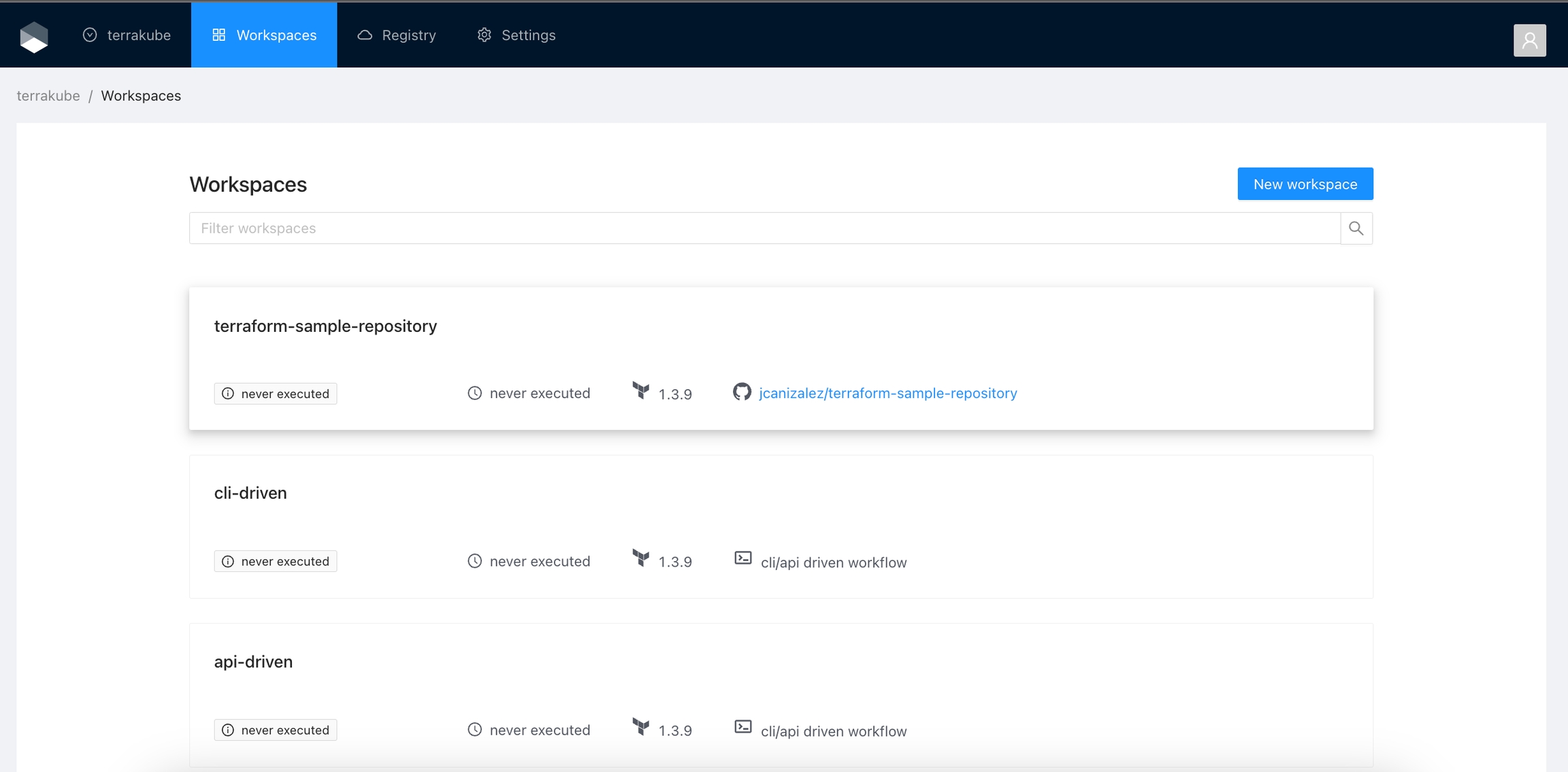
And if you navigate to the Workspace menu you will see the workspace in the Workspaces list
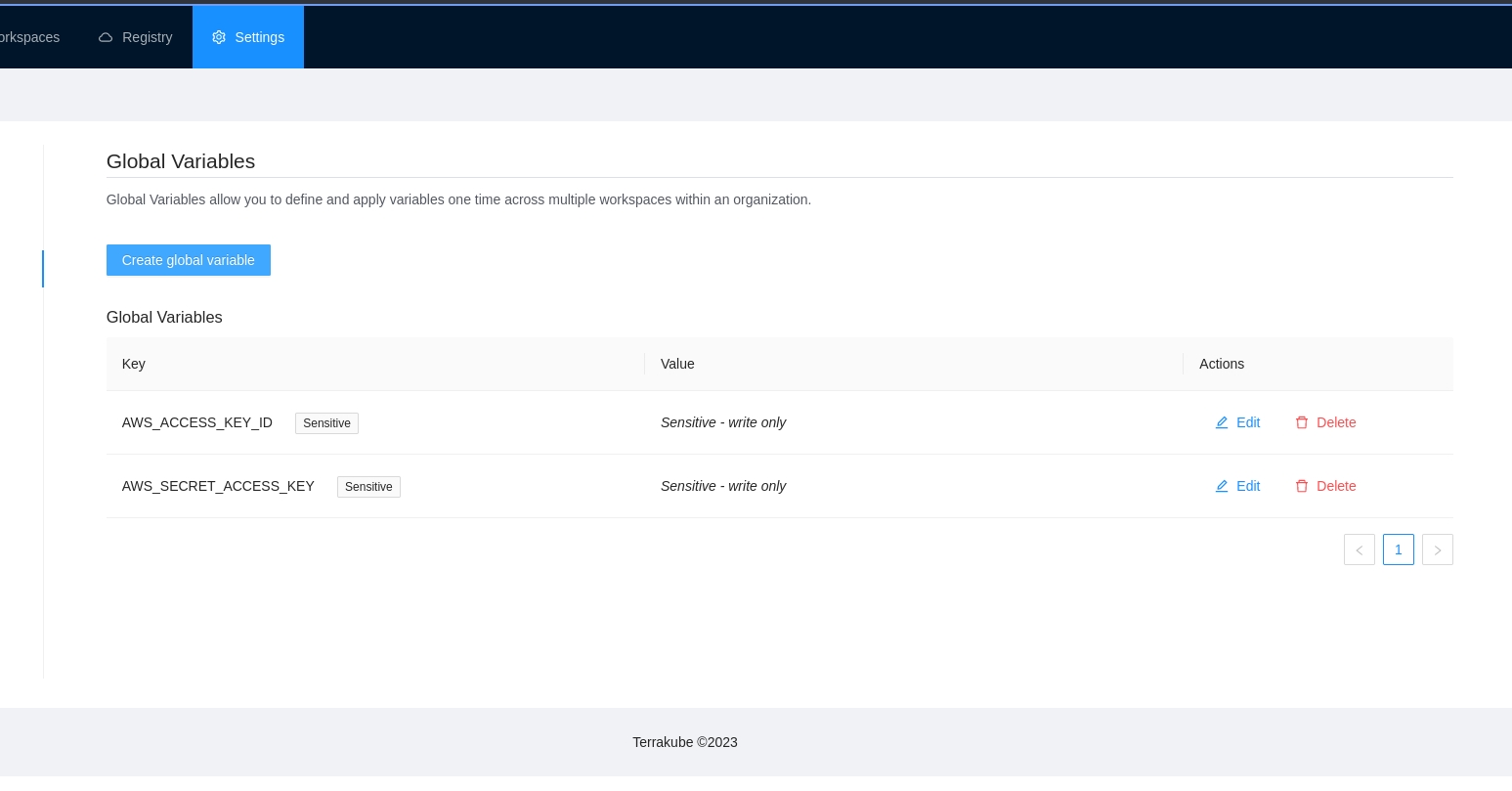
Terrakube workspace variables let you customize configurations and store information like static provider credentials. You can also reference this variables inside your Templates.
You can set variables specifically for each workspace or you can create Global Variables to reuse the same variables across multiple workspaces.
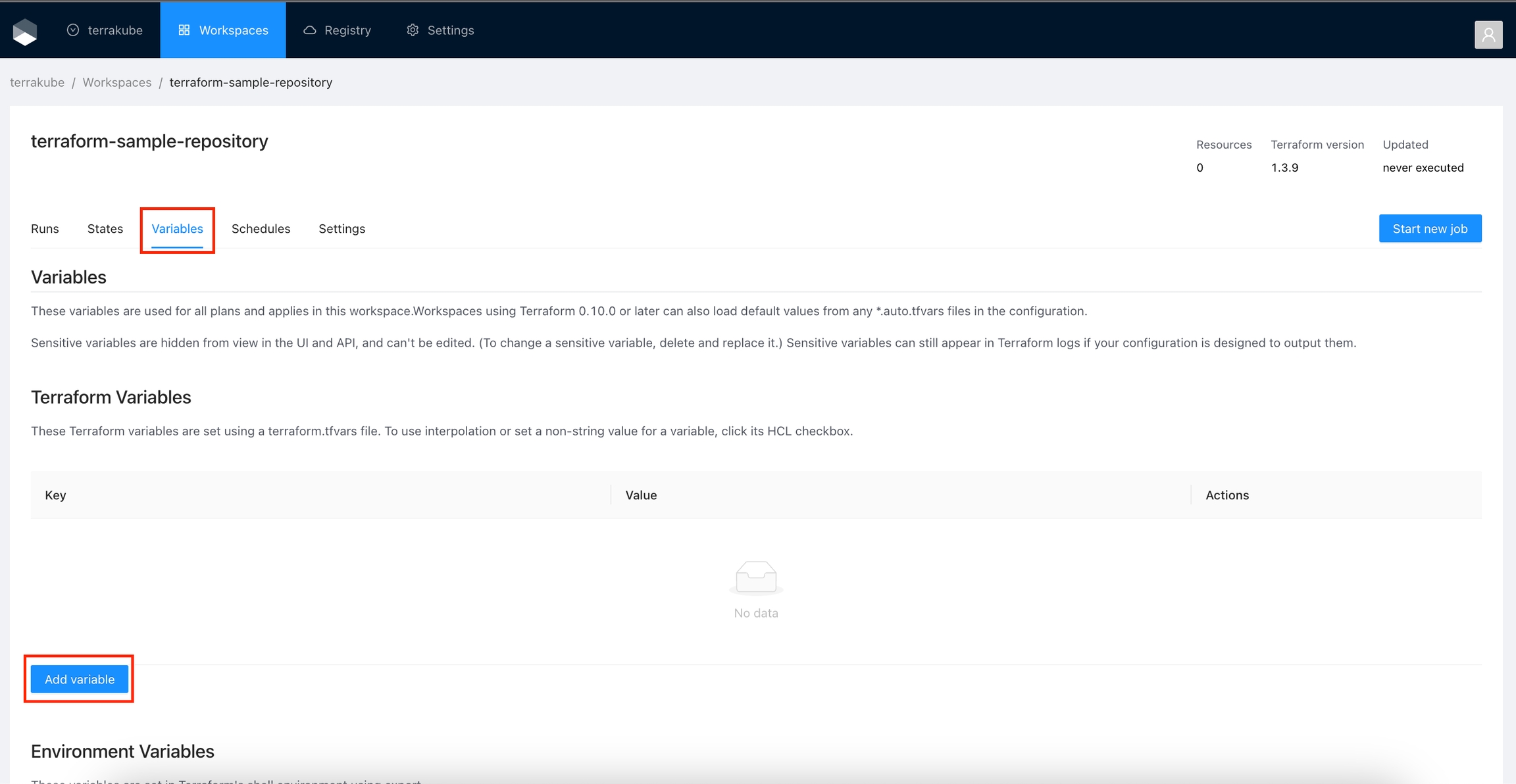
To view and manage a workspace's variables, go to the workspace and click the Variables tab.
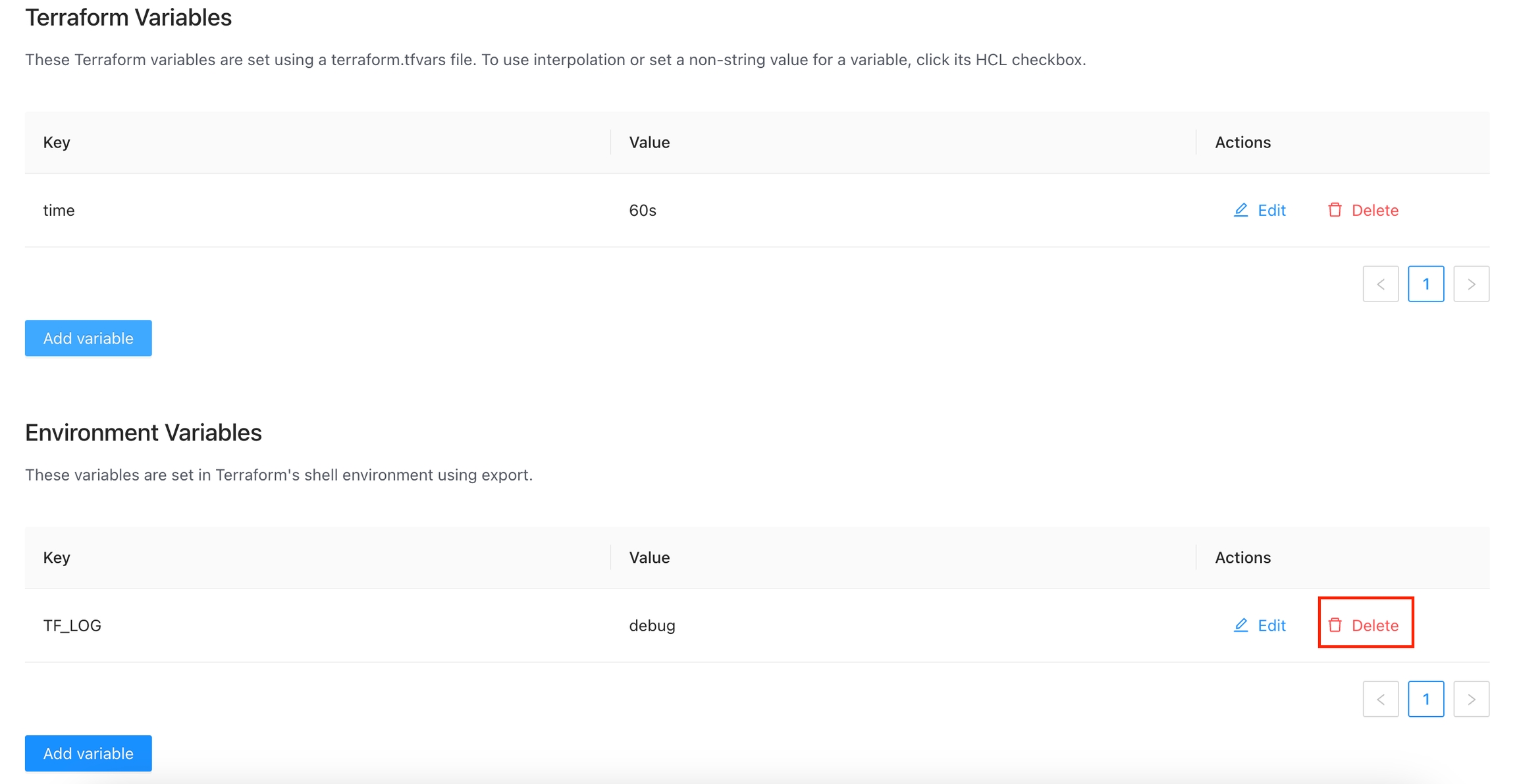
The Variables page appears, showing all workspace-specific variables. This is where you can add, edit, and delete workspace-specific variables.
There are 2 kinds of Variables:
These Terraform variables are set using a terraform.tfvars file. To use interpolation or set a non-string value for a variable, click its HCL checkbox.
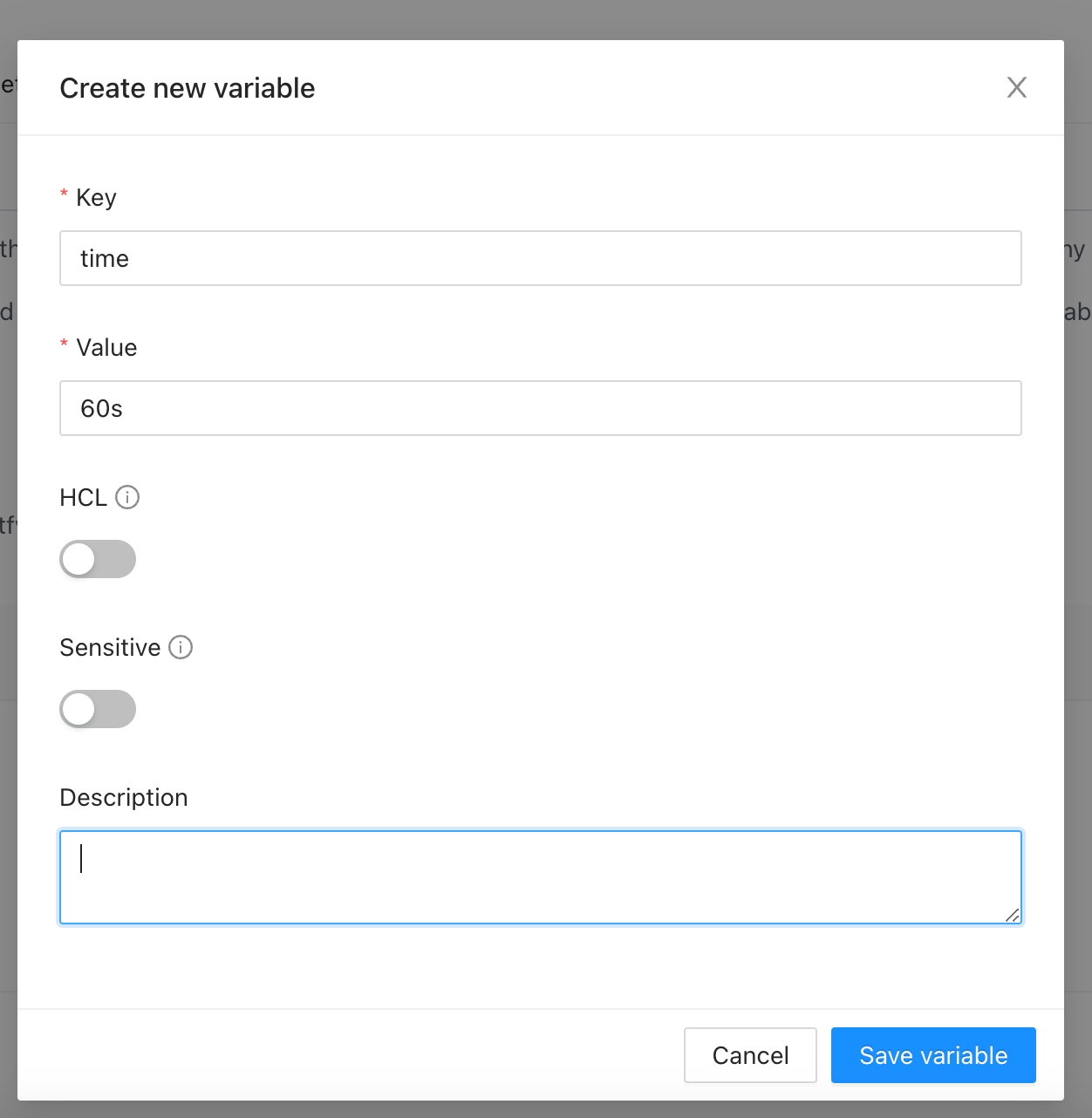
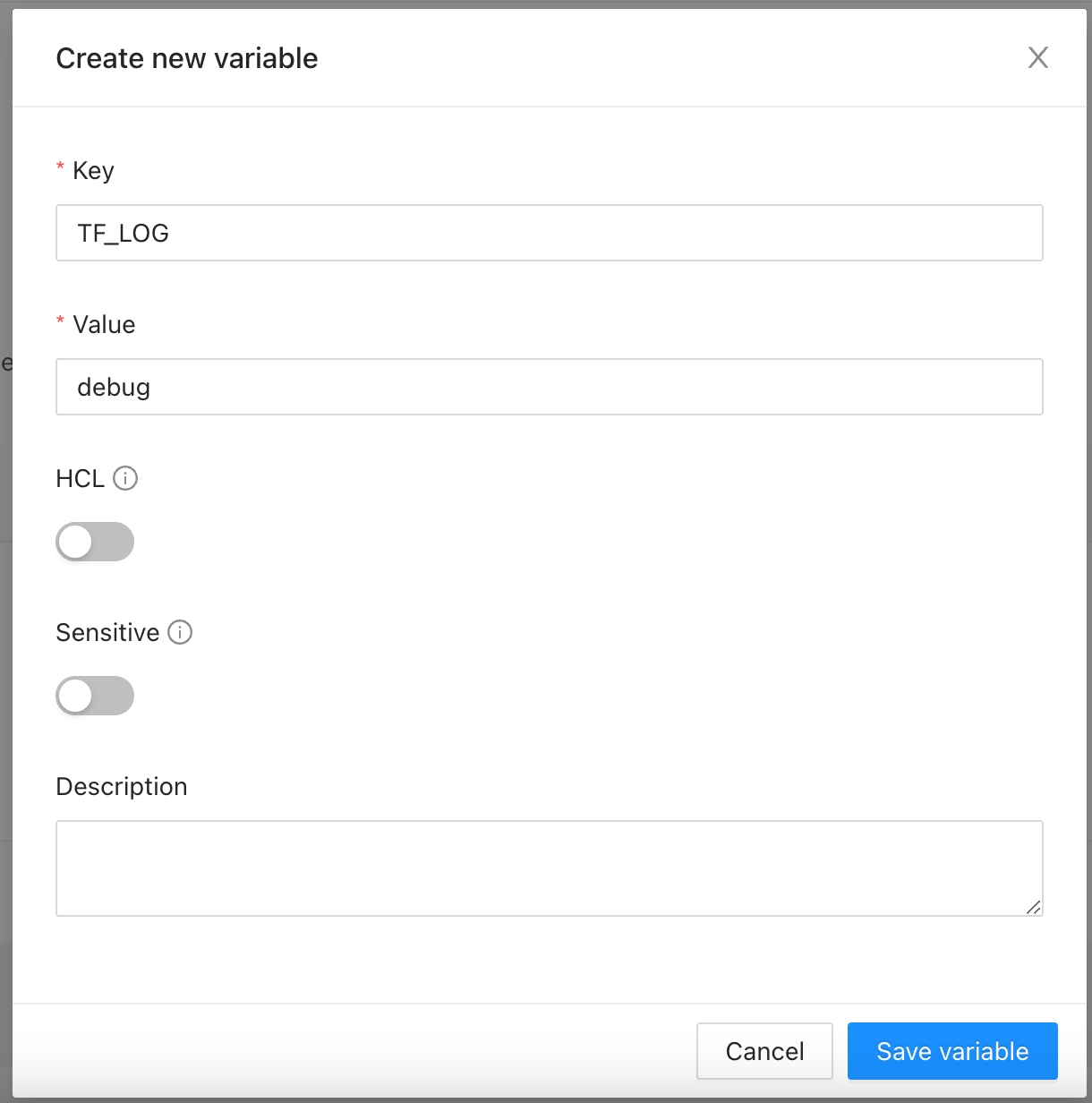
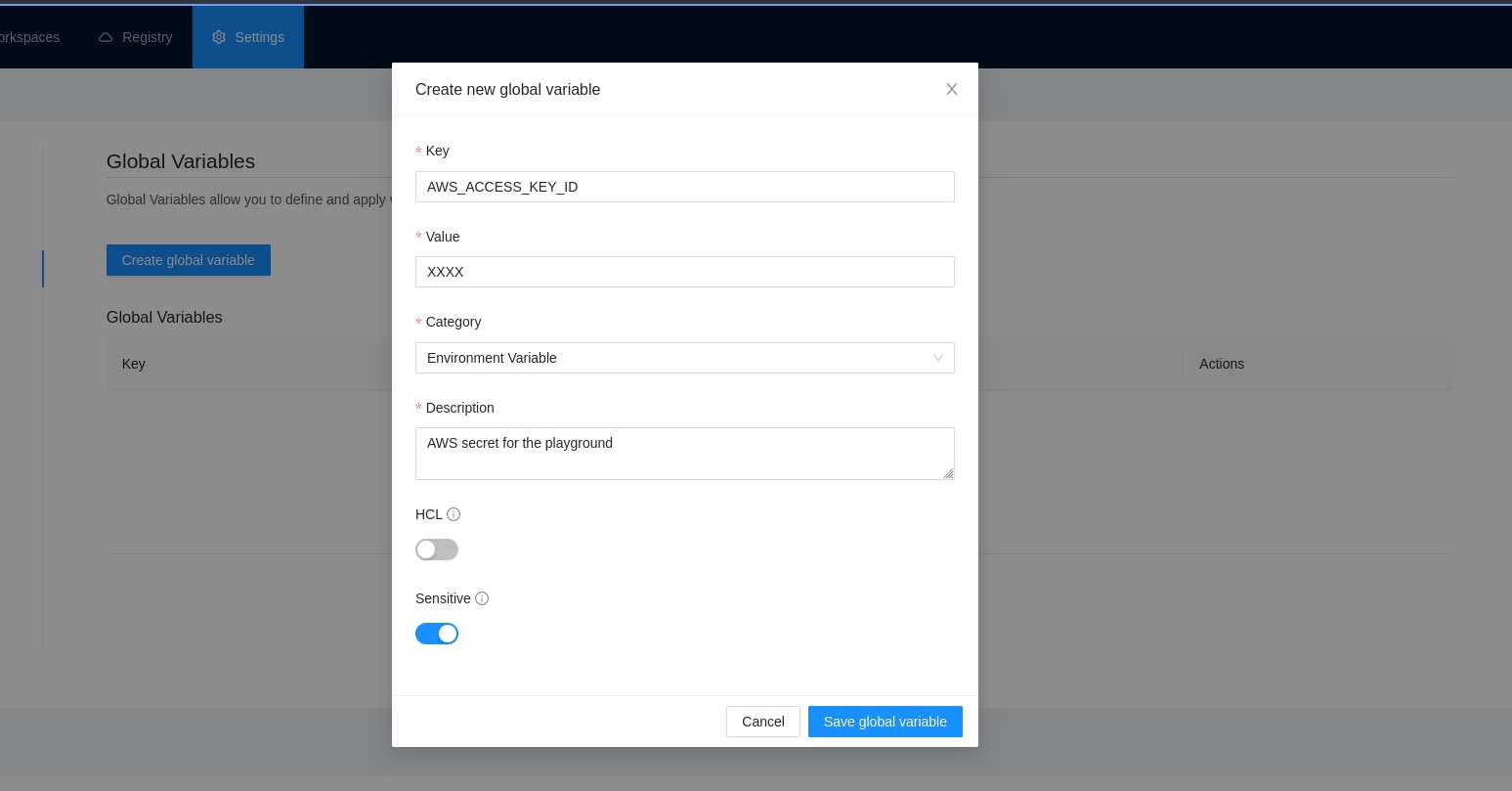
Go to the workspace Variables page and in the Terraform Variables section click the Add variable button.
In the popup, provide the required values. Use the below table as reference:
Key
Unique variable name
Value
Key value
Description
Free text to document the reason for this global variable
HCL
Parse this field as HashiCorp Configuration Language (HCL). This allows you to interpolate values at runtime.
Sensitive
Sensitive variables are never shown in the UI or API. They may appear in Terraform logs if your configuration is designed to output them.
Finally click the Save variable button and the variable will be created.
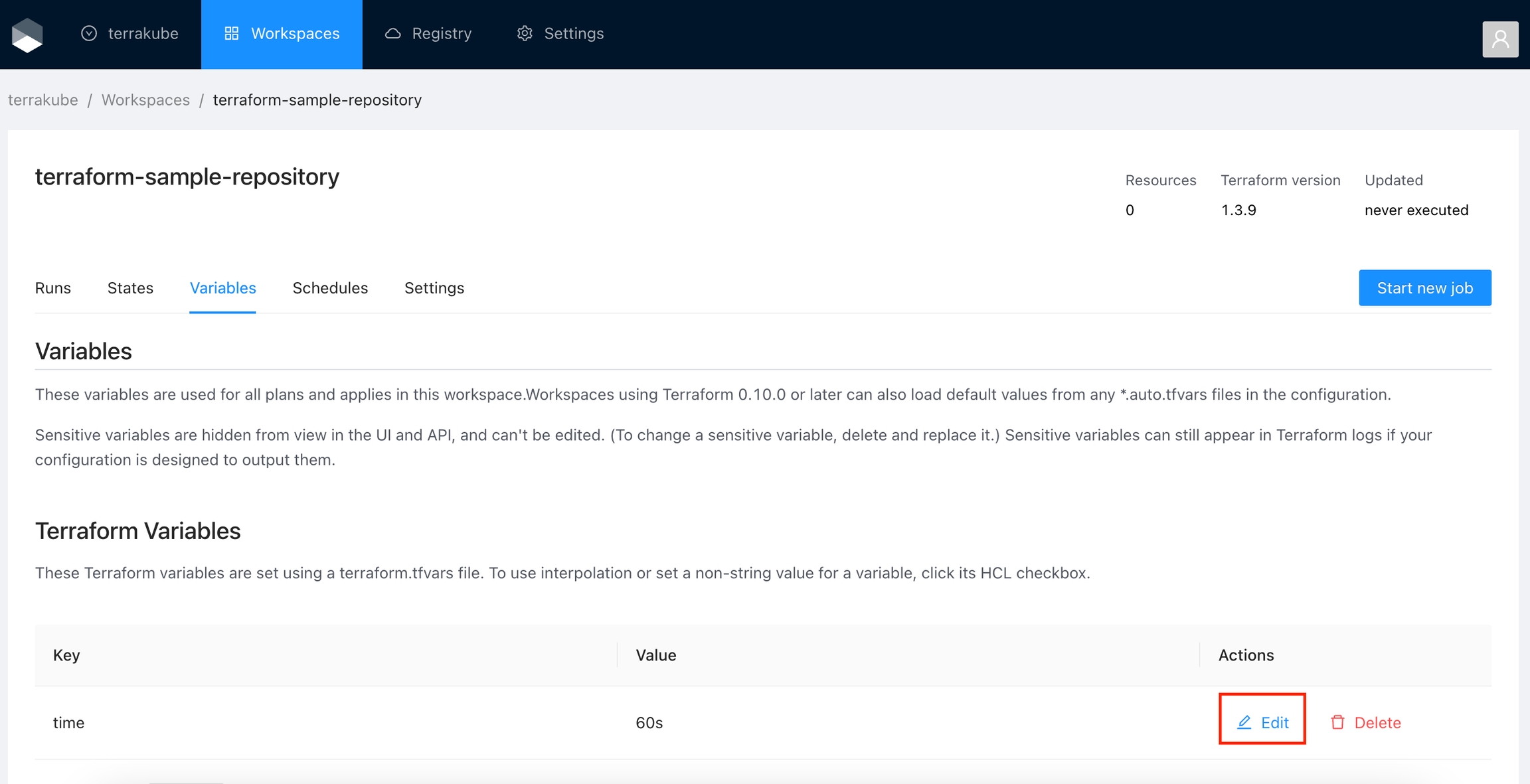
Click the Edit button next to the variable you want to edit.
Make any desired changes and click Save variable.
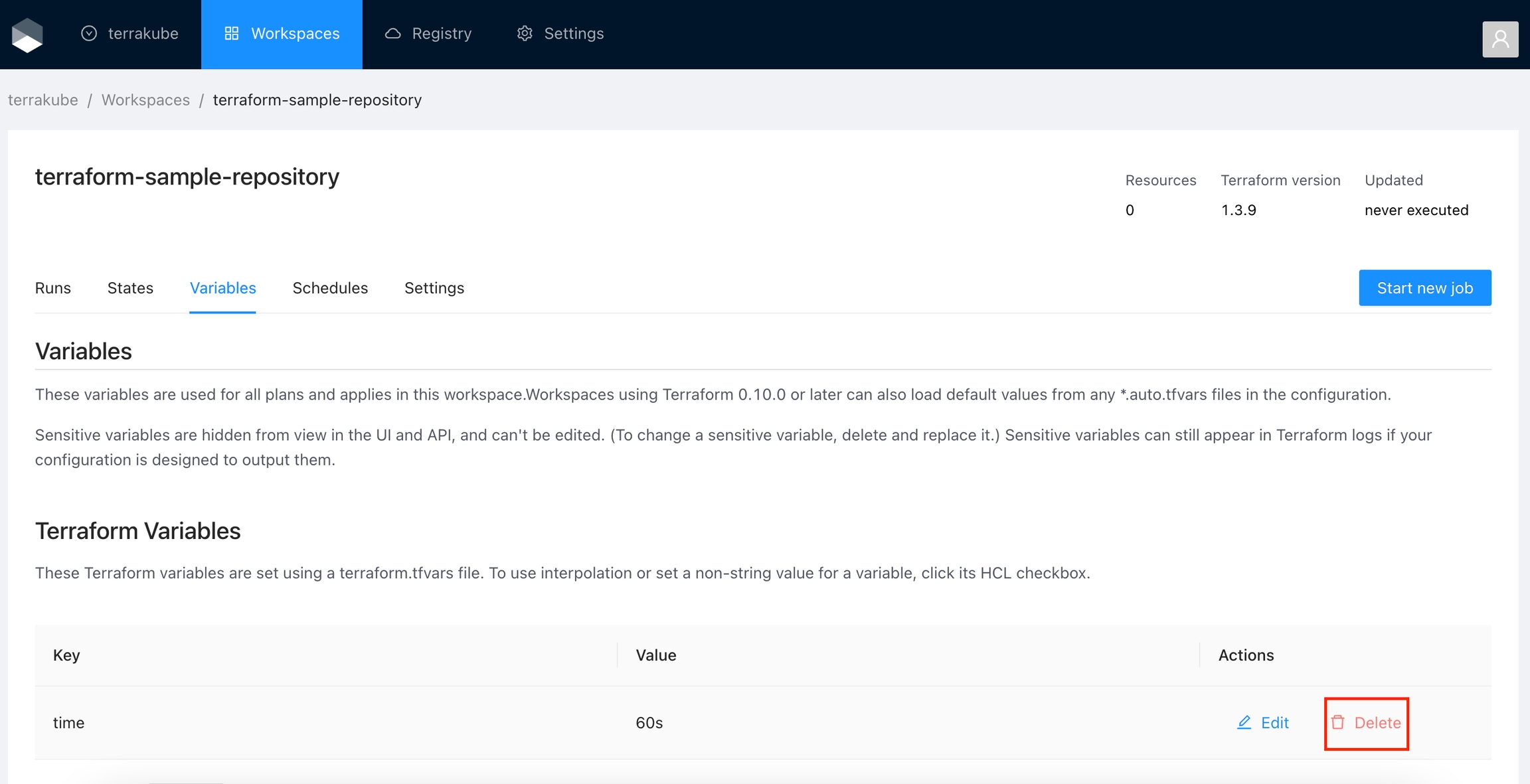
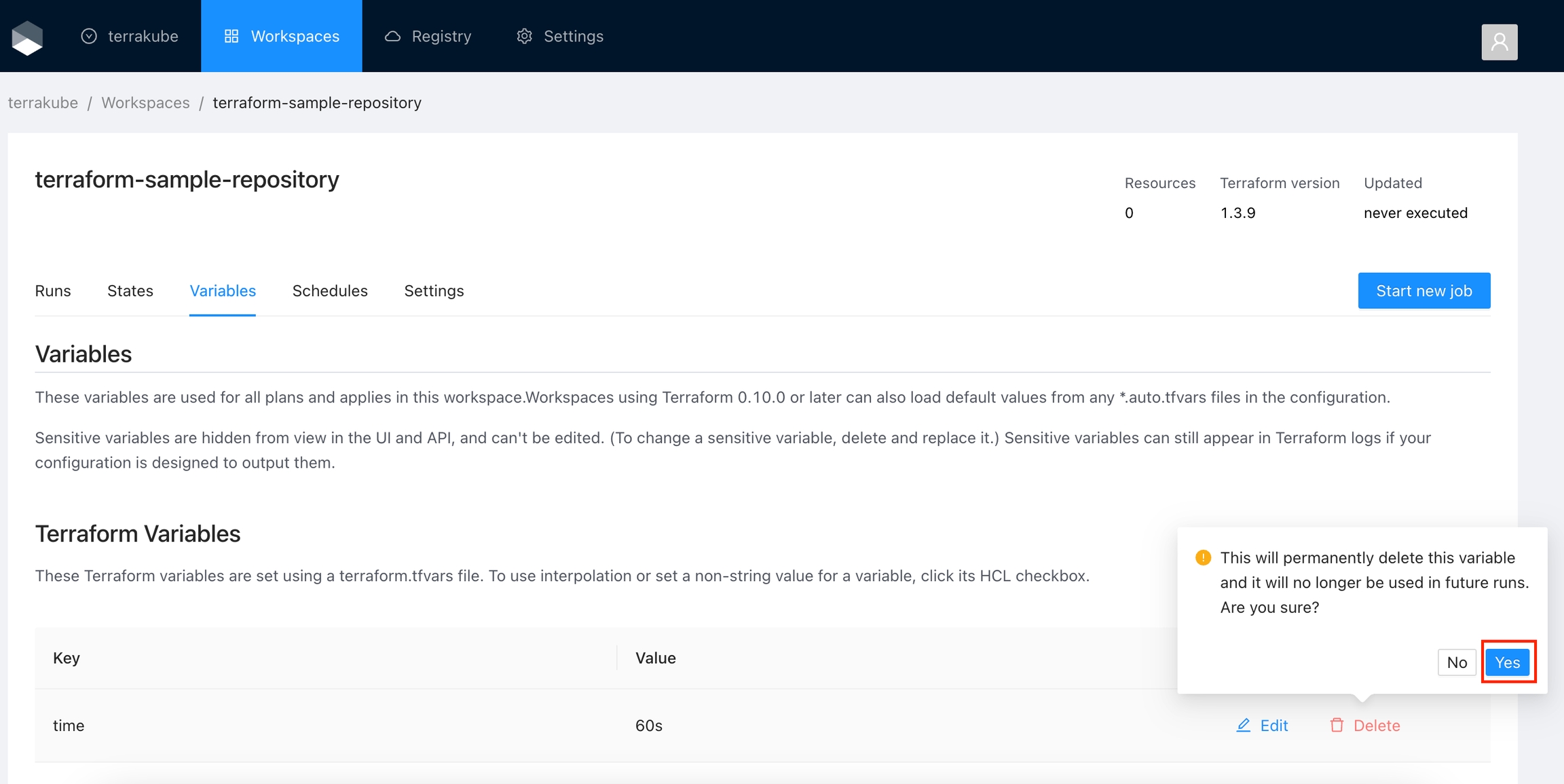
Click the Delete button next to the variable you want to delete.
Click Yes to confirm your action.
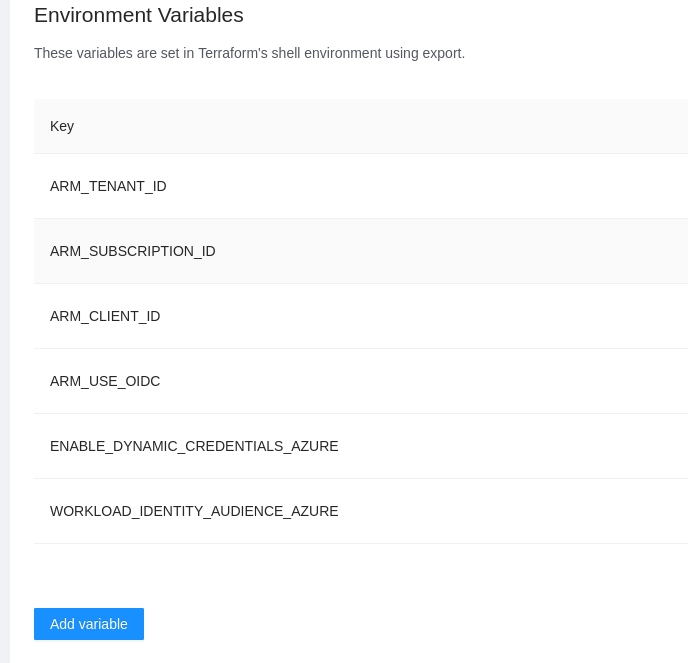
These variables are set in Terraform's shell environment using export.
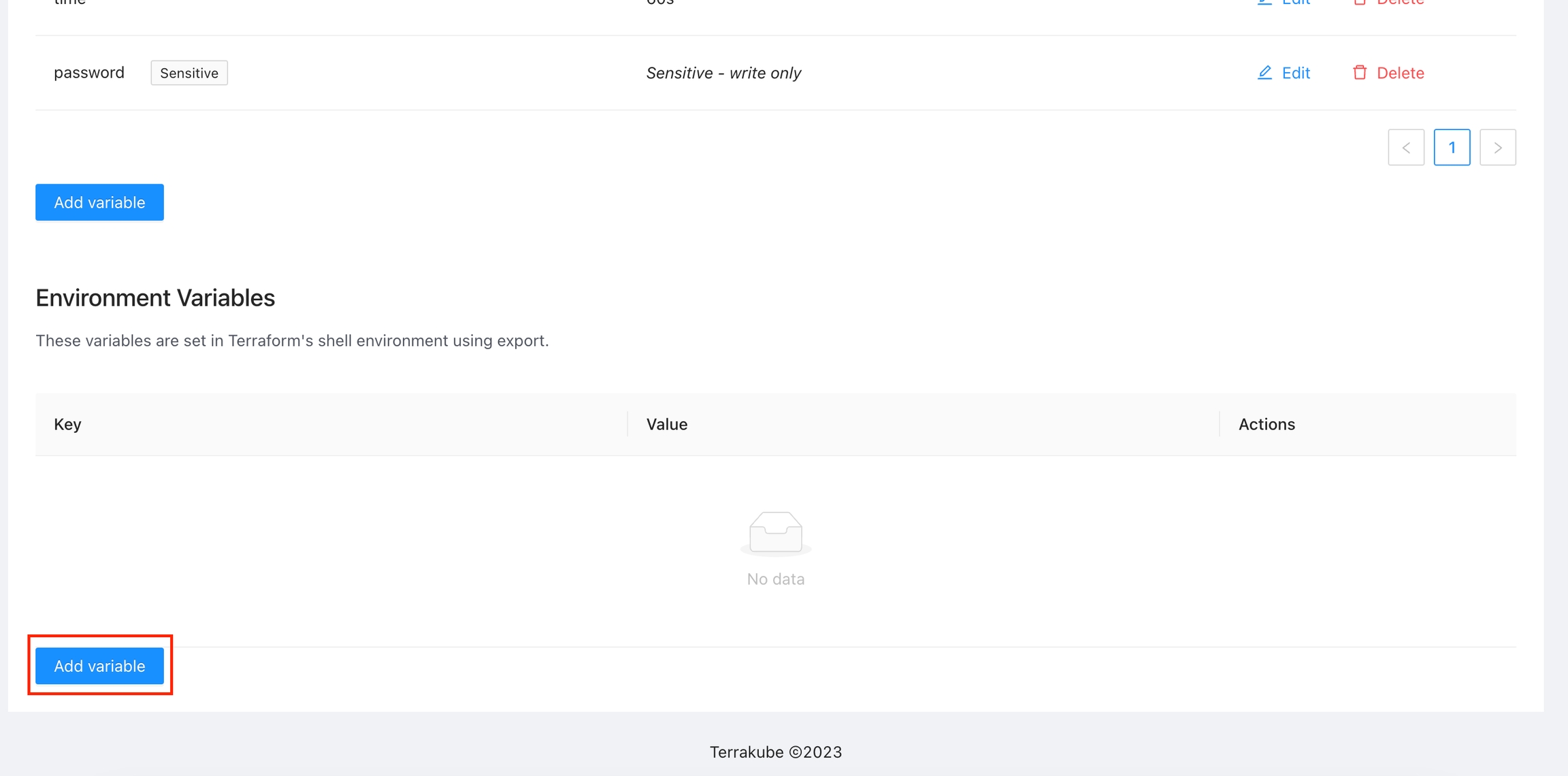
Go to the workspace Variables page and in the Environment Variables section click the Add variable button.
In the popup, provide the required values. Use the below table as reference:
Key
Unique variable name
Value
Key value
Description
Free text to document the reason for this global variable
HCL
Parse this field as HashiCorp Configuration Language (HCL). This allows you to interpolate values at runtime.
Sensitive
Sensitive variables are never shown in the UI or API. They may appear in Terraform logs if your configuration is designed to output them.
Finally click the Save variable button and the variable will be created.
Click the Edit button next to the variable you want to edit.
Make any desired changes and click Save variable.
Click the Delete button next to the variable you want to delete.
Click Yes to confirm your action.
The version of Terraform to use for this workspace. Check if you want to restrict the versions in your Terrakube instance.
The version of Terraform to use for this workspace. Check if you want to restrict the versions in your Terrakube instance.
The version of Terraform to use for this workspace. Check if you want to restrict the versions in your Terrakube instance.
In progress
This feature is available from version 2.21.0
To use Dynamic Provider credentials we need to genera a public and private key that will be use to generate a validate the federated tokens, we can use the following commands
You need to make sure the private key starts with "-----BEGIN PRIVATE KEY-----" if not the following command can be used to transform the private key to the correct format
The public and private key need to be mounted inside the container and the path should be specify in the following environment variables
DynamicCredentialPublicKeyPath
DynamicCredentialPrivateKeyPath
To use Dynamic Provider credentials the following public endpoints were added. This endpoint needs to be accessible for your different cloud providers.
The following environment variables can be used to customize the dynamic credentials configuration:
DynamicCredentialId = This will be the kid in the JWKS endpoint (Default value: 03446895-220d-47e1-9564-4eeaa3691b42)
DynamicCredentialTtl= The TTL for the federated token generated internally in Terrakube (Defafult: 30)
DynamicCredentialPublicKeyPath= The path to the public key to validate the federated tokens
DynamicCredentialPrivateKeyPath=The path to the private key to generate the federated tokens
Terrakube will generate a JWT token internally, this token will be used to authenticate to your cloud provider.
The token structure looks like the following for Azure
The token structure looks like the following for GCP
The token structure looks like the following for AWS
The dynamic provider credential setup in GCP can be done with the Terrraform code available in the following link:
https://github.com/AzBuilder/terrakube/tree/main/dynamic-credential-setup/gcp
The code will also create a sample workspace with all the require environment variables that can be used to test the functionality using the CLI driven workflow.
Make sure to mount your public and private key to the API container as explained here
Mare sure the private key is in "pkcs8" format
Validate the following terrakube api endpoints are working:
Set terraform variables using: "variables.auto.tfvars"
To generate the API token check here
Run Terraform apply to create all the federated credential setup in GCP and a sample workspace in terrakube for testing
To test the following terraform code can be used:
The dynamic provider credential setup in AWS can be done with the Terrraform code available in the following link:
https://github.com/AzBuilder/terrakube/tree/main/dynamic-credential-setup/aws
The code will also create a sample workspace with all the require environment variables that can be used to test the functionality using the CLI driven workflow.
Make sure to mount your public and private key to the API container as explained here
Mare sure the private key is in "pkcs8" format
Validate the following terrakube api endpoints are working:
Set terraform variables using: "variables.auto.tfvars"
To generate the API token check here
Run Terraform apply to create all the federated credential setup in AWS and a sample workspace in terrakube for testing
To test the following terraform code can be used:
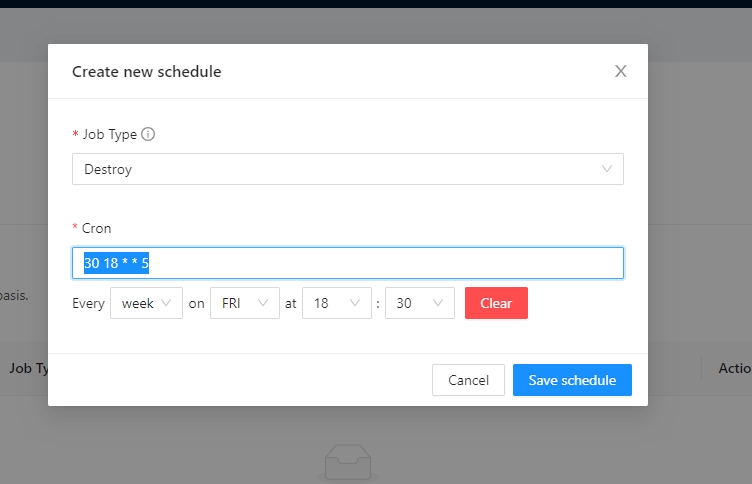
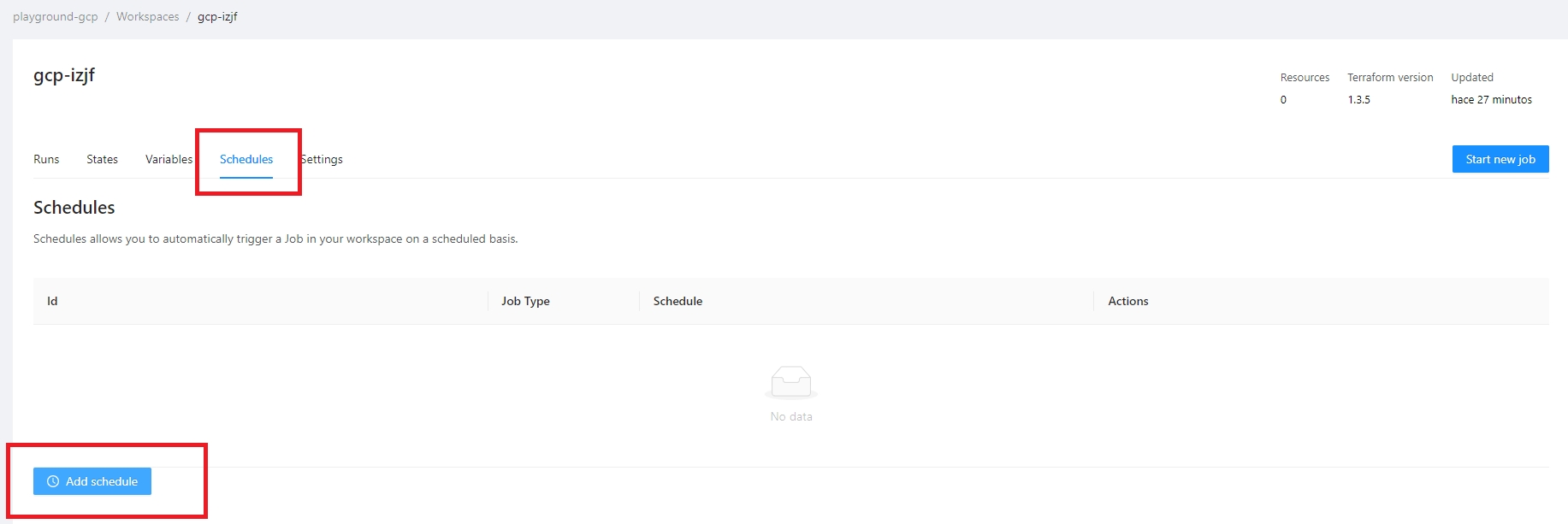
Terrakube allows to schedule a job inside workspaces, this will allow to execute a specific template in an specific time.
To create a workspace schedule click the "schedule" tab and click "Add schedule" like the following image.
This is usefull for example when you want to destroy your infrastructure by the end of every week to save some money with your cloud provider and recreate it every monday morning.
Example.
Lets destroy the workspace every friday at 6 pm
Cron expression will be 30 18 * * 5
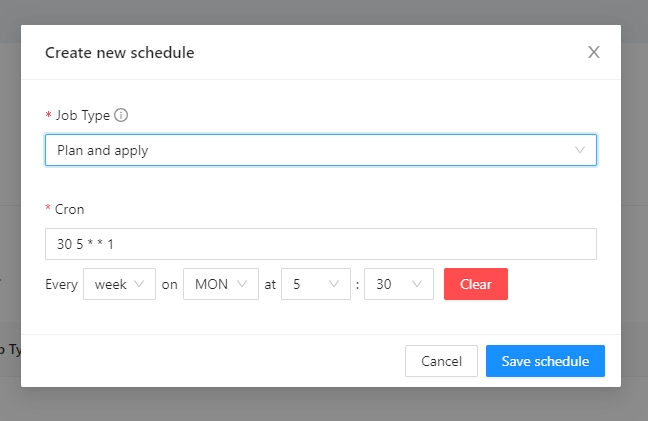
Lets create the workspace every monday at 5:30 am
Cron expression will be 30 5 * * 1
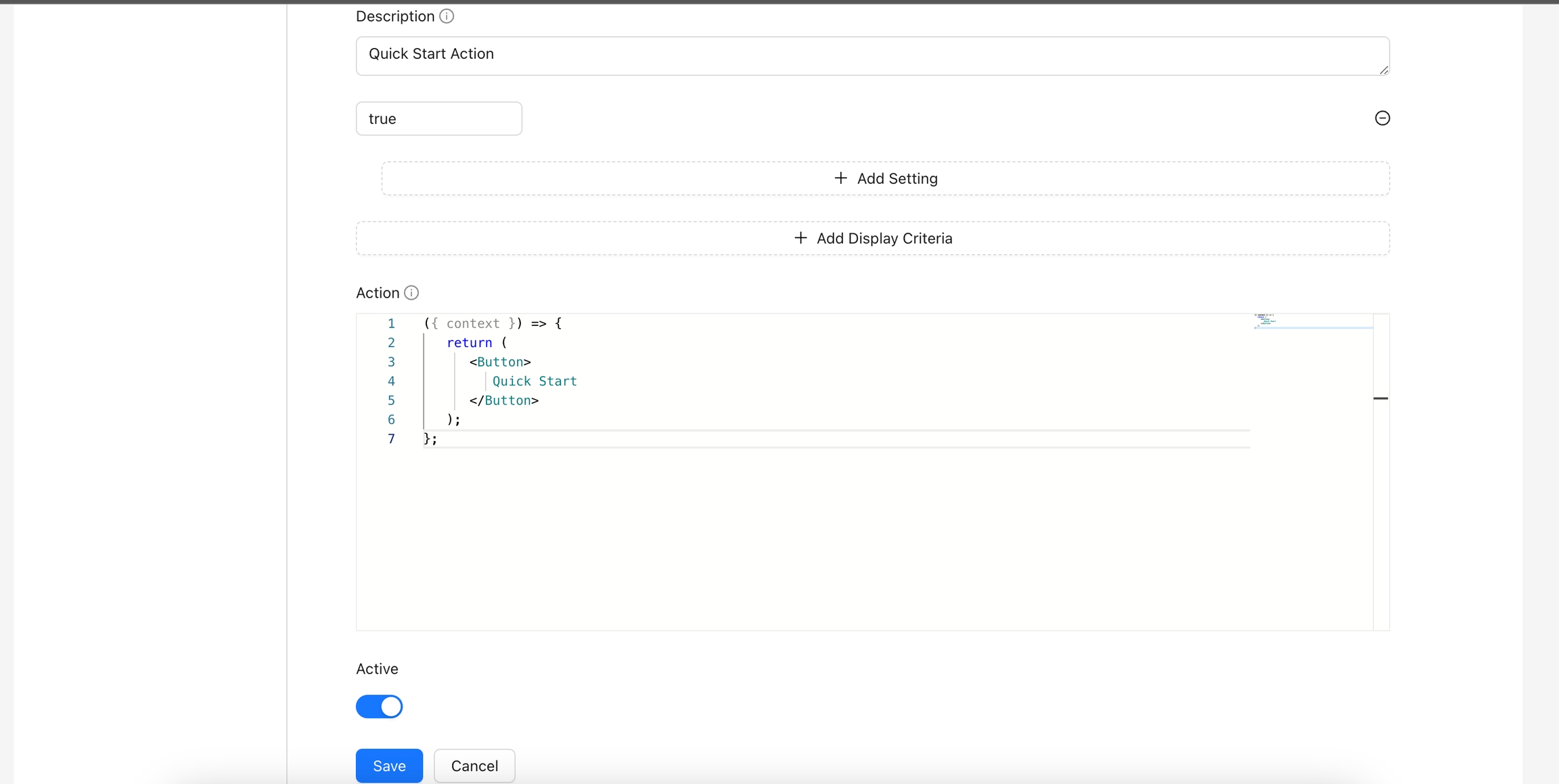
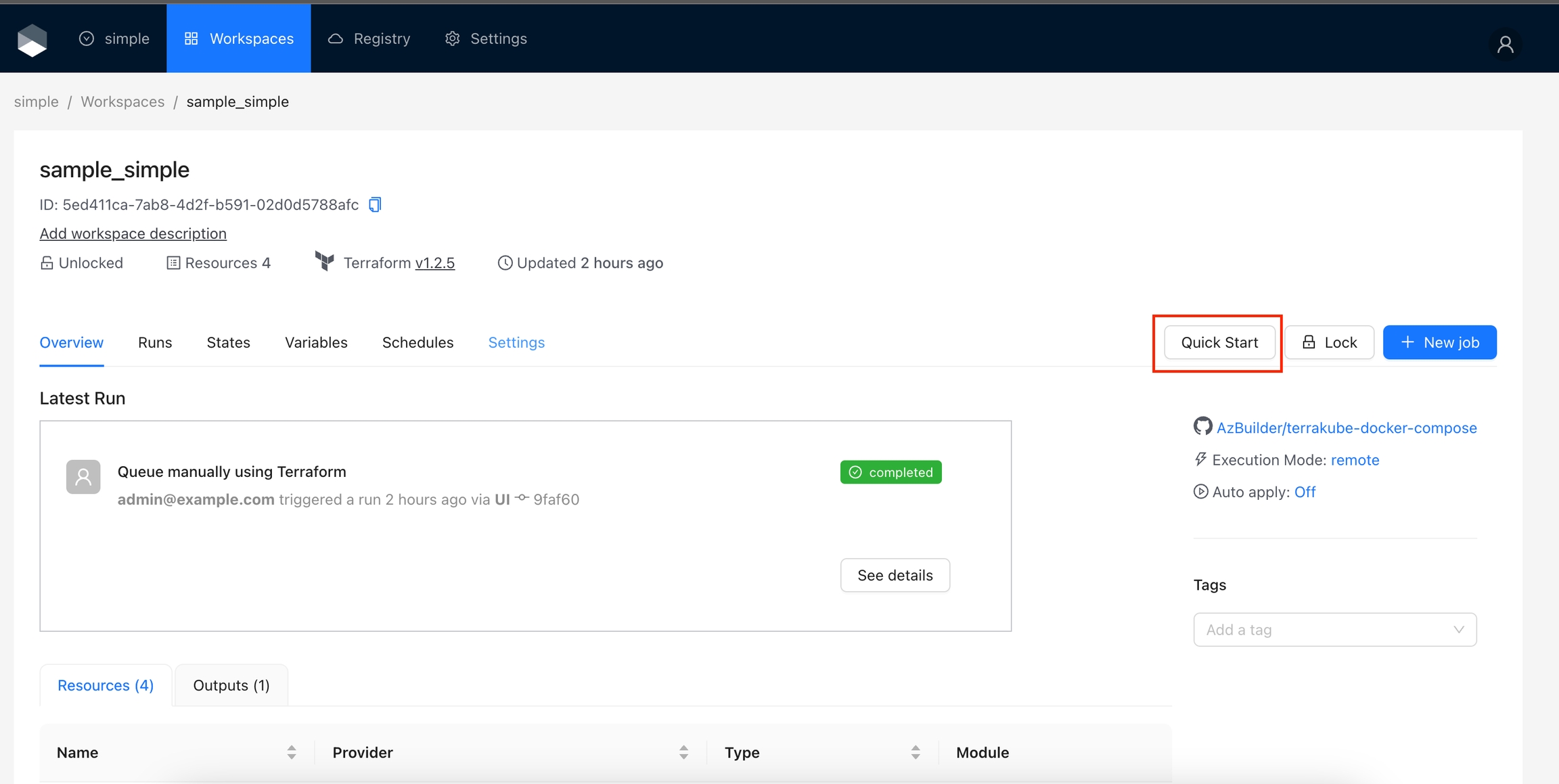
Let's start writing our Hello World action. This action will include a single button with the text "Quick Start".
As you can see, an action is essentially some JavaScript code, specifically a React component. If you are not familiar with JavaScript and React, I recommend before continuing.
This component contains only one button and receives a context parameter. We will discuss more about the context later. For now, you only need to know that the context provides some data related to the area where the action will appear.
Terrakube uses , so by default, all antd components are available when you are developing an action.
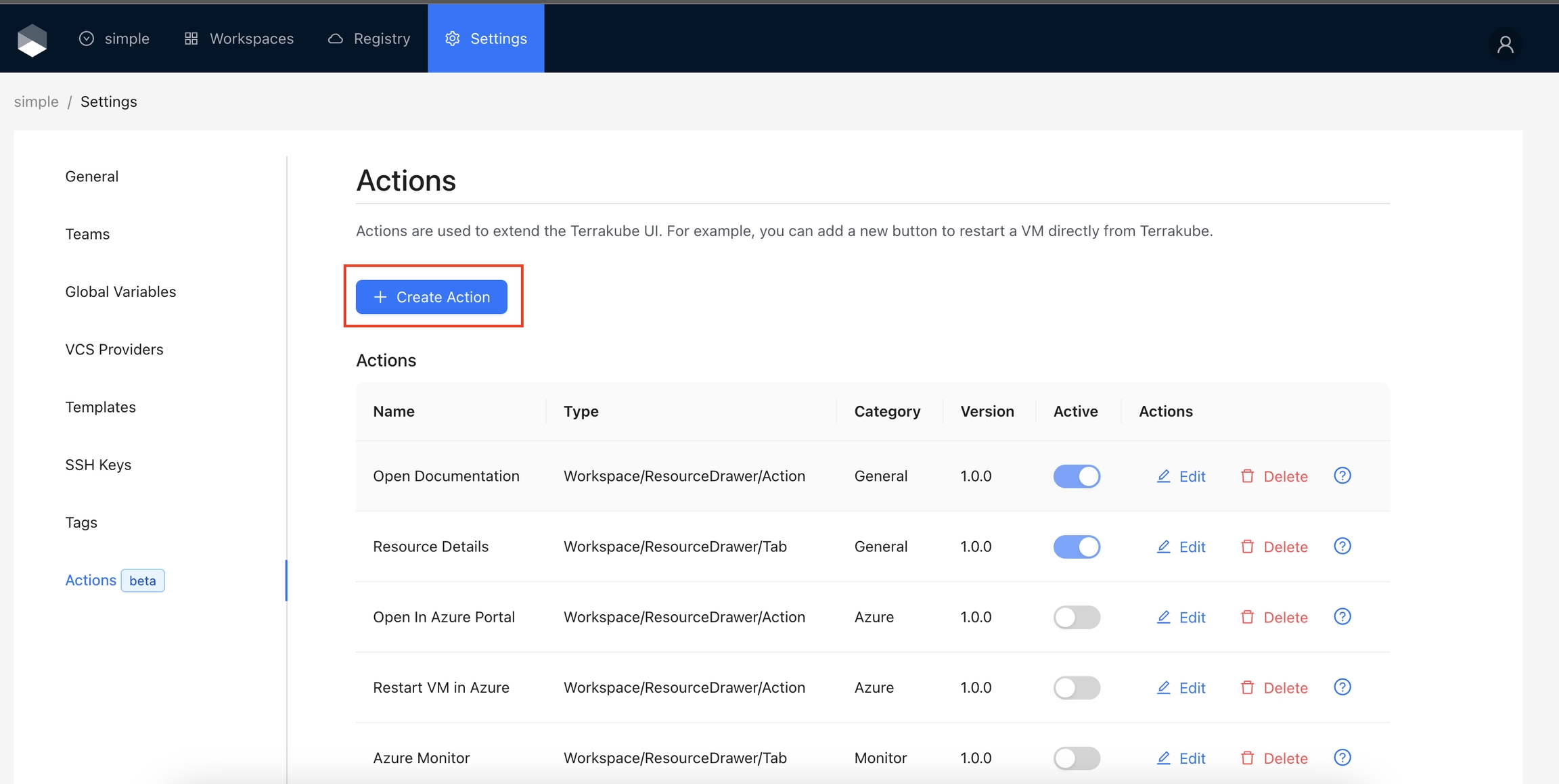
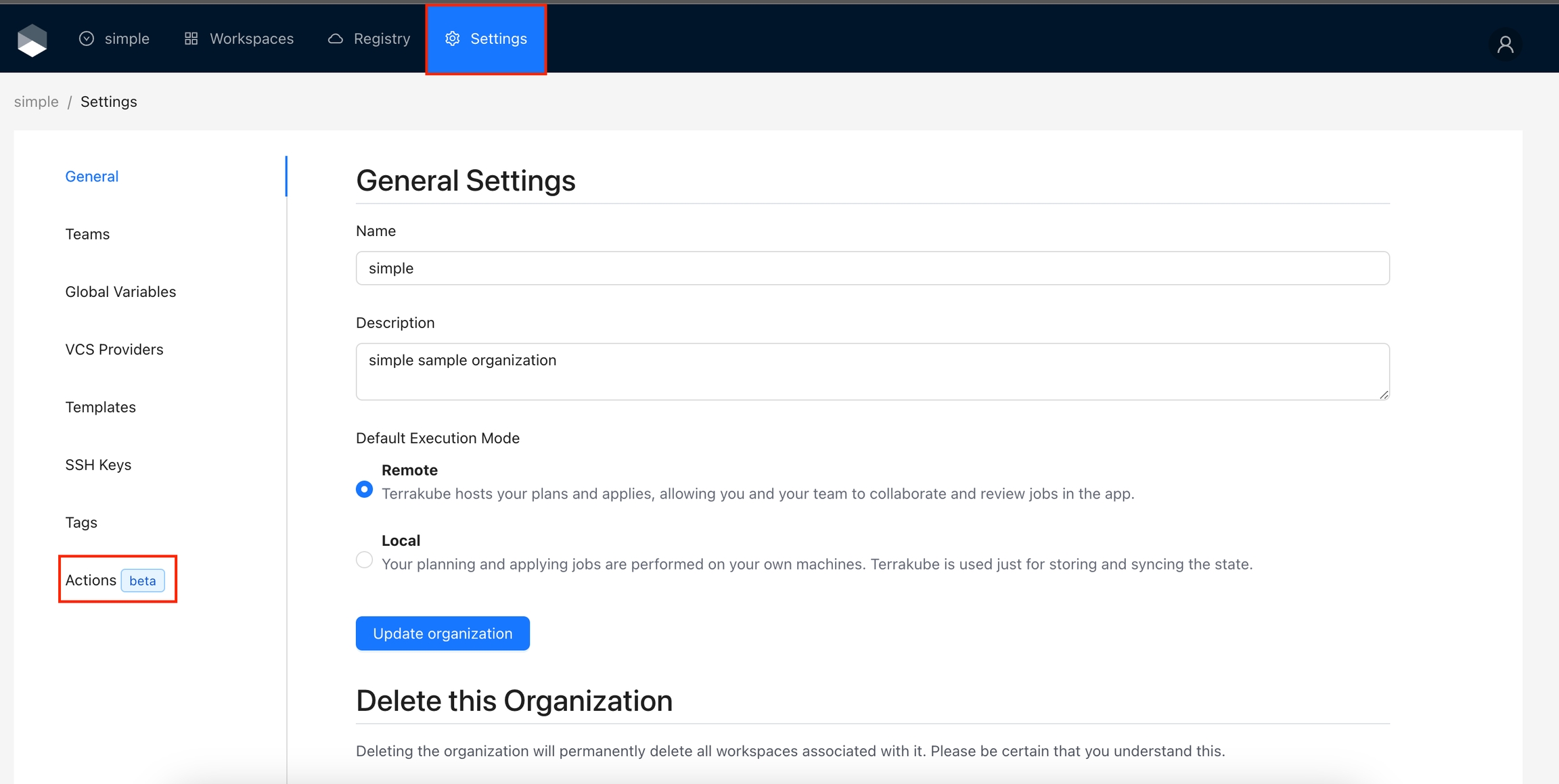
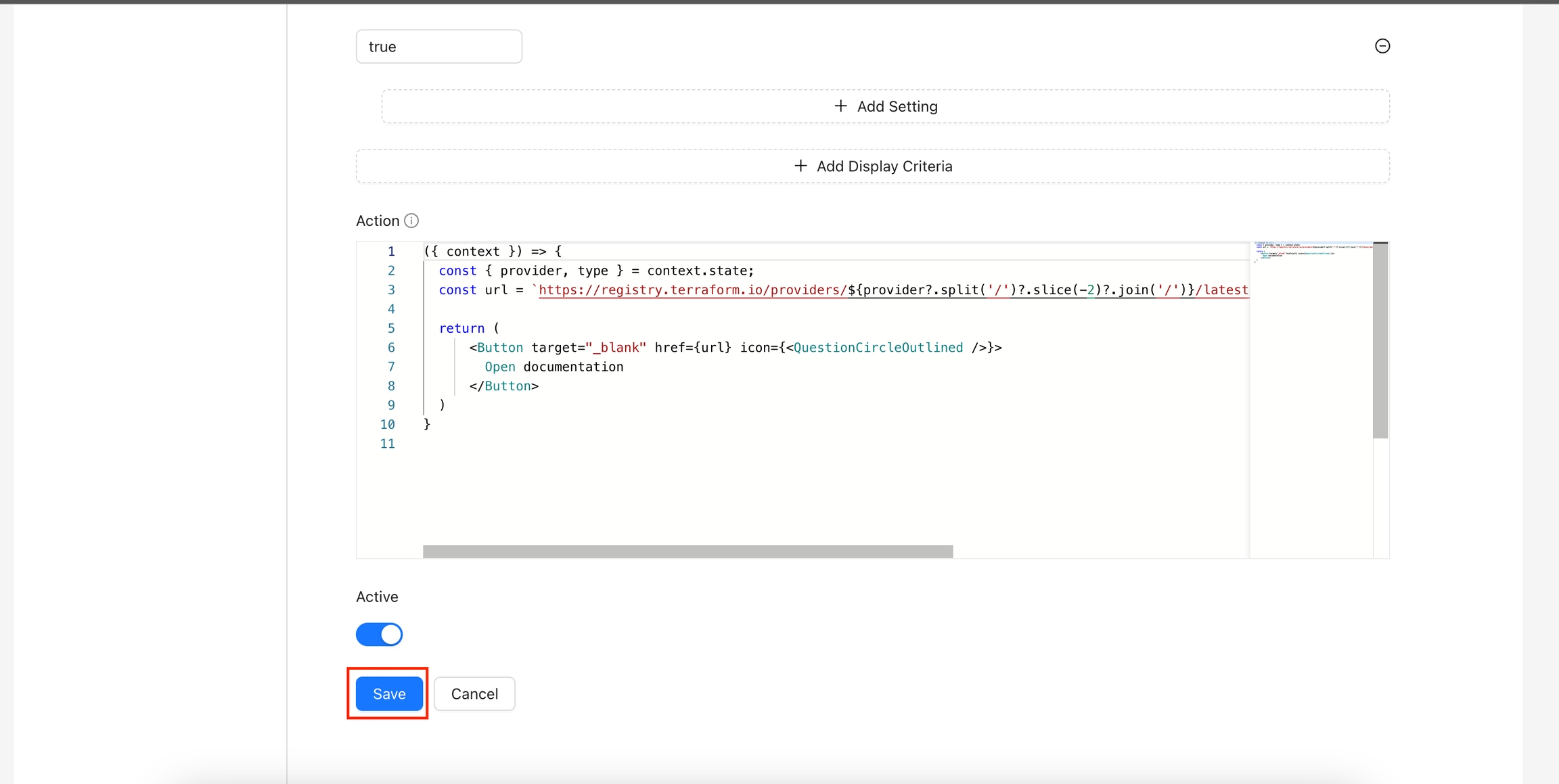
To create the action in your Terrakube instance, navigate to the Organization settings and click the Create Action button
Add the following data and click the save button.
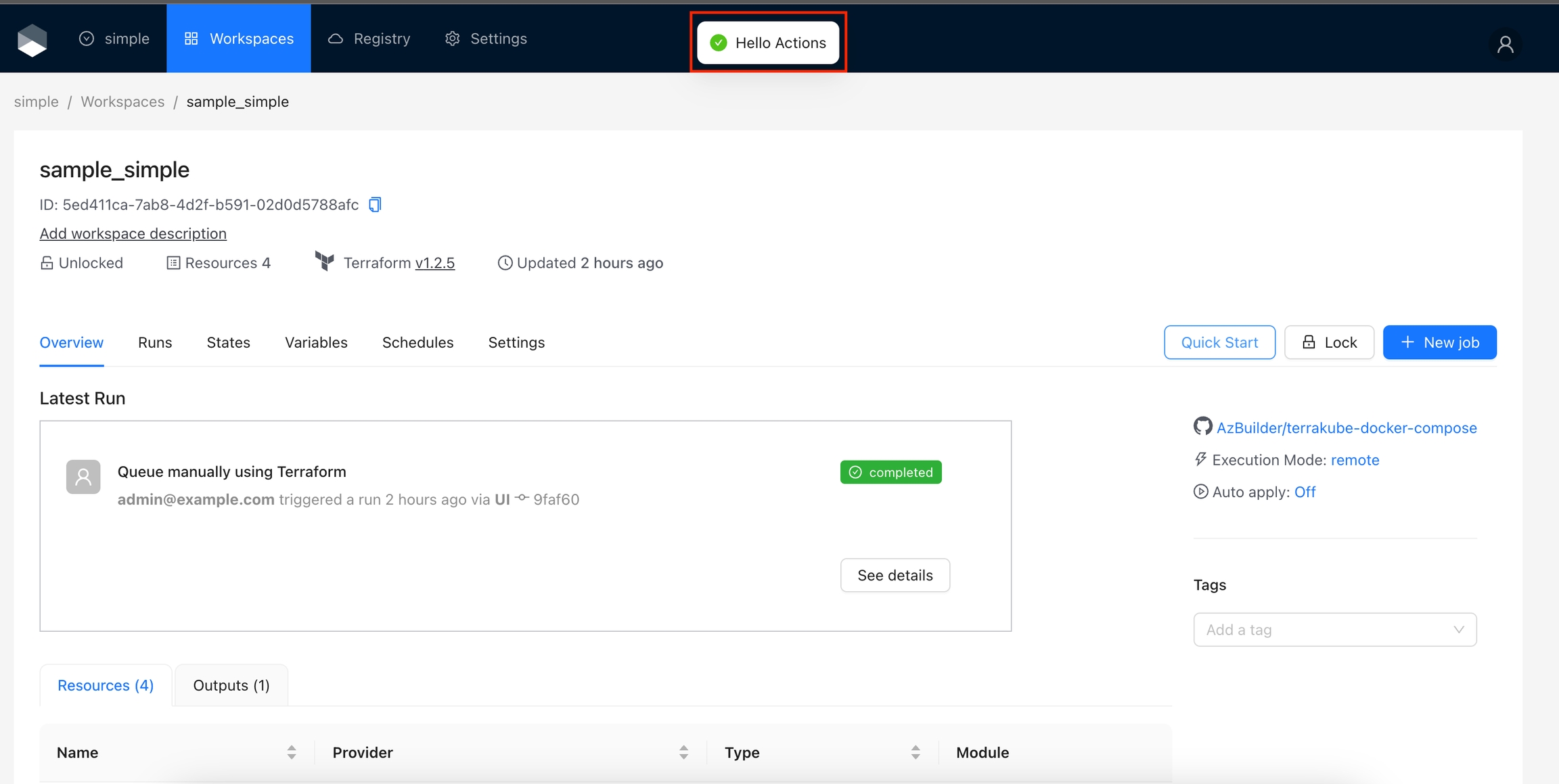
If you go to any workspace, the quick start button should appear.
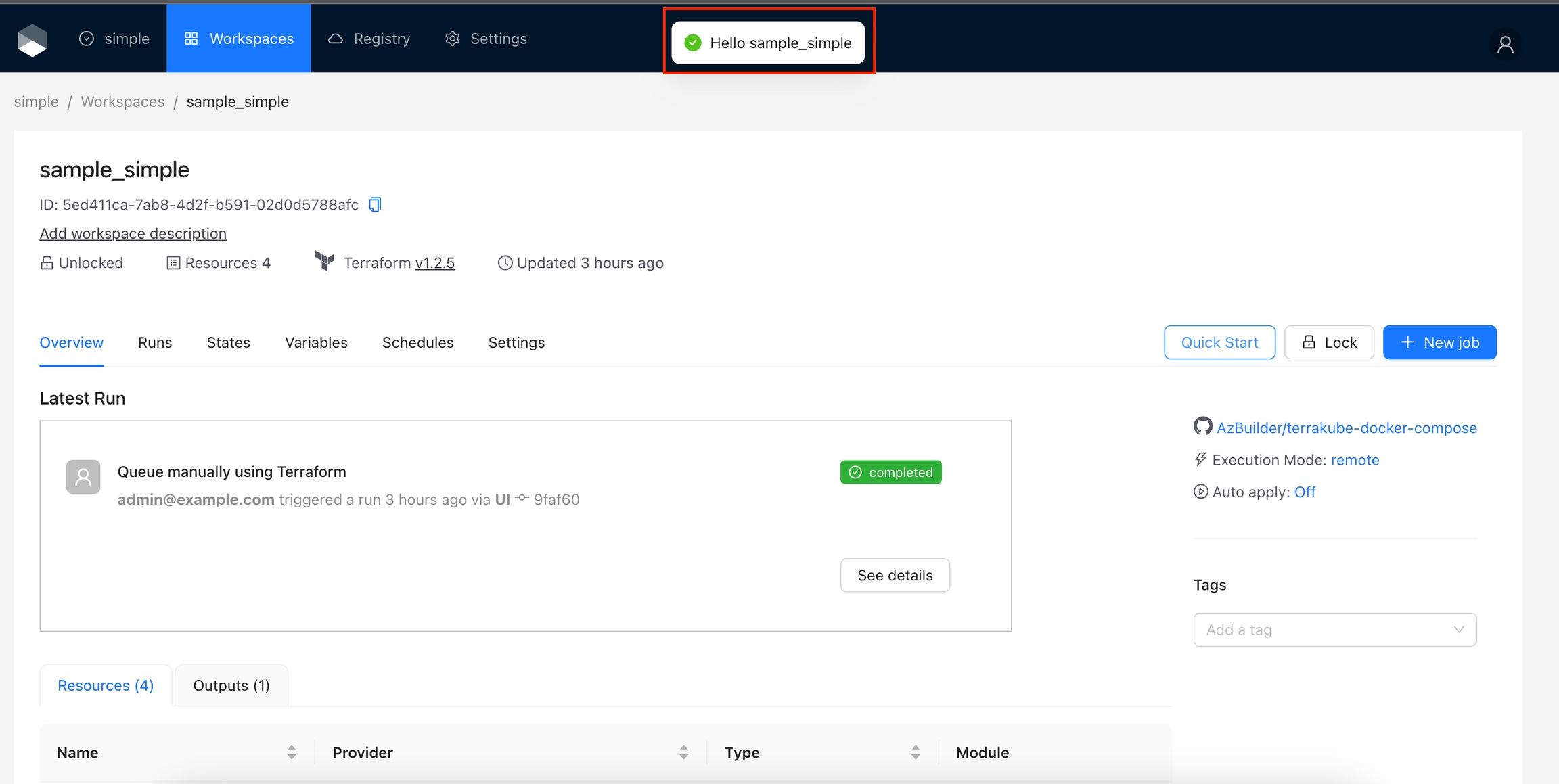
Now let's add some interaction to the button. In the next example, we will use the Ant Design Messages component.
Now, if you update the action code, navigate to any workspace, and click the Quick Start button, you will see the Hello Actions message.
For our quick start action, we will add the name of the workspace to the message.
Update the action code using the code above, click the Quick Start button, and you will see the message now displays the Workspace Name.
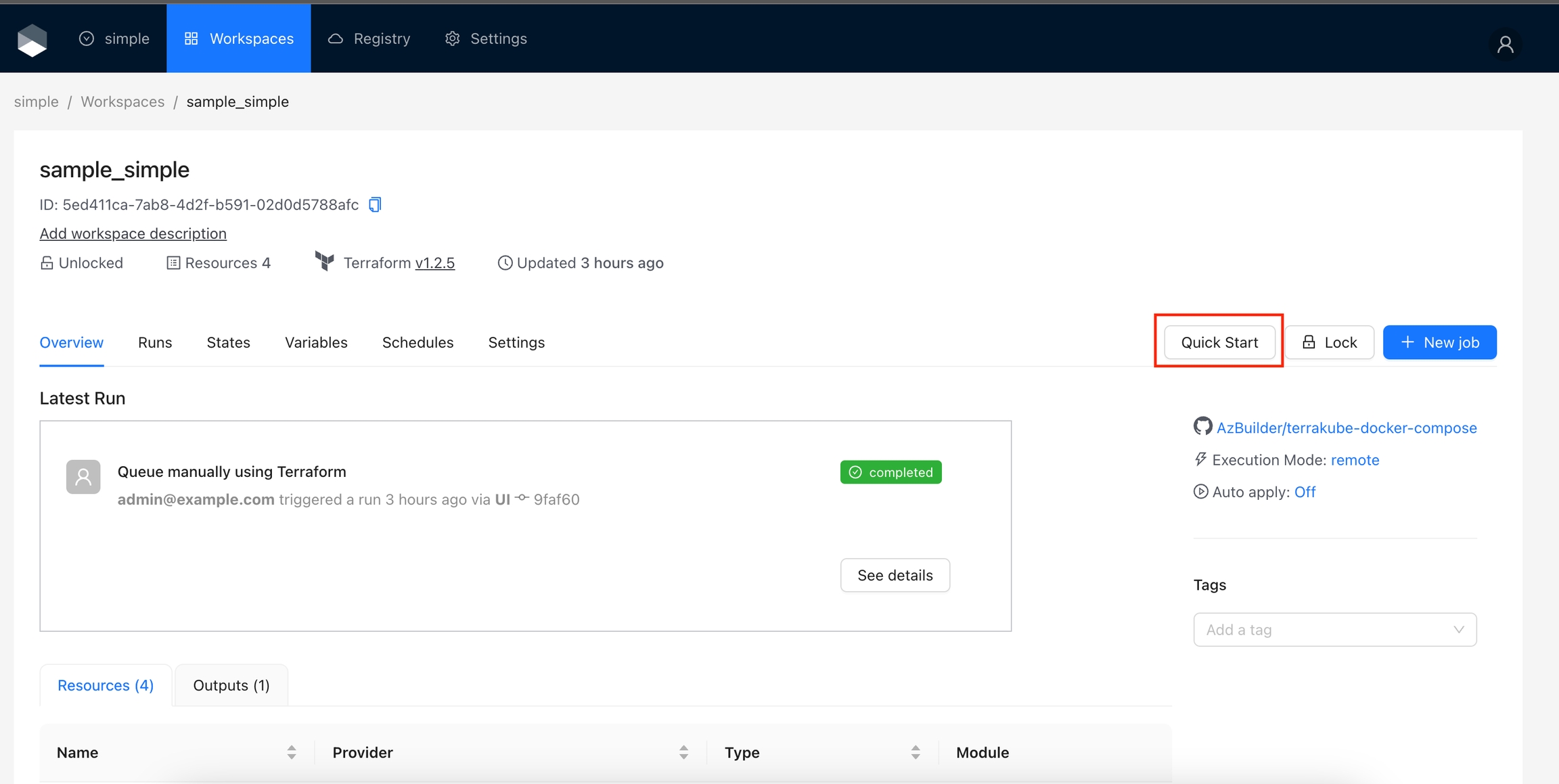
f you view a couple of workspaces in the organization, you will see the "Quick Start" button always appears. This is useful if your action serves a general purpose, but there are scenarios where you want to display the action only for workspaces in a specific organization, with a specific version of Terraform, and so on.
In those cases, you will use display criteria, which provides a powerful way to decide when an action will appear or not. If you remember, we set the display criteria to true before. Now let's modify the criteria to show the action only if the workspace contains a specific name.
Navigate to the Actions settings and change the display criteria to:
(You can use another workspace name if you don't have the "sample_simple" workspace.)
Now the button will appear only for the sample_simple workspace. If you notice, the display criteria is a conditional JavaScript code. So you can use any JavaScript code to display the action based on a regular expression, for organizations starting with certain names, or even combine multiple conditions.
At this moment, our action only interacts with Terrakube data. However, a common requirement is to access other APIs to get some data, for example, to connect to the GitHub API to get the issues related to the workspace, or to connect to a cloud provider to interact with their APIs.
In these cases, we can make use of the Action Proxy. The proxy provides a way to connect to other backend services without needing to directly configure CORS for the API. The proxy also provides a secure way to use credentials without exposing sensitive data to the client.
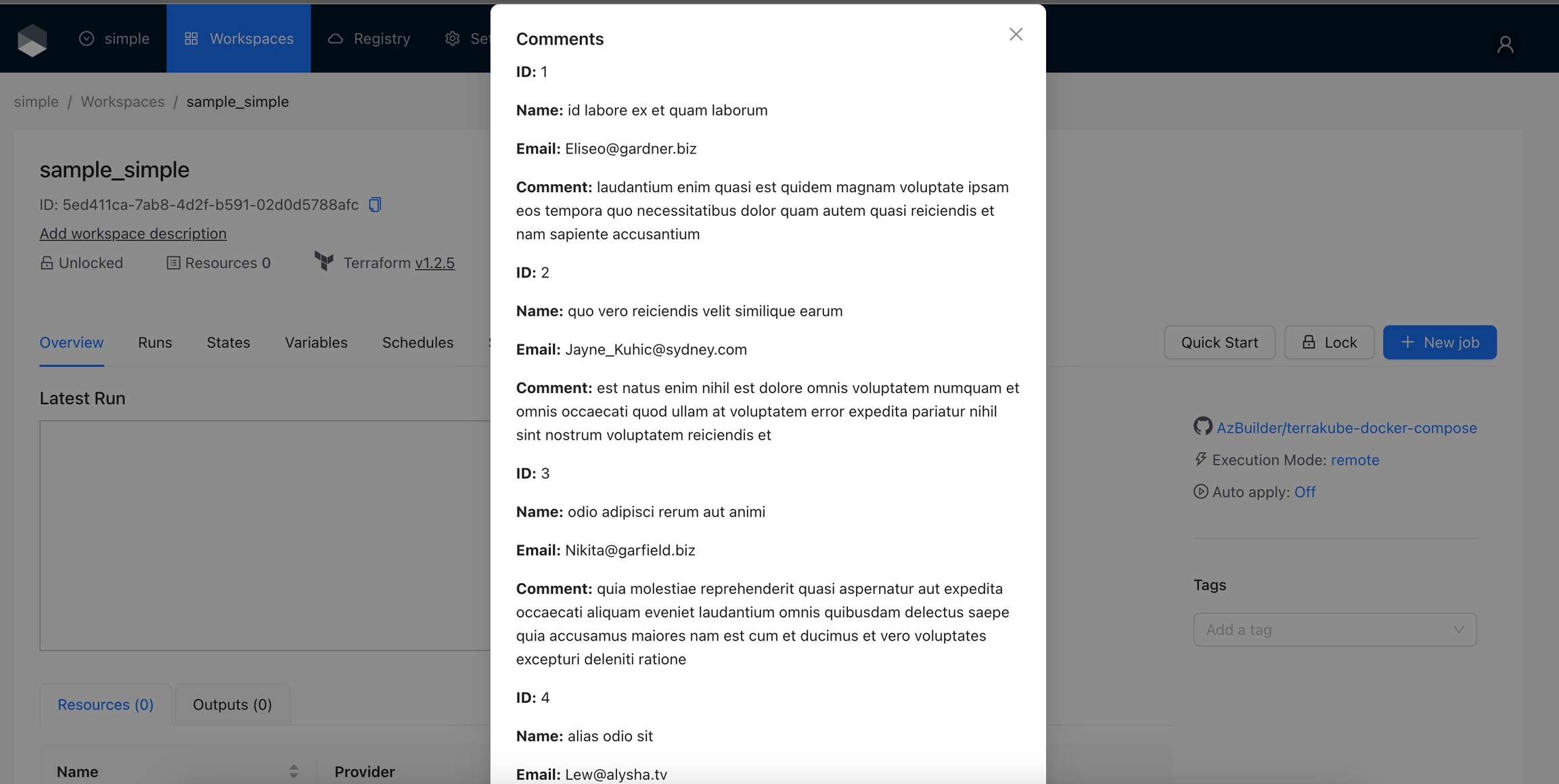
Let's add a simple interaction using mock data from the JSONPlaceholder API that reads the comments from a post.
Now if you click the Quick Start button, you will see a dialog with the comments data from the API. The proxy allows to interact with external apis and securely manage credentials. To know more about the Actions proxy check the documentation.
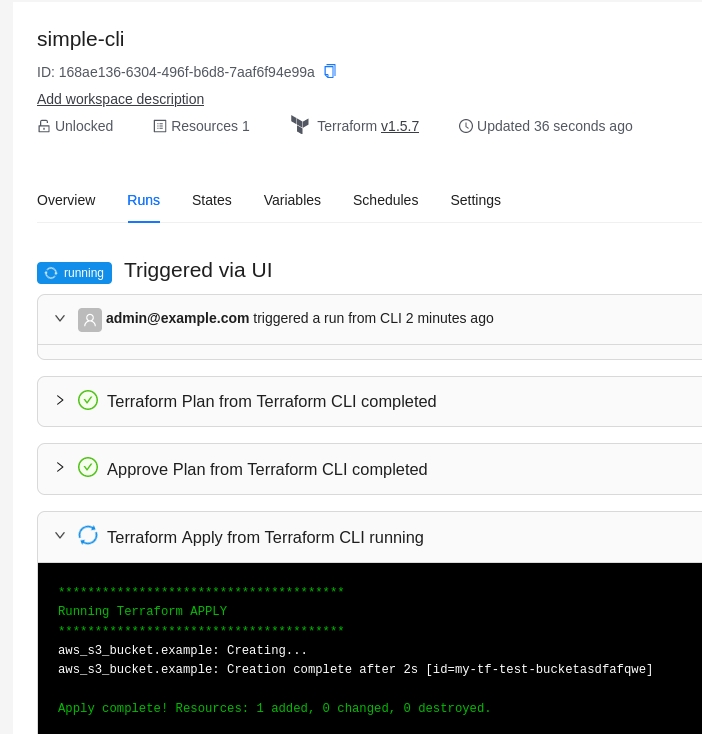
With the CLI integration, you can use Terrakube’s collaboration features in the Terraform CLI workflow that you are already familiar with. This gives you the best of both worlds as a developer who uses the Terraform CLI, and it also works well with your existing CI/CD pipelines.
You can initiate runs with the usual terraform plan and terraform apply commands and then monitor the run progress from your terminal. These runs run remotely in Terrakube.
Terrakube creates default templates for CLI-Driven workflow when you create a new organization, if you delete those templates you won't be able to run this workflow, check for more information.
At the moment all the terraform operations are executed remotely in Terrakube
To use the CLI-driven workflow the firts step will be to setup our project to use the terraform remote backend or the cloud block as the following example:
Hostname
This should be the Terrakube API
Organization
This should be the Terrakube organization where the workspace will be created.
Workspace
The name of the workspace to be created. Or you can use an existing workspace created in the UI using the API or CLI driven workflow.
The cloud block is available in Terraform v1.1 and later. Previous versions can use the remote bakced to configure the CLI workflow and migrate state. Using tags in the cloud block is not yet supported
Once we have added the terraform remote state configuration we will need to authenticate to Terrakube using the following command with the Terrakube API as the following:
The output will look something like the following:
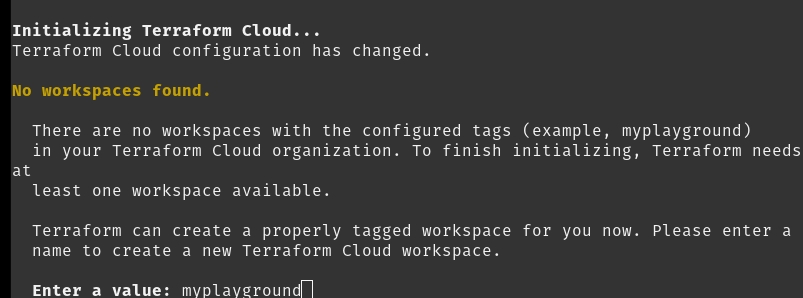
After the authentication is completed you can run the following command to initialized the workspace
The output will look like this:
If the initialization is successfull you should be able to see something like this:
Terrakube will create a new workspace with the name you specify in the cloud block if it doesn’t already exist in your organization. You will see a message about this when you run terraform init.
Once the terraform initialization is completed we should be able to run a terraform plan remotely using the following:
You can use .tfvars file inside the workspace to upload the variables to the workspace automatically
If you go to the Terrakube UI, you will be able to see the workspace plan execution.
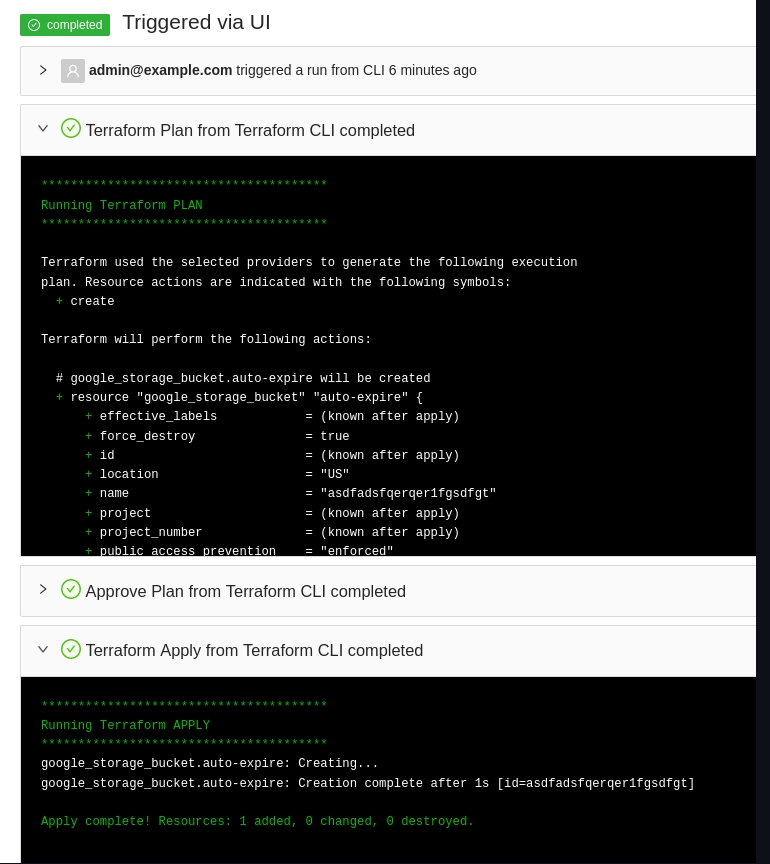
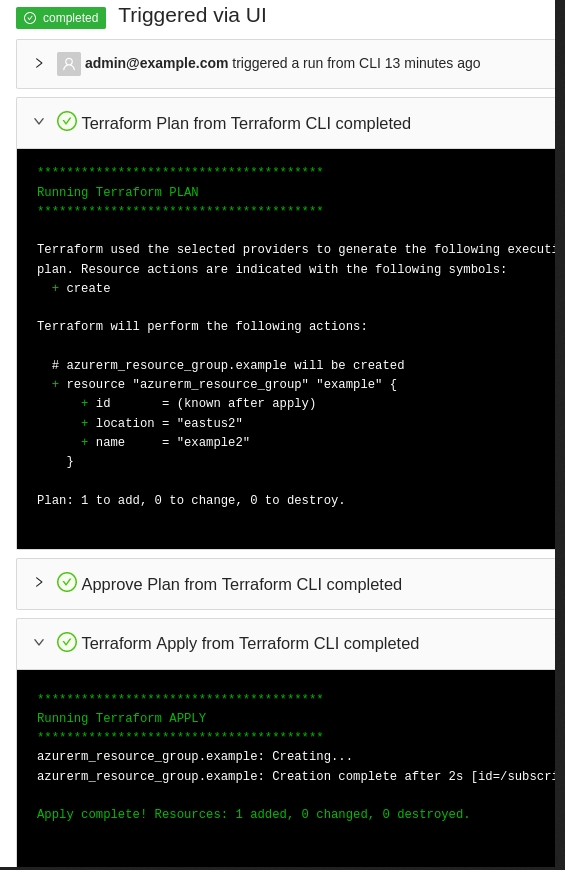
You can also execute a terraform apply and it will run inside Terrakube remotely.
The terraform apply can only be approved using the terraform CLI. You wont be able to approve the job inside the UI.
Terraform Destroy
Executing the terraform destroy is also possible.
Inside the UI the terraform destroy operation will look like this.
The terraform destroy can only be approved using the terraform CLI. You wont be able to approve the job inside the UI.
In this section:
Only users that belongs to Terrakube administrator group can create and edit actions. This group is defined in the terrakube settings during deployment, for more details see
Terrakube actions allow you to extend the UI in Workspaces, functioning similarly to plugins. These actions enable you to add new functions to your Workspace, transforming it into a hub where you can monitor and manage your infrastructure and gain valuable insights. With Terrakube actions, you can quickly observe your infrastructure and apply necessary actions.
Extend Functionality: Customize your Workspace with additional functions specifics to your needs.
Monitor Infrastructure: Gain real-time insights into your infrastructure with various metrics and monitoring tools.
Manage Resources: Directly manage and interact with your resources from within the Workspace.
Flexibility: Quickly disable an action if it is not useful for your organization or set conditions for actions to appear, such as if a resource is hosted in GCP or if the workspace is Dev.
Cloud-Agnostic Hub: Manage multi-cloud infrastructure from a single point, providing observability and actionability without needing to navigate individual cloud portals.
Manage Infrastructure: Restart your Azure VM or add an action to quickly navigate to the resource in the Azure portal directly from Terrakube.
Monitor Metrics: Track and display resource metrics for performance monitoring using tools like Prometheus, Azure Monitor or AWS Cloudwatch.
Integrate with Tools: Seamlessly integrate with tools like Infracost to display resource and Workspace costs.
AI Integration: Use AI to diagnose issues in your Workspaces. By integrating with models like OpenAI, Claude, and Gemini, you can quickly resolve errors in your infrastructure.
Project and Incident Management: Integrate with Jira, GitHub Issues, and ServiceNow to identify Workspaces with pending work items or reported errors.
Documentation: Link your Confluence documentation or wiki pages in your preferred tool, allowing quick access to documents related to your Workspace infrastructure.
After you develop your action. To create a new action in Terrakube:
Navigate to the settings in any Terrakube organization.
Click the Add Action button.
Provide the required information as detailed in the table below:
Click the Save button.
The following will show how easy is to implement an ephemeral workspace using Terrakube custom schedules and templates with the remote CLI-driven workflow.
The first step will be to create a new organization, lets call it "playground".
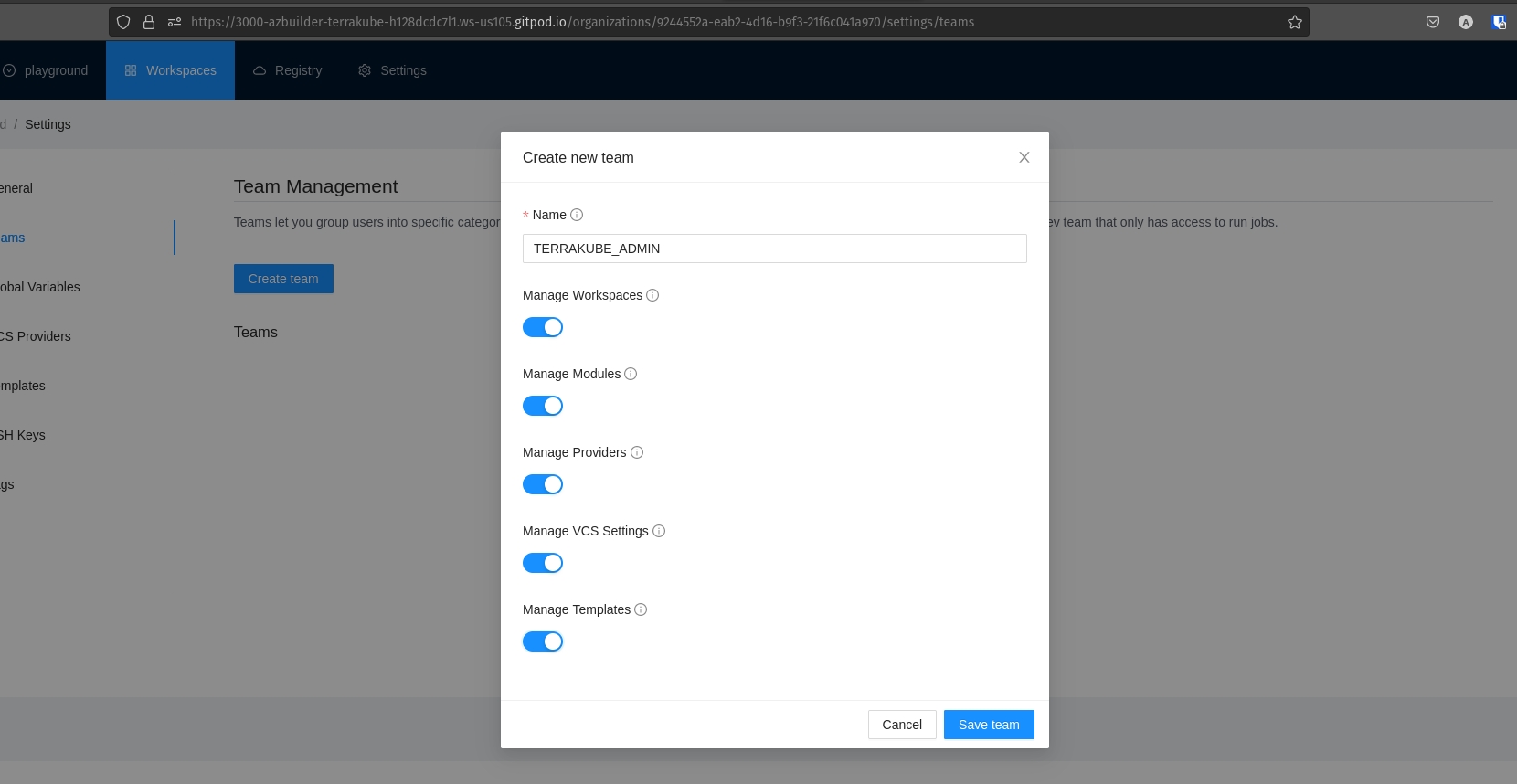
Once we have the playground organization, we need to add a team with access to create templates like the following:
We will also need a team with access to create/delete a workspace only, like the following:
Teams names will depend on your Dex configuration.
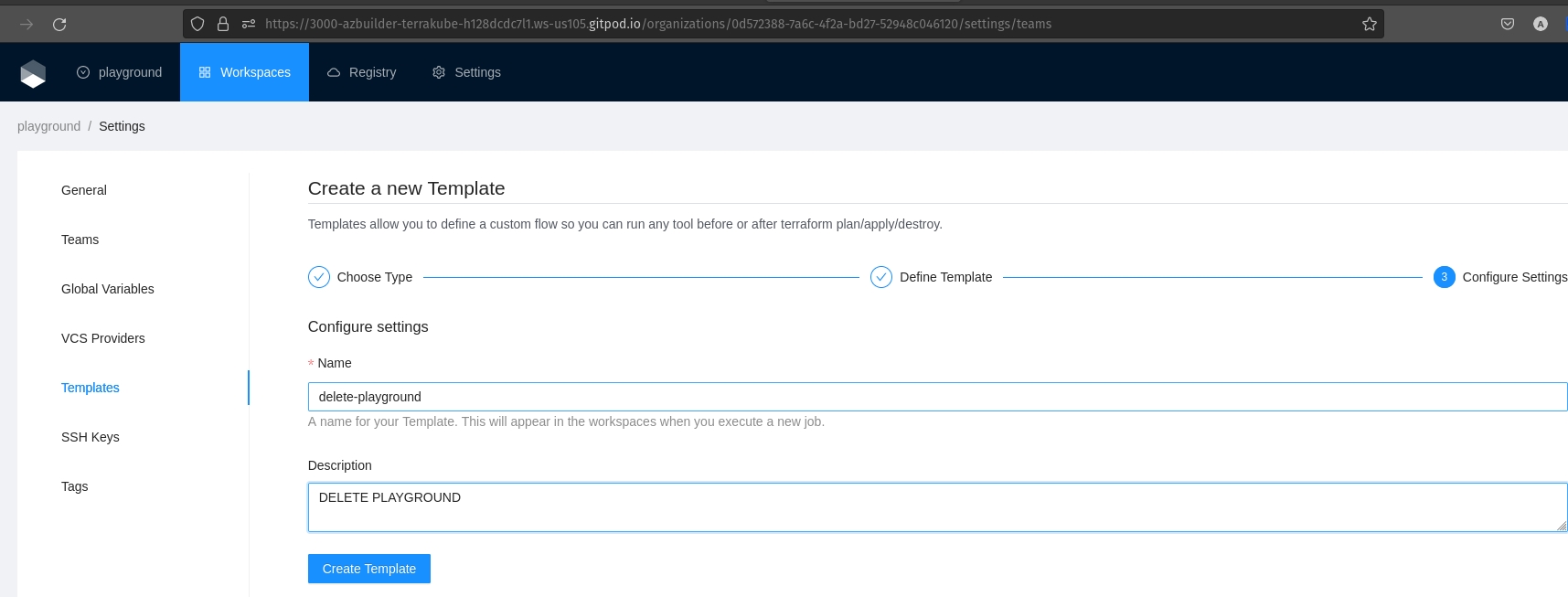
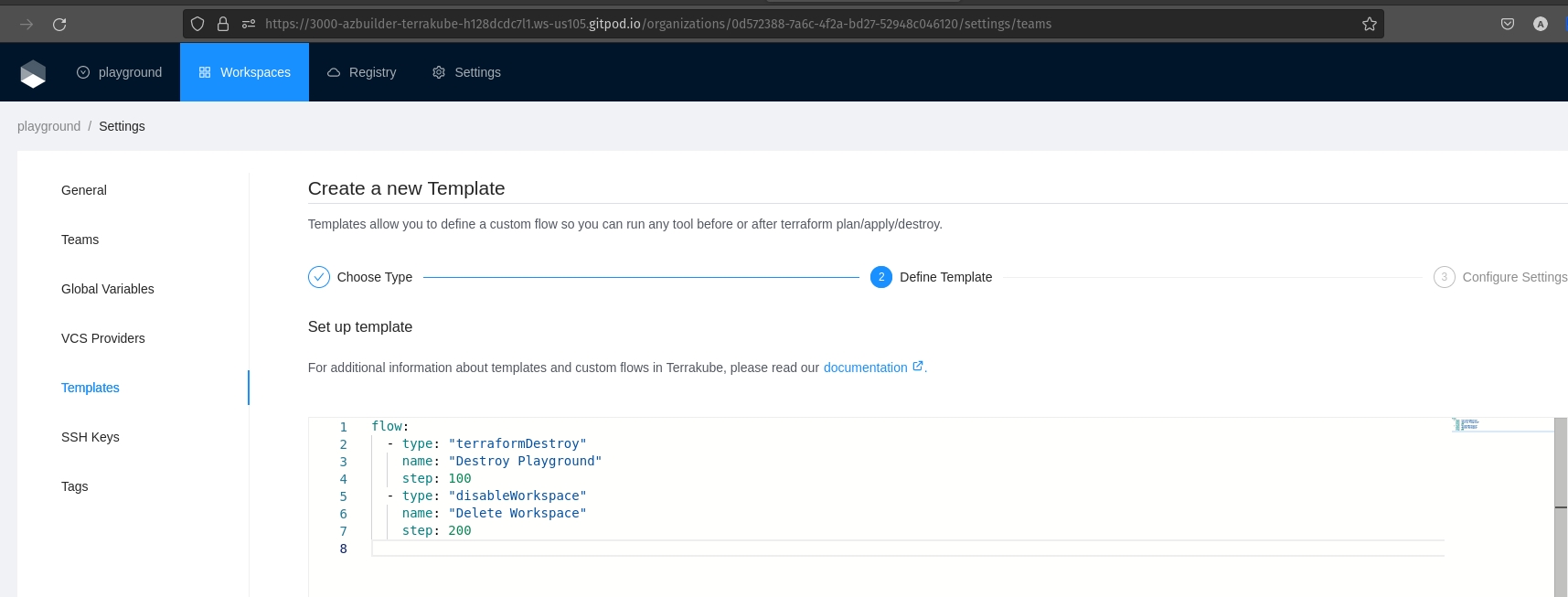
Once we have the two teams in our new playground organization, we can proceed and create a new template that we will be using to auto destroy all the workspace:
Lets call it "delete-playground" and it will have the following code:
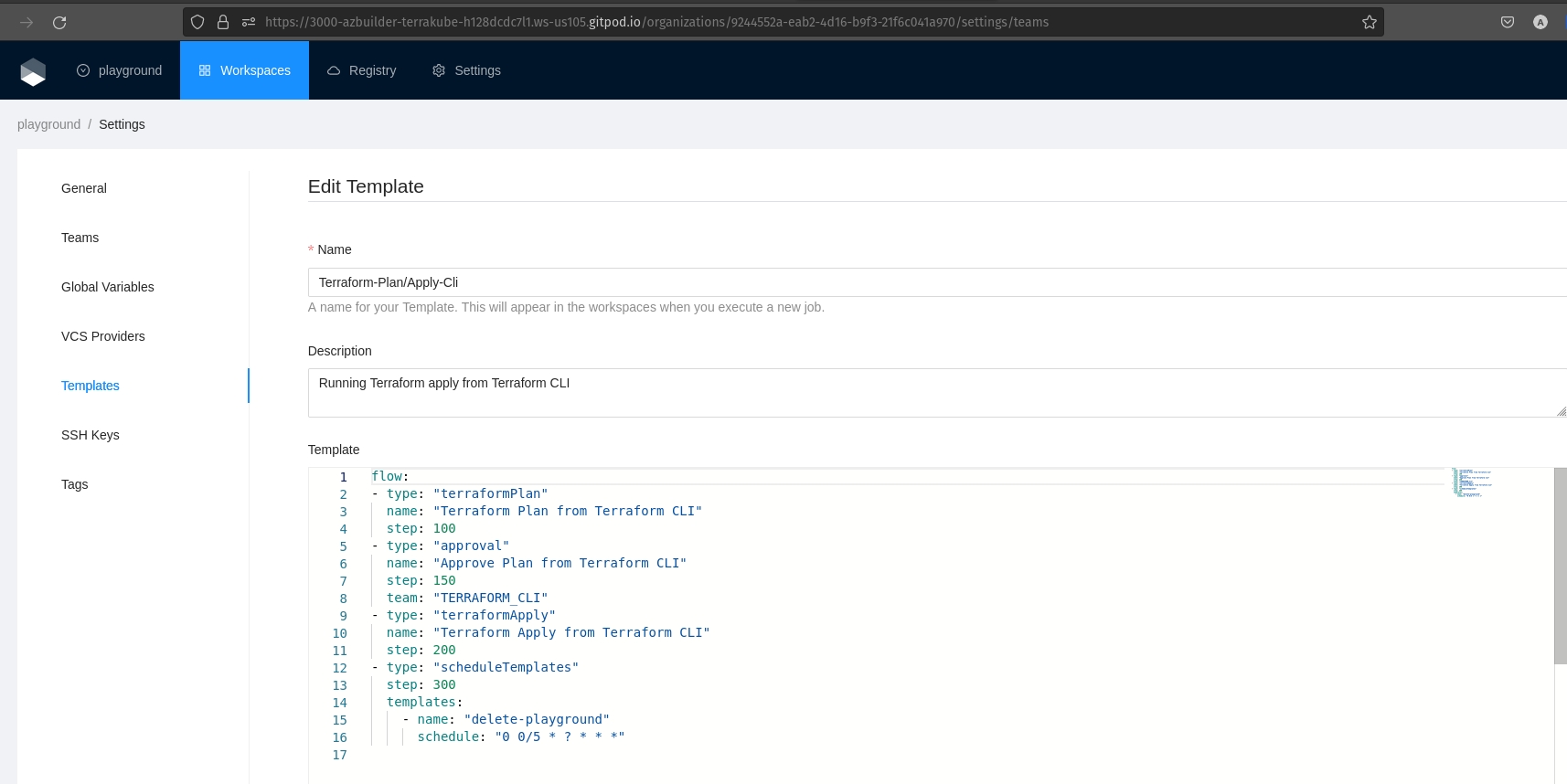
Now we can update the default template that is used when we are using the remote CLI-driven workflow, this template is inside every organization by default and is called "Terraform-Plan/Apply-Cli", usually we don't need to update this template but we will do some small changes to enable ephemeral workspaces in the playground organization.
We need to go the the templates inside the organization settings and edit the template
We will add a new step in the template, this will allow to schedule a job that will be using the "delete-playground" template that we have created above.
We need to use the following template code:
If we pay special attention we just add a new section where we define that the schedule will run every five minutes after the Terraform apply is completed.
In this example we will schedule the template every five minutes for testing purposes.
Now we need to define our Terraform code, lets use the following simple example:
Run terraform login to connect to our Terrakube instance:
Now we can run terraform init to initialize our workspace inside the playground organization, lets use "myplayground" for the name of our new workspace
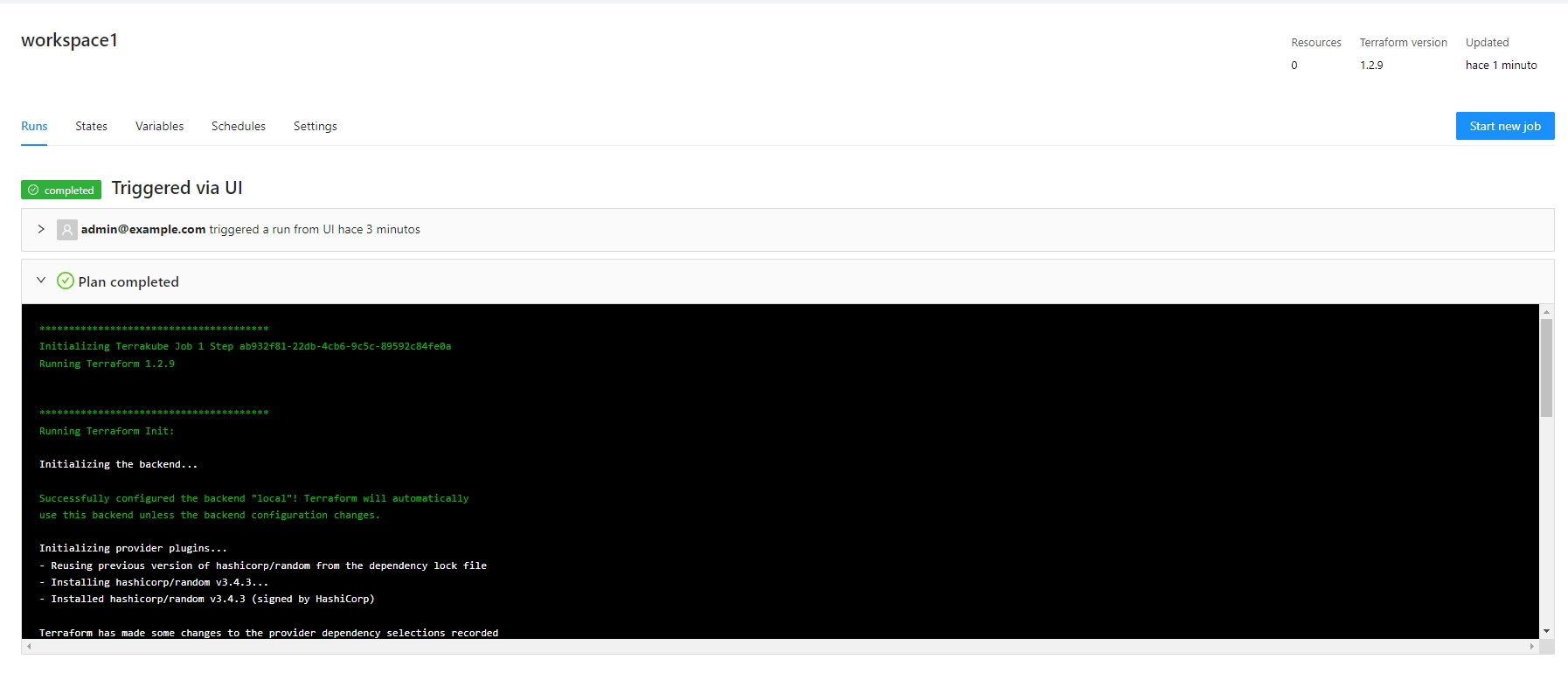
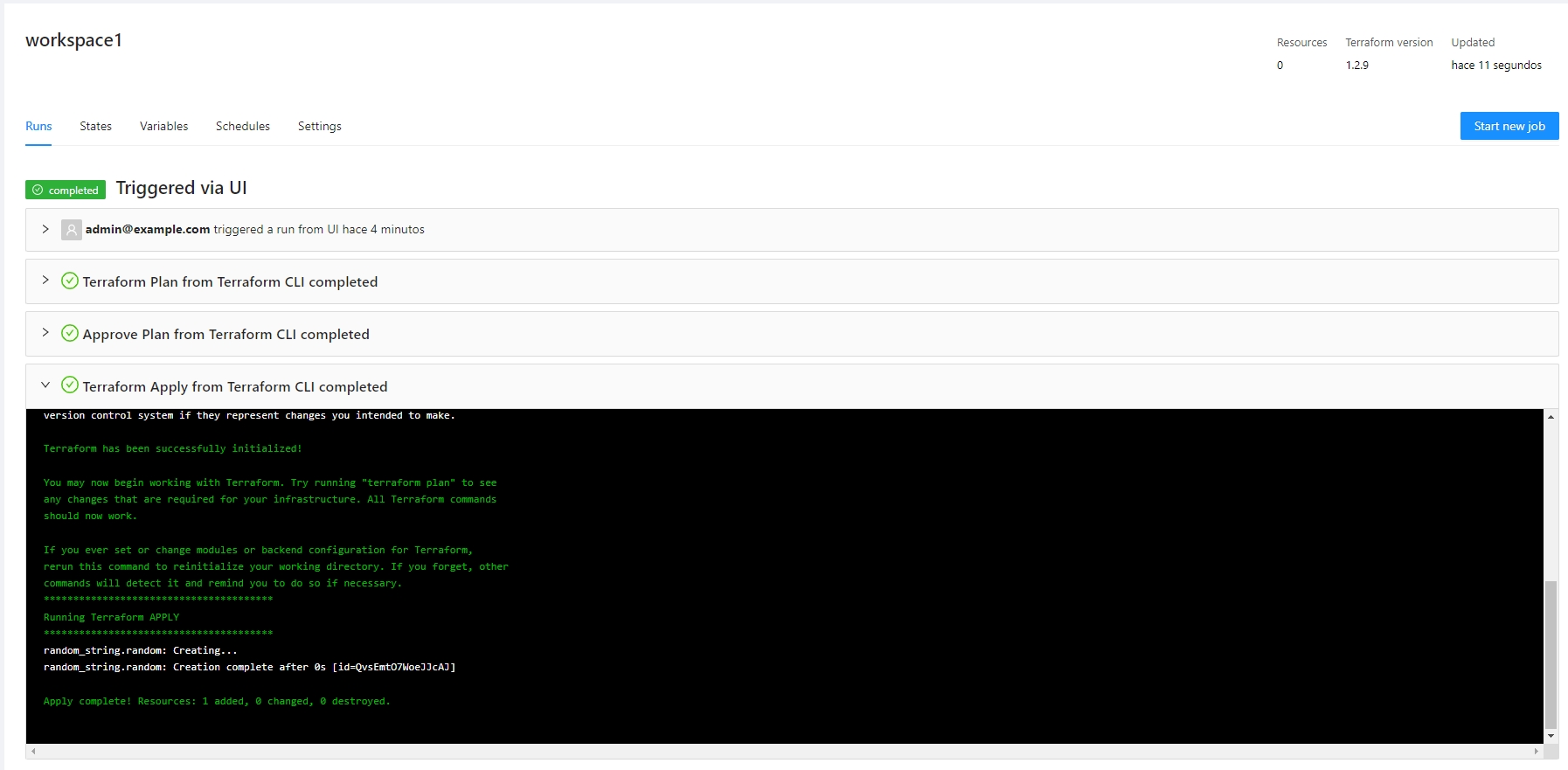
Let's run terraform apply and create our resources:
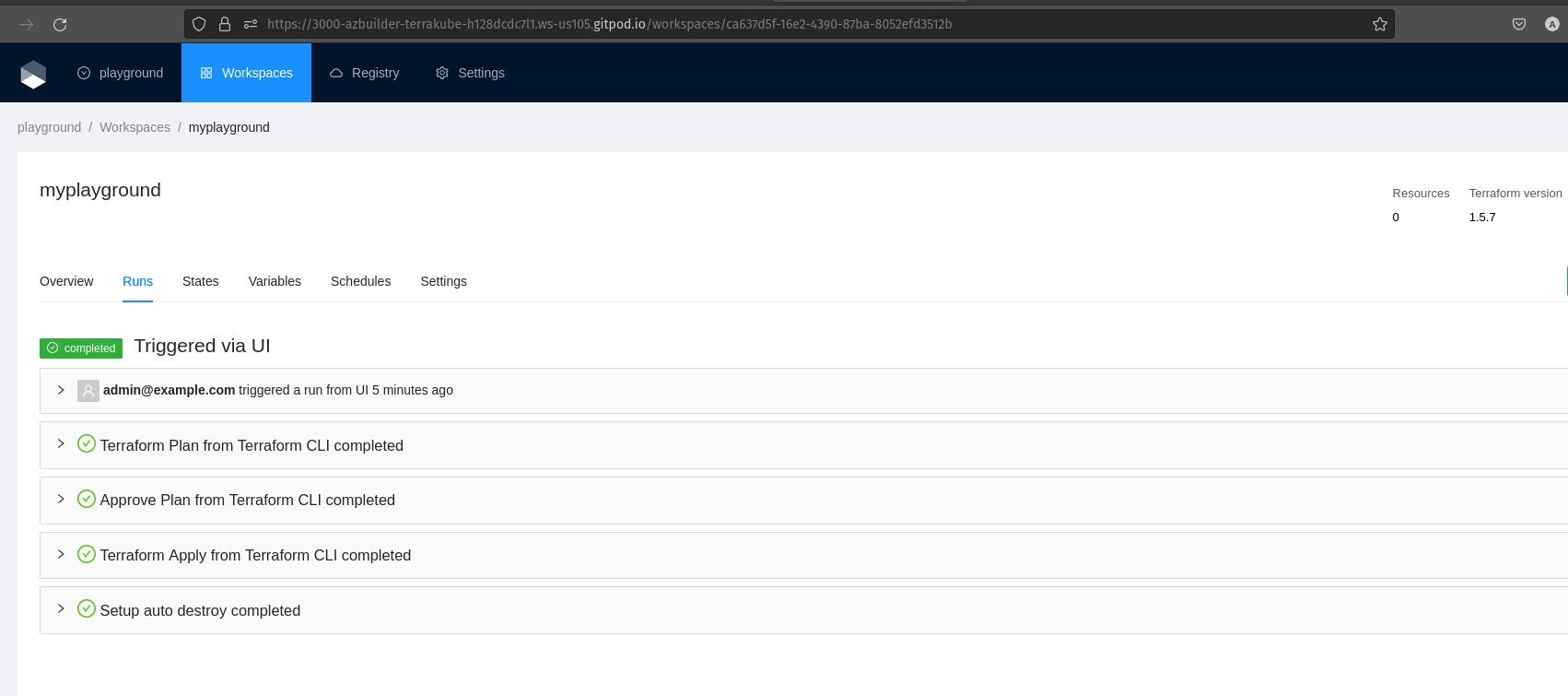
Our new workspace is created and if we go the organization we can see all the information
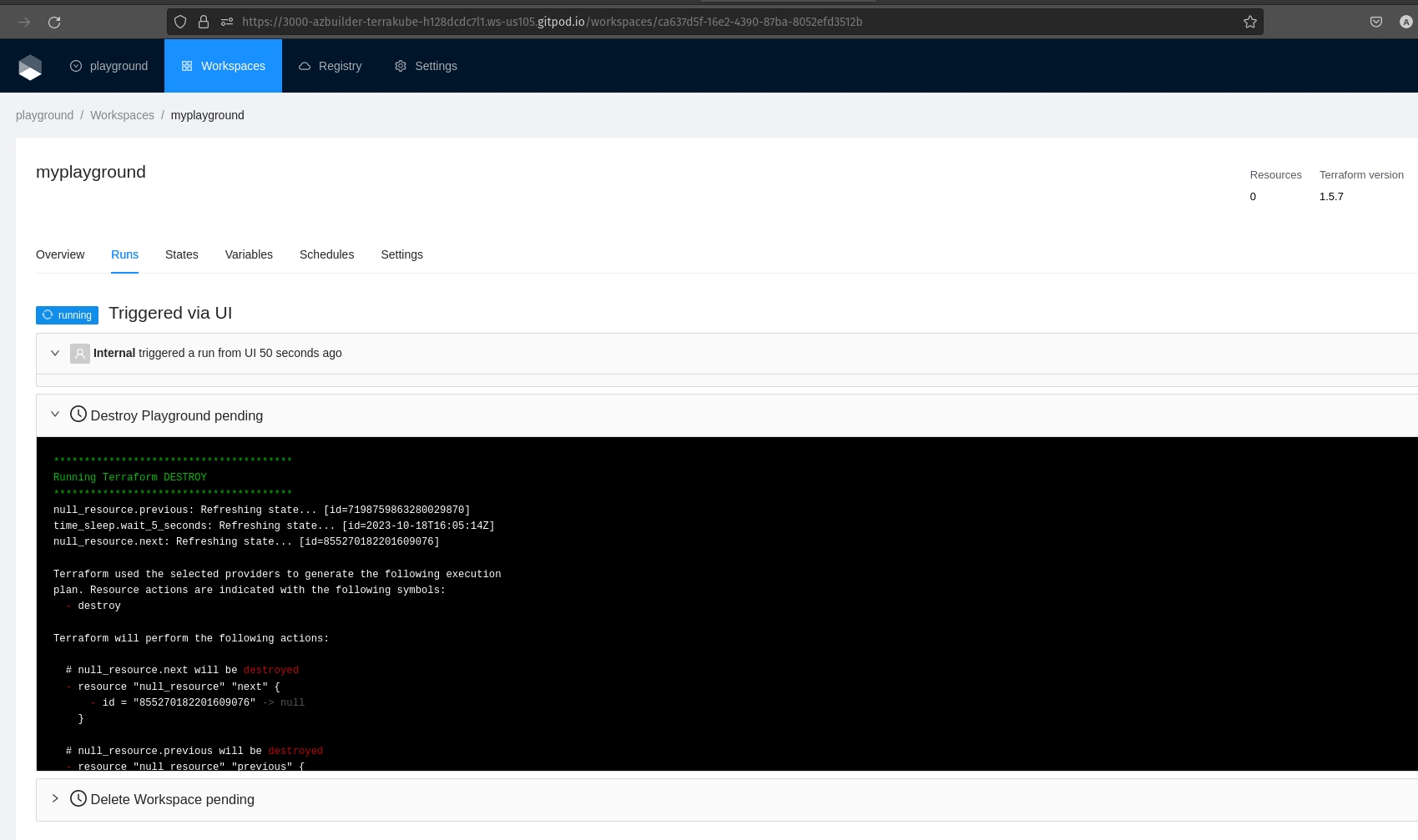
The job will be running to create the resources:
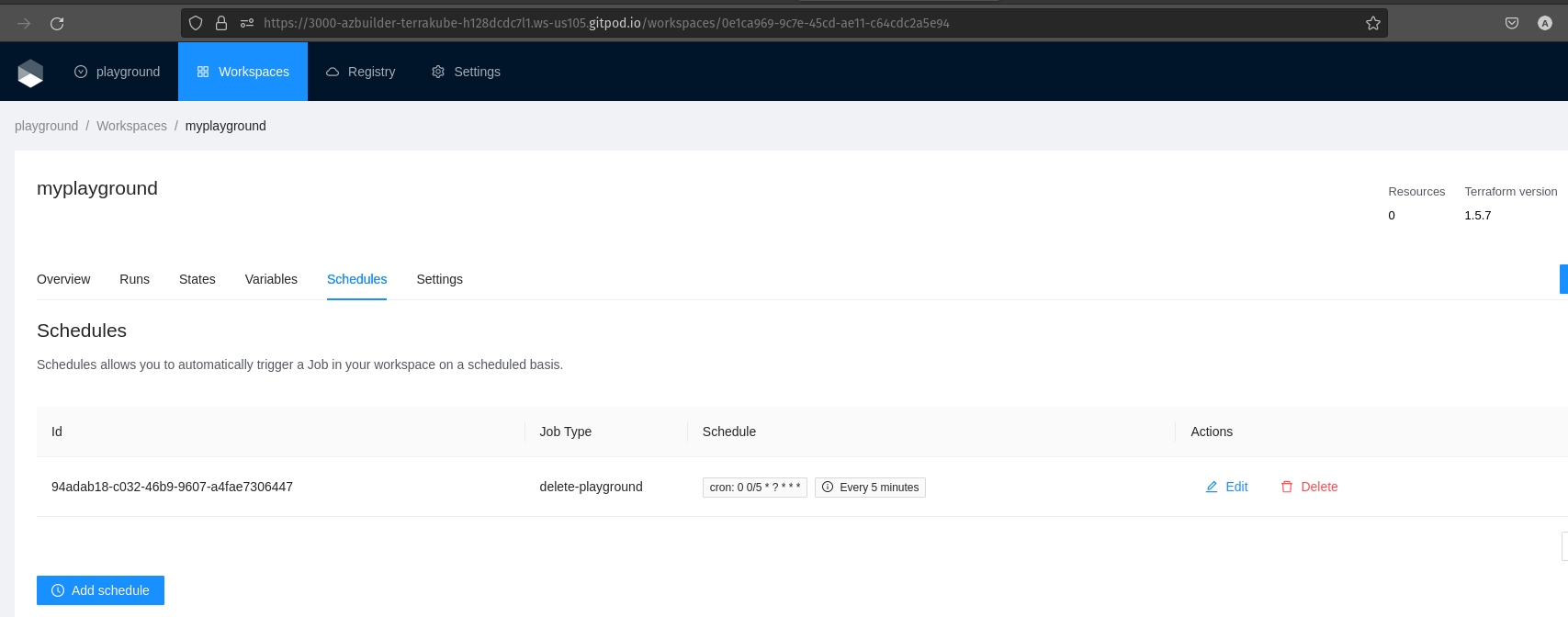
We can see that our job is completed and the setup auto destroy have created a new schedule for our workspace:
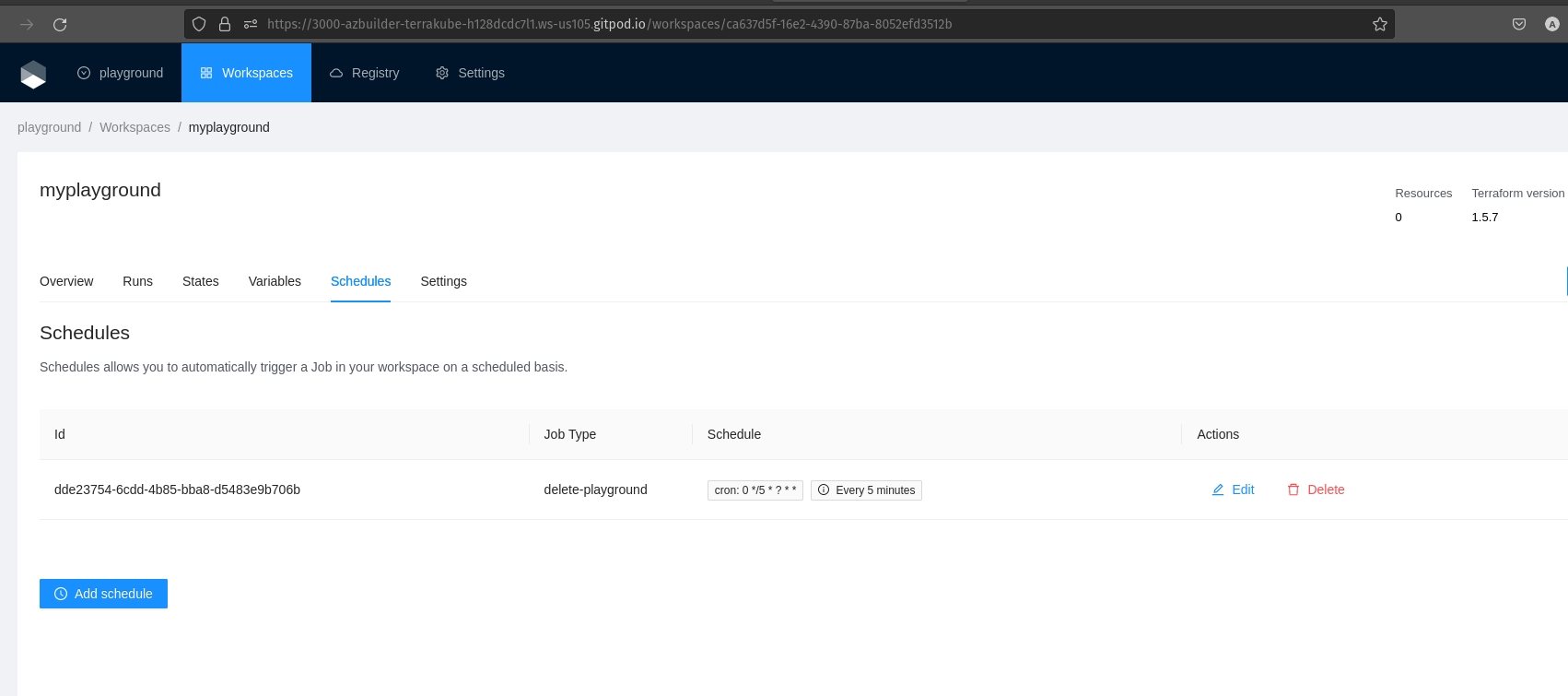
We could go to the schedules tab:
This schedule will run in 5 minutes:
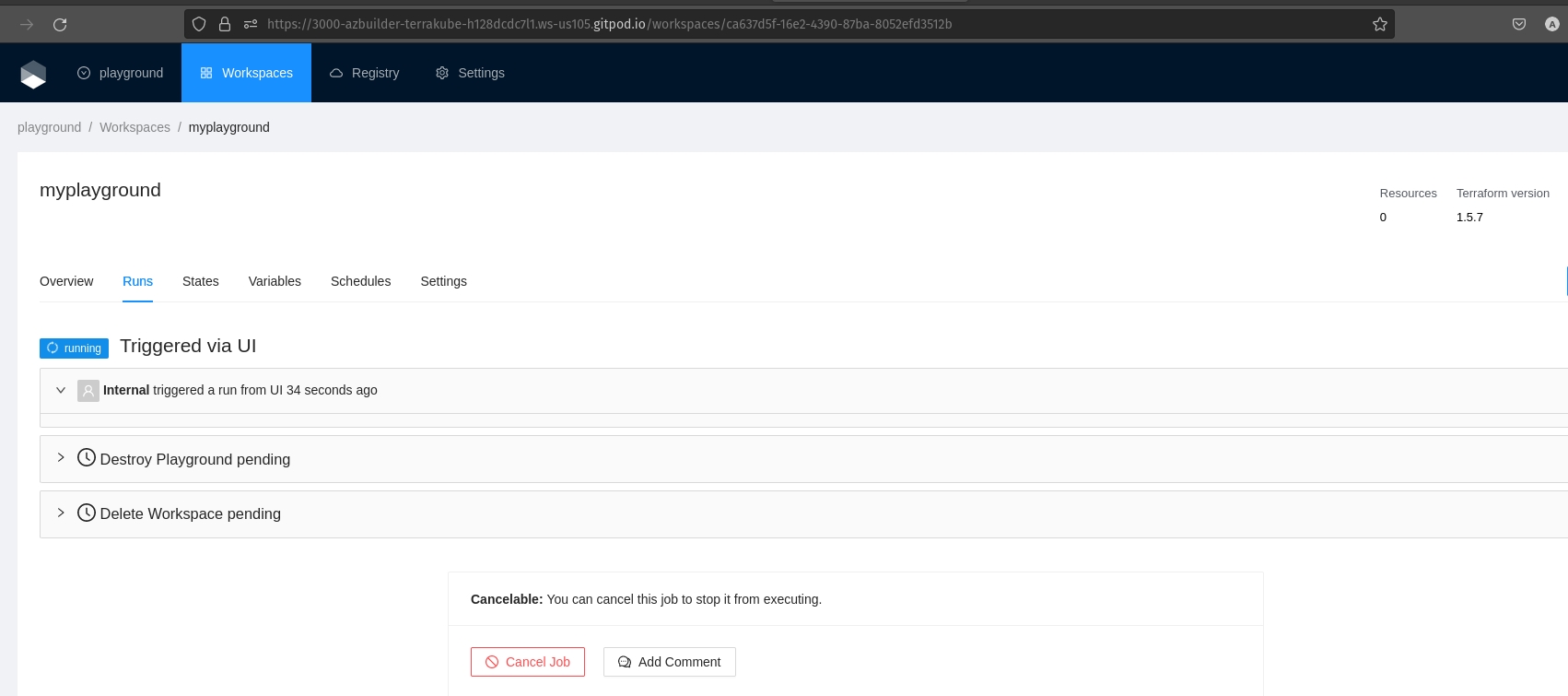
After waiting for 5 minutes we will see that Terrakube have created a new Job automatically
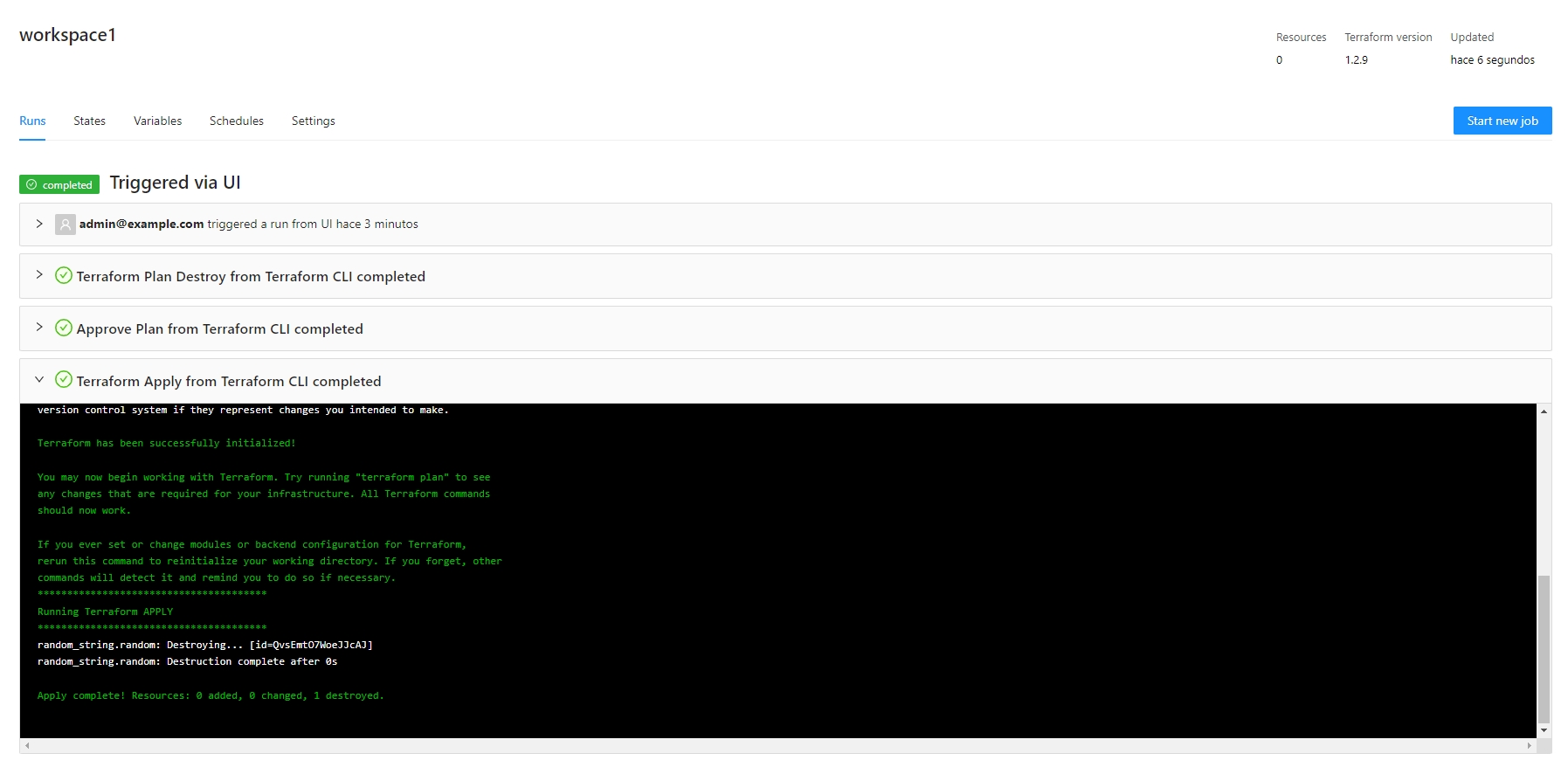
If we check the details for the new job we can see that a terraform destroy will be executed:
All of the workspace resources are deleted and the workspace will be deleted automatically after the destroy is completed.
Once the Job is completed, our workspace information is deleted from Terrakube
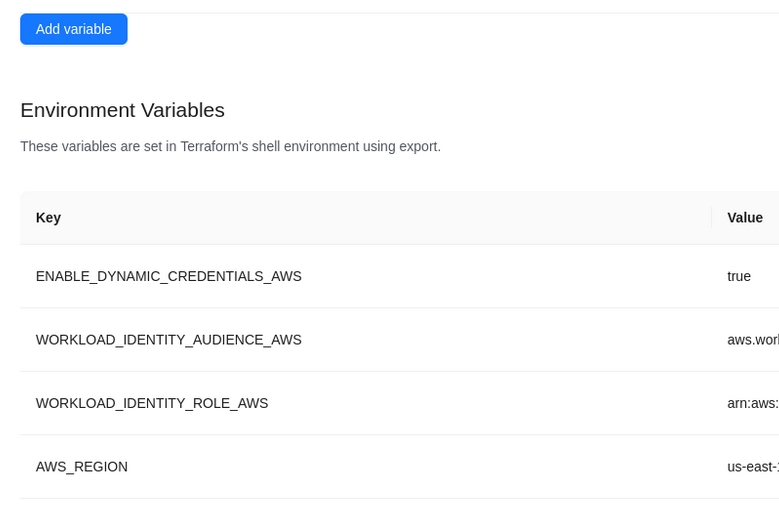
If we are using AWS, AZURE, GCP or any other terraform provider that allow to inject the credentials using environment variables we could use "global variables" to define those.
Global variables will be injected automatically to any workspace inside the playground organization.
To make this action more useful, you can make use of the context. The context is an object that contains data based on the . If you want to see all the data available for every action type, check the .
Now, if you click the Quick Start button, you will see a dialog with the comments data from the API. The proxy allows you to interact with external APIs and securely manage credentials. To learn more about the Actions proxy, check the .
Actions in Terrakube allow you to enhance the Workspace experience by creating custom interactions and functionalities tailored to your needs. You can start by exploring the to understand their implementation and gain more experience.
Actions are React components, and you define an to determine where the action will appear within the interface. Using , you can specify the precise conditions under which an action should be displayed, such as for specific organizations or Terraform versions.
Additionally, the enables integration with external APIs, securely managing credentials without requiring CORS configuration on the Terrakube front end. This is particularly useful when you don't have control over the external API's CORS settings.
Terrakube provides several that you can start using some are enabled by default. Please refer to the documentation for detailed information on each action, including usage and setup instructions.
If you are interested in creating your own actions, you only need knowledge of JavaScript and React, as an action is essentially a React component. For more details please check our , or visit our to see some examples, contribute new actions or suggest improvements.
The schedule is using Quartz format, to learn more about this use this .
ID
terrakube.quick-start
Name
Quick Start
Type
Workspace/Action
Label
Quick Start
Category
General
Version
1.0.0
Description
Quick Start action
Display Criteria
Add a new display criteria and enter true. This means the action will appear always
Action
Add the above code
Active
Enable
ID
A unique ID for your action. Example: terrakube.demo-action or myorg.my-action
Name
A unique name for your action.
Type
Defines the section where this action will appear. Refer to Action Types to see the specific area where the action will be rendered.
Label
For tabs actions, this will be displayed as the tab name. For action buttons, it should be displayed as the button name.
Category
This helps to organize the actions based on their function. Example: General, Azure, Cost, Monitor.
Version
Must follow semantic versioning (e.g., 1.0.0).
Description
A brief description of the action.
Display Criteria
Defines the conditions under which the action should appear based on the context. For more details, check the Display Criteria documentation.
Action
A JavaScript function equivalent to a React component. Receives the context with some data related to the context. See our quick start guide to start creating actions
Active
Enables or disables an action.
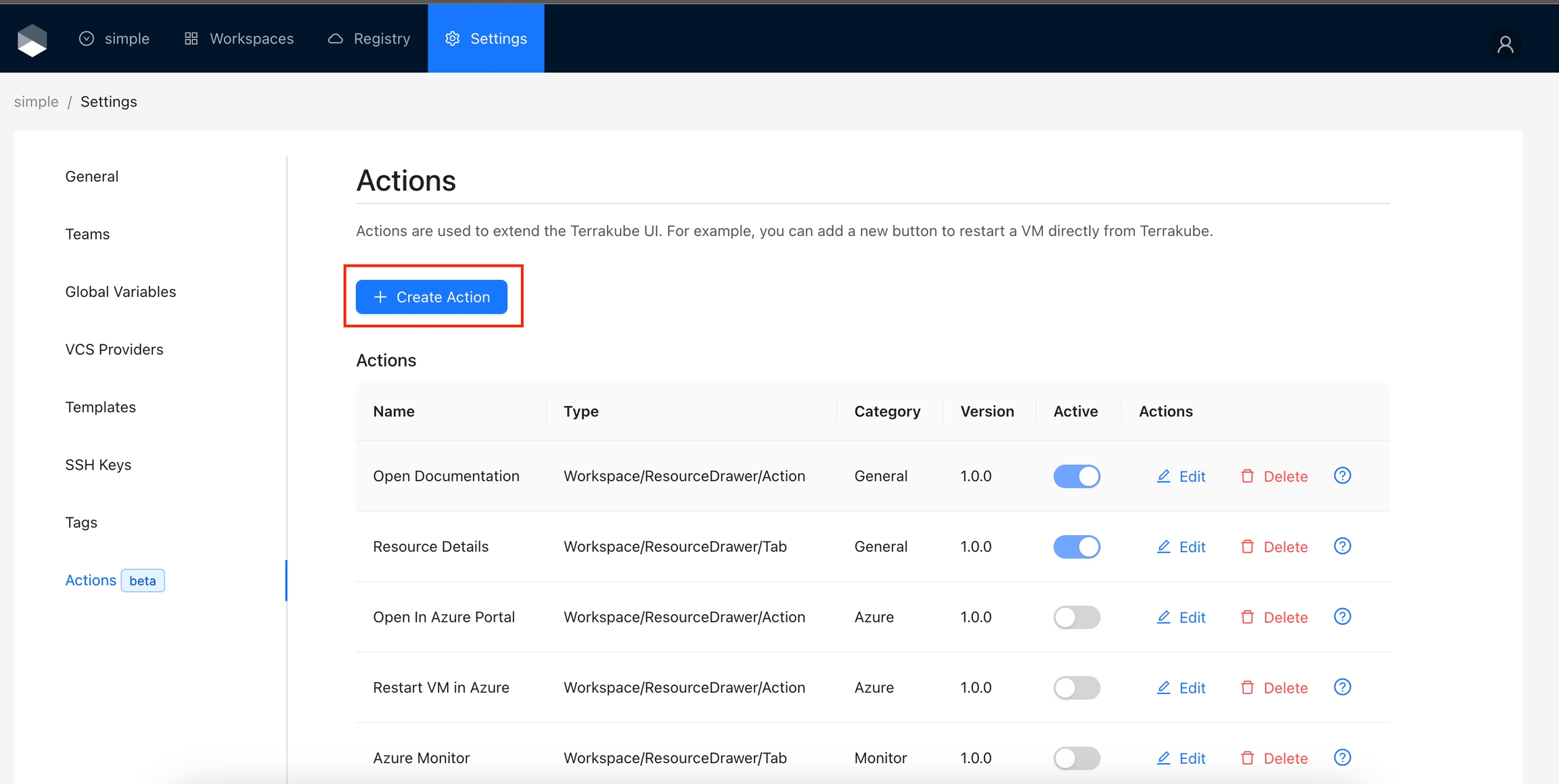
The following actions are added by default in Terrakube. However, not all actions are enabled by default. Please refer to the documentation below if you are interested in activating these actions.
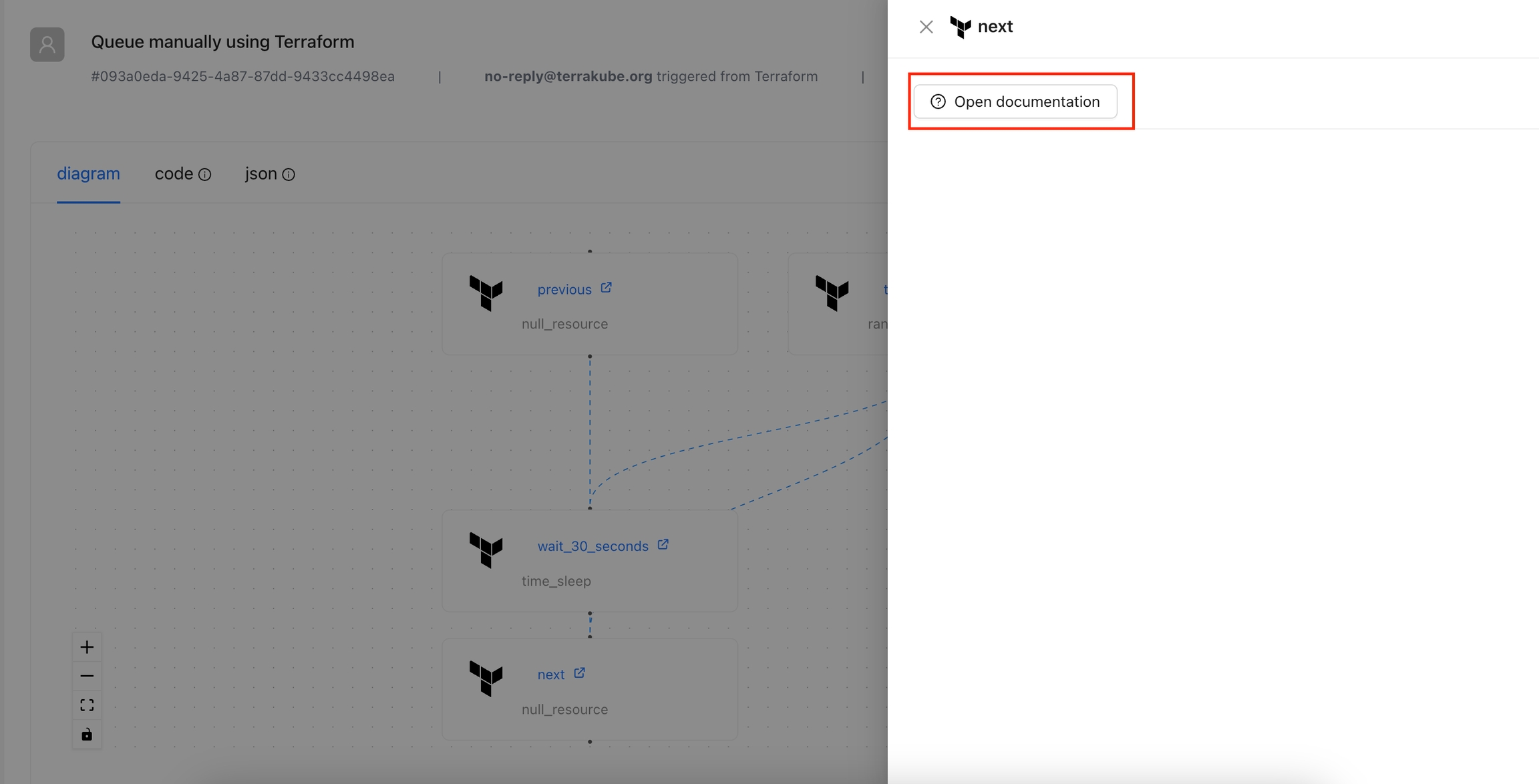
Open Documentation: Adds a button to quickly navigate to the Terraform registry documentation for a specific resource.
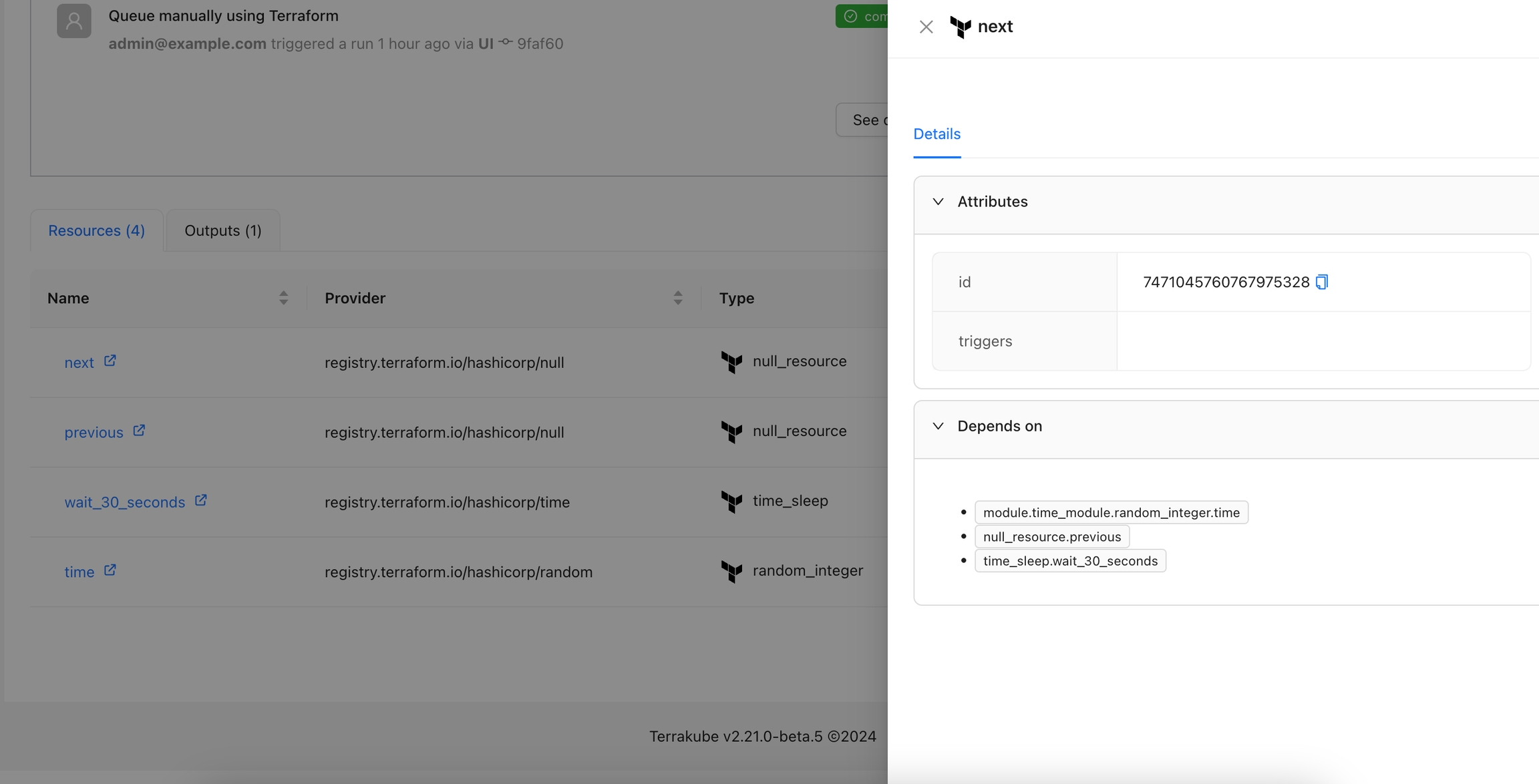
Resource Details: Adds a new panel to visualize the state attributes and dependencies for a resource.
Open in Azure Portal: Adds a button to quickly navigate to the resource in the Azure Portal.
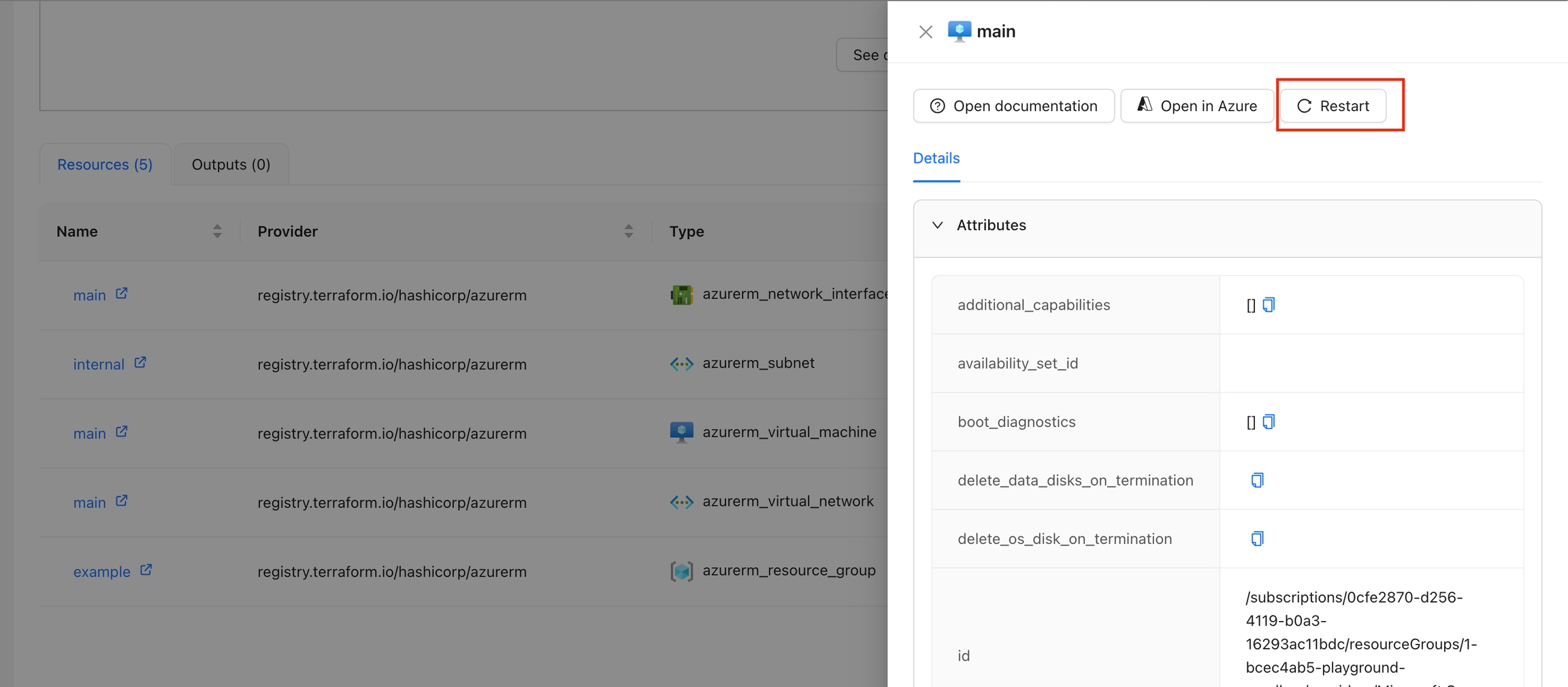
Restart Azure VM: Adds a button to restart the Azure VM directly from the workspace overview.
Azure Monitor: Adds a panel to visualize the metrics for the resource.
Open AI: Adds a button to ask questions or get recommendations using OpenAI based on the workspace data.
The Action Proxy allows you to call other APIs without needing to add the Terrakube frontend to the CORS settings, which is particularly useful if you don't have access to configure CORS. Additionally, it can be used to inject Workspace variables and Global variables into your requests.
The proxy supports POST, GET, PUT, and DELETE methods. You can access it using the axiosInstance variable, which contains an Axios object.
To invoke the proxy, use the following URL format: ${context.apiUrl}/proxy/v1
When calling the Action Proxy, use the following required parameters:
targetUrl: Contains the URL that you want to invoke.
proxyHeaders: Contains the headers that you want to send to the target URL.
workspaceId: The workspace ID that will be used for some validations from the proxy side
If you need to access sensitive keys or passwords from your API call, you can inject variables using the template notation ${{var.variable_name}}, where variable_name represents a Workspace variable or a Global variable.
If you have a Global variable and a Workspace variable with the same name, the Workspace variable value will take priority.
Example Usage
In this example:
${{var.OPENAI_API_KEY}} is a placeholder for a sensitive key that will be injected by the proxy.
proxyBody contains the data to be sent in the request body.
proxyHeaders contains the headers to be sent to the target URL.
targetUrl specifies the API endpoint to be invoked.
workspaceId is used for validations on the proxy side.
By using the Action Proxy, you can easily interact with external APIs while using Terrakube's capabilities to manage and inject necessary variables securely.
The context object contains data related to the Workspace that you can use inside the action. The properties depends on the Action Type.
Tip
Inside your action you can use console.log(context) to quickly explore the available properties for the context
Contains the workspace information in the Terrakube api format. See the docs for more details on the properties available.
context.workspace.id: Id of the workspace
context.workspace.attributes.name: Name of the workspace
context.workspace.attributes.terraformVersion: Terraform version
workspace/action
workspace/resourcedrawer/action
workspace/resourcedrawer/tab
Contains the settings that you configured in the display criteria.
context.settings.Repository: the value of repository that you set for the setting. Example:
workspace/action
workspace/resourcedrawer/action
workspace/resourcedrawer/tab
For workspace/action this property contains the full terraform or open tofu state. For workspace/resourcedrawer/action and workspace/resourcedrawer/tab contains only the section of the resource
workspace/action
workspace/resourcedrawer/action
workspace/resourcedrawer/tab
Contains the Terrakube api Url. Useful if you want to use the Action Proxy or execute a call to the Terrakube API.
workspace/action
workspace/resourcedrawer/action
workspace/resourcedrawer/tab
Display Criteria offer a flexible way to determine when an action will appear. While you can add logic inside your component to show or hide the action, using display criteria provides additional advantages:
Optimize Rendering: Save on the loading cost of each component.
Multiple Criteria: Add multiple display criteria based on your requirements.
Conditional Settings: Define settings to be used when the criteria are met.
A display criteria is a JavaScript condition where you can use the data from the Action Context to decide if the action will appear.
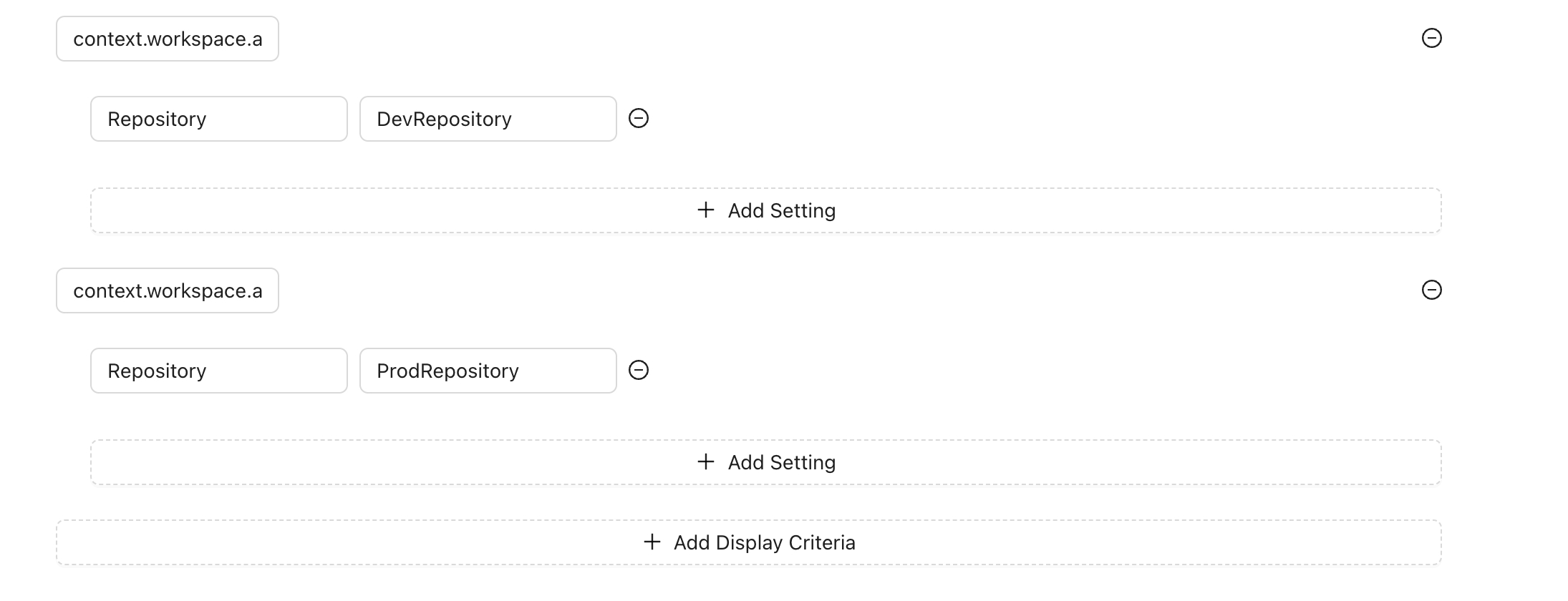
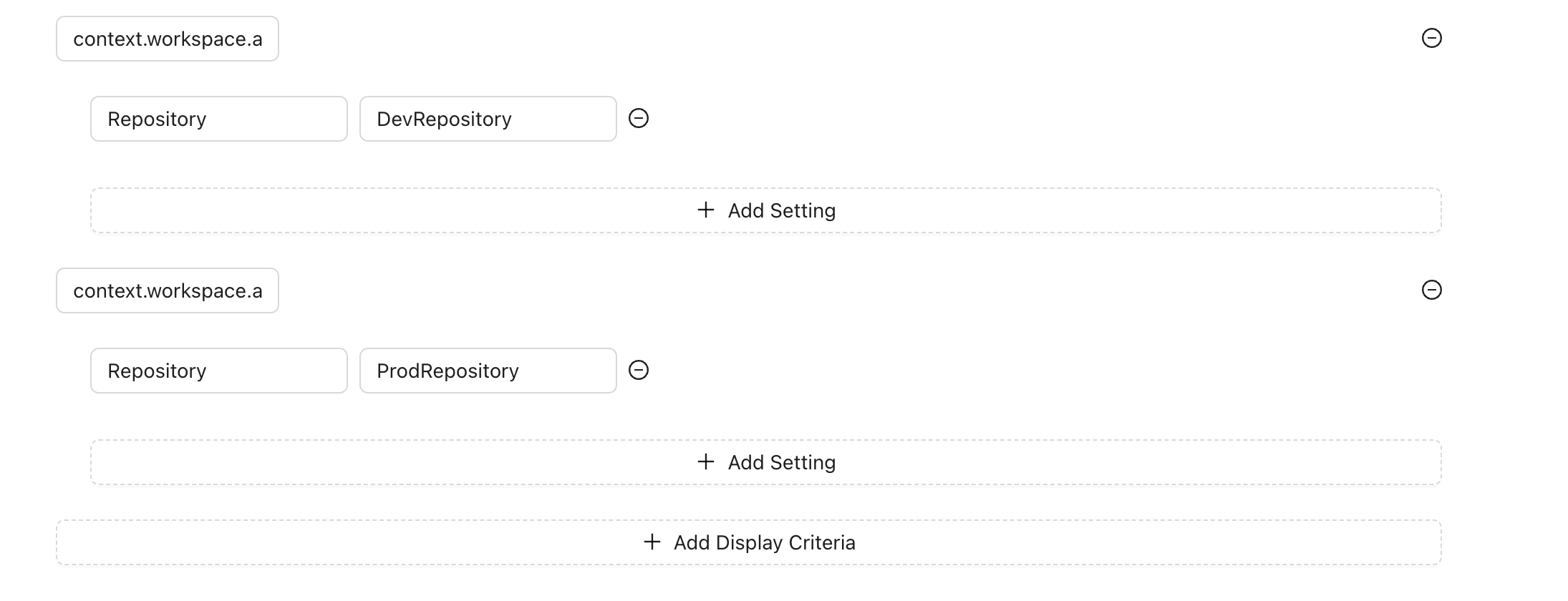
You can set specific settings for each display criteria, which is useful when the action provides configurable options. For example, suppose you have an action that queries GitHub issues using the GitHub API and you want to display the issues using GraphQL. Your issues are stored in two different repositories: one for production and one for non-production.
In this case, you can create settings based on the display criteria to select the repository name. This approach allows your action code to be reusable. You only need to change the settings based on the criteria, rather than modifying the action code itself.
For instance:
Production Environment: For workspaces starting with prod, use the repository name for production issues.
Non-Production Environment: Use the repository name for non-production issues
By setting these configurations, you ensure that your action dynamically adapts to different environments or conditions, enhancing reusability and maintainability.
You might be tempted to store secrets inside settings; however, display criteria settings don't provide a secure way to store sensitive data. For cases where you need to use different credentials for an action based on your workspace, organization or any other condition, you should use template notation instead. This approach allows you to use Workspace Variables or Global Variables to store sensitive settings securely.
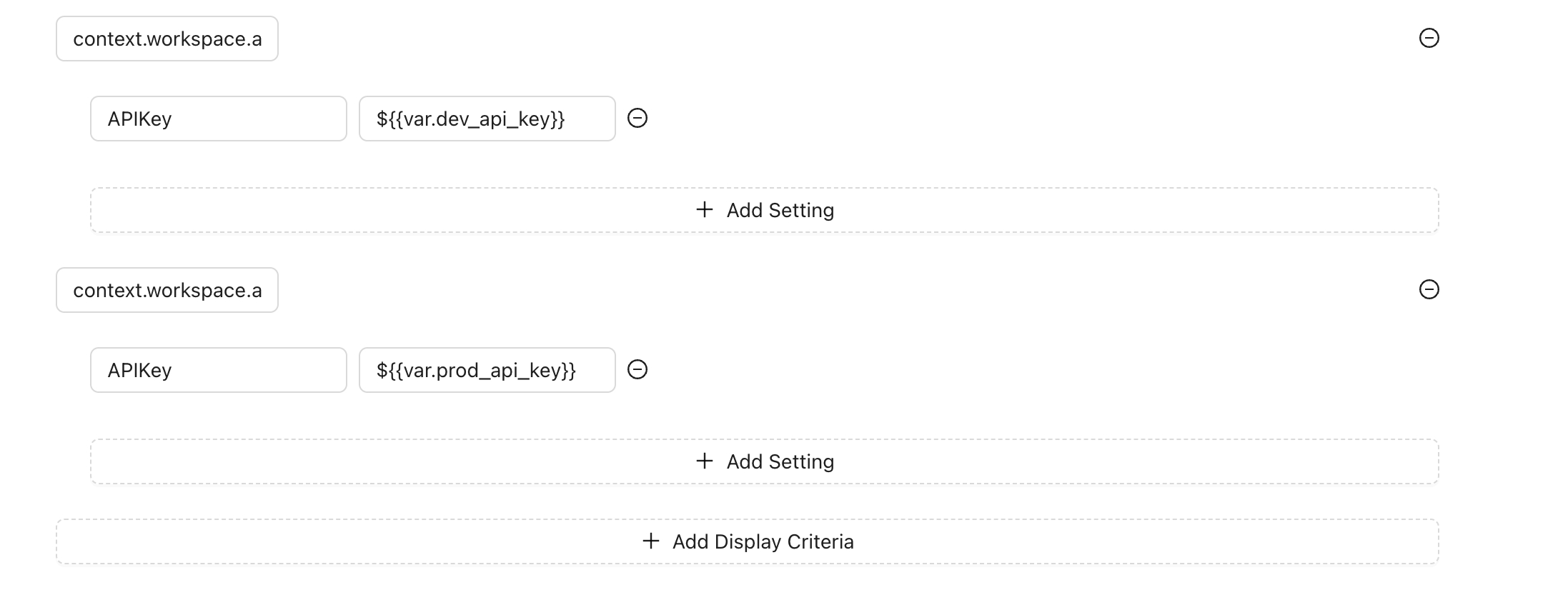
For example, instead of directly storing an API key in the settings, you can reference a variable:
For the development environment: ${{var.dev_api_key}}
For the production environment: ${{var.prod_api_key}}
For the previous example, you will need to create the variables at workspace level or use global variables with the names dev_api_keyand prod_api_key
For more details about using settings in your action and template variables check Action Proxy.
You can define multiple display criteria for your actions. In this case, the first criteria to be met will be applied, and the corresponding settings will be provided via the context.
The dynamic provider credential setup in Azure can be done with the Terrraform code available in the following link:
https://github.com/AzBuilder/terrakube/tree/main/dynamic-credential-setup/azure
The code will also create a sample workspace with all the require environment variables that can be used to test the functionality using the CLI driven workflow.
Make sure to mount your public and private key to the API container as explained here
Mare sure the private key is in "pkcs8" format
Validate the following terrakube api endpoints are working:
Set terraform variables using: "variables.auto.tfvars"
To generate the API token check here
Run Terraform apply to create all the federated credential setup in AWS and a sample workspace in terrakube for testing
To test the following terraform code can be used:
When running a job Terrakube will correctly authenticate to Azure without any credentials inside the workspace
Action Types define where an action will appear in Terrakube. Here is the list of supported types:
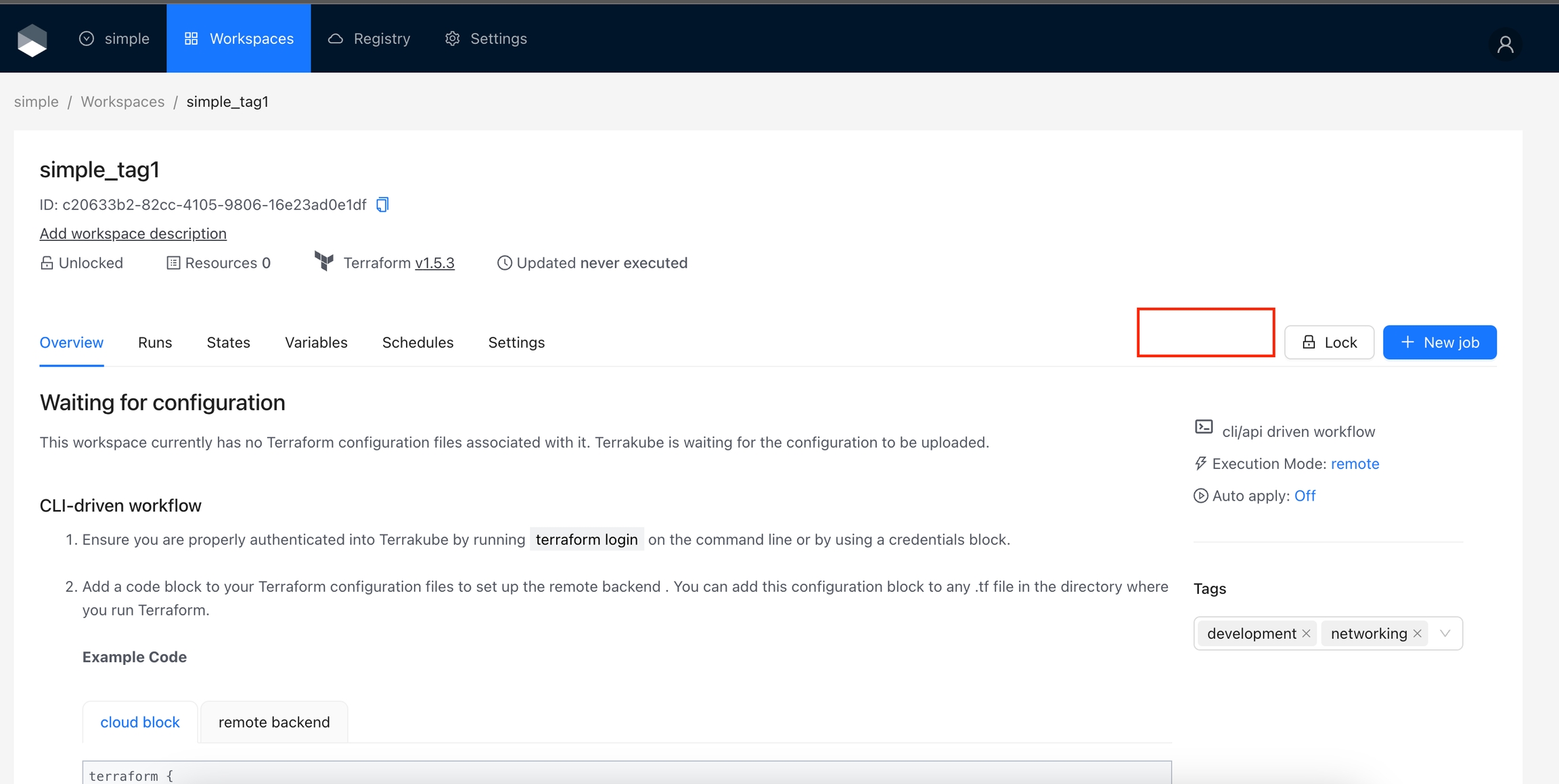
The action will appear on the Workspace page, next to the Lock button. Actions are not limited to buttons, but this section is particularly suitable for adding various kinds of buttons. Use this type for actions that involves interaction with the Workspace
The action will appear for each resource when you click on a resource using the Overview Workspace page or the Visual State Diagram. Use this when an action applies to specific resources, such as restarting a VM or any actions that involve interaction with the resource.
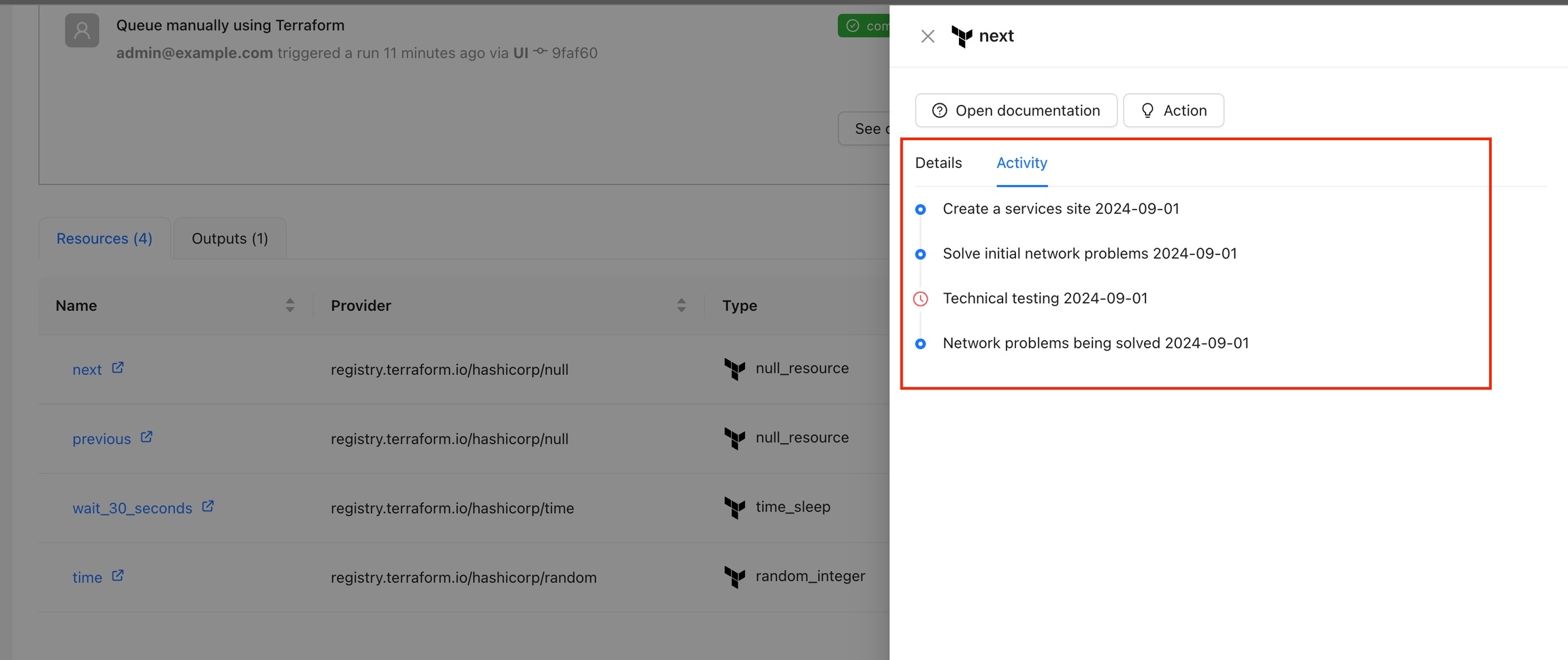
The action will appear for each resource when you click on a resource using the Overview Workspace page or the Visual State Diagram. Use this when you want to display additional data for the resource, such as activity history, costs, metrics, and more.
For this type, theLabel property will be used as the name of the Tab pane.
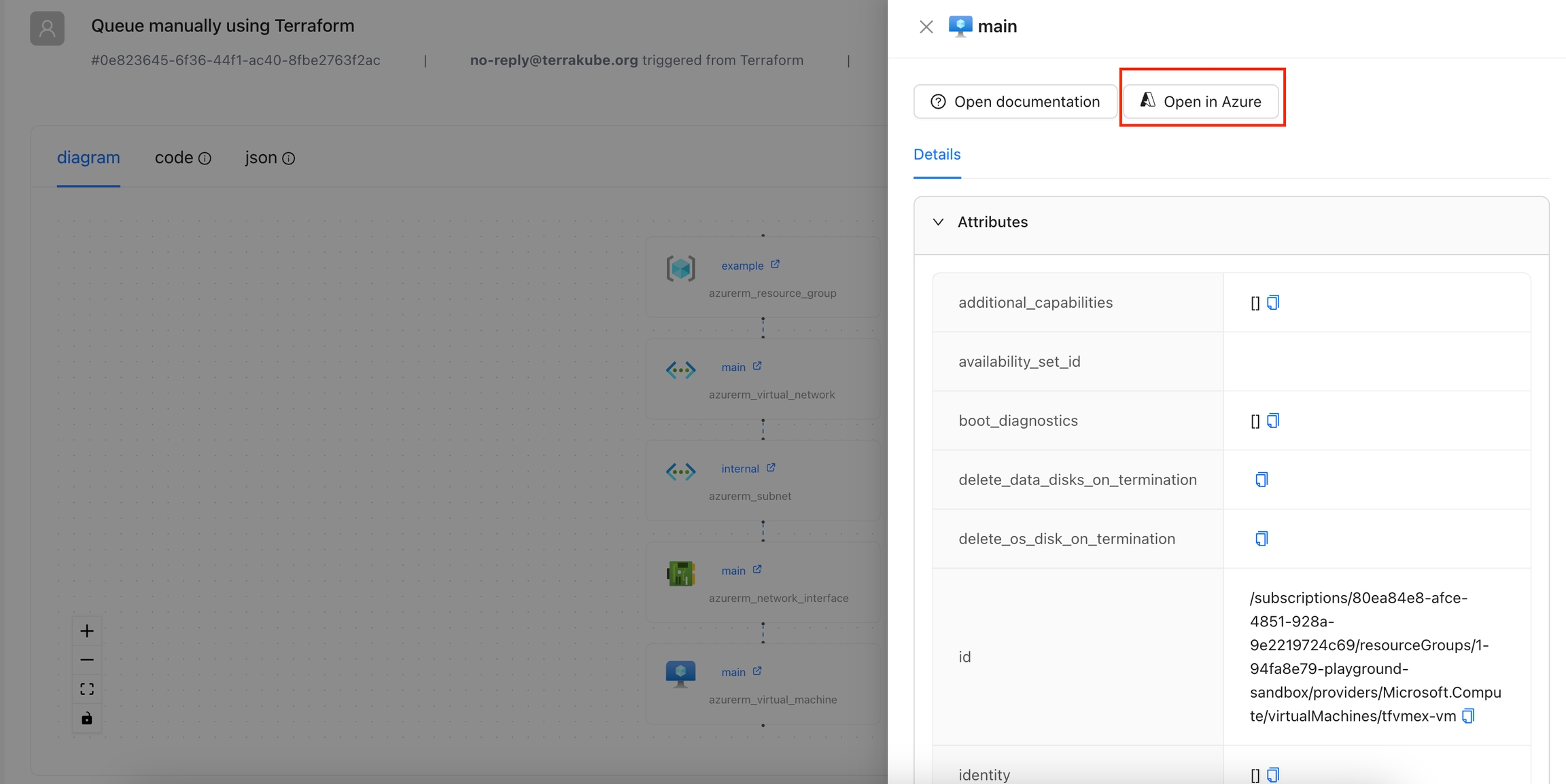
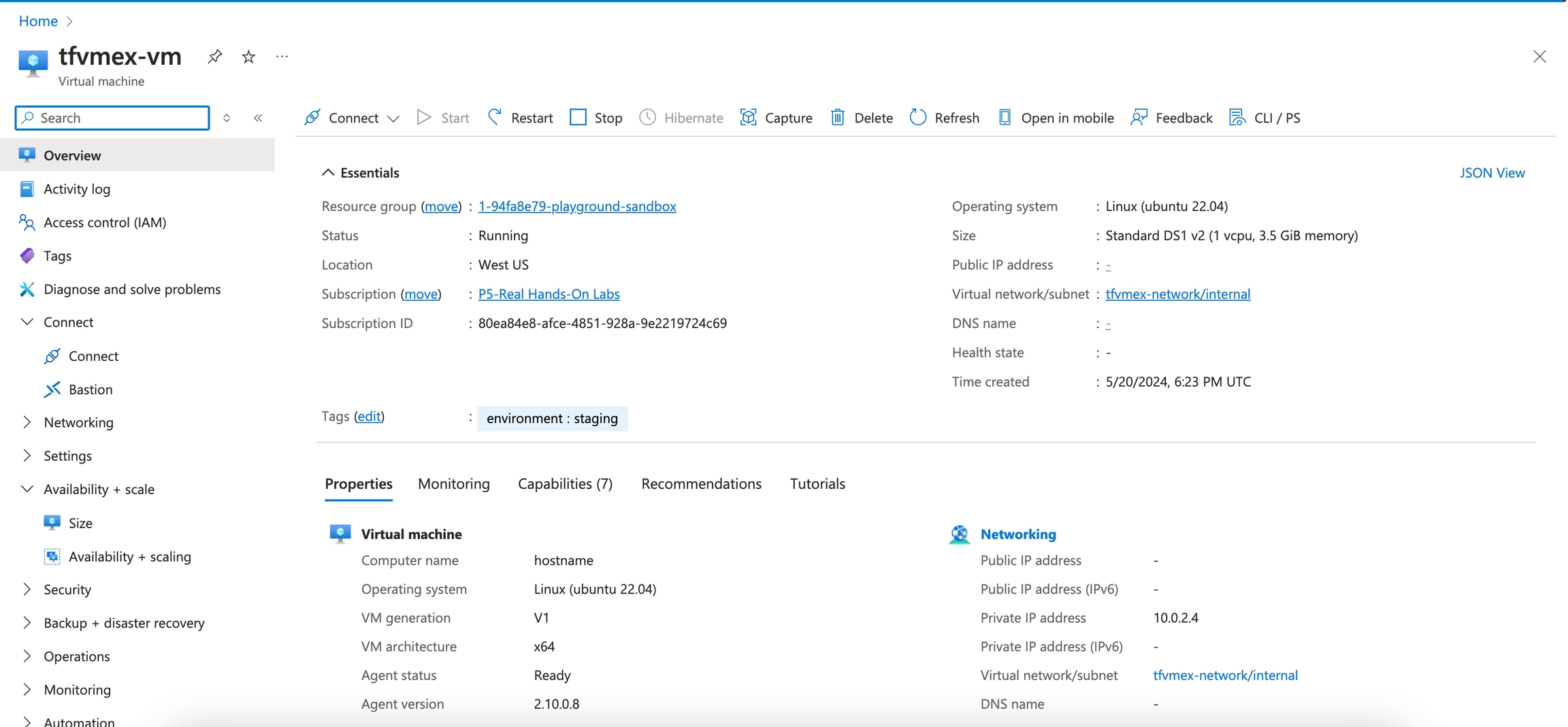
The Open In Azure Portal action is designed to provide quick access to the Azure portal for a specific resource. By using the context of the current state, this action constructs the appropriate URL and presents it as a clickable button.
By default, this Action is disabled and when enabled will appear for all the azurerm resources. If you want to display this action only for certain resources, please check display criteria.
Navigate to the Workspace Overview or the Visual State and click a resource name.
In the Resource Drawer, click the Open in Azure button.
You will be able to see the Azure portal for that resource.
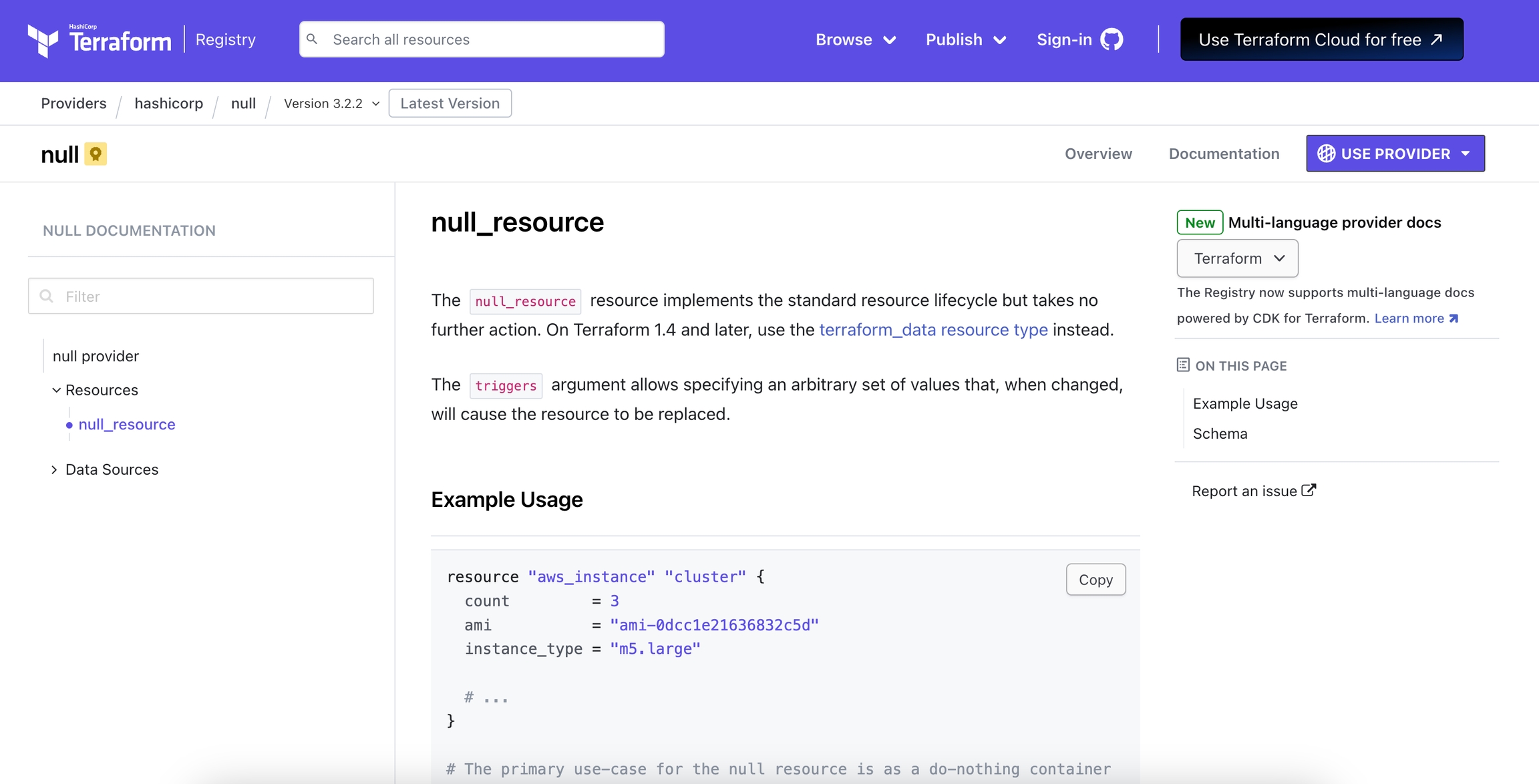
The Open Documentation action is designed to provide quick access to the Terraform registry documentation for a specific provider and resource type. By using the context of the current state, this action constructs the appropriate URL and presents it as a clickable button.
By default this Action is enabled and will appear for all the resources. If you want to display this action only for certain resources, please check display criteria.
Navigate to the Workspace Overview or the Visual State and click a resource name.
In the Resource Drawer, Click the Open documentation button
You will be able to see the documentation for that resource in the Terraform registry
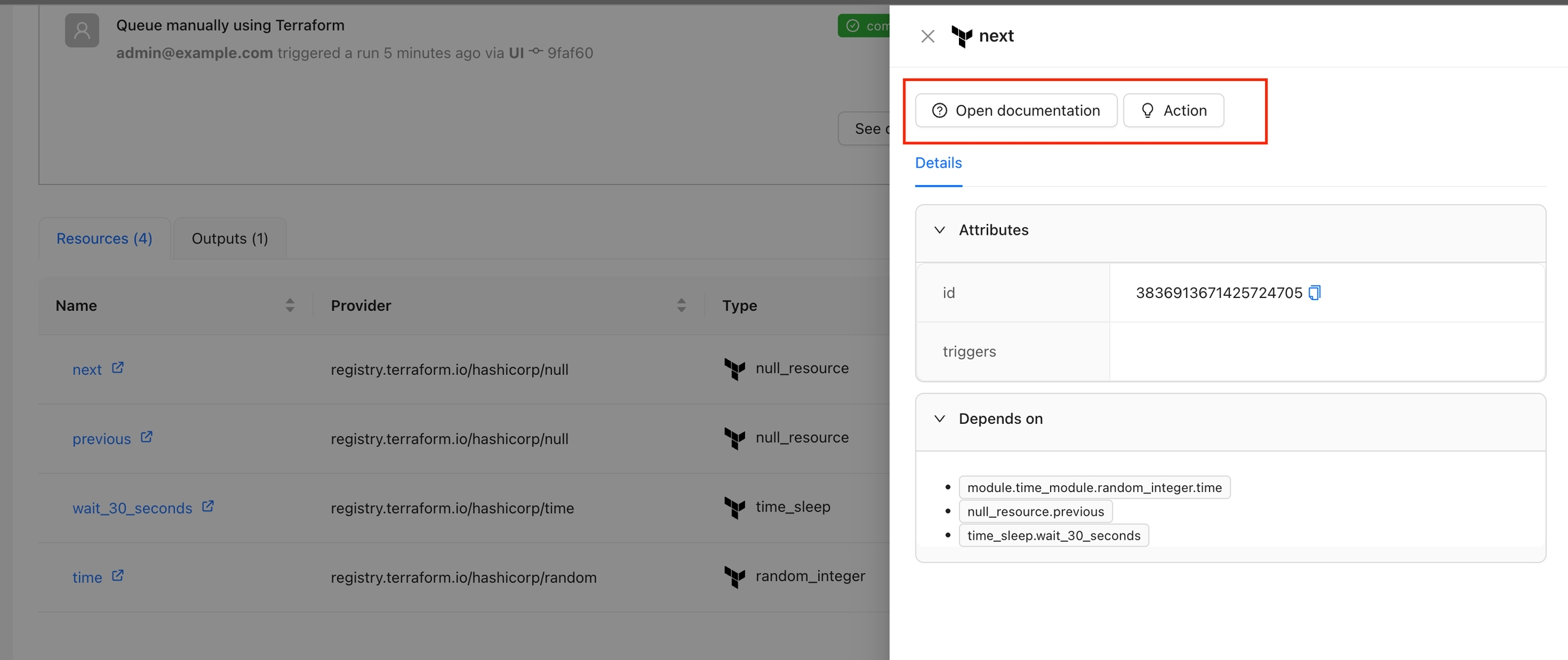
The Resource Details action is designed to show detailed information about a specific resource within the workspace. By using the context of the current state, this action provides a detailed view about the properties and dependencies in a tab within the resource drawer.
By default this Action is enabled and will appear for all the resources. If you want to display this action only for certain resources, please check filtering actions.
Navigate to the Workspace Overview or the Visual State and click a resource name.
In the Resource Drawer, you will see a new tab Details with the resource attributes and dependencies.
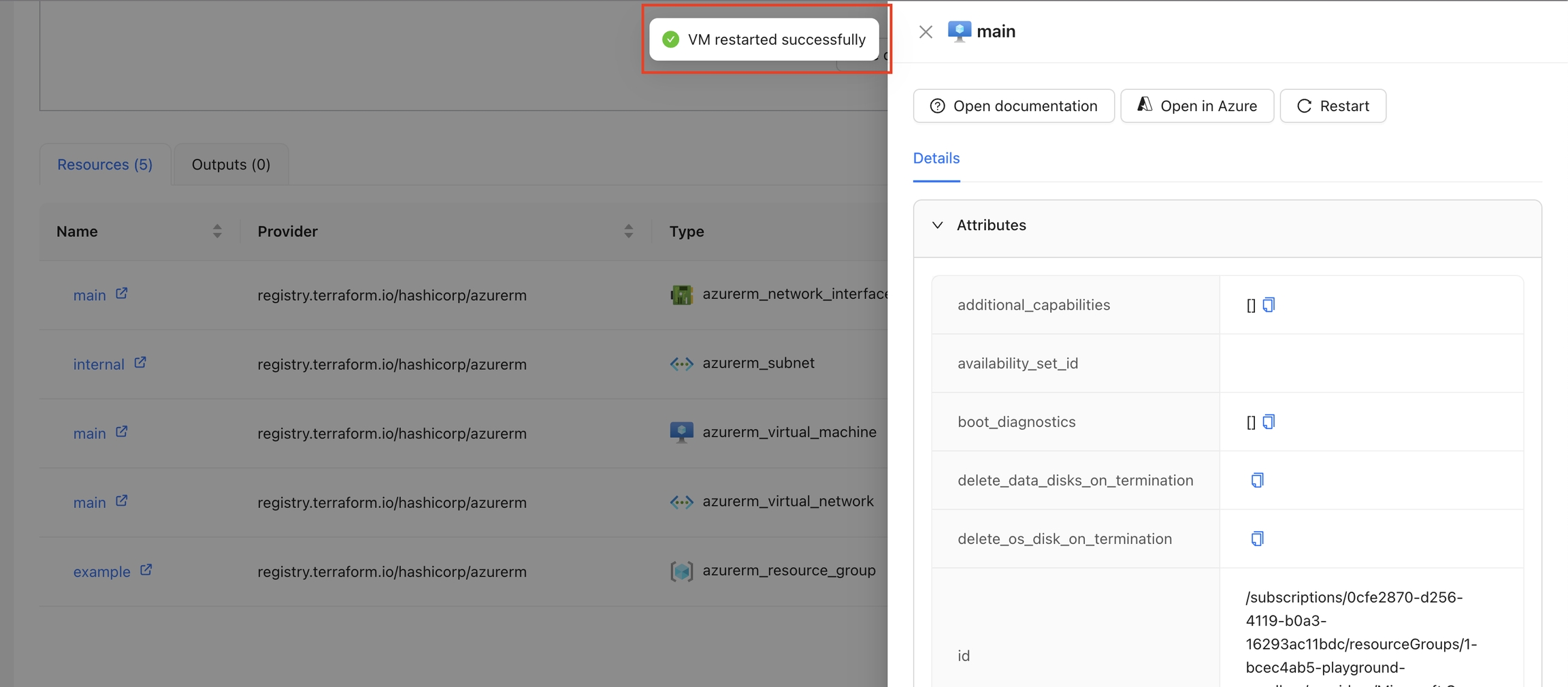
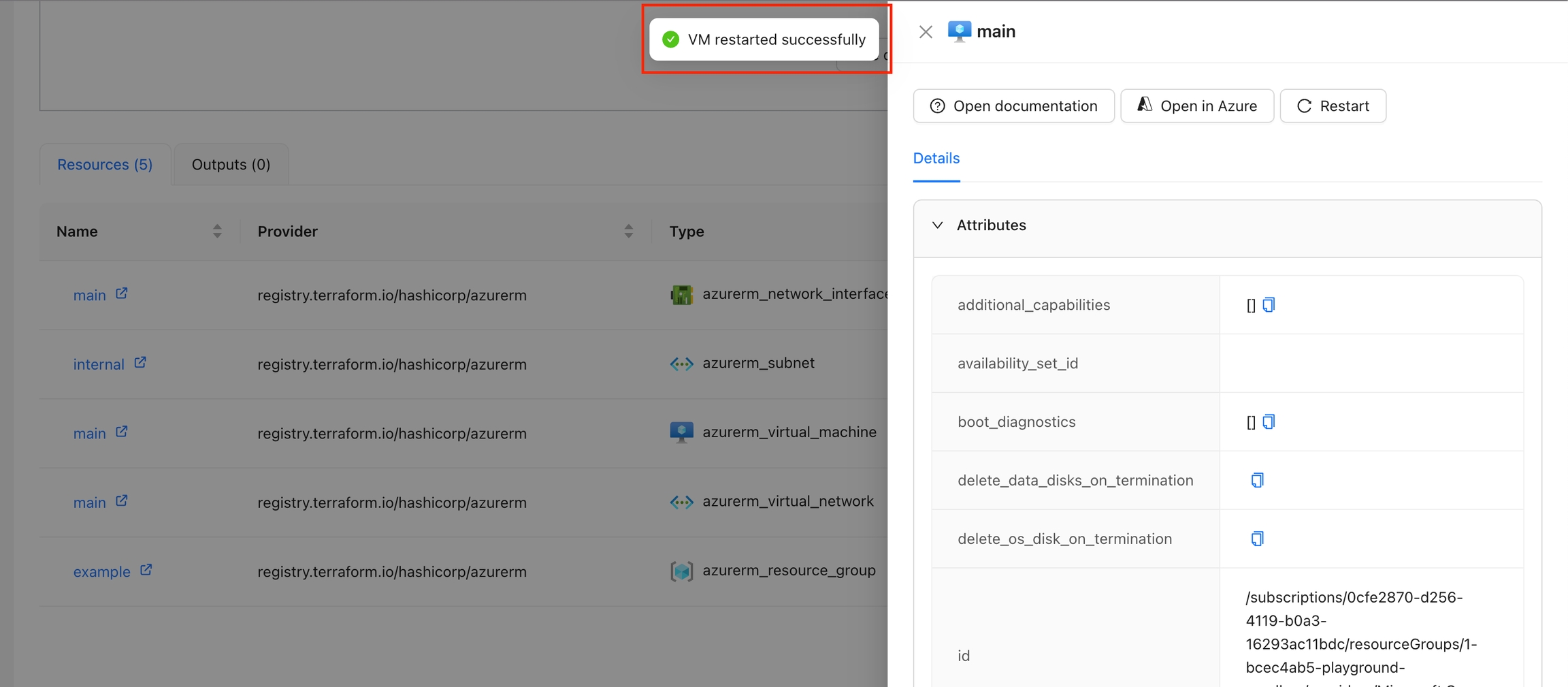
The Restart VM action is designed to restart a specific virtual machine in Azure. By using the context of the current state, this action fetches an Azure access token and issues a restart command to the specified VM. The action ensures that the VM is restarted successfully and provides feedback on the process.
By default, this Action is disabled and when enabled will appear for all resources that have resource type azurerm_virtual_machine. If you want to display this action only for certain resources, please check display criteria.
This action requires the following variables as Workspace Variables or Global Variables in the Workspace Organization:
ARM_CLIENT_ID: The Azure Client ID used for authentication.
ARM_CLIENT_SECRET: The Azure Client Secret used for authentication.
ARM_TENANT_ID: The Azure Tenant ID associated with your subscription.
ARM_SUBSCRIPTION_ID: The Azure Subscription ID where the VM is located.
The Client ID should have at least Virtual Machine Contributor access on the VM or resource group.
Navigate to the Workspace Overview or the Visual State and click on a resource name.
In the Resource Drawer, click the "Restart" button.
The VM will be restarted, and a success or error message will be displayed.
Security Warning
The current action shares the state with the OpenAI API, so it's not recommended for sensitive workspaces. Future versions will provide a mask method before sending the data.
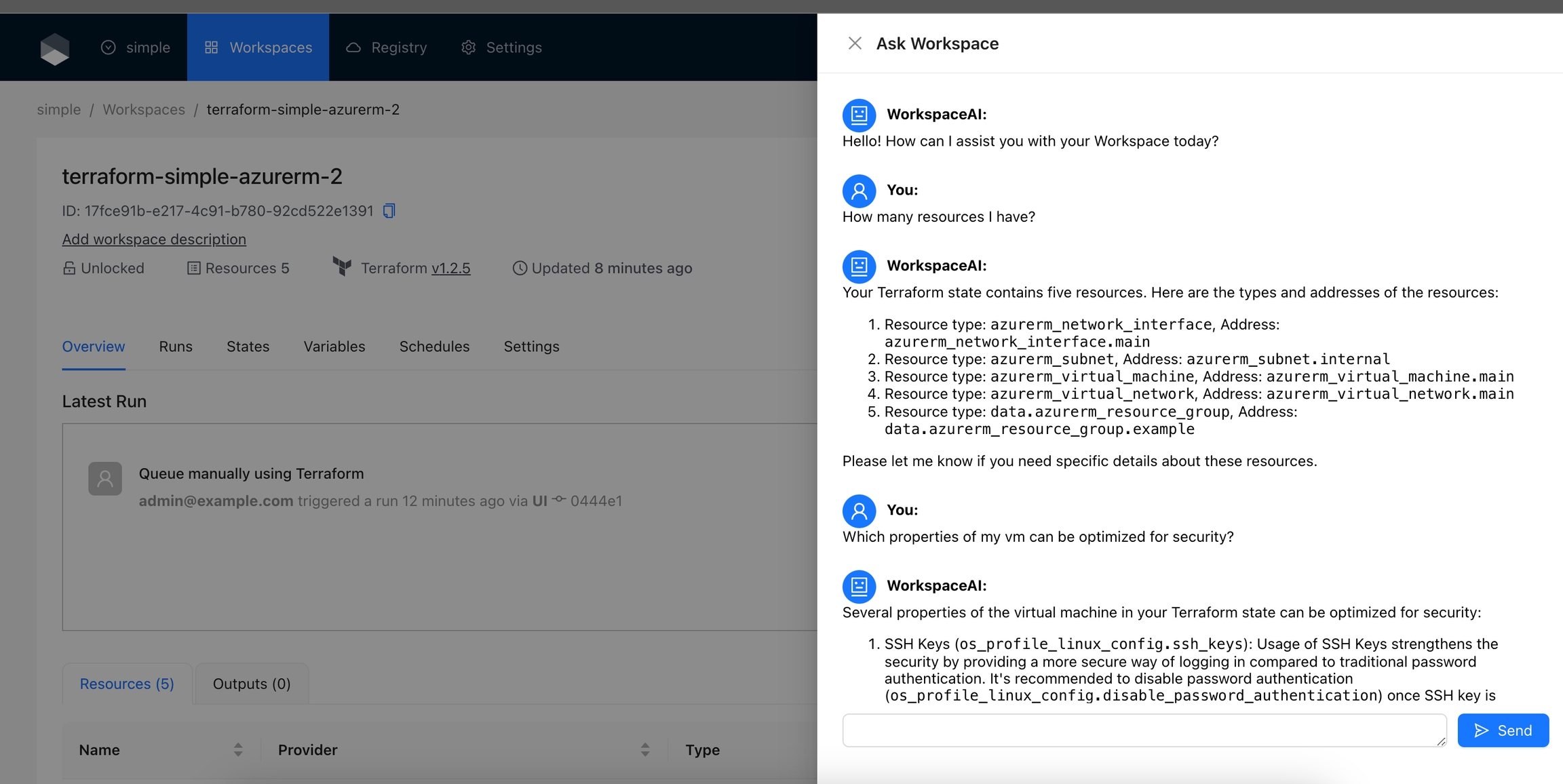
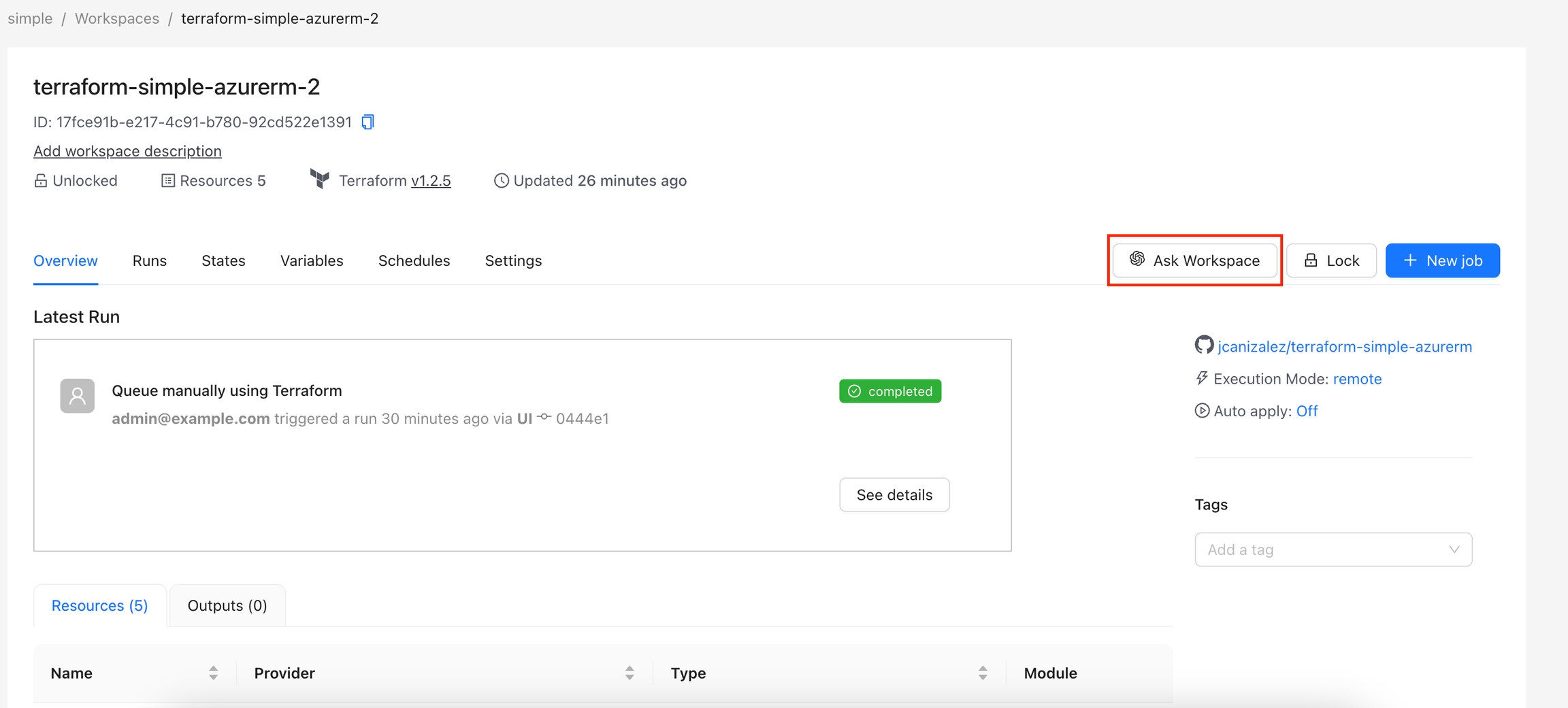
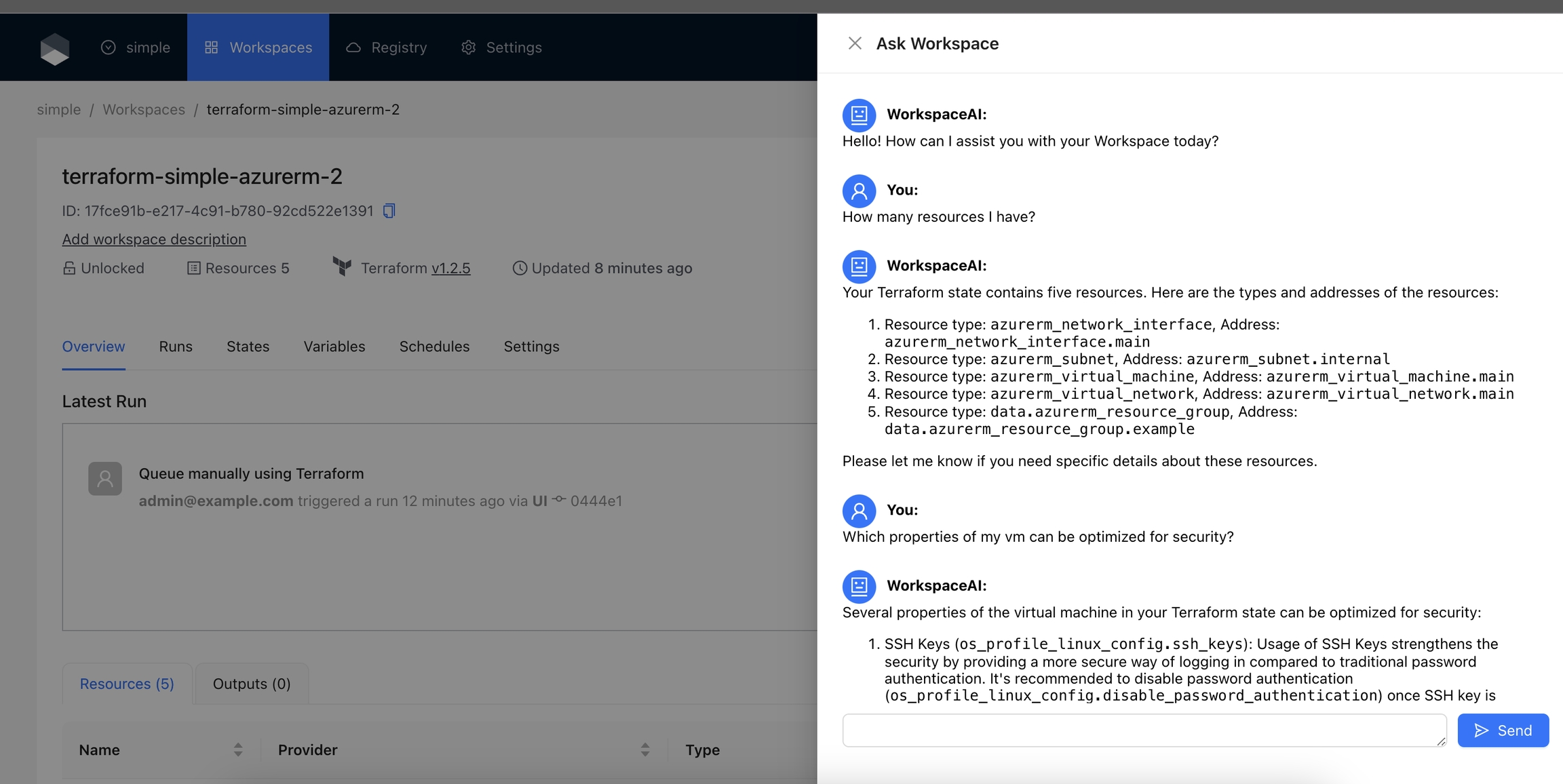
The Ask Workspace action allows users to interact with OpenAI's GPT-4o model to ask questions and get assistance related to their Terraform Workspace. This action provides a chat interface where users can ask questions about their Workspace's Terraform state and receive helpful responses from the AI.
By default, this Action is disabled and when enabled will appear for all resources. If you want to display this action only for certain resources, please check display criteria.
This action requires the following variables as Workspace Variables or Global Variables in the Workspace Organization:
OPENAI_API_KEY: The API key to authenticate requests to the OpenAI API. Please check this guide in how to get an OPEN AI api key
Navigate to the Workspace and click on the Ask Workspace button.
Enter your questions and click the Send button or press the Enter key.
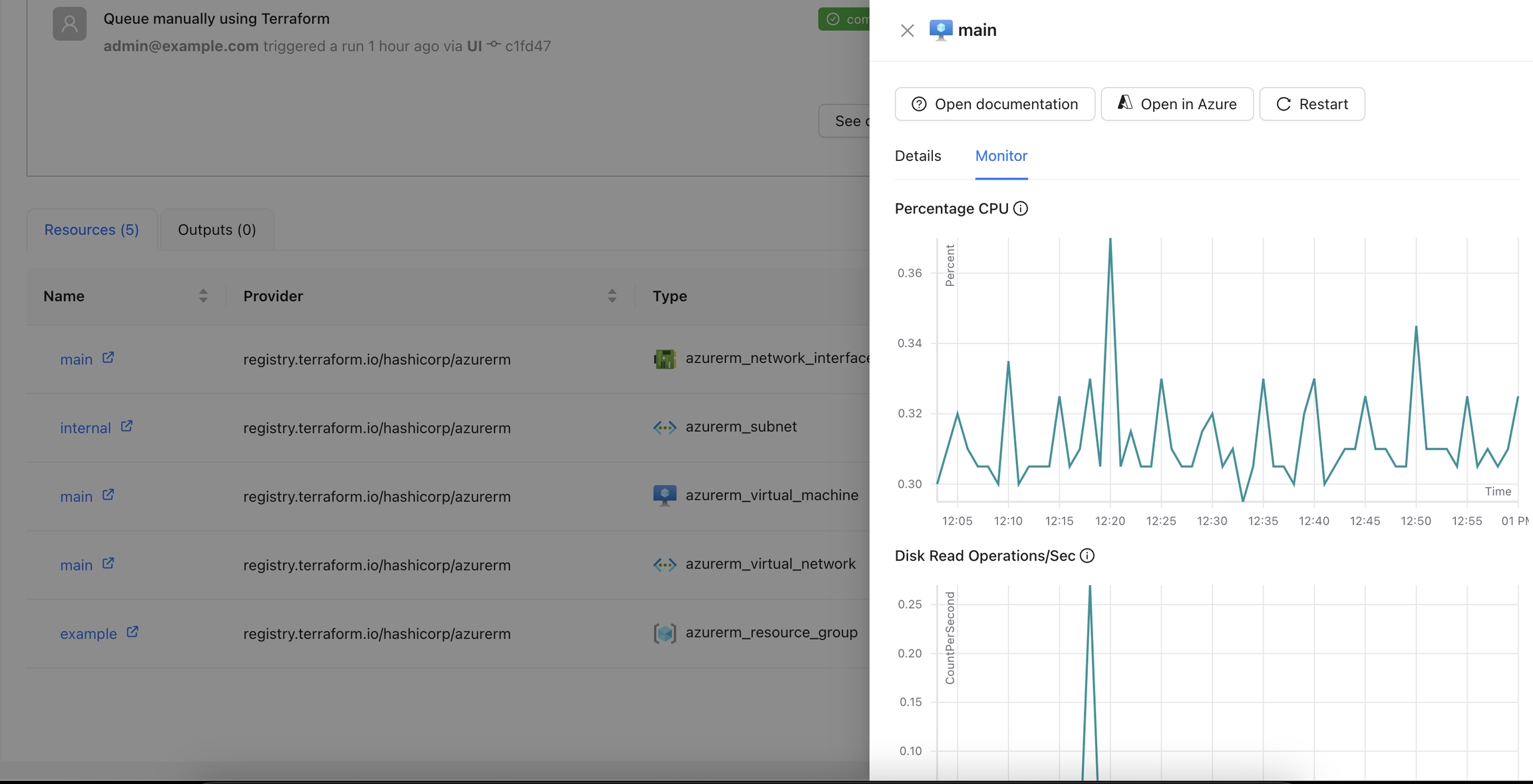
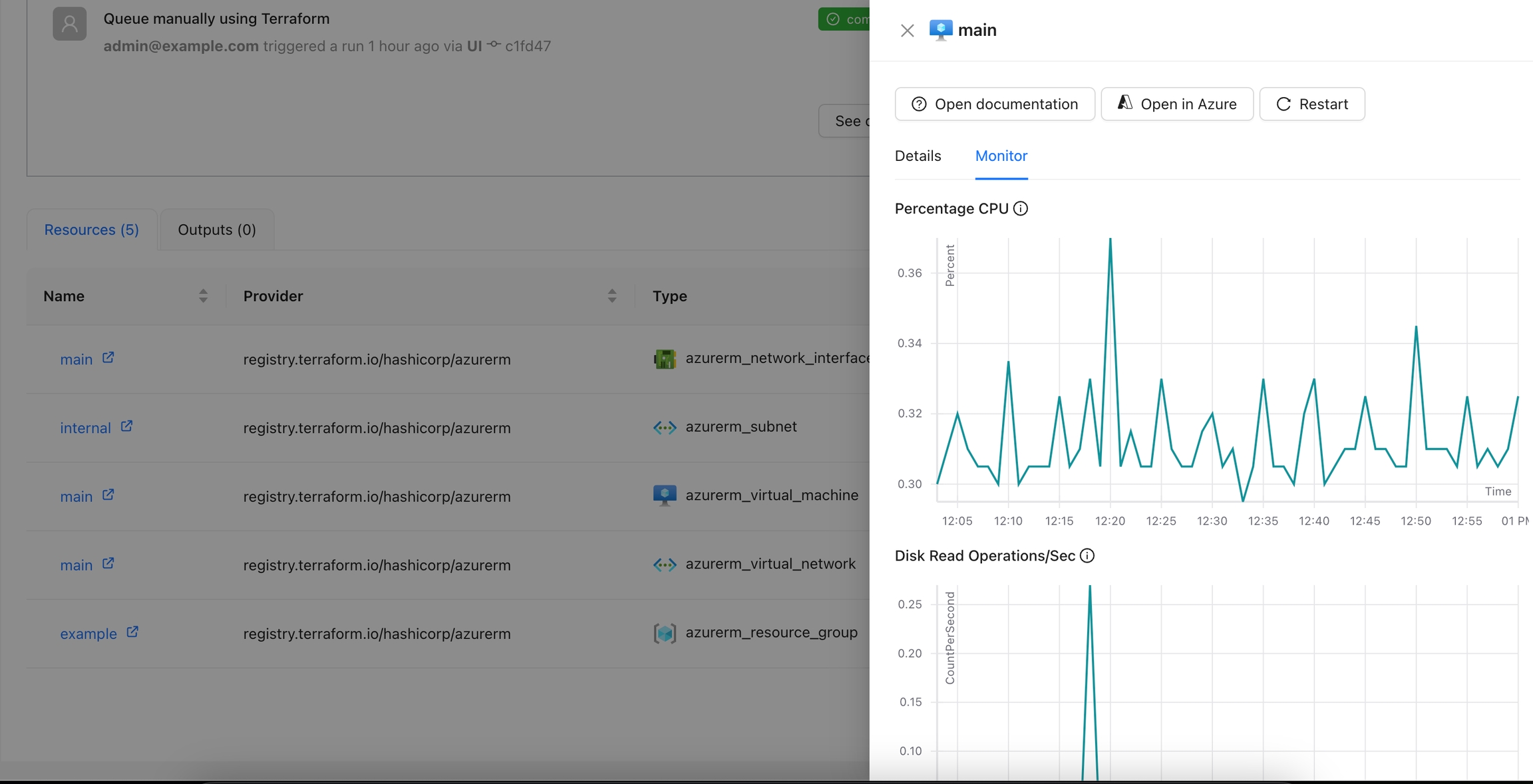
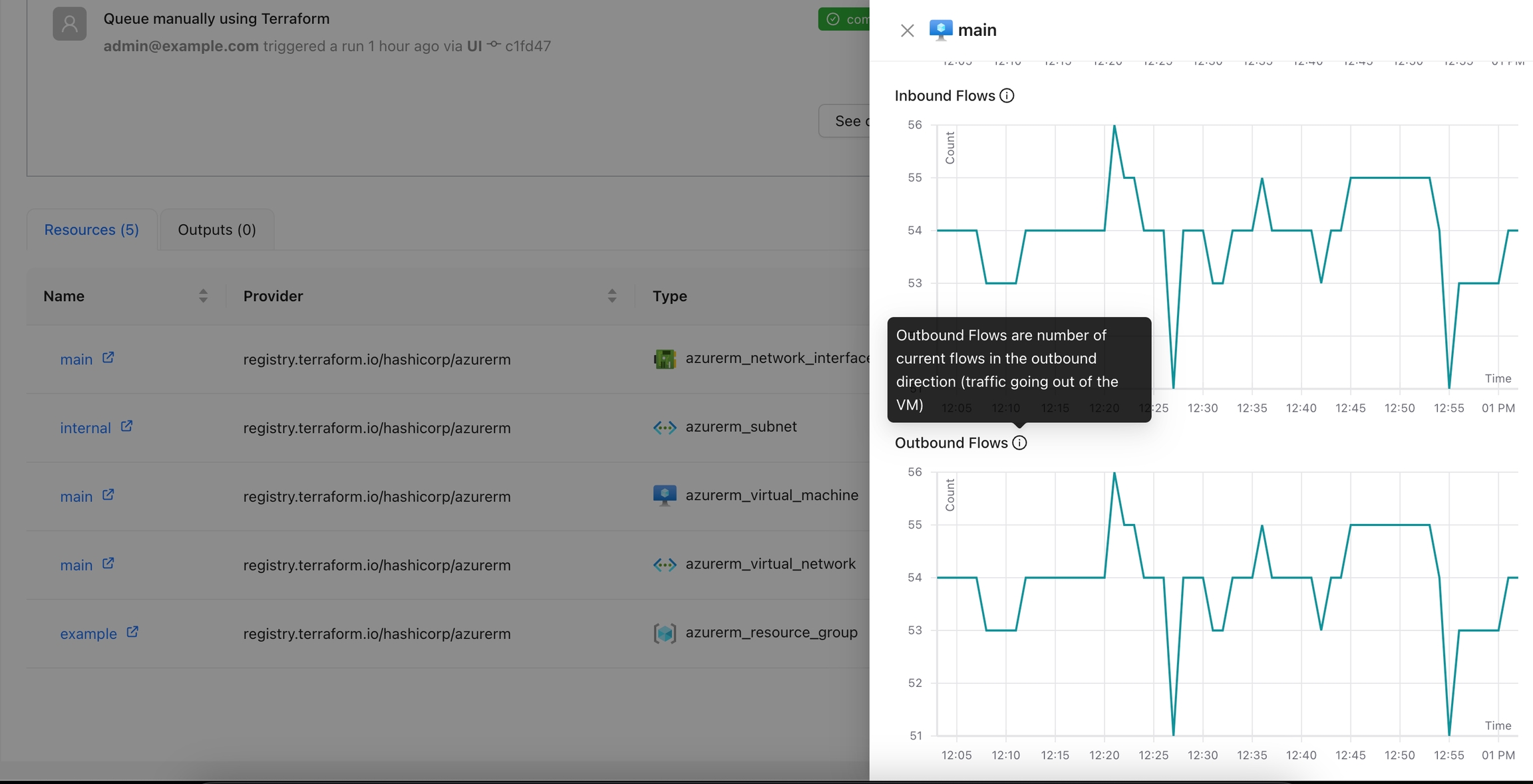
The Azure Monitor Metrics action allows users to fetch and visualize metrics from Azure Monitor for a specified resource.
By default, this Action is disabled and when enabled will appear for all the azurerm resources. If you want to display this action only for certain resources, please check .
This action requires the following variables as or in the Workspace Organization:
ARM_CLIENT_ID: The Azure Client ID used for authentication.
ARM_CLIENT_SECRET: The Azure Client Secret used for authentication.
ARM_TENANT_ID: The Azure Tenant ID associated with your subscription.
ARM_SUBSCRIPTION_ID: The Azure Subscription ID where the VM is located.
The Client ID should have at least Monitoring Reader or Reader access on resource group or subscription.
Navigate to the Workspace Overview or the Visual State and click on a resource name.
Click the Monitor tab to view metrics for the selected resource.
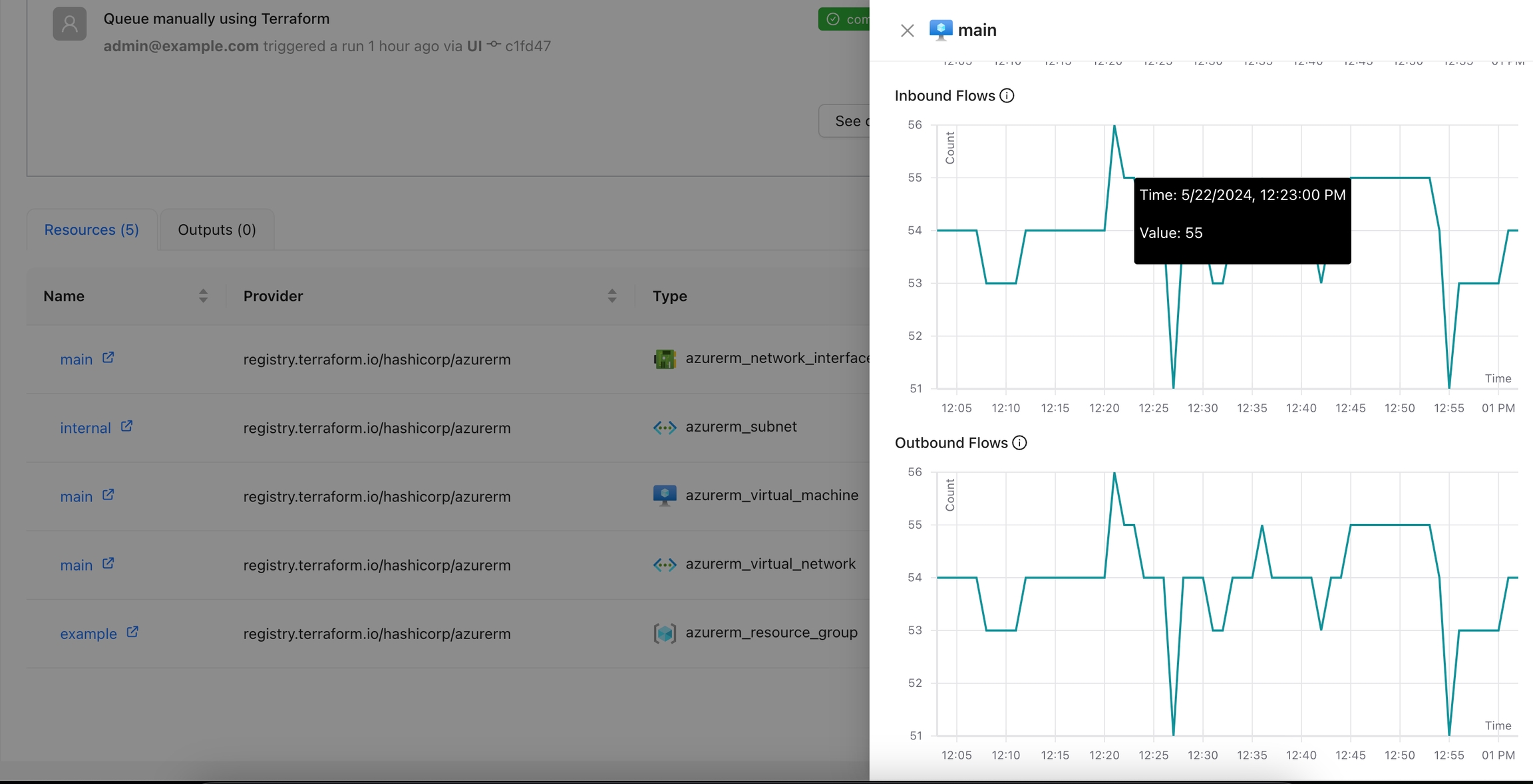
You can view additional details for the metrics using the tooltip.
You can see more details for each chart by navigating through it.